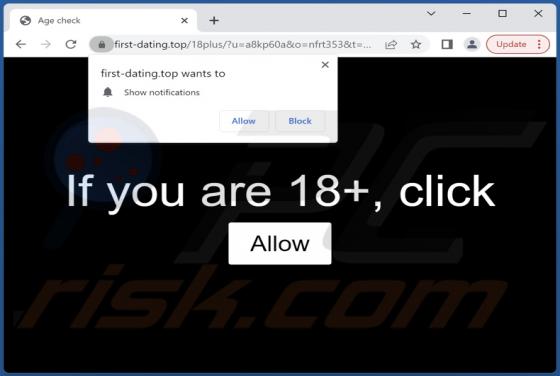
First-dating.top Ads
First-dating[.]top is a rogue page designed to trick visitors into allowing it to deliver browser notification spam. Furthermore, it can redirect visitors to other (likely untrustworthy/malicious) websites. Our research team found the first-dating[.]top webpage while inspecting sites that use rog