How to Detect if an Email Contains a Virus?
Table of Contents
1. Introduction
2. Understanding how Hackers Compose Emails
3. Phishing
4. The Classics never get Old
5. Scan All Attachments
6. Avoid Opening Executable Extension Files (.exe)
7. Conclusion
Introduction
Emails and the act of emailing have become a fundamental tool in how we communicate and do business. Despite their importance companies around the world have struggled to make them a secure platform free from viruses or malware (for the purposes of this article the words “virus” and “malware” are used interchangeably and are used to describe malicious code). Despite its no long history of use within the technology sector email is still the most effective delivery method for attacks. These attacks can siphon valuable data from a corporation’s servers, demand a ransom for access to data, steal banking information, or deny users access to data. Researchers at Verizon discovered in their 2017 Data Breach Investigation Report that 66% of all malware attacks analyzed for that period were installed via email. This is a massive majority considering the sheer amount of attack vectors available to hackers. Despite the number of attack vectors, available email is easily used by both the experienced and inexperienced hacker.

Unfortunately, there pervades an attitude amongst the majority of users that hackers are tech-savvy MIT dropouts who can hack into the most complex defense facilities at a whim. Why would such tech savants waste their time on using emails to get their revenge against companies and governments? While this stereotype is favored by Hollywood, the truth is that anybody with access to an internet connection has the potential at their fingertips to steal and become that little-understood creature known as a hacker. Hackers want to steal data, often from some moral prerogative, rather they want to make a quick buck. Till this day email is the best-proven start point in order to make that quick buck.
As emails are used to spread various pieces of malware, whether they are banking trojans, ransomware, adware, spyware or any other malicious piece of code designed to make somebodies day a nightmare, defending that front is a priority. It is a priority not just for companies but anybody that has access to an internet enabled device. Fortunately, despite it been such a critical area needing defense it can be fairly easily done. It involves understanding how hackers use emails to catch users off guard so they install malware. Once this is understood malicious emails can be easily detected and dealt with.
The rest of the article is dedicated to doing exactly that. Following these relatively simple steps will help prevent a large majority of malware infections.
Understanding how Hackers Compose Emails
Hackers compose their emails to be either enticing or to get your attention within a workplace environment. This is often referred to a social engineering and can be defined as the art of manipulating people so they give up confidential information. The types of information these criminals are seeking can vary, but when individuals are targeted the criminals are usually trying to trick you into giving them your passwords or bank information, or access your computer to secretly install. Hackers use such tactics as they are incredibly effective. Such tactics are effective as they exploit our natural inclination of trust.
This exploiting of our trust can happen in numerous ways and how it is done is dependent on the goals of the hacker. If the hacker was looking to steal banking information they will compose an email to appear on a bank asking you for your login credentials for example. The following more examples of how hackers will compose an email to trick you:
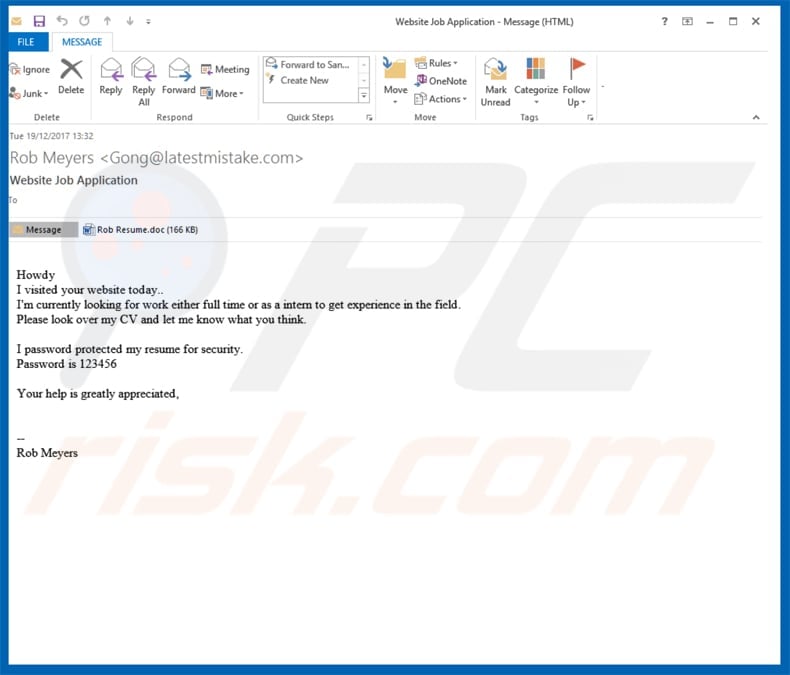
Emails which appear to be a resume. These emails are composed with the intention of getting the user to open an attachment. The attachment contains a malicious payload which when opened can be installed. This method has been seen in ransomware campaigns, namely CryptoWall, GoldenEye, and Cerber.
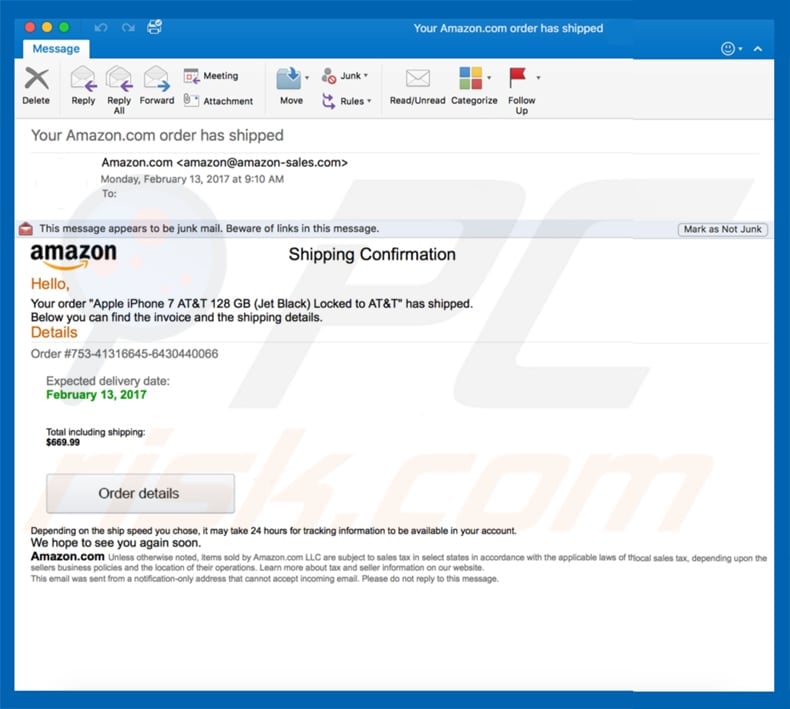
Emails claiming to be from e-commerce giant Amazon. This method was used to distribute the Locky ransomware and appear legitimate at first sight.
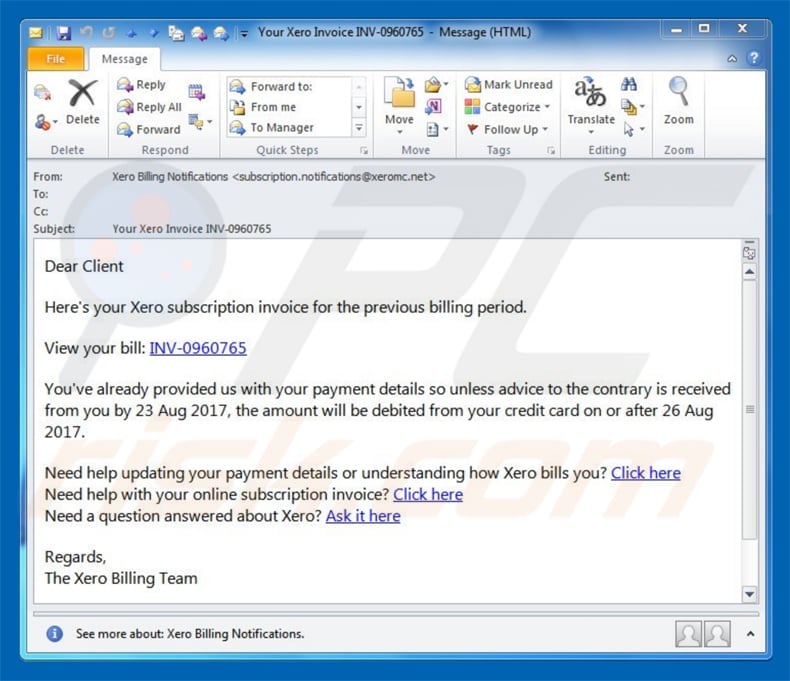
Emails containing invoices. This method often involves sending a mail with the subject header “Invoice XXXXX” and also have a few lines of text designed to get the user to download the attachment. The attachment is often presented as a Microsoft Word document but in reality that contains malware. Locky was spread through another campaign using this method.

Emails referencing sporting or other global events. For example, these can be composed in such a way as to get the users attention and work in much the same way as the methods detailed above.
To create an exhaustive list of all the types of malicious email could fill a novel and hackers don’t just use the same method over and over again. One of the ways to stay ahead of the curve looks for certain traits in emails known to be used, such as often they are written in poor English. It is also important to see who the sender is first before opening the email. If it sent from an address you are not in regular contact with it is advised not to open the email. You should also be wary of URL links, you can check their validity by hovering your mouse over the link, then look at the bottom left corner of your web browser. You should see the real URL that you’re going to be redirected to. If it looks suspicious or ends in .exe, .js or .zip, do not click on it. A simple web search will also display the legitimate URL.
Phishing
Phishing can be seen as the term used within the infosec community to describe the method which hackers attempt to get you to divulge important information. It has become the primary tool for the email-based attacker. Email phishing scams persuade victims to do something they shouldn’t. They can be sent in masses in a trawl for victims, or they can be customized for specific targets, often by researching their company’s organizational structure for information to make them sound more legitimate.
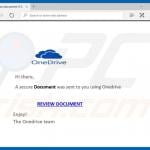
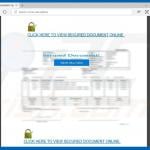
Here are a couple of samples of phishing emails:
Originally focused almost entirely on consumers, phishing has become one of the top threats to business email security. Especially when initiated by state-sponsored attackers, phishing emails are often used as a foothold to gain access to a company’s network. From there, the attacker can play a long game, quietly exploring the entire infrastructure and siphoning off information in the process. Phishing may be a well-established activity, but people are still falling for it. According to Verizon, 23% of recipients are still opening phishing messages. When they do so, almost half of them open emails within the first hour. Phishing attacks use much of the techniques stated above. Be aware that banks will never ask for account details over an unsecured platform such as email, and such details should never be divulged over an email.
The Classics never get Old
Over the past few years, email phishing scams have evolved to include the installation of malware as a second stage in the attack. It’s worrying, then, to note that 11% of phishing email recipients appear to be clicking on the attachments delivered along with the mail. All it takes is one employee to fall for the ruse. If more than one in ten is doing so, then the attackers are winning. In as much as stats illuminate trends, malware infections are a zero-sum game, in that it takes just one user to open an attachment. The malware delivered by email is changing, too. Email threats are like diseases in that we may quash them for a while, but we never truly get rid of them. Sooner or later, they’ll pop up again somewhere and begin to re-infect.
So it is with macro malware. A macro virus is a virus written in the same macro language used for software programs, including Microsoft Excel or word processors such as Microsoft Word. When a macro virus infects a software application, it causes a sequence of actions to begin automatically when the application is opened. This means that the user does not need to install a file rather just open an infected Word document. Popular in the late 90s, it is becoming a popular attack vector again, leading to attacks such as the 5 million USD Bitstamp bitcoin exchange breach. Emails arrive with attachments claiming to be courier notifications, resumes, and sales invoices as mentioned above.
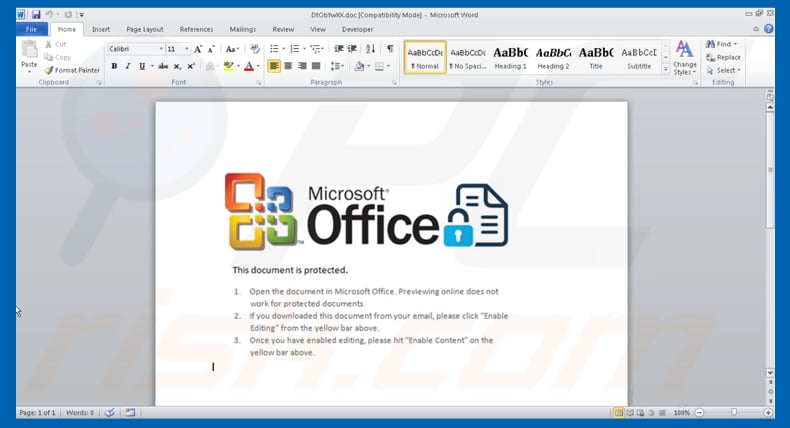
When opened, the document asks the victim to enable macros so that it can run, giving it the opportunity to attack the host. There’s a key difference, though: in the old days, macros infected computers themselves. These days, they serve as downloaders, opening the floodgates for an ocean of other malware, delivered from malicious servers. Clearly, secure email attachments are something that we should aim for.
Scan All Attachments
Part of efficiently navigating the dangerous waters of the internet and by default email services is knowing who to trust and when. This too can catch even the wary as a family member could send a malicious virus without knowing it. It is advised that you treat all emails wearily and scan all attachments. Many antivirus offerings have such a facility and it should be used where ever possible. One of the most malicious malware programs discovered in 2014 was a trojan file designed to look like an HTML page from an online banking service, designed to tempt users into clicking bad links and divulging personal information. To avoid similar styled attacks don’t click financial links in emails. Rather type the correct URL into your browser yourself to go directly to the genuine website for important transactions such as banking.
Even when scanning attachments knowing what type of file extensions are typically used by hackers will also help avoid a nasty infection. Extensions can be recognized by the letters that come after the period in the file name: .GIF (a picture format), .JPG or .JPEG (another picture format), .TIF or .TIFF (an image file format), .MPG or .MPEG4 (a movie), and .MP3 (a music or sound file). Avoid opening extensions you are not aware of even if scanned to be safe as your antivirus may not detect a piece of malware as such.
Avoid Opening Executable Extension Files (.exe)
As a default position never click on an executable file that being any file ending in .exe. These often carry malware and viruses and have been exploited by hackers numerous times. Hackers sometimes try to disguise these files by naming them with two extensions, such as image.gif.exe. In terms of programming languages, it is always the last extension that counts. It is important to note that .exe are the sign of an executable that will automatically run when you download it. Saying that legitimate programs such as Adobe Photoshop or Microsoft Word or any Web browser also use .exe files to install and launch their programs. If unsure if legitimate or not type the complete name into a current web browser or search engine, such as firefox.exe and see what search results show you.
Other program file types that you should be suspicious of and can possibly harm to your PC include those ending with .scr, .reg, .js, .msi, .hta, .bat, .cmd, .scr, .pif, .vbs, .wsf, .cpl, .jar and more. As mentioned above avoid opening these if you are unaware of the file type. Though again, all of these have legitimate uses, so look up the complete filename to see if it indeed a legitimate extension.
Conclusion
Hackers are a notoriously cunning lot and they are constantly evolving new methods to trick users into becoming victims. One of the things that have remained fairly constant is the use of emails as an attack vector. All the above information may seem like a lot to take in at first but by just adopting simple changes in how you respond and treat emails you can go a long way in preventing becoming a victim. Hopefully, the article went some way to also describing trends hackers follow in composing and spreading malware via emails.