A.E.S.R.T Ransomware
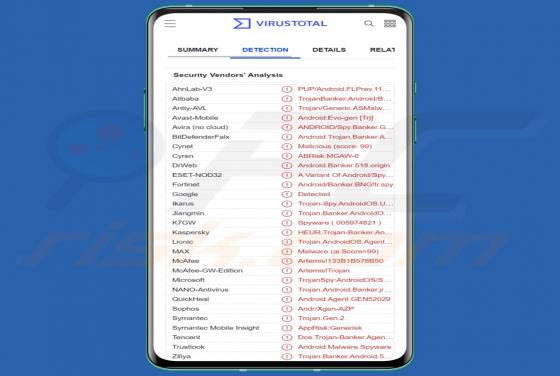
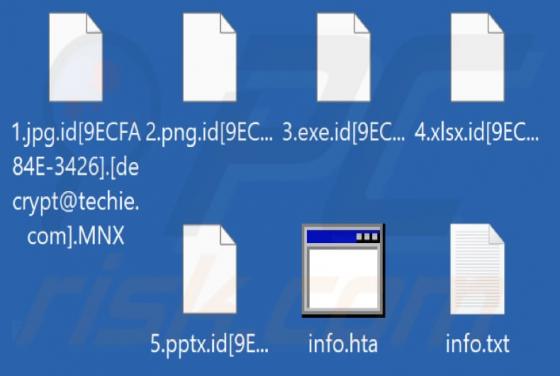
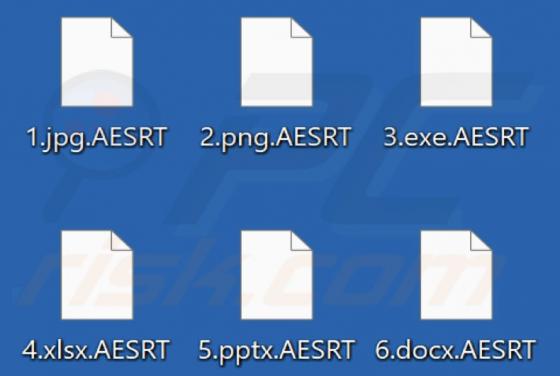
A.E.S.R.T is ransomware that encrypts files, appends the ".AESRT" extension to filenames, and displays a ransom note. Our malware researchers discovered A.E.S.R.T while inspecting samples submitted to the VirusTotal website. An example of how A.E.S.R.T renames files: it changes "1.jpg" to "1.jpg.A