Sodinokibi Ransomware Exploiting Windows Zero-Day
With the malware developers behind GandCrab supposedly retiring something had to fill the void left in the market created by their departure. It would seem a contender has stepped up to the plate and that contenders name is Sodinokibi, also referred to as Sodin or REvil. This new ransomware has been on researchers’ radars since the beginning of 2019 but a comprehensive analysis of the ransomware has proven difficult given that the operators continually change tactics which only leave morsels of information with which to go on.
Researcher’s at Kaspersky Labs have discovered a new campaign seen distributing Sodinokibi, called Sodin by the security firm, which exploits a Windows zero-day vulnerability rather than the tried and tested distribution methods such as spam email campaigns prompting users to download the malicious program. In an article published by Orkhan Mamedov, Artur Pakulov, and Fedor Sinitsyn it was noticed that the malware has been distributed via CVE-2018-8453 Windows zero-day in a campaign which is geographically focused in Asia, targeting Hong Kong, South Korea, and Taiwan. The vulnerability when exploited allows for the escalation of privileges when the Win32k component fails to properly handle objects in memory. The flaw has already received a patch which was released in October 2018. Previously the vulnerability was seen exploited by a state-sponsored hacking group called FruityArmor. In that instance, it was used to distribute a payload designed to remain undetected and persistent on a target’s machine which further allowed the attacker persistent access to the machine.
The use of a zero-day by state actors first, then cybercriminals and other hackers second is by no means a new phenomenon. It is often the case that this occurs in the wild. However, the use of a zero-day in the distribution of ransomware is only seen rarely.
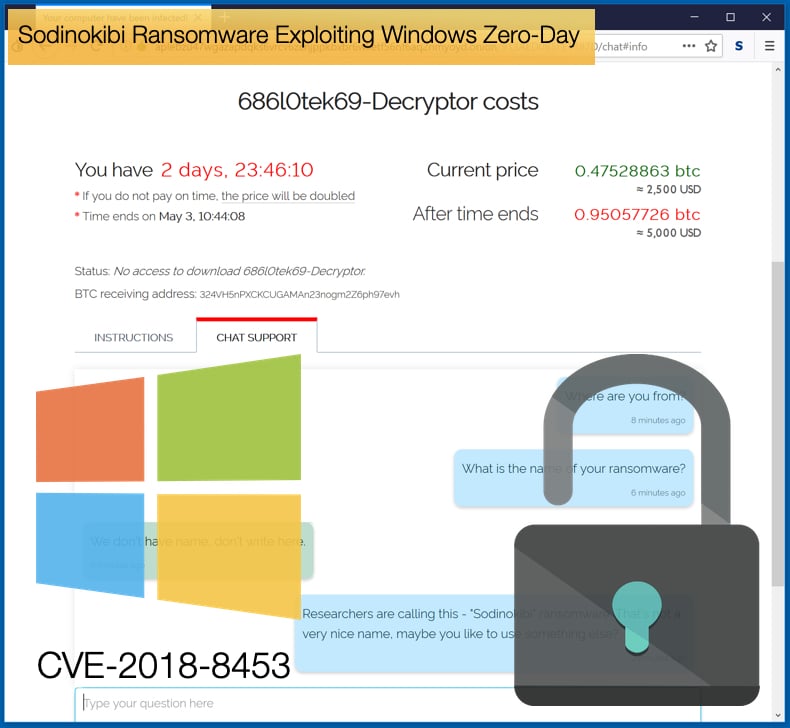
The researchers at Kaspersky noted how rare this tactic is used when distributing ransomware. Despite it being rare it would seem to be within the modus operandi of the Sodinokibi operators. Previously in April 2019, researchers based at Cisco Talos discovered a Sodinokibi campaign exploiting a vulnerability in Oracle WebLogic. The researchers stated that,
“Historically, most varieties of ransomware have required some form of user interaction, such as a user opening an attachment to an email message, clicking on a malicious link, or running a piece of malware on the device. In this case, the attackers simply leveraged the Oracle WebLogic vulnerability, causing the affected server to download a copy of the ransomware from attacker-controlled IP addresses 188.166.74[.]218 and 45.55.211[.]79. The 188.166.74[.]218 IP address is also home to a pair of other malicious domains unrelated to this ransomware attack: arg0s-co[.]uk, which is likely a phishing domain, and projectstore[.]guru, a domain with bogus PDF-related Google search results. The other IP, 45.55.211[.]79, hosts a pair of legitimate Chilean domains and appears to have been infected and repurposed by the attackers. The attackers were ultimately successful at encrypting a number of systems during this incident.”
The latest campaign exploiting the Windows zero-day has other unique characteristics not often seen in other ransomware variants and their associated distribution campaigns. Firstly, Sodinokibi campaigns have been seen to use the “Heaven’s Gate” tactic to evade detection by anti-virus software packages. This tactic was recently seen been used in the case of a malware loader. The tactic involves exploiting a flaw which allows 32-bit programs to hide their processes on 64-bit systems. Secondly, researchers discovered that the ransomware contains a “skeleton key”. This key is works as a backdoor to the encryption process, allowing the Sodinokibi creator to decrypt any file, regardless of the original public & private encryption keys used to lock a victim's data. It has been suggested that incorporation of such key may indicate that Sodinokibi may form part of ransomware as a service, similar to that of GandCrab. By including the key the operators of the ransomware could further decrypt files without the knowledge of the hacker who distributed the ransomware, this would in some cases be the person who is hiring the ransomware as a service.
Links to GandCrab
It has been suggested that there may exist a link to GandCrab that goes beyond similarities. Researchers at Tesorion suggest that Sodinokibi may have started where GandCrab left off. This evolution may even indicate that those behind GandCrab are now behind Sodinokibi. While it is still too early to say for sure researchers have provided some evidence to support this claim. According to the researchers,
“The Cisco Talos team reported how they encountered both Sodinokibi and GandCrab in a single attack, dubbing this ‘The GandCrab affiliate connection’. Besides a connection through an actor using both families, there seems to also be a more technical connection between them. Even though the code bases differ significantly, the lists of strings that are used to generate the URLs are very similar (although not identical), and there are some striking similarities in how this specific part of the code works, e.g., in the somewhat far-fetched way that the random length of the filename is repeatedly recalculated…On top of our technical analysis, we have also encountered another bit of circumstantial evidence supporting a possible connection between GandCrab and Sodinokibi: the number of new GandCrab binaries that we have encountered during the last couple of weeks has decreased significantly when compared to the weeks before that. This coincides rather remarkably with the appearance of the new Sodinokibi family.”
If this is the case, a case only time will tell, researcher’s may be in for a busy period defending against campaigns distributed by various hackers hiring Sodinokibi for the extortion of cryptocurrency from unsuspecting individuals and companies.
Share:

Karolis Liucveikis
Experienced software engineer, passionate about behavioral analysis of malicious apps
Author and general operator of PCrisk's News and Removal Guides section. Co-researcher working alongside Tomas to discover the latest threats and global trends in the cyber security world. Karolis has experience of over 8 years working in this branch. He attended Kaunas University of Technology and graduated with a degree in Software Development in 2017. Extremely passionate about technical aspects and behavior of various malicious applications.
PCrisk security portal is brought by a company RCS LT.
Joined forces of security researchers help educate computer users about the latest online security threats. More information about the company RCS LT.
Our malware removal guides are free. However, if you want to support us you can send us a donation.
DonatePCrisk security portal is brought by a company RCS LT.
Joined forces of security researchers help educate computer users about the latest online security threats. More information about the company RCS LT.
Our malware removal guides are free. However, if you want to support us you can send us a donation.
Donate
▼ Show Discussion