Sextortion Scammers Change Tactics
In December 2019 this publication covered the emergence of sextortion scammers using ransomware in a bid to increase illicit earnings. It would appear that yet again such scammers are feeling the pinch and changes tactics once more in order to make money. The scammers behind the “Aaron Smith” scam, named after the email address used to send out the scam emails, made nearly 150,000 USD in Bitcoin in the period between August 30 and October 15. These profits have taken a remarkable knock, with the operators making only 17,000 USD in the first quarter of 2019.
In an effort to prevent this downward slide from continuing the scammers have changed tactics in order to prevent spam filters from stopping their emails of reaching their potential victims. According to researchers at Cisco Talos in a recently published article, revealed how the scammers adopted a relatively simple technique in an attempt to bypass spam filters. In the email example provided in the article, one would not be able to see that the message hides something behind the normal text. On deeper analysis, the message reveals a more complex underlying code that mixes plain text letters with HTML character entities. The recipient sees only the rendering of the email client. It is when the email is viewed in such a way the technique employed by the scammers is revealed.
The HTML code revealed that the scammers' embedded multiple images in the email body. This means that the anti-spam software and filters do not have a lot of information to scan and then determine if the message is spam or not. This technique was first seen in 2005 but it is no guarantee that the spam filters will be bypassed. As the researchers were quick to point out such filters have developed in that time. The scammers also faced another problem stemming from the Bitcoin address used to receive payments. Bitcoin addresses are a long complex set of characters and in order to enter it in the method of embedding images means that the scammers would have to enter the address in by hand.
This increases the likelihood of error and no easy payday. In some instances the scammers were demanding up to 7,000 USD in Bitcoin, if the wallet address was incorrect they would not receive a dime.
Understanding the Anatomy of the Scam
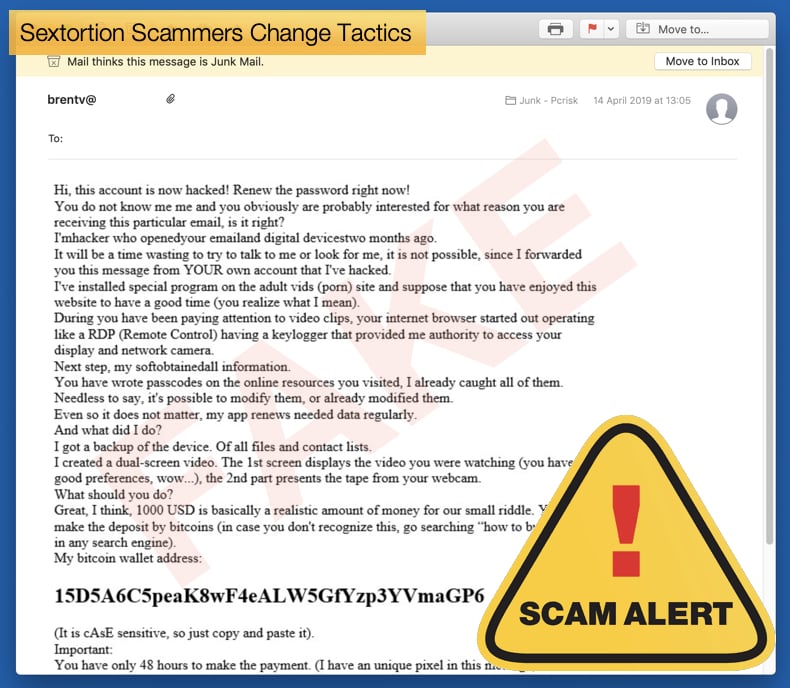
Sextortion scams at their core are a form of blackmail, which involves scaring the victim into paying. Such scams look to convince the victim that they have proof of the victim in a compromising position and threaten to inform the world of such. Often the scammer will give “evidence” in the form of a password used by the victim to convince the victim that the scammer has access to the computer question and all the supposed misbehavior on part of the victim. In another recently discovered campaign scammer are looking to play the social engineering campaign card again, this time in a newer novel way.
Here's a list of most popular (April 2019) sextortion email templates used by scammers (according to pcrisk.com malware researchers):
- I Hacked Your Device
- Your Account Was Hacked
- I Sent You An Email From Your Account
- I Have Bad News For You
The campaign discovered at the beginning of April 2019 involves the scammer stating they have placed a keylogger, a piece of malware which records keystrokes, on the victim’s computer and has evidence of you “playing with yourself” while visiting a porn site. Further the scammer insists that they have access to the victim’s contact list and will distribute the supposed proof of the embarrassing incident to all those on the contacts list. This is a fairly standard example of how the scam plays itself out, however, it does include another method to make some cash off the victim. The emails include a .zip file titled “proof of wrongdoing” or some variant thereof, once the potential victim opens the file they are told its password protected. To get the password the victim needs to “view the video” on the link in the email. However, there is no video at that link instead there is a page that asks you to pay 100 USD in bitcoin or other digital currency and he will send the password so you can open the file.
If the victim pays the 100 USD they still will not be able to see the supposed proof, because it is a password protected archive. This tactic plays on the behavior of victims to pay a smaller amount which may seem trivial in the face of the perceived embarrassment of having what is private exposed to the public at large. Researchers noted in another similar campaign that,
“Another campaign switched from attaching ZIP files to PDFs. These PDFs then link to a webpage, which is redirecting to a Cryptonator — a cryptocurrency wallet — portal requesting $25 for the ZIP file. This may be an indication that the initial effort of sending a ZIP file directly is not paying off as well as expected,”
These scams are almost entirely dependent on the victim believing that the scammer has compromising material. In many instances, no such material exists and users should not be duped into handing over funds on the basis of supposed evidence. Further users can add two-factor authentication (2FA) protection layer to online accounts, where available, is also a good step to make sure that cybercriminals do not get access to your private data. These means that even if a password is exposed online, hackers and scammers they still need to get through another layer of security. Another habit users can adopt is to scrutinize emails for the tell-tale signs your address has been included in a mass spam email campaign and to make sure passwords are not being used across sensitive accounts.
Share:

Karolis Liucveikis
Experienced software engineer, passionate about behavioral analysis of malicious apps
Author and general operator of PCrisk's News and Removal Guides section. Co-researcher working alongside Tomas to discover the latest threats and global trends in the cyber security world. Karolis has experience of over 8 years working in this branch. He attended Kaunas University of Technology and graduated with a degree in Software Development in 2017. Extremely passionate about technical aspects and behavior of various malicious applications.
PCrisk security portal is brought by a company RCS LT.
Joined forces of security researchers help educate computer users about the latest online security threats. More information about the company RCS LT.
Our malware removal guides are free. However, if you want to support us you can send us a donation.
DonatePCrisk security portal is brought by a company RCS LT.
Joined forces of security researchers help educate computer users about the latest online security threats. More information about the company RCS LT.
Our malware removal guides are free. However, if you want to support us you can send us a donation.
Donate
▼ Show Discussion