Cyber criminals exploiting the name of Coronavirus
Over the last several weeks the global health emergency surrounding the Coronavirus has overshadowed many other world events. Daily breaking news surrounding the virus’ spread too far-flung regions demand attention. Now, hackers are looking to further their own aims by abusing the medical threat posed by the virus. Currently, three separate campaigns have been discovered using the Coronavirus in an attempt to harvest user credentials or, as in one case, spread Emotet. This is by no means a new tactic, often phishers will send out spam emails related to upcoming sporting events or other world events that garner mass attention to try to get recipients to click on a link or malicious document. Exploiting a global health emergency, as declared by the World Health Organisation, is a key indicator of the moral fiber of the attackers behind these campaigns.
The first phishing campaign, known as Wuhan coronavirus, was discovered by phishing simulation and security awareness training outfit KnowBe4. In the email composed by the attackers, they promise to provide a list of infections within the area the email recipient lives to trick them into clicking a link which redirects the recipient to a portal designed to steal their credentials. In the sample email shared with the public, the attackers try to pass the email off as an official alert distributed via the CDC Health Alert Network. In attempting to be an official release of the US Centers for Disease Control and Prevention (CDC) as well as statements like, “CDC has established an Incident Management System to coordinate a domestic and international public health response,” the attackers are actively attempting to lure the recipient into clicking the malicious link. This is often done to create a sense of urgency by presenting the situation as an emergency requiring immediate action.
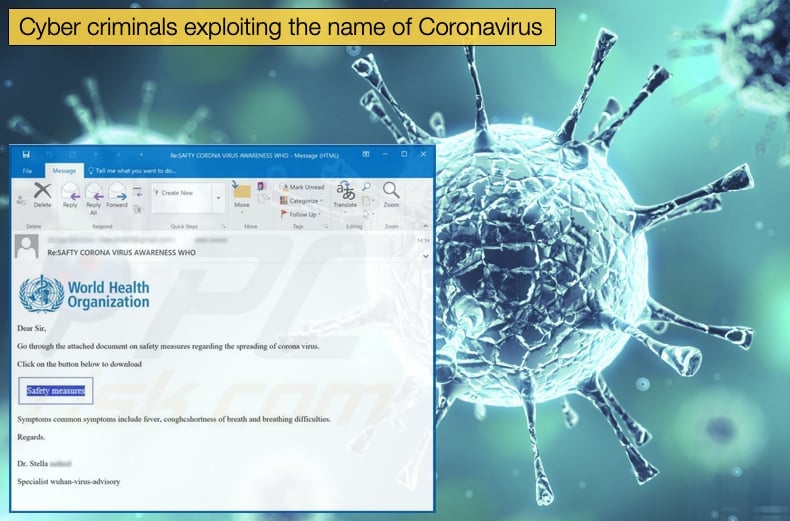
The phishing mail can be regarded as well-crafted as even the link is camouflaged to pass itself off as an official alert. However, when clicked it redirects the victim to an attacker-controlled and Outlook-themed phishing landing page used for collecting and stealing user credentials. Speaking to Bleeping Computer, Eric Howes, principal researcher at KnowBe4, said,
“This phish leverages public fear over a widely publicized virus threat…It is a bit unusual in that the bad guys are usually not so nimble in exploiting current events (they seem to put more time/effort in developing payloads and methods for obfuscating payloads). Then again, this story has been building for several weeks. The phishing email itself is rather well done, so I'm guessing whoever is behind it modeled the email after existing CDC press releases. There is a subject/verb agreement error in the second paragraph, but it's a common one that plenty of folks make. Still, not the kind of error one would expect from a professional PR operation, which the CDC undoubtedly has. Doubtful whether most readers would notice, though.”
The second campaign discovered, known as 2019-nCOV, was discovered by researchers at security firm Mimecast. In details released to various media publications, the campaign targets residents in the UK and the US. The email includes an attachment with text urging the recipient to download the attachment and go through the contents as it provides safety tips that “can save you.”
The attachment is a PDF that includes a malicious payload, as to the malware dropped little detail is provided. Francis Gaffney, Mimecast's director of threat intelligence, stated,
“The sole intention of these threat actors is to play on the public’s genuine fear to increase the likelihood of users clicking on an attachment or link delivered in a malicious communication, to cause infection, or for monetary gain. This is a rational choice by criminals as research has shown that over 90% of compromises occur by email and that over 90% of those breaches are primarily attributable to user error.”
Emotet’s Latest Distribution Excuse
Discovered by IBM’s X-Force yet another spam email campaign was uncovered by researchers. This time targeting users in Japan, the email again used the Coronavirus as the lure to further the attacker’s malicious aims. The email contains a malicious Word document that when downloaded will drop Emotet on the victim’s PC. While the leveraging of the Coronavirus is worrying, what is more so is that those behind Emotet appear to be increasing their attack radius. Previously, Emotet was seen targeting organizations in Western Europe and North America. This spread across the globe can be attributed to Emotet provisioning access to TrickBot threat actors who often then later drop the Ryuk ransomware.
The email itself is written in coherent Japanese and appears at face value to be legitimate. Some of the emails discovered by researchers in their spam traps displayed email formats that accurately mimic those used by the Kyoto Prefecture, as well as information correct to the municipal body. Inside the mail, the recipient will find the malicious Word document and as with past distribution campaigns, the document attempts to trick recipients into allowing macros. From there the infection path is typically Emotet starting with malicious PowerShell scripts that end up fetching and running executable files with the final payload being the Emotet file.
Those behind Emotet have constantly used world events as a driver for tricking users into installing Emotet. Even Greta Thunberg has been used as a lure in the past. However, researchers believe the latest campaign may be more successful when compared to those in the past given the media attention already given to the Coronavirus. Recently security researchers started observing spam campaigns distributing malware, the rogue email templates included references to Coronavirus and logos of World Health Organisation.
Share:

Karolis Liucveikis
Experienced software engineer, passionate about behavioral analysis of malicious apps
Author and general operator of PCrisk's News and Removal Guides section. Co-researcher working alongside Tomas to discover the latest threats and global trends in the cyber security world. Karolis has experience of over 8 years working in this branch. He attended Kaunas University of Technology and graduated with a degree in Software Development in 2017. Extremely passionate about technical aspects and behavior of various malicious applications.
PCrisk security portal is brought by a company RCS LT.
Joined forces of security researchers help educate computer users about the latest online security threats. More information about the company RCS LT.
Our malware removal guides are free. However, if you want to support us you can send us a donation.
DonatePCrisk security portal is brought by a company RCS LT.
Joined forces of security researchers help educate computer users about the latest online security threats. More information about the company RCS LT.
Our malware removal guides are free. However, if you want to support us you can send us a donation.
Donate
▼ Show Discussion