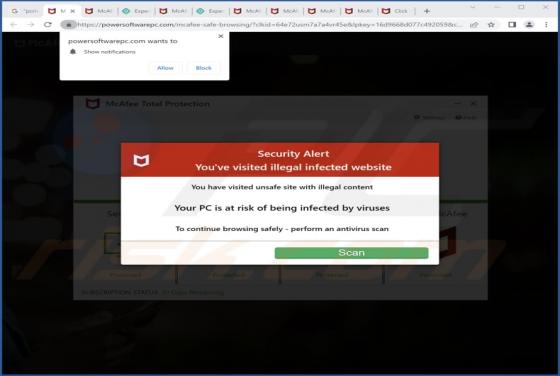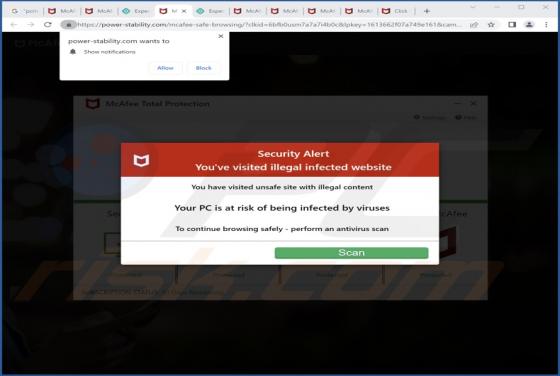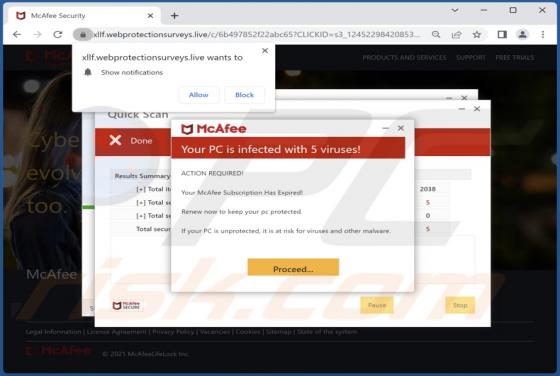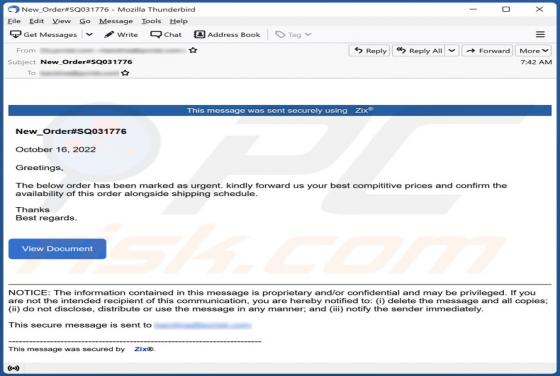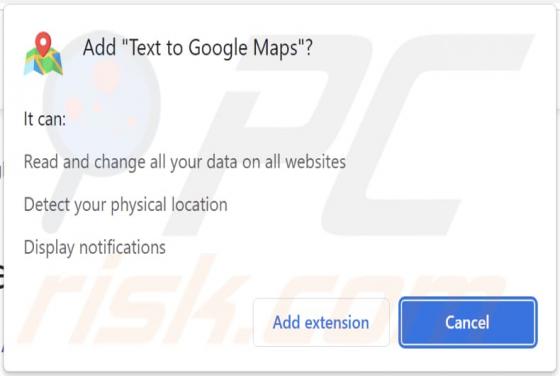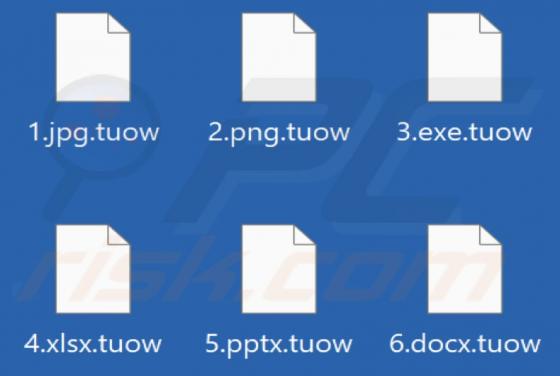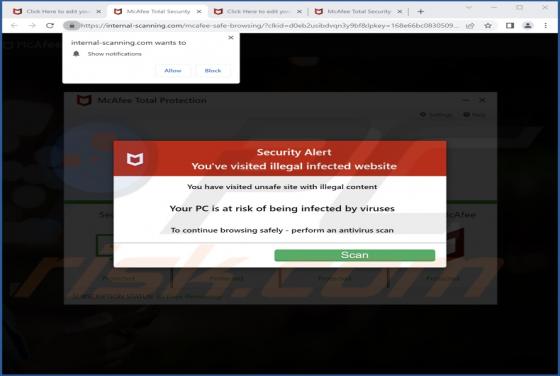
Internal-scanning.com Ads
Internal-scanning[.]com is a rogue page that runs scams, promotes browser notification spam, and redirects visitors to other (likely unreliable/dangerous) sites. Our researchers discovered this untrustworthy webpage while inspecting websites that use rogue advertising networks. Typically, pages l