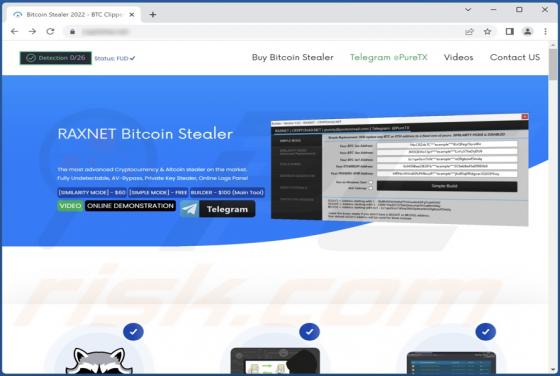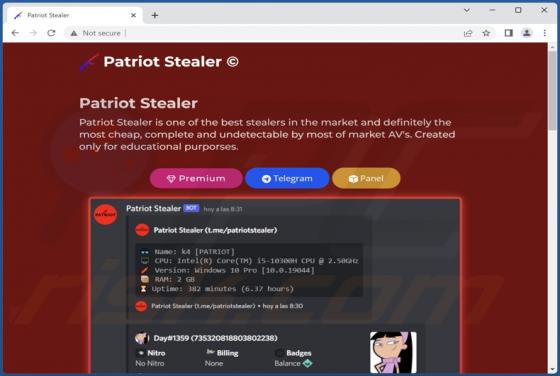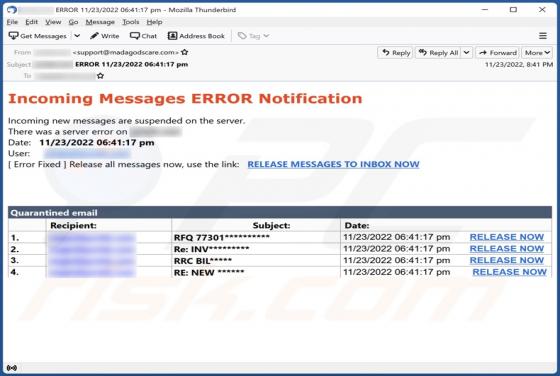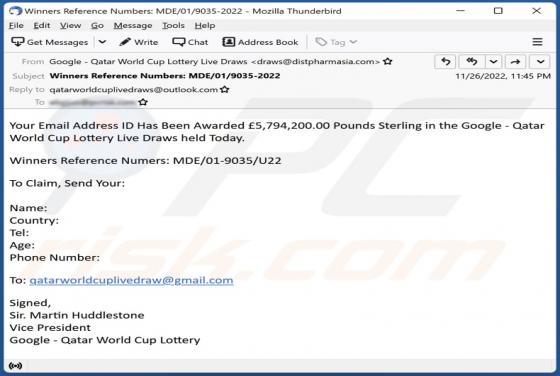
Cryptonite (.cryptn8) Ransomware
Cryptonite (.cryptn8) is a ransomware designed to encrypt data and demand payment for the decryption. As reported by Fortinet, this is a customizable version of ransomware that is available for free, which is uncommon. Malware of this type usually appends the encrypted files with an extension, an