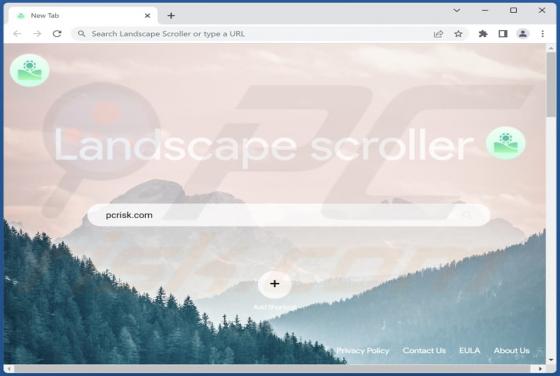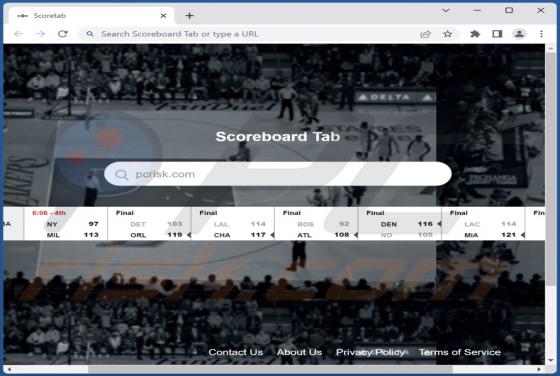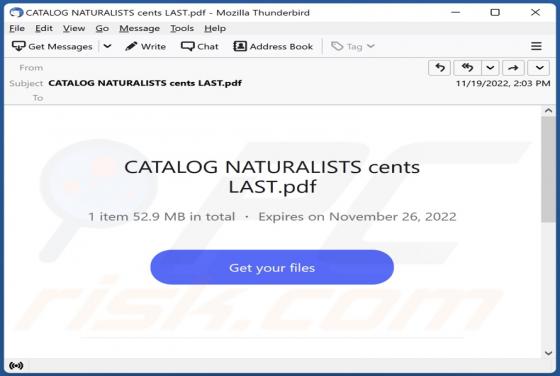
NATURALISTS Email Scam
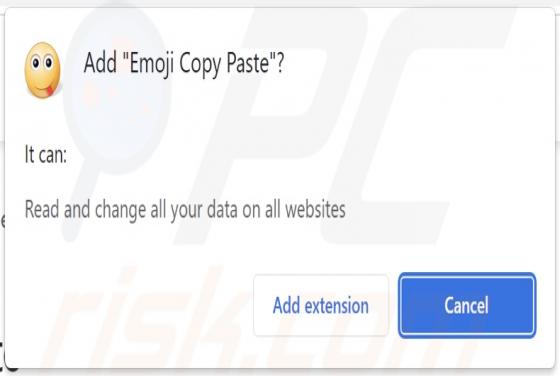
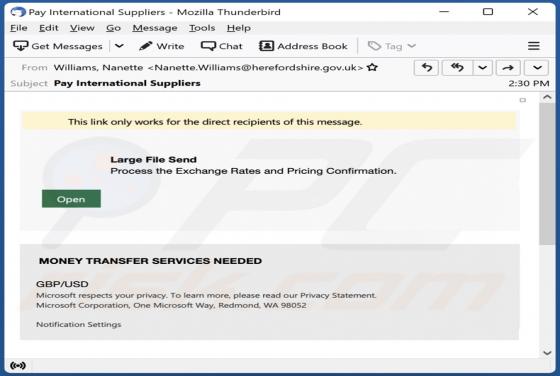
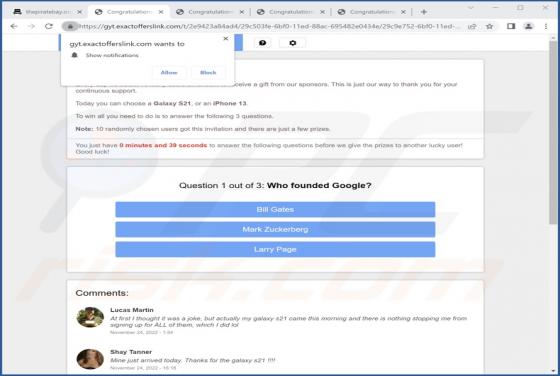
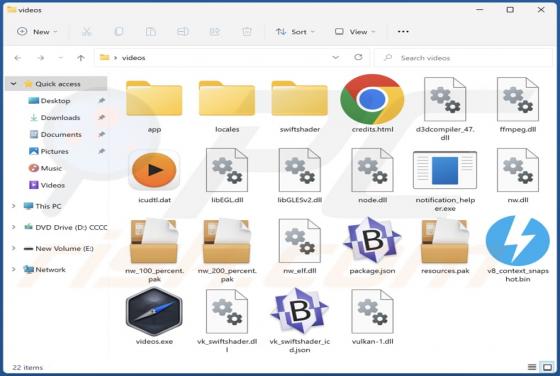
After inspecting the "NATURALISTS" email - we determined that it is spam operating as a phishing scam. This letter targets recipients' email account log-in credentials (passwords) by claiming that they must sign in to access the shared file. This spam email is presented as a notification r