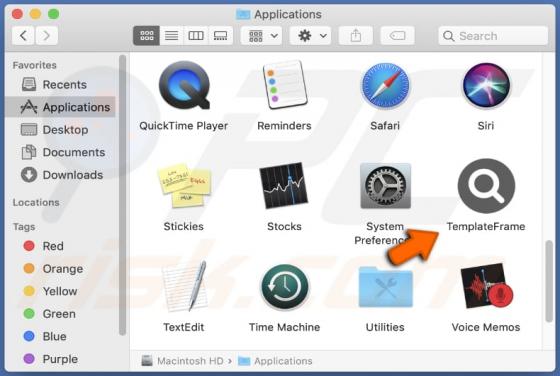
TemplateFrame Adware (Mac)
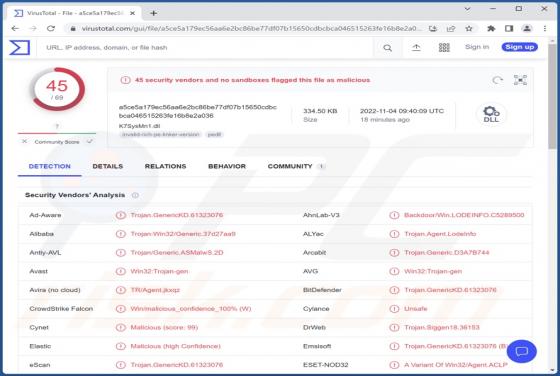
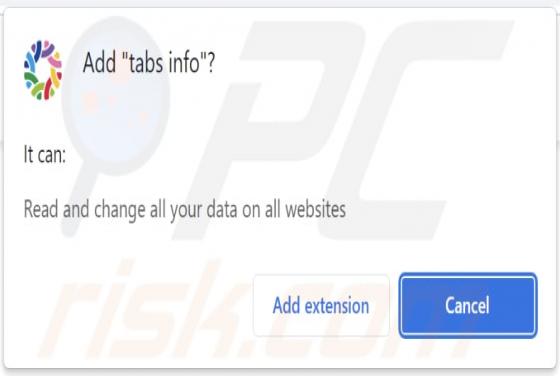
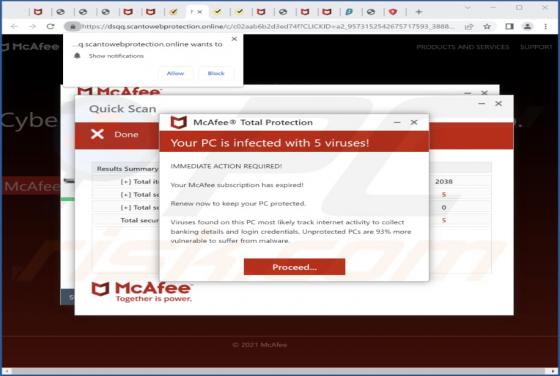
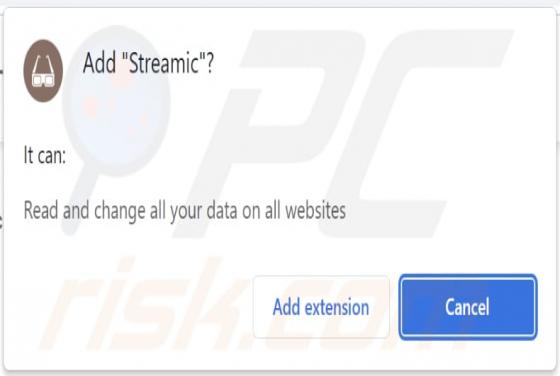
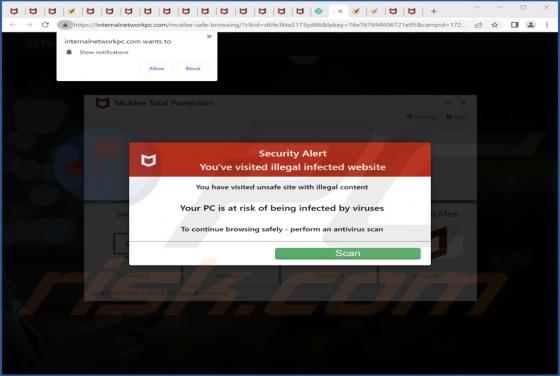
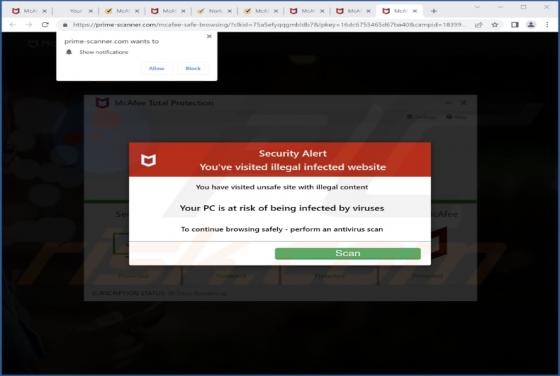
While analyzing various deceptive websites, our team discovered an application named TemplateFrame. After installing and testing this app, we found that it generates advertisements. Therefore, we classified TemplateFrame as adware. Clicking on advertisements displayed by TemplateFrame ca