Avoid getting scammed by "I sent you an email from your account" spam email
Phishing/ScamAlso Known As: I Sent You An Email From Your Account spam
Get free scan and check if your device is infected.
Remove it nowTo use full-featured product, you have to purchase a license for Combo Cleaner. Seven days free trial available. Combo Cleaner is owned and operated by RCS LT, the parent company of PCRisk.com.
What kind of email is "I sent you an email from your account"?
"I sent you an email from your account" is a spam email campaign (scam) used by cyber criminals who threaten to proliferate compromising/humiliating videos of recipients if their ransom demands are not met. This is a common scam, and one of many similar versions.
If you receive this email, simply ignore it and do not believe any of the statements within the message. The email is proliferated via an "email spoofing" method used to falsify the sender's email address. In this way, scammers behind this email make it seem as if the recipient of the email is also the sender.
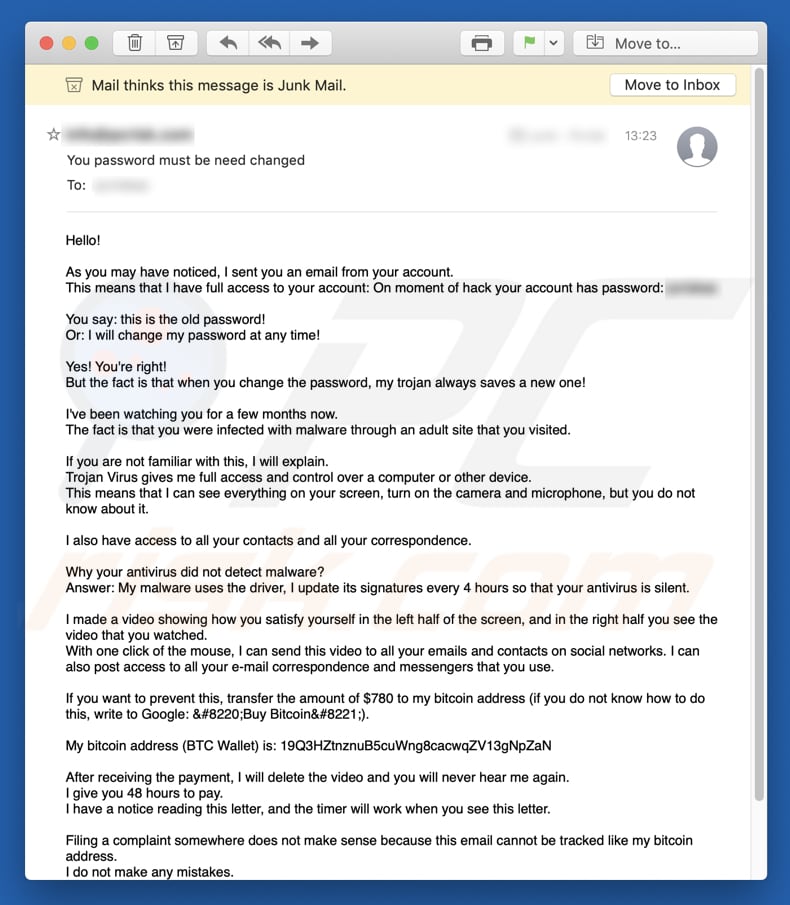
"I sent you an email from your account" email scam overview
Cyber criminals claim that they have gained full access to the recipient's email account and obtained the password. It is also stated that the computer is infected with a trojan that allows them to change the password at any time (even if the user creates a new one). According to these scammers, this trojan was installed when the recipient visited an adult website.
Furthermore, they state that they are capable of controlling the recipient's computer remotely, monitor activities in real time, turn the camera and microphone on, etc.
People behind the "I sent you an email from your account" scam claim that they have, at some point, recorded a compromising video that will be sent to all of the recipient's contacts, unless $780 in Bitcoins is transferred to a provided Bitcoin Wallet within 48 hours.
Furthermore, they also threaten to proliferate the video if the ransom email is shared with any other party. All statements regarding recorded videos, trojan infections, stolen data, etc. are false. Scammers send these emails to thousands of people hoping that some will fall for it. Never trust this or other similar scams.
| Name | I Sent You An Email From Your Account Email Scam |
| Threat Type | Phishing, Scam, Social Engineering, Fraud |
| Fake Claim | Scammer claims that he has infected victim's computer with a trojan and used it to record a compromising video. He also claims to have access to various recipient's accounts (including email). |
| Cyber Criminal Cryptowallet Address (Bitcoin) |
19Q3HZtnznuB5cuWng8cacwqZV13gNpZaN, 1P3eUgQzL12tDo2oh9csyo7HFxLer8vJsG, 1J9iAfnHhvhhMrP7c8n3bmvWh6CcjjynUt, 17g8bzF6fvGzWf2sWqbSx3vt66fbj7NTFm, 1CWL7u7EVXszicDh8CbXte1zndWk1LG6jo, bc1qc3lgelwfhy0ez5s0pdqgnhs5940gj2vsw9p35s, 1Fb847Hq9FhWbEs8VUFmehCKmk6fh2jcb9, 1KLfJMUv1xbLRikPr3x7BqQoMhZTgcuctn, 1F3qnUEQFrZ8fnNLzGEZaR9YCS4ePXsEni, bc1qwwt4p95kddm8y7ndtut33h49nuq3l92m9h5v0v (cyber criminals change their cryptowallet addresses with each new spam campaign). |
| Symptoms | Received an email that threatens to send supposedly recorded video of user watching adult videos to family members and colleagues. Email(s) in the inbox state that ones passwords have been stolen. |
| Distribution methods | This scam is spread wide via spam email campaigns. |
| Damage | Monetary loss - completely unnecessary payments for fake claims about hacking and in reality non-existent video recordings. |
| Malware Removal (Windows) |
To eliminate possible malware infections, scan your computer with legitimate antivirus software. Our security researchers recommend using Combo Cleaner. Download Combo CleanerTo use full-featured product, you have to purchase a license for Combo Cleaner. 7 days free trial available. Combo Cleaner is owned and operated by RCS LT, the parent company of PCRisk.com. |
Spam campaigns in general
Examples of other similar spam campaigns include Looked At You For Several Months, I Am A Spyware Software Developer, and So I'm The Hacker Who Broke Your Email. Scammers who spread these emails simply attempt to trick people into paying ransoms so that they do not reveal various photos or videos (they actually do not exist).
Another type of spam email campaign aims to infect recipients' computers with high-risk viruses such as TrickBot, Emotet, AZORult, Adwind, etc. These emails infect computers through attachments or links associated with Microsoft Office documents, PDF documents, archive files (ZIP, RAR, and so on), executable files, etc.
Opening these attachments leads to installation of malicious programs that often spread other infections or steal personal data (banking details, various passwords, logins, and so on). Having these programs installed can lead to financial loss, privacy issues, problems with browsing safety, or computer infections with other viruses such as ransomware.
We receive a great deal of feedback from concerned users about this scam email. Here is the most popular question we receive:
Q: Hi pcrisk.com team, I received an email stating that my computer was hacked and they have a video of me. Now they are asking for a ransom in Bitcoins. I think this must be true because they listed my real name and password in the email. What should I do?
A: Do not worry about this email. Neither hackers nor cyber criminals have infiltrated/hacked your computer and there is no video of you watching pornography. Simply ignore the message and do not send any Bitcoins. Your email, name, and password was probably stolen from a compromised website such as Yahoo (these website breaches are common). If you are concerned, you can check if your accounts have been compromised by visiting haveibeenpwned website.
How do spam campaigns infect computers?
Spam email campaigns that contain malicious attachments can only affect systems when an infected attachment is opened (or executable file is executed). Therefore, these emails cannot proliferate malware without the manual intervention of the recipient.
For example, if the attachment is a Microsoft Office document, it must be opened and permission to use macro commands given. Once this is done, malicious MS Office documents are able to download and install various computer infections. If the attachment is an archive file, it will probably contain an executable file that needs to be executed before it can do any harm.
How to avoid installation of malware?
If there is an email is received from an unknown/untrustworthy address or the email context seems irrelevant/does not concern you, do not open the presented link or attachment. Do not download software from dubious, unofficial websites (or other sources), using third party downloaders, peer-to-peer networks, and so on.
Install/download software carefully: check all available settings or options (such as "Custom", "Manual") and deselect additionally-included apps that you do not want to download/install. Never use third party, unofficial (fake) software updaters, since these often install viruses rather than the updates.
Use functions and tools provided by official software developers. Use Microsoft Office versions that are no older than 2010. Later versions have "Protected View" mode that can prevent malicious attachments from downloading various infections. If you have already opened malicious attachments, we recommend running a scan with Combo Cleaner Antivirus for Windows to automatically eliminate infiltrated malware.
Text presented in the "I sent you an email from your account" email message:
Subject: You password must be need changed
Hello!
As you may have noticed, I sent you an email from your account.
This means that I have full access to your account: On moment of hack your account has password: *********You say: this is the old password!
Or: I will change my password at any time!Yes! You're right!
But the fact is that when you change the password, my trojan always saves a new one!I've been watching you for a few months now.
The fact is that you were infected with malware through an adult site that you visited.If you are not familiar with this, I will explain.
Trojan Virus gives me full access and control over a computer or other device.
This means that I can see everything on your screen, turn on the camera and microphone, but you do not know about it.I also have access to all your contacts and all your correspondence.
Why your antivirus did not detect malware?
Answer: My malware uses the driver, I update its signatures every 4 hours so that your antivirus is silent.I made a video showing how you satisfy yourself in the left half of the screen, and in the right half you see the video that you watched.
With one click of the mouse, I can send this video to all your emails and contacts on social networks. I can also post access to all your e-mail correspondence and messengers that you use.If you want to prevent this, transfer the amount of $780 to my bitcoin address (if you do not know how to do this, write to Google: Buy Bitcoin ).
My bitcoin addresses (BTC Wallets) are: 19Q3HZtnznuB5cuWng8cacwqZV13gNpZaN, 1HPhZrmyevkNXKo1MYnZG1A65p2PtyEpqc, 18kXxMp9NuTMUFVAfXR4TFT4CrrHWVzwm4, 1PNpAXTo6jh4V9dhXRvimNYqPYjvZEnQiu, 16LBDius3vg6ufFvnc7PGXfiTZgphuZgr5, 18eBGkYam1wjz1S77jz3VmADuYYFzhA3vB, 1BPUUNghhuwQjDDvFd3TnJz2ato5dyDLr8, 1DrCbXWfTqJbaiak2wjGUQiEo1WBzCBnof, 1GEhuEajkFXVe7vhtZqy1hRLdCaguhWBC2, 19rvCcYfSwPUSvJJKNyTyRFi5vxt6zaqJC, 1KeCBKUgQDyyMpaXhfpRi2qUvyrjcsT44o, 1Jh1miFmhTmGQvn6Zejaqg85viD4k1vVjG, 142e8SgyTLnkvwkDkNNon9jMtKY4UDvQqr, 1GoWy5yMzh3XXBiYxLU9tKCBMgibpznGio, 1GdSHQ4aE7zUD8HDqVJDEwU9dxn3LfJLMK, 1N5PXJHzJFyFfyqd32Gn9FZsVzNz8hqjqs, 1JBFFHR8tGiMgYLpnZCVG8n4cSpm591urc, 14tfS3yWL2cABhXVJZ97XRhuDXC69aWH6Y, 1N6dubqFmnyQ2qDWvi32ppVbc3kKMTYcGW, 1DHymxN8JqSwECGLPVbRMVWXrod8vvii5A
After receiving the payment, I will delete the video and you will never hear me again.
I give you 48 hours to pay.
I have a notice reading this letter, and the timer will work when you see this letter.Filing a complaint somewhere does not make sense because this email cannot be tracked like my bitcoin address.
I do not make any mistakes.If I find that you have shared this message with someone else, the video will be immediately distributed.
Best wishes!
Another variant of "I sent you an email from your account" email letter:
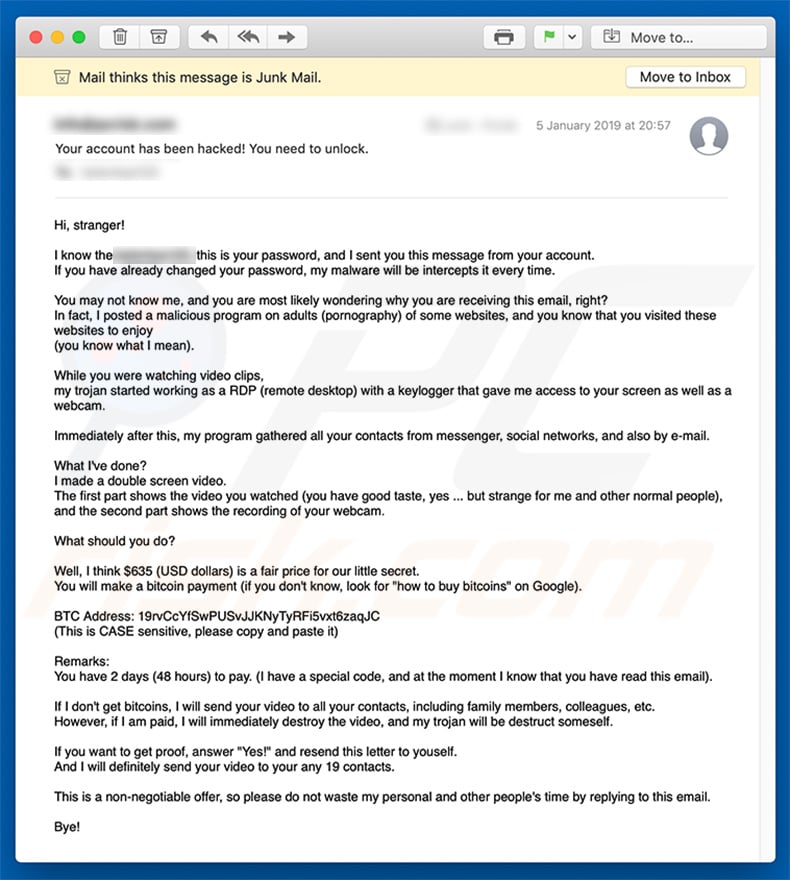
Text presented within this mail:
subject: Your account has been hacked! You need to unlock.
Hi, stranger!
I know the ********, this is your password, and I sent you this message from your account.
If you have already changed your password, my malware will be intercepts it every time.You may not know me, and you are most likely wondering why you are receiving this email, right?
In fact, I posted a malicious program on adults (pornography) of some websites, and you know that you visited these websites to enjoy
(you know what I mean).While you were watching video clips,
my trojan started working as a RDP (remote desktop) with a keylogger that gave me access to your screen as well as a webcam.Immediately after this, my program gathered all your contacts from messenger, social networks, and also by e-mail.
What I've done?
I made a double screen video.
The first part shows the video you watched (you have good taste, yes ... but strange for me and other normal people),
and the second part shows the recording of your webcam.What should you do?
Well, I think $635 (USD dollars) is a fair price for our little secret.
You will make a bitcoin payment (if you don't know, look for "how to buy bitcoins" on Google).BTC Address: 19rvCcYfSwPUSvJJKNyTyRFi5vxt6zaqJC, 1J36BsmxdqhuJhaSftiTc3MqEhmgdwcCNT, 1CZVUZa4sJrzQX5mBLucdgAMeVvkaj2dmv, 1MrUDSrZiqD3ijxsBUPt2SukoFy534orP2, 15G9wyGRDssFXsfwEm1ihdJs2xabVPDu68, 142e8SgyTLnkvwkDkNNon9jMtKY4UDvQqr, 1NL9MTdnTxsVxEg9nHeY5oiw5U9Mxzsh8v, 1DASN5fH1E1PCoxU9qMEF7QDjnXcA2b3Km, 1GoWy5yMzh3XXBiYxLU9tKCBMgibpznGio, 1B3Lx1t4CQSt3ck85bqzGHC9TeEQGANhUR, 19qqYeGgbzhT8Lic5WsbDZgJkzAy82R6fF, 1EHDCx1rXd7w6SguvcneeotsPhyDaetGKm, 14H8TULh8pw6RDB897Shtx88jobVu3RaVU, 12rXGKW3dVmyUCTTuSUpP8dm118Di4MHhd
(This is CASE sensitive, please copy and paste it)Remarks:
You have 2 days (48 hours) to pay. (I have a special code, and at the moment I know that you have read this email).If I don't get bitcoins, I will send your video to all your contacts, including family members, colleagues, etc.
However, if I am paid, I will immediately destroy the video, and my trojan will be destruct someself.If you want to get proof, answer "Yes!" and resend this letter to youself.
And I will definitely send your video to your any 19 contacts.This is a non-negotiable offer, so please do not waste my personal and other people's time by replying to this email.
Bye!
Yet another variant of this email spam campaign:
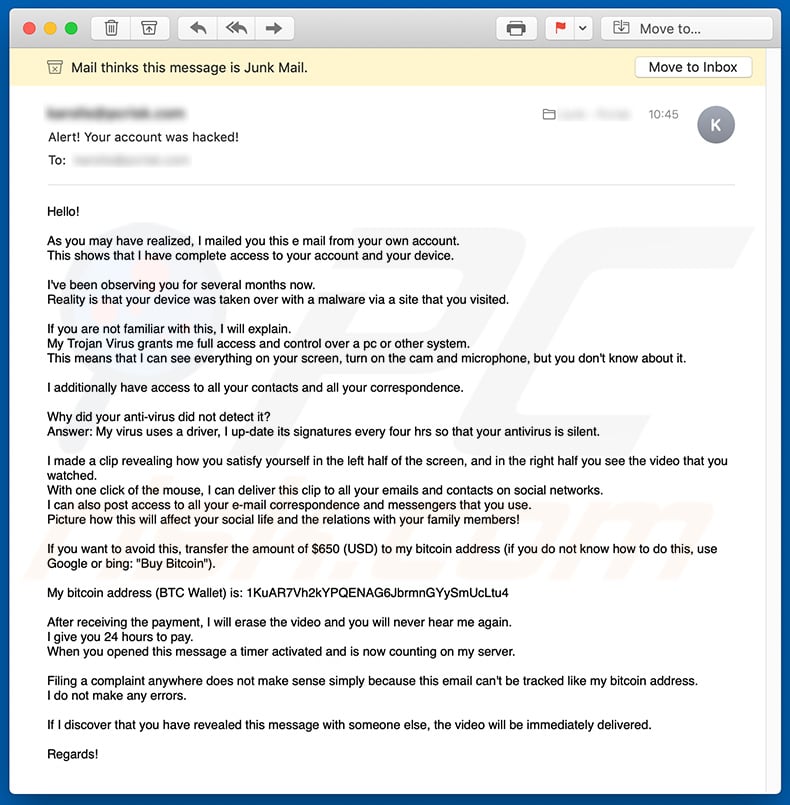
Text presented within this letter:
Subject: Alert! Your account was hacked!
Hello!
As you may have realized, I mailed you this e mail from your own account.
This shows that I have complete access to your account and your device.I've been observing you for several months now.
Reality is that your device was taken over with a malware via a site that you visited.If you are not familiar with this, I will explain.
My Trojan Virus grants me full access and control over a pc or other system.
This means that I can see everything on your screen, turn on the cam and microphone, but you don't know about it.I additionally have access to all your contacts and all your correspondence.
Why did your anti-virus did not detect it?
Answer: My virus uses a driver, I up-date its signatures every four hrs so that your antivirus is silent.I made a clip revealing how you satisfy yourself in the left half of the screen, and in the right half you see the video that you watched.
With one click of the mouse, I can deliver this clip to all your emails and contacts on social networks.
I can also post access to all your e-mail correspondence and messengers that you use.
Picture how this will affect your social life and the relations with your family members!If you want to avoid this, transfer the amount of $650 (USD) to my bitcoin address (if you do not know how to do this, use Google or bing: "Buy Bitcoin").
My bitcoin address (BTC Wallet) is: 1KuAR7Vh2kYPQENAG6JbrmnGYySmUcLtu4, 1K7nnDHosR5czKZtuKT928YSxXXNSaDK6H, 1C2EbKJCZKtHMJawxBqyzZ9SHQVwRyfist, 1C1ehibCgeuLwF4VbSAzoDapDLbKtjivbP, 18yTDtmrUeRAdjC2gNscnbV6Dfn6UUsaMk, 14bscQz6FSjUyUgEv5NxjeKUFtY3yR1cCu, 16htiAFUVMXCsUMfvpPJFUuGRyvtxw1To9, 1HouKKY29benTnpiP2vVdLcKamN4NJrksk, 1NiXnj8DcDTnawYqz57GeVRMxw6WDTy3ba, 15bbfkGkNMjz857G5ya4RNRo5dWb1dRsxR
After receiving the payment, I will erase the video and you will never hear me again.
I give you 24 hours to pay.
When you opened this message a timer activated and is now counting on my server.Filing a complaint anywhere does not make sense simply because this email can't be tracked like my bitcoin address.
I do not make any errors.If I discover that you have revealed this message with someone else, the video will be immediately delivered.
Regards!
A new variant of this email scam - trying to evade email spam filters by separating Bitcoin address into two separate lines:
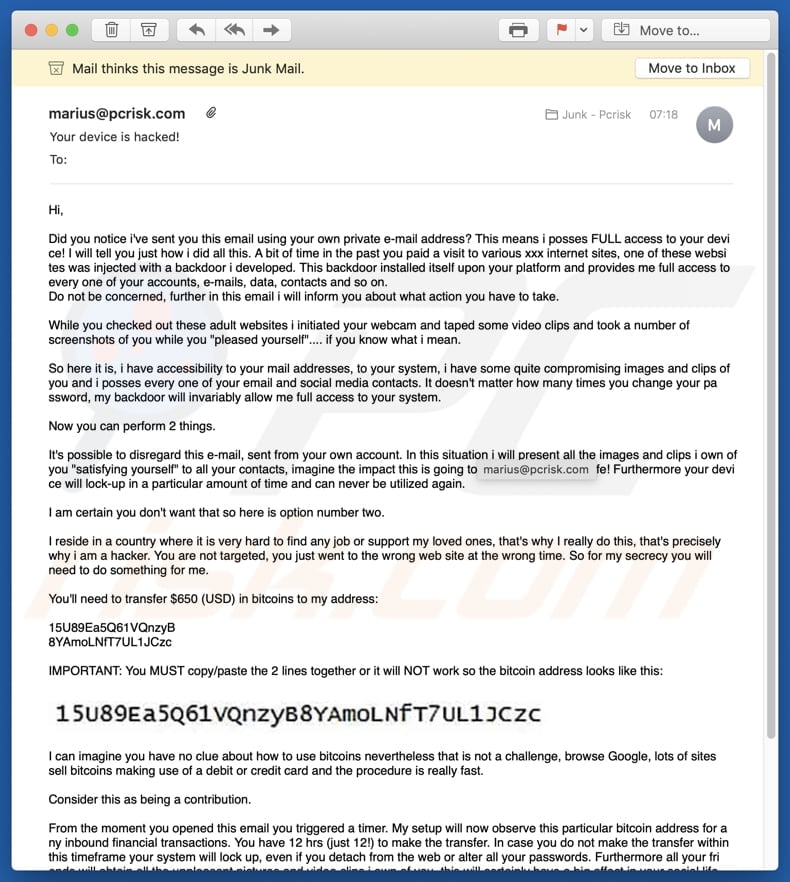
Text presented in this variant:
Subject: Your device is hacked!
Hi,
Did you notice i've sent you this email using your own private e-mail address? This means i posses FULL access to your device! I will tell you just how i did all this. A bit of time in the past you paid a visit to various xxx internet sites, one of these websites was injected with a backdoor i developed. This backdoor installed itself upon your platform and provides me full access to every one of your accounts, e-mails, data, contacts and so on.
Do not be concerned, further in this email i will inform you about what action you have to take.While you checked out these adult websites i initiated your webcam and taped some video clips and took a number of screenshots of you while you "pleased yourself".... if you know what i mean.
So here it is, i have accessibility to your mail addresses, to your system, i have some quite compromising images and clips of you and i posses every one of your email and social media contacts. It doesn't matter how many times you change your password, my backdoor will invariably allow me full access to your system.
Now you can perform 2 things.
It's possible to disregard this e-mail, sent from your own account. In this situation i will present all the images and clips i own of you "satisfying yourself" to all your contacts, imagine the impact this is going to have on your social life! Furthermore your device will lock-up in a particular amount of time and can never be utilized again.
I am certain you don't want that so here is option number two.
I reside in a country where it is very hard to find any job or support my loved ones, that's why I really do this, that's precisely why i am a hacker. You are not targeted, you just went to the wrong web site at the wrong time. So for my secrecy you will need to do something for me.
You'll need to transfer $650 (USD) in bitcoins to my address:
15U89Ea5Q61VQnzyB
8YAmoLNfT7UL1JCzcIMPORTANT: You MUST copy/paste the 2 lines together or it will NOT work so the bitcoin address looks like this:
15U89Ea5Q61VQnzyB8YAmoLNfT7UL1JCzc, 1LRuigr82sxPmQt5XDQ7PprJu9qX1rJFMN, 13nsNBfoVwXDHY4puRD1AHjARbomKhsxEL, 1FCFYKzJHbKDcAL2wX8hpZdUdGJcfkWfxd, 1F3mAYuD3sEjufi5pPgDjAAM6SJPN6bFvn, 1NKrw3sP7C9igNozkB2Pd4VnZuk8d6WGV
I can imagine you have no clue about how to use bitcoins nevertheless that is not a challenge, browse Google, lots of sites sell bitcoins making use of a debit or credit card and the procedure is really fast.
Consider this as being a contribution.
From the moment you opened this email you triggered a timer. My setup will now observe this particular bitcoin address for any inbound financial transactions. You have 12 hrs (just 12!) to make the transfer. In case you do not make the transfer within this timeframe your system will lock up, even if you detach from the web or alter all your passwords. Furthermore all your friends will obtain all the unpleasant pictures and video clips i own of you, this will certainly have a big affect in your social life.
If the transaction does come in before its due my setup will automatically shut down the backdoor on your platform and delete all the information, pictures and videos i have of you and you will never ever hear from me again then you can go on to live your life as if this never happened.I do not want to do damage nevertheless i will do no matter what it takes to feed my spouse and children.
Since you have only 12 hrs you better start the transaction right now!
All the best!
Cyber criminals have translated this email scam and are now targeting computer users in various countries, here's an example of this scam email targeting Chinese users:
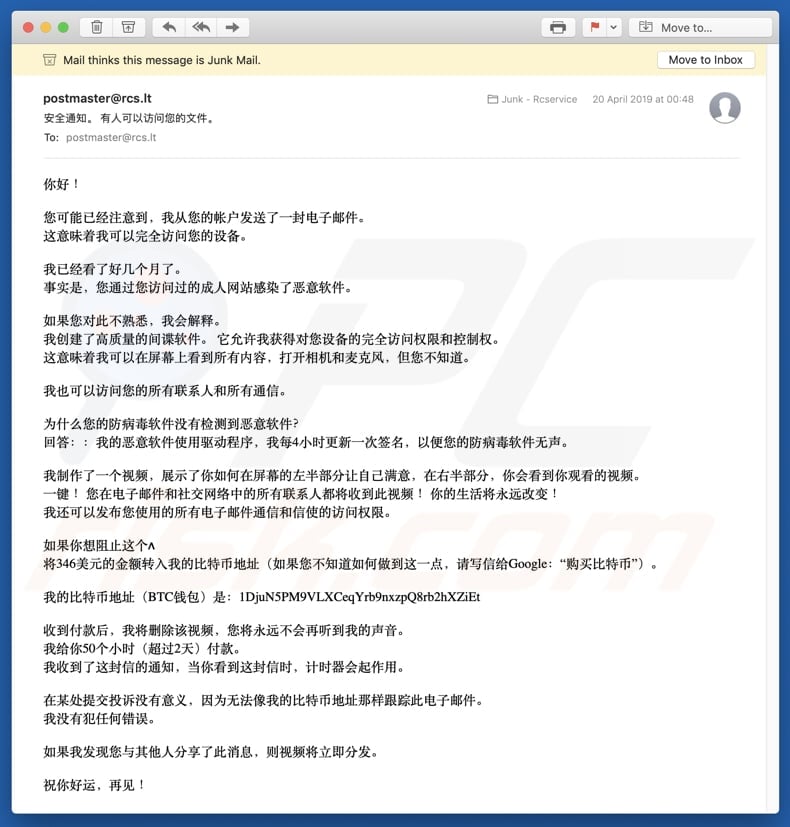
Chinese text presented in this email scam:
Subject: 安全通知。 有人可以访问您的文件。
你好!
您可能已经注意到,我从您的帐户发送了一封电子邮件。
这意味着我可以完全访问您的设备。我已经看了好几个月了。
事实是,您通过您访问过的成人网站感染了恶意软件。如果您对此不熟悉,我会解释。
我创建了高质量的间谍软件。 它允许我获得对您设备的完全访问权限和控制权。
这意味着我可以在屏幕上看到所有内容,打开相机和麦克风,但您不知道。我也可以访问您的所有联系人和所有通信。
为什么您的防病毒软件没有检测到恶意软件?
回答::我的恶意软件使用驱动程序,我每4小时更新一次签名,以便您的防病毒软件无声。我制作了一个视频,展示了你如何在屏幕的左半部分让自己满意,在右半部分,你会看到你观看的视频。
一键! 您在电子邮件和社交网络中的所有联系人都将收到此视频! 你的生活将永远改变!
我还可以发布您使用的所有电子邮件通信和信使的访问权限。如果你想阻止这个ʌ
将346美元的金额转入我的比特币地址(如果您不知道如何做到这一点,请写信给Google:“购买比特币”)。我的比特币地址(BTC钱包)是:1DjuN5PM9VLXCeqYrb9nxzpQ8rb2hXZiEt
收到付款后,我将删除该视频,您将永远不会再听到我的声音。
我给你50个小时(超过2天)付款。
我收到了这封信的通知,当你看到这封信时,计时器会起作用。在某处提交投诉没有意义,因为无法像我的比特币地址那样跟踪此电子邮件。
我没有犯任何错误。如果我发现您与其他人分享了此消息,则视频将立即分发。
祝你好运,再见!
Screenshot of "" spam email targeting Russian users:
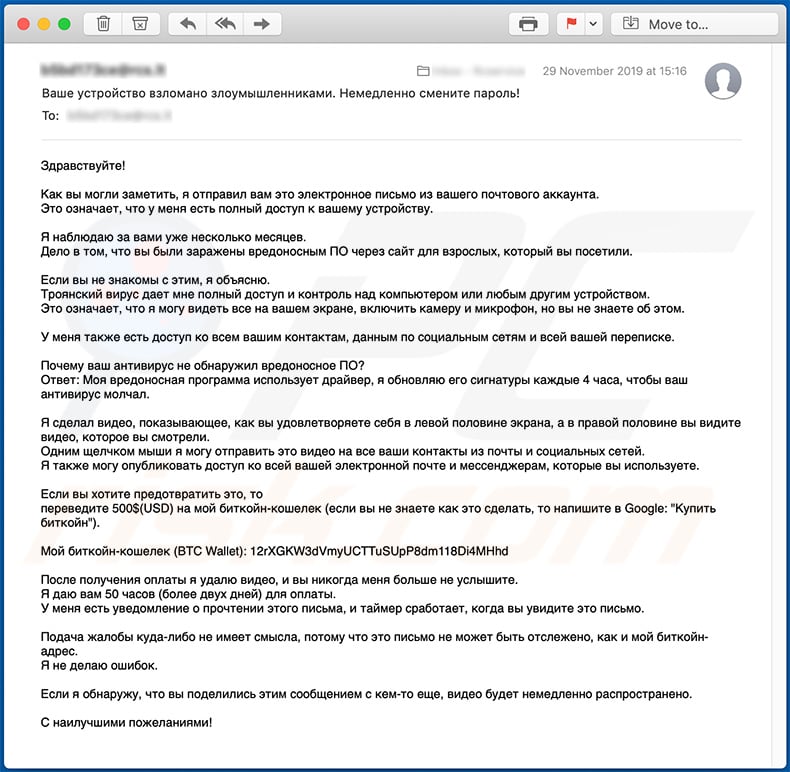
Text presented within this email:
Subject: Ваше устройство взломано злоумышленниками. Немедленно смените пароль!
Здравствуйте!Как вы могли заметить, я отправил вам это электронное письмо из вашего почтового аккаунта.
Это означает, что у меня есть полный доступ к вашему устройству.Я наблюдаю за вами уже несколько месяцев.
Дело в том, что вы были заражены вредоносным ПО через сайт для взрослых, который вы посетили.Если вы не знакомы с этим, я объясню.
Троянский вирус дает мне полный доступ и контроль над компьютером или любым другим устройством.
Это означает, что я могу видеть все на вашем экране, включить камеру и микрофон, но вы не знаете об этом.У меня также есть доступ ко всем вашим контактам, данным по социальным сетям и всей вашей переписке.
Почему ваш антивирус не обнаружил вредоносное ПО?
Ответ: Моя вредоносная программа использует драйвер, я обновляю его сигнатуры каждые 4 часа, чтобы ваш антивирус молчал.Я сделал видео, показывающее, как вы удовлетворяете себя в левой половине экрана, а в правой половине вы видите видео, которое вы смотрели.
Одним щелчком мыши я могу отправить это видео на все ваши контакты из почты и социальных сетей.
Я также могу опубликовать доступ ко всей вашей электронной почте и мессенджерам, которые вы используете.Если вы хотите предотвратить это, то
переведите 500$(USD) на мой биткойн-кошелек (если вы не знаете как это сделать, то напишите в Google: "Купить биткойн").Мой биткойн-кошелек (BTC Wallet): 12rXGKW3dVmyUCTTuSUpP8dm118Di4MHhd, 1k8fn2VMauUeHKuPuF5jqcVbVUw58Dc1H, 1EuACsW2dRECausKxA96yPGLNbWDFHL5Kz, 1EvxiAhfaK9K7uzNYtgjpWhKYpwMevH94C, 162DnzzVEYbJYaFKnTB9N2oaqFdL9Cq4oV, 1DZeuHWbitizaUAHYTqpiRbVz2g4xeQaq2
После получения оплаты я удалю видео, и вы никогда меня больше не услышите.
Я даю вам 50 часов (более двух дней) для оплаты.
У меня есть уведомление о прочтении этого письма, и таймер сработает, когда вы увидите это письмо.Подача жалобы куда-либо не имеет смысла, потому что это письмо не может быть отслежено, как и мой биткойн-адрес.
Я не делаю ошибок.Если я обнаружу, что вы поделились этим сообщением с кем-то еще, видео будет немедленно распространено.
С наилучшими пожеланиями!
Another example of "I Sent You An Email From Your Account" scam email:
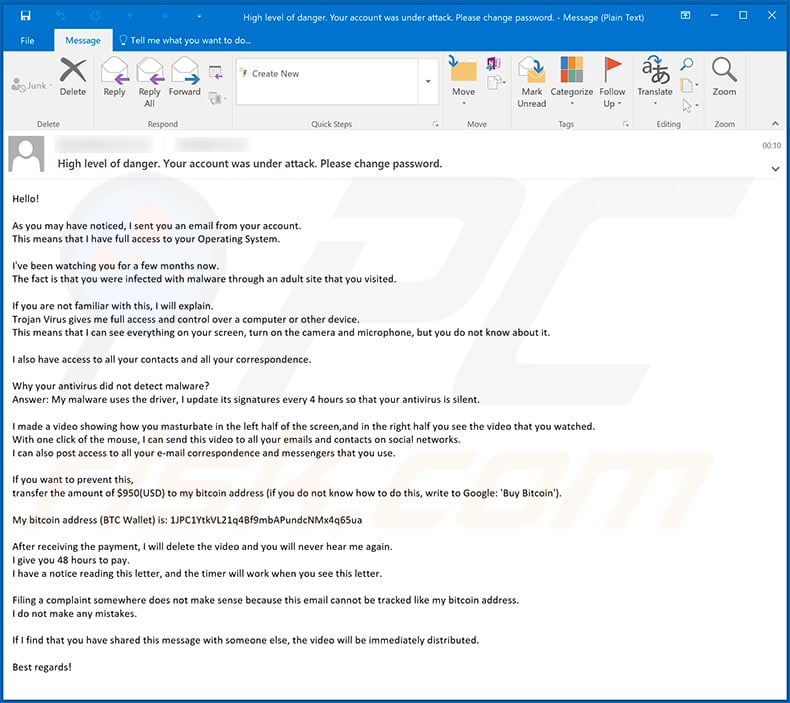
Text presented within this mail:
Subject: High level of danger. Your account was under attack. Please change password.
Hello!
As you may have noticed, I sent you an email from your account.
This means that I have full access to your Operating System.I've been watching you for a few months now.
The fact is that you were infected with malware through an adult site that you visited.If you are not familiar with this, I will explain.
Trojan Virus gives me full access and control over a computer or other device.
This means that I can see everything on your screen, turn on the camera and microphone, but you do not know about it.I also have access to all your contacts and all your correspondence.
Why your antivirus did not detect malware?
Answer: My malware uses the driver, I update its signatures every 4 hours so that your antivirus is silent.I made a video showing how you masturbate in the left half of the screen,and in the right half you see the video that you watched.
With one click of the mouse, I can send this video to all your emails and contacts on social networks.
I can also post access to all your e-mail correspondence and messengers that you use.If you want to prevent this,
transfer the amount of $950(USD) to my bitcoin address (if you do not know how to do this, write to Google: 'Buy Bitcoin').My bitcoin address (BTC Wallet) is: 1JPC1YtkVL21q4Bf9mbAPundcNMx4q65ua
After receiving the payment, I will delete the video and you will never hear me again.
I give you 48 hours to pay.
I have a notice reading this letter, and the timer will work when you see this letter.Filing a complaint somewhere does not make sense because this email cannot be tracked like my bitcoin address.
I do not make any mistakes.If I find that you have shared this message with someone else, the video will be immediately distributed.
Best regards!
An example of "I Sent You An Email From Your Account" spam email written in Czech language:
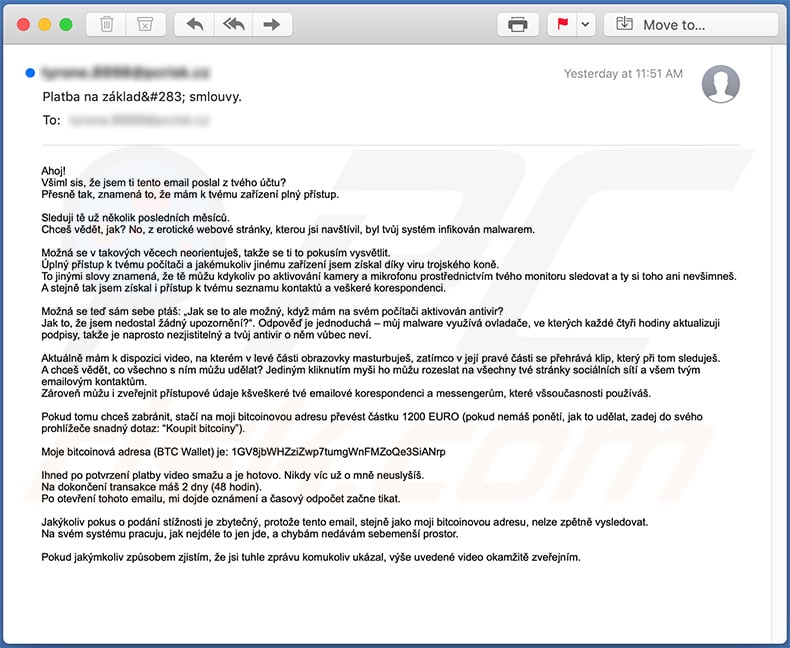
Text presented within:
Ahoj!
Všiml sis, že jsem ti tento email poslal z tvého účtu?
Přesně tak, znamená to, že mám k tvému zařízení plný přístup.Sleduji tě už několik posledních měsíců.
Chceš vědět, jak? No, z erotické webové stránky, kterou jsi navštívil, byl tvůj systém infikován malwarem.Možná se v takových věcech neorientuješ, takže se ti to pokusím vysvětlit.
Úplný přístup k tvému počítači a jakémukoliv jinému zařízení jsem získal díky viru trojského koně.
To jinými slovy znamená, že tě můžu kdykoliv po aktivování kamery a mikrofonu prostřednictvím tvého monitoru sledovat a ty si toho ani nevšimneš.
A stejně tak jsem získal i přístup k tvému seznamu kontaktů a veškeré korespondenci.Možná se teď sám sebe ptáš: „Jak se to ale možný, když mám na svém počítači aktivován antivir?
Jak to, že jsem nedostal žádný upozornění?“. Odpověď je jednoduchá – můj malware využívá ovladače, ve kterých každé čtyři hodiny aktualizuji podpisy, takže je naprosto nezjistitelný a tvůj antivir o něm vůbec neví.Aktuálně mám k dispozici video, na kterém v levé části obrazovky masturbuješ, zatímco v její pravé části se přehrává klip, který při tom sleduješ.
A chceš vědět, co všechno s ním můžu udělat? Jediným kliknutím myši ho můžu rozeslat na všechny tvé stránky sociálních sítí a všem tvým emailovým kontaktům.
Zároveň můžu i zveřejnit přístupové údaje kšveškeré tvé emailové korespondenci a messengerům, které všsoučasnosti používáš.Pokud tomu chceš zabránit, stačí na moji bitcoinovou adresu převést částku 1200 EURO (pokud nemáš ponětí, jak to udělat, zadej do svého prohlížeče snadný dotaz: “Koupit bitcoiny”).
Moje bitcoinová adresa (BTC Wallet) je: 1GV8jbWHZziZwp7tumgWnFMZoQe3SiANrp, 1Jf7EsLoD7kiTqohD6pbeWoRKsuvHG9KWW, 1DdWha3etffaYYnckHsQaySM6sJMWD6tDZ
Ihned po potvrzení platby video smažu a je hotovo. Nikdy víc už o mně neuslyšíš.
Na dokončení transakce máš 2 dny (48 hodin).
Po otevření tohoto emailu, mi dojde oznámení a časový odpočet začne tikat.Jakýkoliv pokus o podání stížnosti je zbytečný, protože tento email, stejně jako moji bitcoinovou adresu, nelze zpětně vysledovat.
Na svém systému pracuju, jak nejdéle to jen jde, a chybám nedávám sebemenší prostor.Pokud jakýmkoliv způsobem zjistím, že jsi tuhle zprávu komukoliv ukázal, výše uvedené video okamžitě zveřejním.
An Italian variant of "I Sent You An Email From Your Account" scam email:
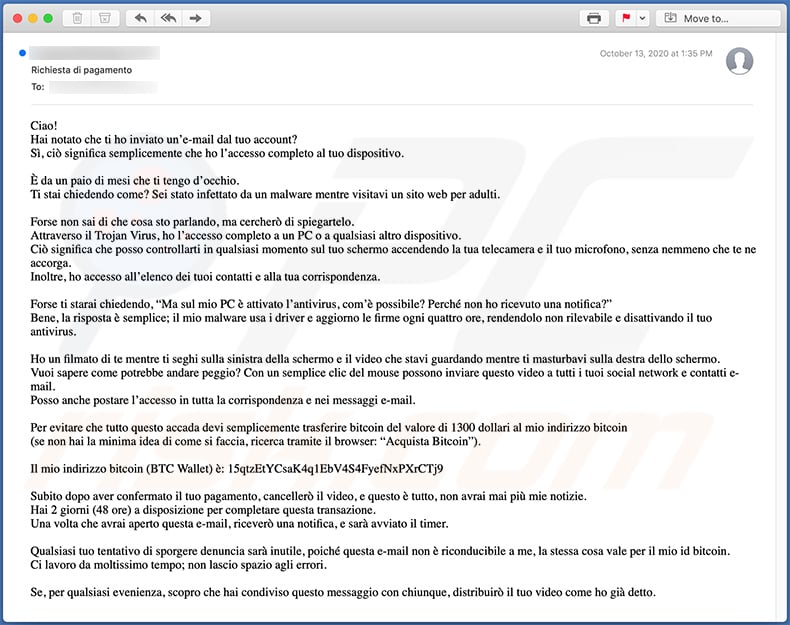
Text presented within:
Subject: Richiesta di pagamento
Ciao!
Hai notato che ti ho inviato un’e-mail dal tuo account?
Sì, ciò significa semplicemente che ho l’accesso completo al tuo dispositivo.È da un paio di mesi che ti tengo d’occhio.
Ti stai chiedendo come? Sei stato infettato da un malware mentre visitavi un sito web per adulti.Forse non sai di che cosa sto parlando, ma cercherò di spiegartelo.
Attraverso il Trojan Virus, ho l’accesso completo a un PC o a qualsiasi altro dispositivo.
Ciò significa che posso controllarti in qualsiasi momento sul tuo schermo accendendo la tua telecamera e il tuo microfono, senza nemmeno che te ne accorga.
Inoltre, ho accesso all’elenco dei tuoi contatti e alla tua corrispondenza.Forse ti starai chiedendo, “Ma sul mio PC è attivato l’antivirus, com’è possibile? Perché non ho ricevuto una notifica?”
Bene, la risposta è semplice; il mio malware usa i driver e aggiorno le firme ogni quattro ore, rendendolo non rilevabile e disattivando il tuo antivirus.Ho un filmato di te mentre ti seghi sulla sinistra della schermo e il video che stavi guardando mentre ti masturbavi sulla destra dello schermo.
Vuoi sapere come potrebbe andare peggio? Con un semplice clic del mouse possono inviare questo video a tutti i tuoi social network e contatti e-mail.
Posso anche postare l’accesso in tutta la corrispondenza e nei messaggi e-mail.Per evitare che tutto questo accada devi semplicemente trasferire bitcoin del valore di 1300 dollari al mio indirizzo bitcoin
(se non hai la minima idea di come si faccia, ricerca tramite il browser: “Acquista Bitcoin”).Il mio indirizzo bitcoin (BTC Wallet) è: 15qtzEtYCsaK4q1EbV4S4FyefNxPXrCTj9, 1JtmEMgtPgv4QG5y3B1BviMktbijX799Cb
Subito dopo aver confermato il tuo pagamento, cancellerò il video, e questo è tutto, non avrai mai più mie notizie.
Hai 2 giorni (48 ore) a disposizione per completare questa transazione.
Una volta che avrai aperto questa e-mail, riceverò una notifica, e sarà avviato il timer.Qualsiasi tuo tentativo di sporgere denuncia sarà inutile, poiché questa e-mail non è riconducibile a me, la stessa cosa vale per il mio id bitcoin.
Ci lavoro da moltissimo tempo; non lascio spazio agli errori.Se, per qualsiasi evenienza, scopro che hai condiviso questo messaggio con chiunque, distribuirò il tuo video come ho già detto.
Yet another Spanish variant of "I Sent You An Email From Your Account" scam email:
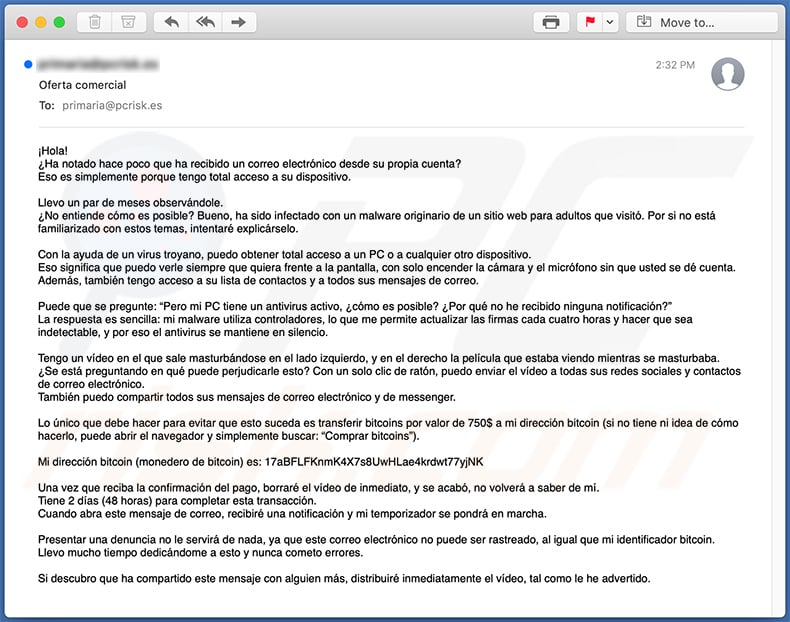
Text presented within:
Subject: Oferta comercial
¡Hola!
¿Ha notado hace poco que ha recibido un correo electrónico desde su propia cuenta?
Eso es simplemente porque tengo total acceso a su dispositivo.Llevo un par de meses observándole.
¿No entiende cómo es posible? Bueno, ha sido infectado con un malware originario de un sitio web para adultos que visitó. Por si no está familiarizado con estos temas, intentaré explicárselo.Con la ayuda de un virus troyano, puedo obtener total acceso a un PC o a cualquier otro dispositivo.
Eso significa que puedo verle siempre que quiera frente a la pantalla, con solo encender la cámara y el micrófono sin que usted se dé cuenta.
Además, también tengo acceso a su lista de contactos y a todos sus mensajes de correo.Puede que se pregunte: “Pero mi PC tiene un antivirus activo, ¿cómo es posible? ¿Por qué no he recibido ninguna notificación?”
La respuesta es sencilla: mi malware utiliza controladores, lo que me permite actualizar las firmas cada cuatro horas y hacer que sea indetectable, y por eso el antivirus se mantiene en silencio.Tengo un vídeo en el que sale masturbándose en el lado izquierdo, y en el derecho la película que estaba viendo mientras se masturbaba.
¿Se está preguntando en qué puede perjudicarle esto? Con un solo clic de ratón, puedo enviar el vídeo a todas sus redes sociales y contactos de correo electrónico.
También puedo compartir todos sus mensajes de correo electrónico y de messenger.Lo único que debe hacer para evitar que esto suceda es transferir bitcoins por valor de 750$ a mi dirección bitcoin (si no tiene ni idea de cómo hacerlo, puede abrir el navegador y simplemente buscar: “Comprar bitcoins”).
Mi dirección bitcoin (monedero de bitcoin) es: 17aBFLFKnmK4X7s8UwHLae4krdwt77yjNK
Una vez que reciba la confirmación del pago, borraré el vídeo de inmediato, y se acabó, no volverá a saber de mí.
Tiene 2 días (48 horas) para completar esta transacción.
Cuando abra este mensaje de correo, recibiré una notificación y mi temporizador se pondrá en marcha.Presentar una denuncia no le servirá de nada, ya que este correo electrónico no puede ser rastreado, al igual que mi identificador bitcoin.
Llevo mucho tiempo dedicándome a esto y nunca cometo errores.Si descubro que ha compartido este mensaje con alguien más, distribuiré inmediatamente el vídeo, tal como le he advertido.
A Portuguese variant of "I Sent You An Email From Your Account" scam email:
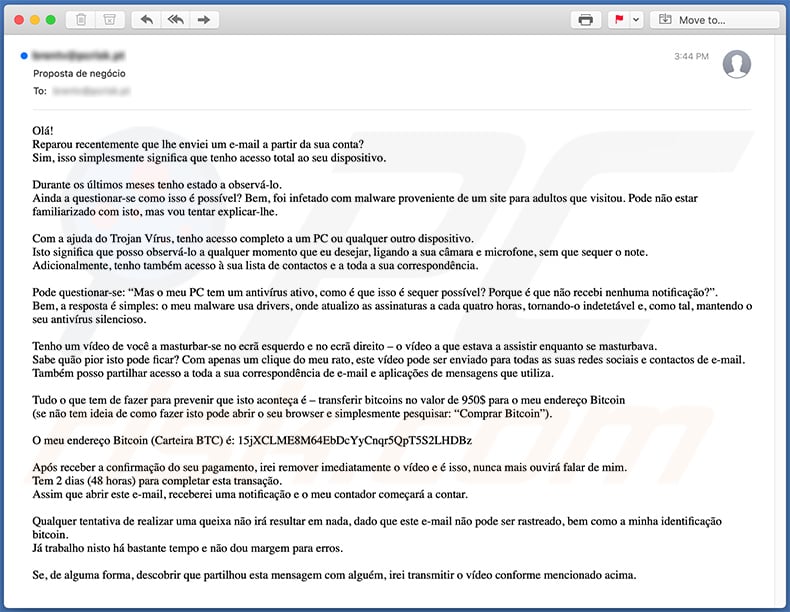
Text presented within:
Subject: Proposta de negócio
Olá!
Reparou recentemente que lhe enviei um e-mail a partir da sua conta?
Sim, isso simplesmente significa que tenho acesso total ao seu dispositivo.Durante os últimos meses tenho estado a observá-lo.
Ainda a questionar-se como isso é possível? Bem, foi infetado com malware proveniente de um site para adultos que visitou. Pode não estar familiarizado com isto, mas vou tentar explicar-lhe.Com a ajuda do Trojan Vírus, tenho acesso completo a um PC ou qualquer outro dispositivo.
Isto significa que posso observá-lo a qualquer momento que eu desejar, ligando a sua câmara e microfone, sem que sequer o note.
Adicionalmente, tenho também acesso à sua lista de contactos e a toda a sua correspondência.Pode questionar-se: “Mas o meu PC tem um antivírus ativo, como é que isso é sequer possível? Porque é que não recebi nenhuma notificação?”.
Bem, a resposta é simples: o meu malware usa drivers, onde atualizo as assinaturas a cada quatro horas, tornando-o indetetável e, como tal, mantendo o seu antivírus silencioso.Tenho um vídeo de você a masturbar-se no ecrã esquerdo e no ecrã direito – o vídeo a que estava a assistir enquanto se masturbava.
Sabe quão pior isto pode ficar? Com apenas um clique do meu rato, este vídeo pode ser enviado para todas as suas redes sociais e contactos de e-mail.
Também posso partilhar acesso a toda a sua correspondência de e-mail e aplicações de mensagens que utiliza.Tudo o que tem de fazer para prevenir que isto aconteça é – transferir bitcoins no valor de 950$ para o meu endereço Bitcoin
(se não tem ideia de como fazer isto pode abrir o seu browser e simplesmente pesquisar: “Comprar Bitcoin”).O meu endereço Bitcoin (Carteira BTC) é: 15jXCLME8M64EbDcYyCnqr5QpT5S2LHDBz, 1GLWLdAczAxYex1WphmhF27qdDgtvLK7yz
Após receber a confirmação do seu pagamento, irei remover imediatamente o vídeo e é isso, nunca mais ouvirá falar de mim.
Tem 2 dias (48 horas) para completar esta transação.
Assim que abrir este e-mail, receberei uma notificação e o meu contador começará a contar.Qualquer tentativa de realizar uma queixa não irá resultar em nada, dado que este e-mail não pode ser rastreado, bem como a minha identificação bitcoin.
Já trabalho nisto há bastante tempo e não dou margem para erros.Se, de alguma forma, descobrir que partilhou esta mensagem com alguém, irei transmitir o vídeo conforme mencionado acima.
Yet another Czech variant of "I Sent You An Email From Your Account" spam email:
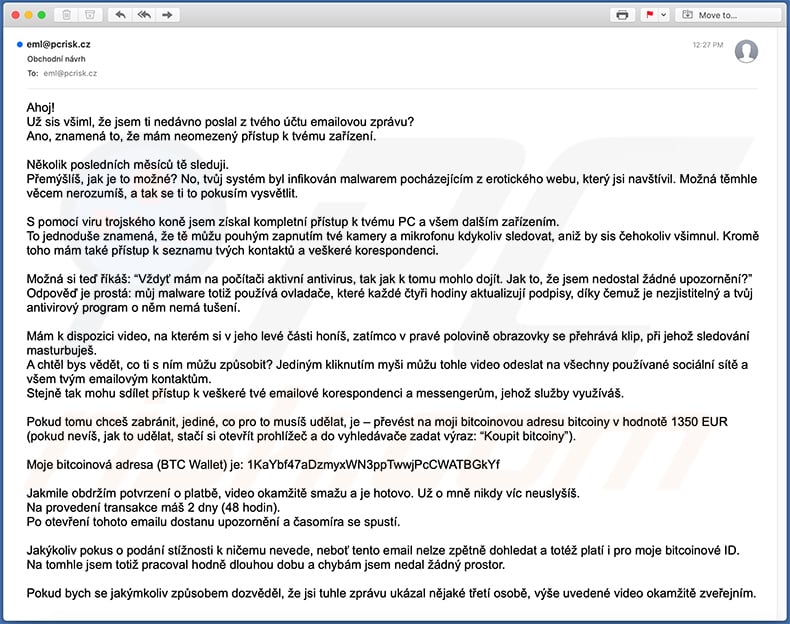
Text presented within:
Subject: Obchodní návrh
Ahoj!
Už sis všiml, že jsem ti nedávno poslal z tvého účtu emailovou zprávu?
Ano, znamená to, že mám neomezený přístup k tvému zařízení.Několik posledních měsíců tě sleduji.
Přemýšlíš, jak je to možné? No, tvůj systém byl infikován malwarem pocházejícím z erotického webu, který jsi navštívil. Možná těmhle věcem nerozumíš, a tak se ti to pokusím vysvětlit.S pomocí viru trojského koně jsem získal kompletní přístup k tvému PC a všem dalším zařízením.
To jednoduše znamená, že tě můžu pouhým zapnutím tvé kamery a mikrofonu kdykoliv sledovat, aniž by sis čehokoliv všimnul. Kromě toho mám také přístup k seznamu tvých kontaktů a veškeré korespondenci.Možná si teď říkáš: “Vždyť mám na počítači aktivní antivirus, tak jak k tomu mohlo dojít. Jak to, že jsem nedostal žádné upozornění?”
Odpověď je prostá: můj malware totiž používá ovladače, které každé čtyři hodiny aktualizují podpisy, díky čemuž je nezjistitelný a tvůj antivirový program o něm nemá tušení.Mám k dispozici video, na kterém si v jeho levé části honíš, zatímco v pravé polovině obrazovky se přehrává klip, při jehož sledování masturbuješ.
A chtěl bys vědět, co ti s ním můžu způsobit? Jediným kliknutím myši můžu tohle video odeslat na všechny používané sociální sítě a všem tvým emailovým kontaktům.
Stejně tak mohu sdílet přístup k veškeré tvé emailové korespondenci a messengerům, jehož služby využíváš.Pokud tomu chceš zabránit, jediné, co pro to musíš udělat, je – převést na moji bitcoinovou adresu bitcoiny v hodnotě 1350 EUR
(pokud nevíš, jak to udělat, stačí si otevřít prohlížeč a do vyhledávače zadat výraz: “Koupit bitcoiny”).Moje bitcoinová adresa (BTC Wallet) je: 1KaYbf47aDzmyxWN3ppTwwjPcCWATBGkYf, 1Lsx7zGBeJSZCAv7zRu128Ho8K6uRKHVnt, 15kbS9SY8Q6VVbktUTTb4pPCFU2sC24QYu
Jakmile obdržím potvrzení o platbě, video okamžitě smažu a je hotovo. Už o mně nikdy víc neuslyšíš.
Na provedení transakce máš 2 dny (48 hodin).
Po otevření tohoto emailu dostanu upozornění a časomíra se spustí.Jakýkoliv pokus o podání stížnosti k ničemu nevede, neboť tento email nelze zpětně dohledat a totéž platí i pro moje bitcoinové ID.
Na tomhle jsem totiž pracoval hodně dlouhou dobu a chybám jsem nedal žádný prostor.Pokud bych se jakýmkoliv způsobem dozvěděl, že jsi tuhle zprávu ukázal nějaké třetí osobě, výše uvedené video okamžitě zveřejním.
Another Italian variant of "I Sent You An Email From Your Account" spam email:
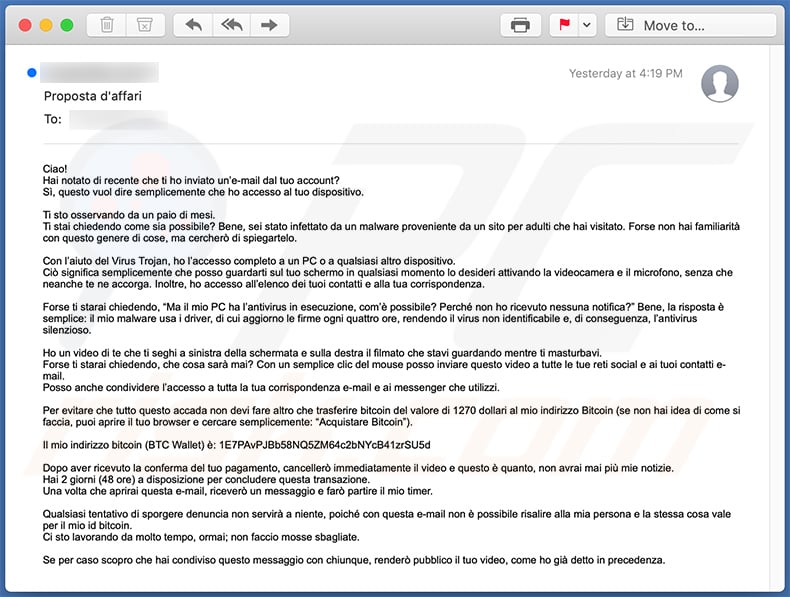
Text presented within:
Subject: Proposta d'affari
Ciao!
Hai notato di recente che ti ho inviato un’e-mail dal tuo account?
Sì, questo vuol dire semplicemente che ho accesso al tuo dispositivo.Ti sto osservando da un paio di mesi.
Ti stai chiedendo come sia possibile? Bene, sei stato infettato da un malware proveniente da un sito per adulti che hai visitato. Forse non hai familiarità con questo genere di cose, ma cercherò di spiegartelo.Con l’aiuto del Virus Trojan, ho l’accesso completo a un PC o a qualsiasi altro dispositivo.
Ciò significa semplicemente che posso guardarti sul tuo schermo in qualsiasi momento lo desideri attivando la videocamera e il microfono, senza che neanche te ne accorga. Inoltre, ho accesso all’elenco dei tuoi contatti e alla tua corrispondenza.Forse ti starai chiedendo, “Ma il mio PC ha l’antivirus in esecuzione, com’è possibile? Perché non ho ricevuto nessuna notifica?” Bene, la risposta è semplice: il mio malware usa i driver, di cui aggiorno le firme ogni quattro ore, rendendo il virus non identificabile e, di conseguenza, l’antivirus silenzioso.
Ho un video di te che ti seghi a sinistra della schermata e sulla destra il filmato che stavi guardando mentre ti masturbavi.
Forse ti starai chiedendo, che cosa sarà mai? Con un semplice clic del mouse posso inviare questo video a tutte le tue reti social e ai tuoi contatti e-mail.
Posso anche condividere l’accesso a tutta la tua corrispondenza e-mail e ai messenger che utilizzi.Per evitare che tutto questo accada non devi fare altro che trasferire bitcoin del valore di 1270 dollari al mio indirizzo Bitcoin (se non hai idea di come si faccia, puoi aprire il tuo browser e cercare semplicemente: “Acquistare Bitcoin”).
Il mio indirizzo bitcoin (BTC Wallet) è: 1E7PAvPJBb58NQ5ZM64c2bNYcB41zrSU5d
Dopo aver ricevuto la conferma del tuo pagamento, cancellerò immediatamente il video e questo è quanto, non avrai mai più mie notizie.
Hai 2 giorni (48 ore) a disposizione per concludere questa transazione.
Una volta che aprirai questa e-mail, riceverò un messaggio e farò partire il mio timer.Qualsiasi tentativo di sporgere denuncia non servirà a niente, poiché con questa e-mail non è possibile risalire alla mia persona e la stessa cosa vale per il mio id bitcoin.
Ci sto lavorando da molto tempo, ormai; non faccio mosse sbagliate.Se per caso scopro che hai condiviso questo messaggio con chiunque, renderò pubblico il tuo video, come ho già detto in precedenza.
A Polish variant of "I Sent You An Email From Your Account" spam email:
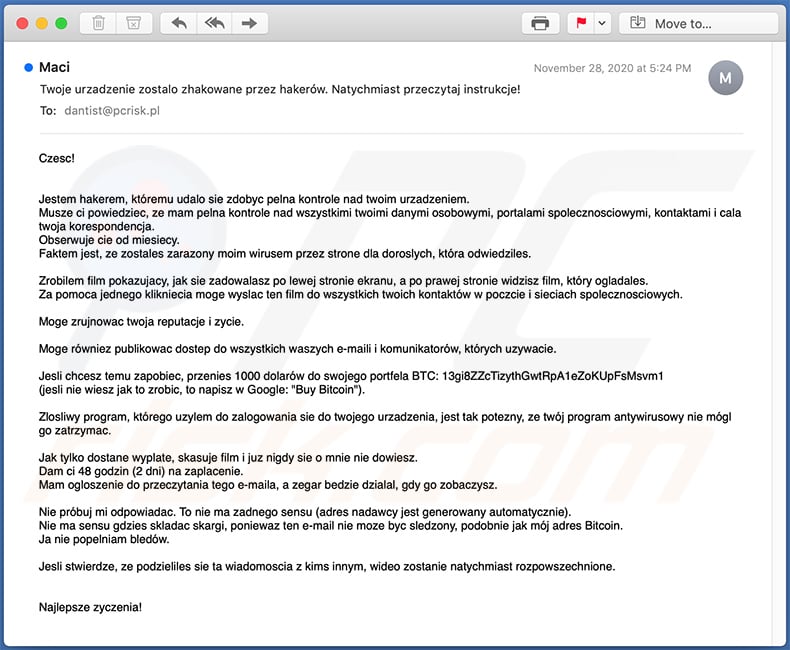
Text presented within:
Subject: Twoje urzadzenie zostalo zhakowane przez hakerów. Natychmiast przeczytaj instrukcje!
Czesc!
Jestem hakerem, któremu udalo sie zdobyc pelna kontrole nad twoim urzadzeniem.
Musze ci powiedziec, ze mam pelna kontrole nad wszystkimi twoimi danymi osobowymi, portalami spolecznosciowymi, kontaktami i cala twoja korespondencja.
Obserwuje cie od miesiecy.
Faktem jest, ze zostales zarazony moim wirusem przez strone dla doroslych, która odwiedziles.Zrobilem film pokazujacy, jak sie zadowalasz po lewej stronie ekranu, a po prawej stronie widzisz film, który ogladales.
Za pomoca jednego klikniecia moge wyslac ten film do wszystkich twoich kontaktów w poczcie i sieciach spolecznosciowych.Moge zrujnowac twoja reputacje i zycie.
Moge równiez publikowac dostep do wszystkich waszych e-maili i komunikatorów, których uzywacie.
Jesli chcesz temu zapobiec, przenies 1000 dolarów do swojego portfela BTC: 13gi8ZZcTizythGwtRpA1eZoKUpFsMsvm1
(jesli nie wiesz jak to zrobic, to napisz w Google: "Buy Bitcoin").Zlosliwy program, którego uzylem do zalogowania sie do twojego urzadzenia, jest tak potezny, ze twój program antywirusowy nie mógl go zatrzymac.
Jak tylko dostane wyplate, skasuje film i juz nigdy sie o mnie nie dowiesz.
Dam ci 48 godzin (2 dni) na zaplacenie.
Mam ogloszenie do przeczytania tego e-maila, a zegar bedzie dzialal, gdy go zobaczysz.Nie próbuj mi odpowiadac. To nie ma zadnego sensu (adres nadawcy jest generowany automatycznie).
Nie ma sensu gdzies skladac skargi, poniewaz ten e-mail nie moze byc sledzony, podobnie jak mój adres Bitcoin.
Ja nie popelniam bledów.Jesli stwierdze, ze podzieliles sie ta wiadomoscia z kims innym, wideo zostanie natychmiast rozpowszechnione.
Najlepsze zyczenia!
A German variant of "I Sent You An Email From Your Account" scam email:
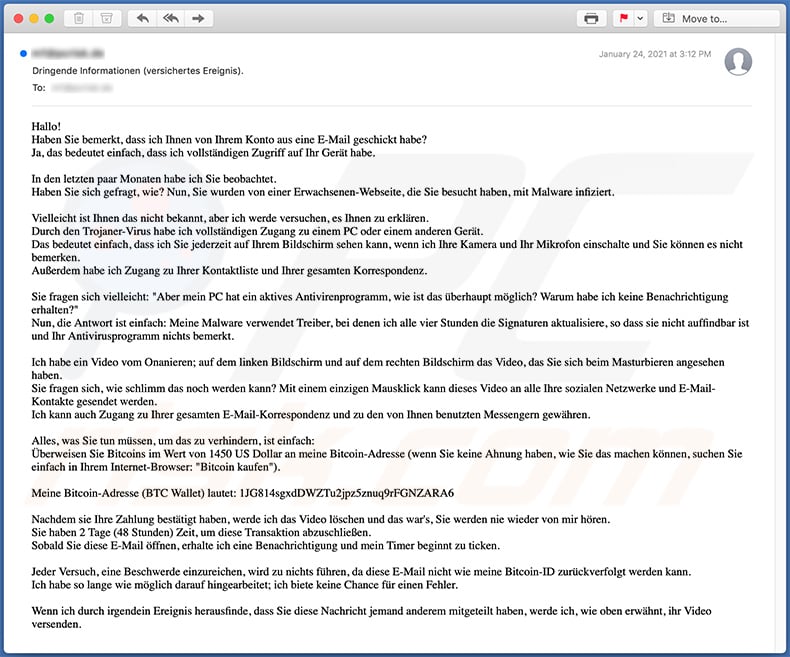
Text presented within:
Subject: Dringende Informationen (versichertes Ereignis).
Hallo!
Haben Sie bemerkt, dass ich Ihnen von Ihrem Konto aus eine E-Mail geschickt habe?
Ja, das bedeutet einfach, dass ich vollständigen Zugriff auf Ihr Gerät habe.In den letzten paar Monaten habe ich Sie beobachtet.
Haben Sie sich gefragt, wie? Nun, Sie wurden von einer Erwachsenen-Webseite, die Sie besucht haben, mit Malware infiziert.Vielleicht ist Ihnen das nicht bekannt, aber ich werde versuchen, es Ihnen zu erklären.
Durch den Trojaner-Virus habe ich vollständigen Zugang zu einem PC oder einem anderen Gerät.
Das bedeutet einfach, dass ich Sie jederzeit auf Ihrem Bildschirm sehen kann, wenn ich Ihre Kamera und Ihr Mikrofon einschalte und Sie können es nicht bemerken.
Außerdem habe ich Zugang zu Ihrer Kontaktliste und Ihrer gesamten Korrespondenz.Sie fragen sich vielleicht: "Aber mein PC hat ein aktives Antivirenprogramm, wie ist das überhaupt möglich? Warum habe ich keine Benachrichtigung erhalten?"
Nun, die Antwort ist einfach: Meine Malware verwendet Treiber, bei denen ich alle vier Stunden die Signaturen aktualisiere, so dass sie nicht auffindbar ist und Ihr Antivirusprogramm nichts bemerkt.Ich habe ein Video vom Onanieren; auf dem linken Bildschirm und auf dem rechten Bildschirm das Video, das Sie sich beim Masturbieren angesehen haben.
Sie fragen sich, wie schlimm das noch werden kann? Mit einem einzigen Mausklick kann dieses Video an alle Ihre sozialen Netzwerke und E-Mail-Kontakte gesendet werden.
Ich kann auch Zugang zu Ihrer gesamten E-Mail-Korrespondenz und zu den von Ihnen benutzten Messengern gewähren.Alles, was Sie tun müssen, um das zu verhindern, ist einfach:
Überweisen Sie Bitcoins im Wert von 1450 US Dollar an meine Bitcoin-Adresse (wenn Sie keine Ahnung haben, wie Sie das machen können, suchen Sie einfach in Ihrem Internet-Browser: "Bitcoin kaufen").Meine Bitcoin-Adresse (BTC Wallet) lautet: 1JG814sgxdDWZTu2jpz5znuq9rFGNZARA6
Nachdem sie Ihre Zahlung bestätigt haben, werde ich das Video löschen und das war's, Sie werden nie wieder von mir hören.
Sie haben 2 Tage (48 Stunden) Zeit, um diese Transaktion abzuschließen.
Sobald Sie diese E-Mail öffnen, erhalte ich eine Benachrichtigung und mein Timer beginnt zu ticken.Jeder Versuch, eine Beschwerde einzureichen, wird zu nichts führen, da diese E-Mail nicht wie meine Bitcoin-ID zurückverfolgt werden kann.
Ich habe so lange wie möglich darauf hingearbeitet; ich biete keine Chance für einen Fehler.Wenn ich durch irgendein Ereignis herausfinde, dass Sie diese Nachricht jemand anderem mitgeteilt haben, werde ich, wie oben erwähnt, ihr Video versenden.
Yet another Italian variant of "I Sent You An Email From Your Account" scam email:
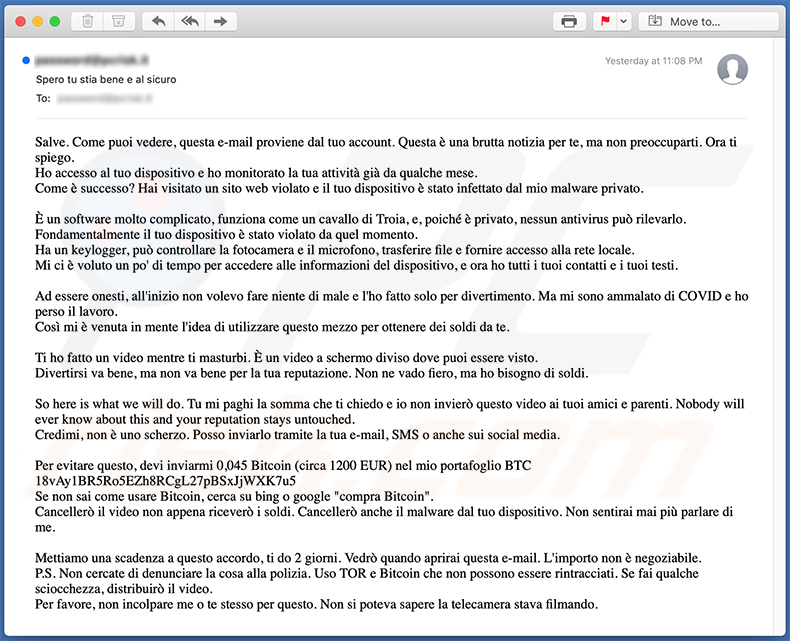
Text presented within:
Subject: Spero tu stia bene e al sicuro
Salve. Come puoi vedere, questa e-mail proviene dal tuo account. Questa è una brutta notizia per te, ma non preoccuparti. Ora ti spiego.
Ho accesso al tuo dispositivo e ho monitorato la tua attività già da qualche mese.
Come è successo? Hai visitato un sito web violato e il tuo dispositivo è stato infettato dal mio malware privato.È un software molto complicato, funziona come un cavallo di Troia, e, poiché è privato, nessun antivirus può rilevarlo. Fondamentalmente il tuo dispositivo è stato violato da quel momento.
Ha un keylogger, può controllare la fotocamera e il microfono, trasferire file e fornire accesso alla rete locale.
Mi ci è voluto un po' di tempo per accedere alle informazioni del dispositivo, e ora ho tutti i tuoi contatti e i tuoi testi.Ad essere onesti, all'inizio non volevo fare niente di male e l'ho fatto solo per divertimento. Ma mi sono ammalato di COVID e ho perso il lavoro.
Così mi è venuta in mente l'idea di utilizzare questo mezzo per ottenere dei soldi da te.Ti ho fatto un video mentre ti masturbi. È un video a schermo diviso dove puoi essere visto.
Divertirsi va bene, ma non va bene per la tua reputazione. Non ne vado fiero, ma ho bisogno di soldi.So here is what we will do. Tu mi paghi la somma che ti chiedo e io non invierò questo video ai tuoi amici e parenti. Nobody will ever know about this and your reputation stays untouched.
Credimi, non è uno scherzo. Posso inviarlo tramite la tua e-mail, SMS o anche sui social media.Per evitare questo, devi inviarmi 0,045 Bitcoin (circa 1200 EUR) nel mio portafoglio BTC 18vAy1BR5Ro5EZh8RCgL27pBSxJjWXK7u5, 1K9AdKDi5nTnYoeWFJ6yDtGYSn8m3qTYqo
Se non sai come usare Bitcoin, cerca su bing o google "compra Bitcoin".
Cancellerò il video non appena riceverò i soldi. Cancellerò anche il malware dal tuo dispositivo. Non sentirai mai più parlare di me.Mettiamo una scadenza a questo accordo, ti do 2 giorni. Vedrò quando aprirai questa e-mail. L'importo non è negoziabile.
P.S. Non cercate di denunciare la cosa alla polizia. Uso TOR e Bitcoin che non possono essere rintracciati. Se fai qualche sciocchezza, distribuirò il video.
Per favore, non incolpare me o te stesso per questo. Non si poteva sapere la telecamera stava filmando.
Another example of "I Sent You An Email From Your Account" spam email:
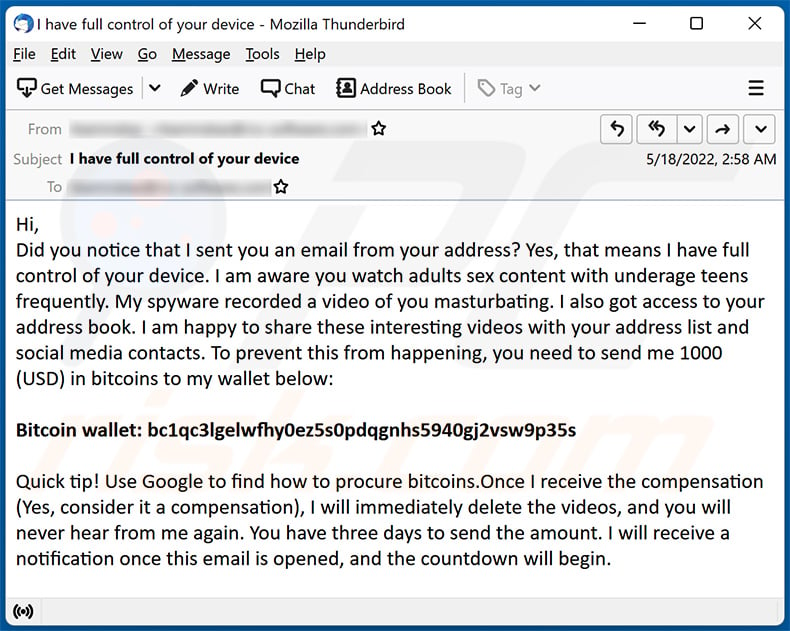
Text presented within:
Subject: I have full control of your device
Hi,
Did you notice that I sent you an email from your address? Yes, that means I have full control of your device. I am aware you watch adults sex content with underage teens frequently. My spyware recorded a video of you masturbating. I also got access to your address book. I am happy to share these interesting videos with your address list and social media contacts. To prevent this from happening, you need to send me 1000 (USD) in bitcoins to my wallet below:
Bitcoin wallet: bc1qc3lgelwfhy0ez5s0pdqgnhs5940gj2vsw9p35sQuick tip! Use Google to find how to procure bitcoins.Once I receive the compensation (Yes, consider it a compensation), I will immediately delete the videos, and you will never hear from me again. You have three days to send the amount. I will receive a notification once this email is opened, and the countdown will begin.
Instant automatic malware removal:
Manual threat removal might be a lengthy and complicated process that requires advanced IT skills. Combo Cleaner is a professional automatic malware removal tool that is recommended to get rid of malware. Download it by clicking the button below:
DOWNLOAD Combo CleanerBy downloading any software listed on this website you agree to our Privacy Policy and Terms of Use. To use full-featured product, you have to purchase a license for Combo Cleaner. 7 days free trial available. Combo Cleaner is owned and operated by RCS LT, the parent company of PCRisk.com.
Quick menu:
- What is I Sent You An Email From Your Account spam?
- Types of malicious emails.
- How to spot a malicious email?
- What to do if you fell for an email scam?
Types of malicious emails:
![]() Phishing Emails
Phishing Emails
Most commonly, cybercriminals use deceptive emails to trick Internet users into giving away their sensitive private information, for example, login information for various online services, email accounts, or online banking information.
Such attacks are called phishing. In a phishing attack, cybercriminals usually send an email message with some popular service logo (for example, Microsoft, DHL, Amazon, Netflix), create urgency (wrong shipping address, expired password, etc.), and place a link which they hope their potential victims will click on.
After clicking the link presented in such email message, victims are redirected to a fake website that looks identical or extremely similar to the original one. Victims are then asked to enter their password, credit card details, or some other information that gets stolen by cybercriminals.
![]() Emails with Malicious Attachments
Emails with Malicious Attachments
Another popular attack vector is email spam with malicious attachments that infect users' computers with malware. Malicious attachments usually carry trojans that are capable of stealing passwords, banking information, and other sensitive information.
In such attacks, cybercriminals' main goal is to trick their potential victims into opening an infected email attachment. To achieve this goal, email messages usually talk about recently received invoices, faxes, or voice messages.
If a potential victim falls for the lure and opens the attachment, their computers get infected, and cybercriminals can collect a lot of sensitive information.
While it's a more complicated method to steal personal information (spam filters and antivirus programs usually detect such attempts), if successful, cybercriminals can get a much wider array of data and can collect information for a long period of time.
![]() Sextortion Emails
Sextortion Emails
This is a type of phishing. In this case, users receive an email claiming that a cybercriminal could access the webcam of the potential victim and has a video recording of one's masturbation.
To get rid of the video, victims are asked to pay a ransom (usually using Bitcoin or another cryptocurrency). Nevertheless, all of these claims are false - users who receive such emails should ignore and delete them.
How to spot a malicious email?
While cyber criminals try to make their lure emails look trustworthy, here are some things that you should look for when trying to spot a phishing email:
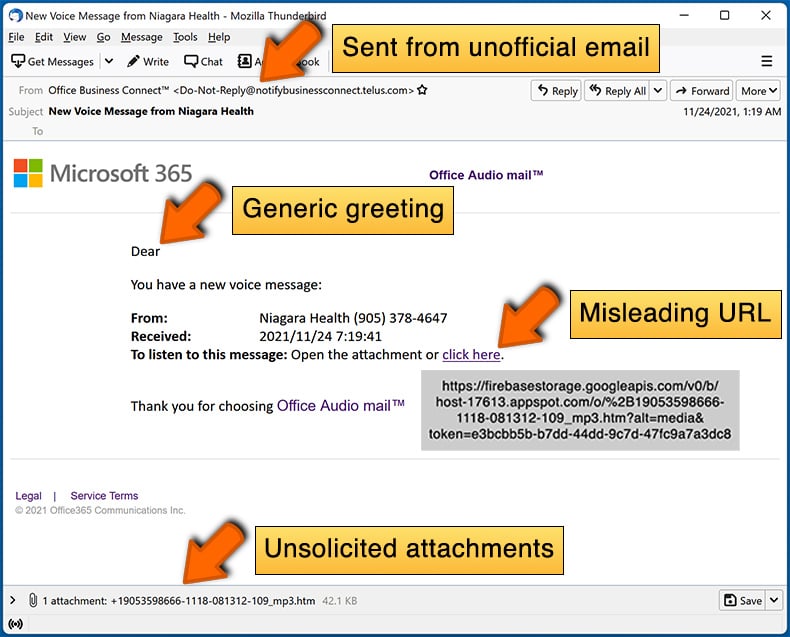
- Check the sender's ("from") email address: Hover your mouse over the "from" address and check if it's legitimate. For example, if you received an email from Microsoft, be sure to check if the email address is @microsoft.com and not something suspicious like @m1crosoft.com, @microsfot.com, @account-security-noreply.com, etc.
- Check for generic greetings: If the greeting in the email is "Dear user", "Dear @youremail.com", "Dear valued customer", this should raise suspiciousness. Most commonly, companies call you by your name. Lack of this information could signal a phishing attempt.
- Check the links in the email: Hover your mouse over the link presented in the email, if the link that appears seems suspicious, don't click it. For example, if you received an email from Microsoft and the link in the email shows that it will go to firebasestorage.googleapis.com/v0... you shouldn't trust it. It's best not to click any links in the emails but to visit the company website that sent you the email in the first place.
- Don't blindly trust email attachments: Most commonly, legitimate companies will ask you to log in to their website and to view any documents there; if you received an email with an attachment, it's a good idea to scan it with an antivirus application. Infected email attachments are a common attack vector used by cybercriminals.
To minimise the risk of opening phishing and malicious emails we recommend using Combo Cleaner Antivirus for Windows.
Example of a spam email:
What to do if you fell for an email scam?
- If you clicked on a link in a phishing email and entered your password - be sure to change your password as soon as possible. Usually, cybercriminals collect stolen credentials and then sell them to other groups that use them for malicious purposes. If you change your password in a timely manner, there's a chance that criminals won't have enough time to do any damage.
- If you entered your credit card information - contact your bank as soon as possible and explain the situation. There's a good chance that you will need to cancel your compromised credit card and get a new one.
- If you see any signs of identity theft - you should immediately contact the Federal Trade Commission. This institution will collect information about your situation and create a personal recovery plan.
- If you opened a malicious attachment - your computer is probably infected, you should scan it with a reputable antivirus application. For this purpose, we recommend using Combo Cleaner Antivirus for Windows.
- Help other Internet users - report phishing emails to Anti-Phishing Working Group, FBI’s Internet Crime Complaint Center, National Fraud Information Center and U.S. Department of Justice.
Frequently Asked Questions (FAQ)
Why did I receive this email?
Spam emails are not personal. Cyber criminals distribute these letters in massive campaigns - therefore, thousands of users receive identical messages.
Was my computer actually hacked and does the sender have any information?
No, all the claims made by sextortion scam emails are false. Therefore, neither were your devices infected nor have the senders made/obtained compromising recordings featuring you. These emails pose no threat.
How did cyber criminals get my email password?
There are several possibilities. Scammers can "spoof" email addresses - so it only appears as though it was sent from the receipt's account. The email credentials could have been acquired through a phishing scam. They are commonly promoted through spam emails and entail phishing websites/files that are disguised as account log-in pages, registration/subscription forms, or similar. The least likely scenario is that this information was obtained through a data breach on your or a service provider's end.
I have sent cryptocurrency to the address presented in this email, can I get my money back?
Cryptocurrency transactions are practically untraceable. Hence, you will be unable to return your funds since these transactions are irreversible.
I have provided my personal information when tricked by a spam email, what should I do?
If you have disclosed account credentials - immediately change the passwords of all potentially exposed accounts and inform their official support. And if you have provided other private data (e.g., ID card details, credit card numbers, etc.) - contact the corresponding authorities without delay.
I have read a spam email but didn't open the attachment, is my computer infected?
No, reading a spam email will not lead to a system infection. Malware download/installation processes are jumpstarted when the attachments or links present in these letters are opened/clicked.
I have downloaded and opened a file attached to a spam email, is my computer infected?
If it was an executable (.exe, .run, etc.) - most likely, yes. However, you might have avoided triggering an infection if it was a document (.doc, .xls, .pdf, etc.). These formats may require additional user interaction (e.g., enabling macro commands) to start downloading/installing malware.
Will Combo Cleaner remove malware infections present in email attachments?
Yes, Combo Cleaner is capable of detecting and eliminating nearly all known malware infections. It has to be emphasized that performing a complete system scan is paramount - as high-end malicious software tends to hide deep within systems.
Share:

Tomas Meskauskas
Expert security researcher, professional malware analyst
I am passionate about computer security and technology. I have an experience of over 10 years working in various companies related to computer technical issue solving and Internet security. I have been working as an author and editor for pcrisk.com since 2010. Follow me on Twitter and LinkedIn to stay informed about the latest online security threats.
PCrisk security portal is brought by a company RCS LT.
Joined forces of security researchers help educate computer users about the latest online security threats. More information about the company RCS LT.
Our malware removal guides are free. However, if you want to support us you can send us a donation.
DonatePCrisk security portal is brought by a company RCS LT.
Joined forces of security researchers help educate computer users about the latest online security threats. More information about the company RCS LT.
Our malware removal guides are free. However, if you want to support us you can send us a donation.
Donate
▼ Show Discussion