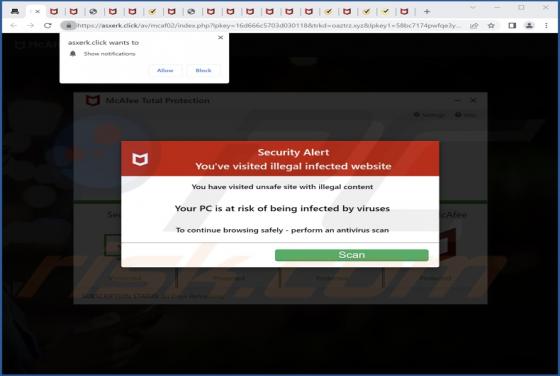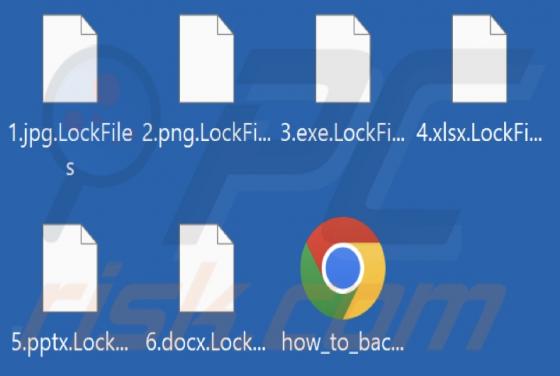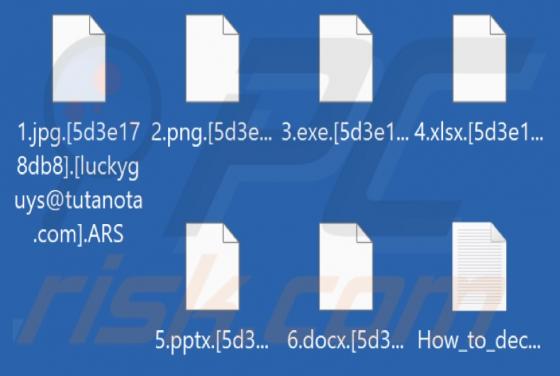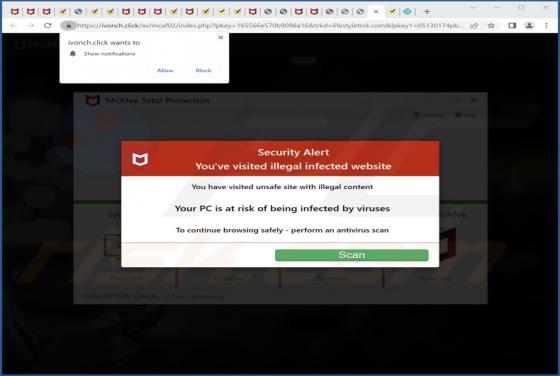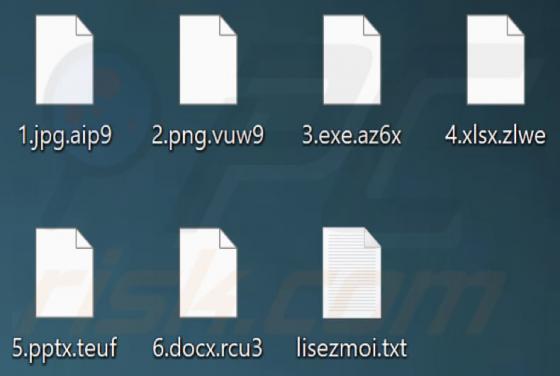
CRYPTONITE Ransomware
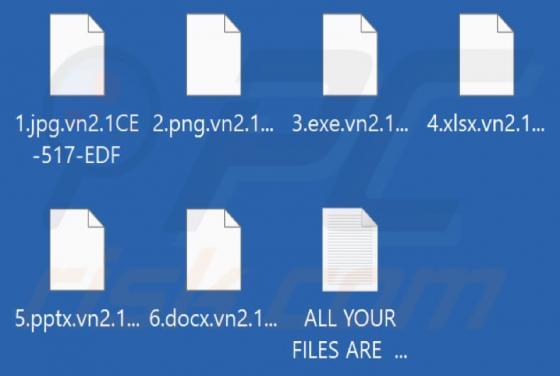
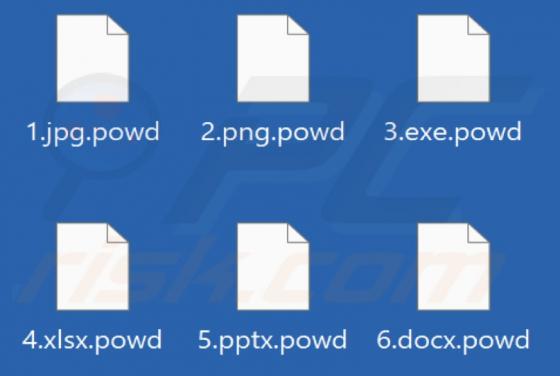
CRYPTONITE is ransomware based on another ransomware called Chaos. Our team discovered CRYPTONITE while checking the VirusTotal site for recently submitted malware samples. During our analysis, this ransomware encrypted files and appended four random characters as their new extension. Also, CRYPT