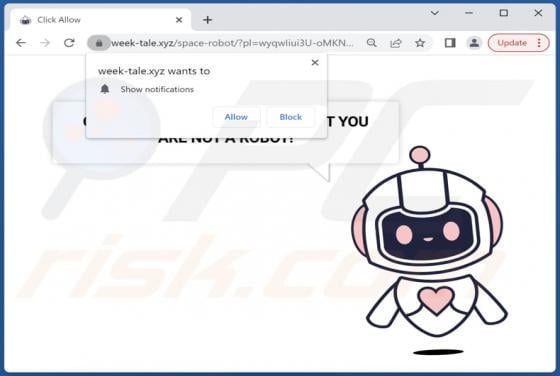
Week-tale.xyz Ads
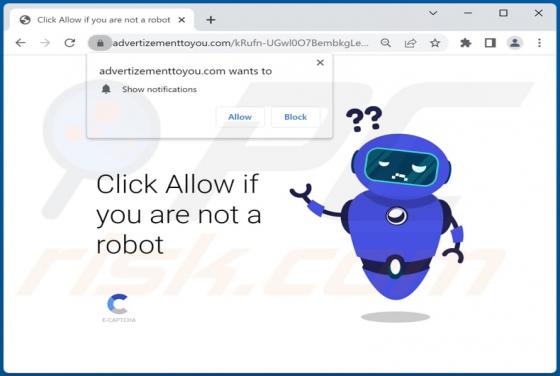
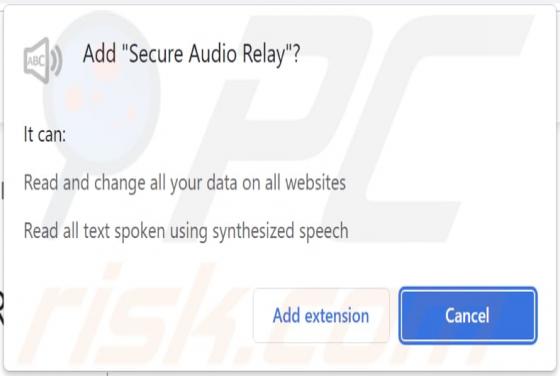
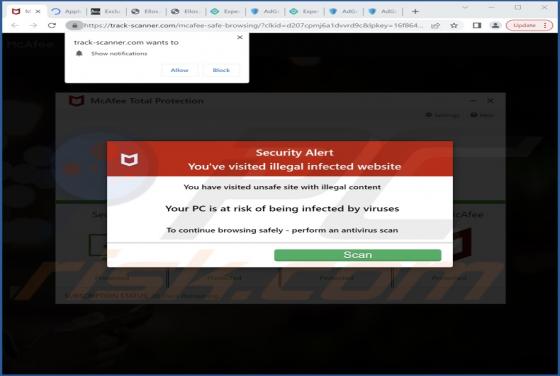
Week-tale[.]xyz is a deceptive website designed to lure visitors into granting it permission to show notifications. Also, it can redirect to a scam website (and possibly other untrustworthy pages). Our team discovered week-tale[.]xyz while examining illegal movie streaming pages, torrent sites, an