How to avoid installation of malware through the Coronavirus spam campaign
Phishing/ScamAlso Known As: Coronavirus spam
Get free scan and check if your device is infected.
Remove it nowTo use full-featured product, you have to purchase a license for Combo Cleaner. Seven days free trial available. Combo Cleaner is owned and operated by RCS LT, the parent company of PCRisk.com.
What is "Coronavirus Email Virus"?
There are a number of variants of the Coronavirus spam campaign. Cyber criminals use it to deceive recipients into infecting their computers with malicious programs such as Agent Tesla, Emotet, LokiBot, Remcos, TrickBot, FormBook, Ave Maria, LimeRAT, CrimsonRAT, and other high-risk malware.
They send emails that contain 1) a website link that downloads a malicious file/display dubious content (e.g., phishing sites), or 2) a malicious attachment. In any case, if opened and executed, these files/attachments install a malicious program. We strongly recommend that you ignore this email, which has nothing to do with the coronavirus.
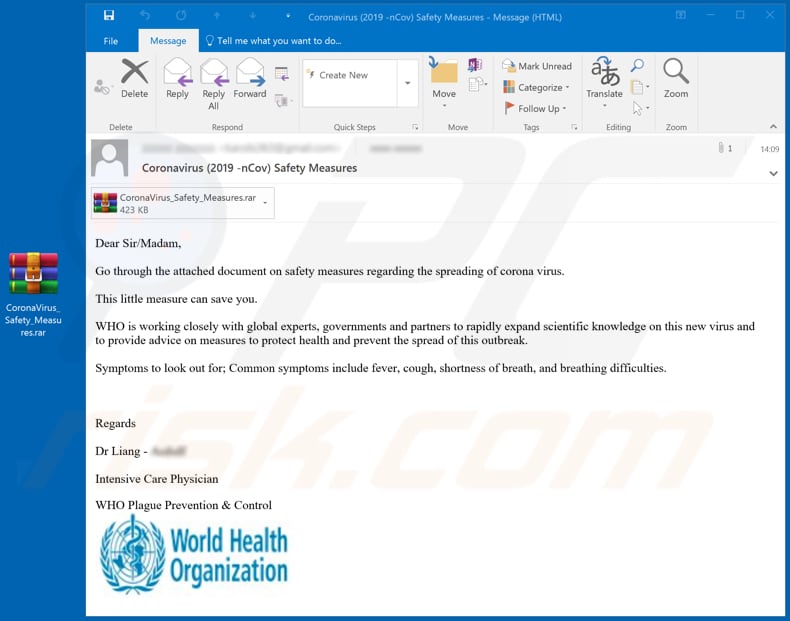
This spam campaign variant is disguised as a message from the World Health Organization (WHO) regarding protective measures against the new coronavirus. It suggests that the attached file or included website link contains information about how to prevent coronavirus from spreading and avoid being infected.
In fact, the attached files that are downloaded via the included link install another malicious program. This coronavirus spam campaign is used to spread different malicious programs. It is likely that the cyber criminals responsible attempt to infect computers with a Trojan or ransomware.
They might also use a coronavirus campaign to spread other types of malware. Typically, they proliferate Trojans that steal sensitive information such as logins, passwords, credit card details (or other banking information), etc., or open 'backdoors' for other malicious software to infiltrate.
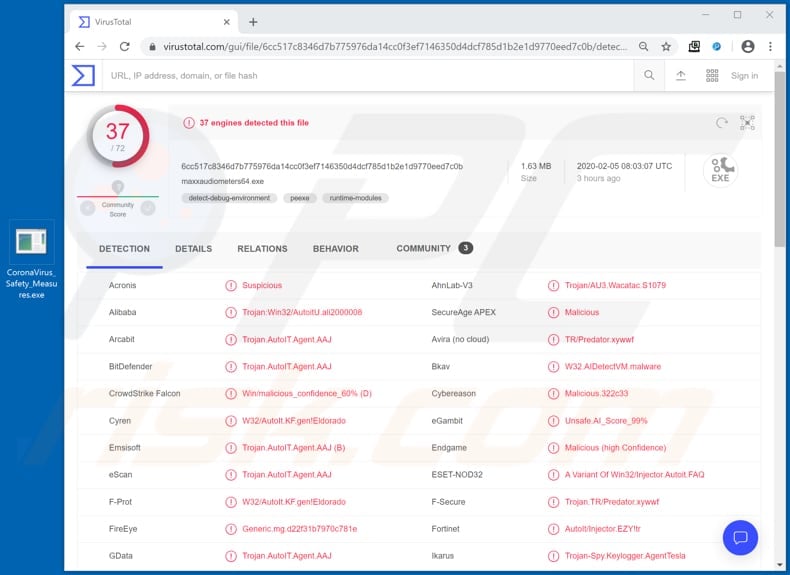
Ransomware encrypts files so that victims cannot recover them without specific tools that can only be purchased from the developers. In this way, victims of ransomware often lose data and money. Research shows that the executable within the "CoronaVirus_Safety_Measures.rar" file, which is attached to one of the emails of this spam campaign, spreads Agent Tesla.
This is a remote access tool, which, if installed, allows criminals to take control over the infected computer. One of its main features is keylogging - it can be used to record system keystrokes (record pressed keys). This feature can be employed to steal accounts, credentials and various other personal information.
Regardless of what malicious software cyber criminals behind this spam campaign attempt to distribute, attachments and website links must never be opened. By opening them, recipients risk experiencing monetary/data loss, problems relating to privacy, browsing safety, having their identities stolen, and other serious issues.
| Name | Coronavirus spam |
| Threat Type | Trojan, password-stealing virus, banking malware, spyware. |
| Hoax | This spam campaign delivers emails disguised as messages regarding protective measures against the coronavirus. |
| Attachment(s) | CoronaVirus_Safety_Measures.rar |
| Detection Names (CoronaVirus_Safety_Measures.rar) | Arcabit (Trojan.AutoIT.Agent.AAJ), Emsisoft (Trojan.AutoIT.Agent.AAJ (B)), ESET-NOD32 (A Variant Of Win32/Injector.Autoit.FAQ), Kaspersky (Trojan-Dropper.Win32.Autit.nlm), Full List Of Detections (VirusTotal) |
| Symptoms | Trojans are designed to stealthily infiltrate the victim's computer and remain silent, and thus no particular symptoms are clearly visible on an infected machine. |
| Payload | Agent Tesla, Emotet, LokiBot, Remcos, TrickBot, FormBook, Ave Maria, LimeRAT, CrimsonRAT, and a variety of other malicious programs. |
| Distribution methods | Infected email attachments, malicious online advertisements, social engineering, software 'cracks'. |
| Damage | Stolen passwords and banking information, identity theft, the victim's computer added to a botnet. |
| Malware Removal (Windows) |
To eliminate possible malware infections, scan your computer with legitimate antivirus software. Our security researchers recommend using Combo Cleaner. Download Combo CleanerTo use full-featured product, you have to purchase a license for Combo Cleaner. 7 days free trial available. Combo Cleaner is owned and operated by RCS LT, the parent company of PCRisk.com. |
Other examples of spam campaigns used by cyber criminals to trick recipients into installing malicious software include "Greta Thunberg Email Virus", "Christmas Party Email" and "UPS Email Virus". In most cases, these campaigns are disguised as important, official messages from legitimate companies.
Recipients who open attachments or files downloaded through website links included in such emails often infect their systems with high-risk malware, which cyber criminals spread to generate revenue in various ways.
How did "Coronavirus Email Virus" infect my computer?
Research shows that cyber criminals spread malware through this spam campaign by including a website link or attaching a malicious file to their emails.
Most commonly used file formats to spread malware through emails (attachments and/or website links within them) are malicious Microsoft Office, PDF document, executable file such as .exe, archive file (ZIP, RAR) or JavaScript files. Typically, these files infect systems when recipients execute (open) them.
For example, if an attachment (or a file downloaded through a link) is an MS Office document and it is opened with a Microsoft Office 2010 or later, it will ask permission to enable macros commands (editing). By granting this permission, the malicious document is allowed to install a malicious program.
Older MS Office versions (developed before 2010) do not include 'Protected View mode' and, therefore, install malware without asking permission.
How to avoid installation of malware
No software should be downloaded or installed through third party downloaders/installers, unofficial websites, Peer-to-Peer networks (e.g., torrent clients, eMule), or other such tools/sources. Use official websites and direct links. Installed software should not be updated via unofficial, third party tools.
The only safe way to achieve is to use implemented functions/tools that are provided by official developers. The same applies to activation of licensed (paid) software. Furthermore, it is illegal to use unofficial activation ('cracking') tools and they often cause installation of malware.
Attachments that are included in irrelevant emails that are received from unknown, suspicious addresses should not be opened. Cyber criminals tend to disguise their emails as official, important, legitimate, etc. Attachments and/or website links in emails should be opened only only when it is safe to do so.
Regularly scan the operating system with a reputable anti-spyware or antivirus suite and remove detected threats immediately. If you have already opened "Coronavirus Email Virus" attachment, we recommend running a scan with Combo Cleaner Antivirus for Windows to automatically eliminate infiltrated malware.
Text presented in one variant of the "Coronavirus Email Virus" email message:
Subject: Coronavirus (2019 -nCov) Safety Measures
Dear Sir/Madam,Go through the attached document on safety measures regarding the spreading of corona virus.
This little measure can save you.
WHO is working closely with global experts, governments and partners to rapidly expand scientific knowledge on this new virus and to provide advice on measures to protect health and prevent the spread of this outbreak.
Symptoms to look out for; Common symptoms include fever, cough, shortness of breath, and breathing difficulties.
Regards
Dr Liang -
Intensive Care Physician
WHO Plague Prevention & Control
Screenshot of another variant of the "Coronavirus Email Virus" email message:
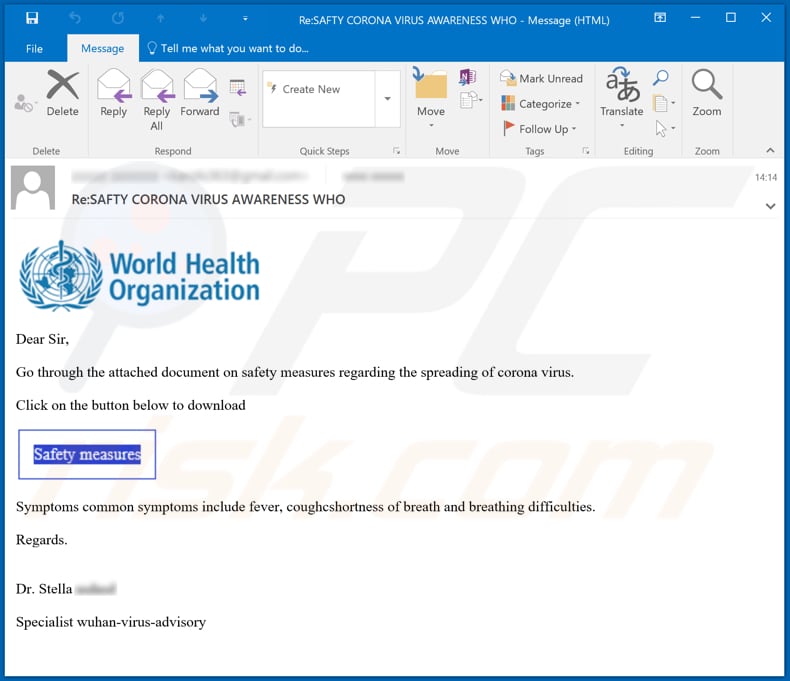
Text in this email:
Subject: Re:SAFTY CORONA VIRUS AWARENESS WHO
Dear Sir,
Go through the attached document on safety measures regarding the spreading of corona virus.
Click on the button below to download
Symptoms common symptoms include fever, coughcshortness of breath and breathing difficulties.Regards.
Dr. StellaSpecialist wuhan-virus-advisory
Screenshot a malicious file which is distributed through the "Coronavirus Email Virus" spam campaign and is detected as threat by a number of virus detection engines on VirusTotal:
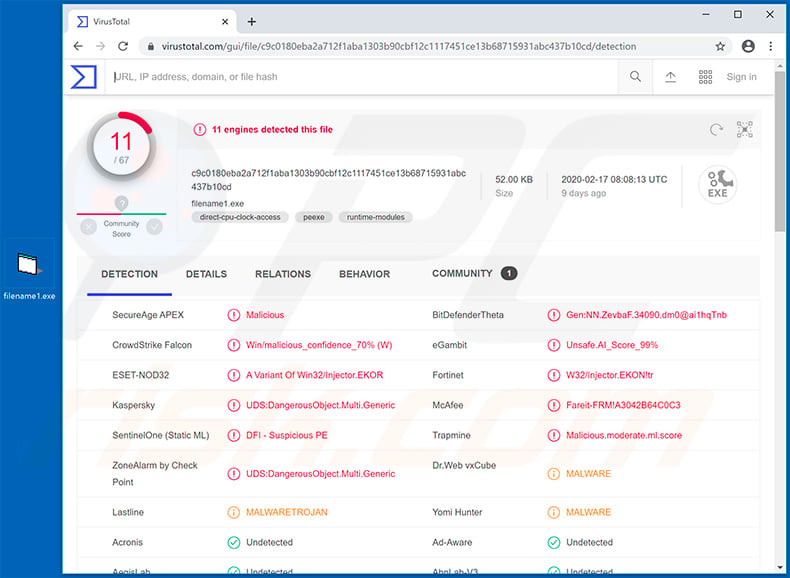
Another malicious attachment (a VBS file) distributed via coronavirus-related email spam campaigns. This attachment is designed to inject systems with Remcos RAT:
Criminals have recently released another variant coronavirus-related spam campaign which promotes Remcos RAT, Ave Maria Trojan and LimeRAT:
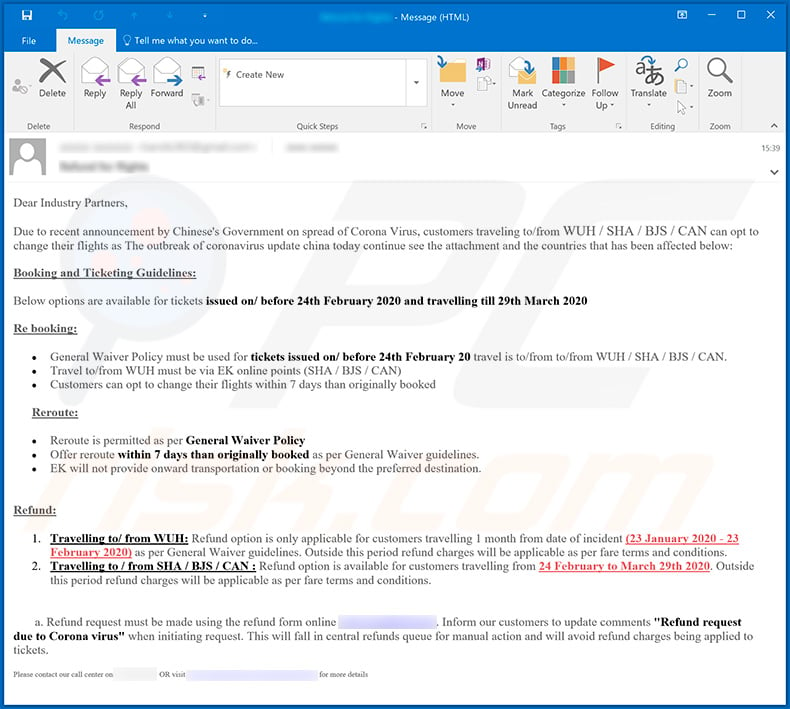
Text presented within this email:
Dear Industry Partners,
Due to recent announcement by Chinese's Government on spread of Corona Virus, customers traveling to/from WUH / SHA / BJS / CAN can opt to change their flights as The outbreak of coronavirus update china today continue see the attachment and the countries that has been affected below:
Booking and Ticketing Guidelines:
Below options are available for tickets issued on/ before 24th February 2020 and travelling till 29th March 2020
Re booking:
General Waiver Policy must be used for tickets issued on/ before 24th February 20 travel is to/from to/from WUH / SHA / BJS / CAN.
Travel to/from WUH must be via EK online points (SHA / BJS / CAN)
Customers can opt to change their flights within 7 days than originally bookedReroute:
Reroute is permitted as per General Waiver Policy
Offer reroute within 7 days than originally booked as per General Waiver guidelines.
EK will not provide onward transportation or booking beyond the preferred destination.Refund:
1. Travelling to/ from WUH: Refund option is only applicable for customers travelling 1 month from date of incident (23 January 2020 - 23 February 2020) as per General Waiver guidelines. Outside this period refund charges will be applicable as per fare terms and conditions.
2. Travelling to / from SHA / BJS / CAN : Refund option is available for customers travelling from 24 February to March 29th 2020. Outside this period refund charges will be applicable as per fare terms and conditions.a. Refund request must be made using the refund form online *******. Inform our customers to update comments "Refund request due to Corona virus" when initiating request. This will fall in central refunds queue for manual action and will avoid refund charges being applied to tickets.
Please contact our call center on ******* OR visit ******* for more details
Yet another variant of coronavirus-related spam campaign which is used to spread FormBook virus:
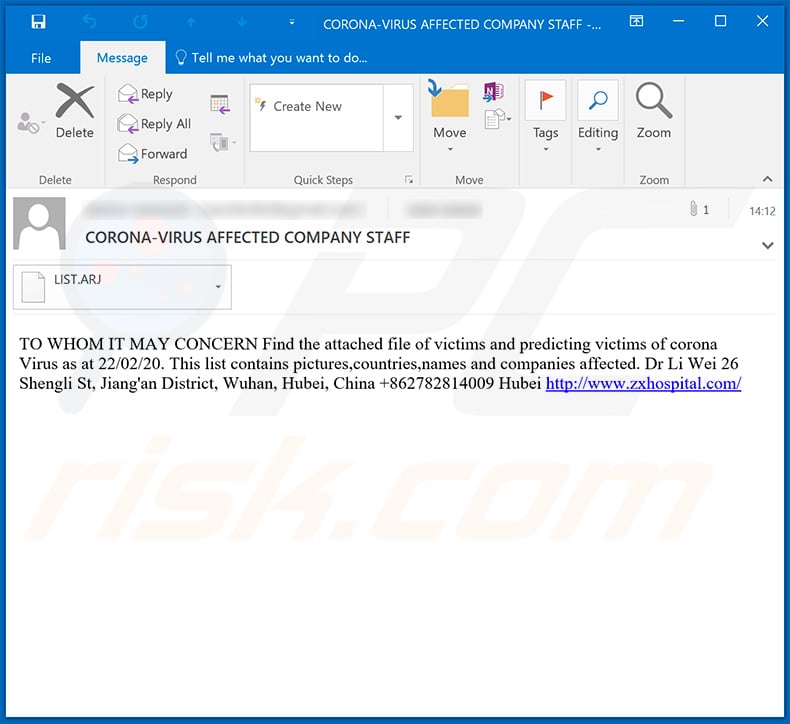
Text presented within this email:
Subject: CORONA-VIRUS AFFECTED COMPANY STAFF
TO WHOM IT MAY CONCERN Find the attached file of victims and predicting victims of corona Virus as at 22/02/20. This list contains pictures,countries,names and companies affected. Dr Li Wei 26 Shengli St, Jiang'an District, Wuhan, Hubei, China +862782814009 Hubei hxxp://www.zxhospital.com/
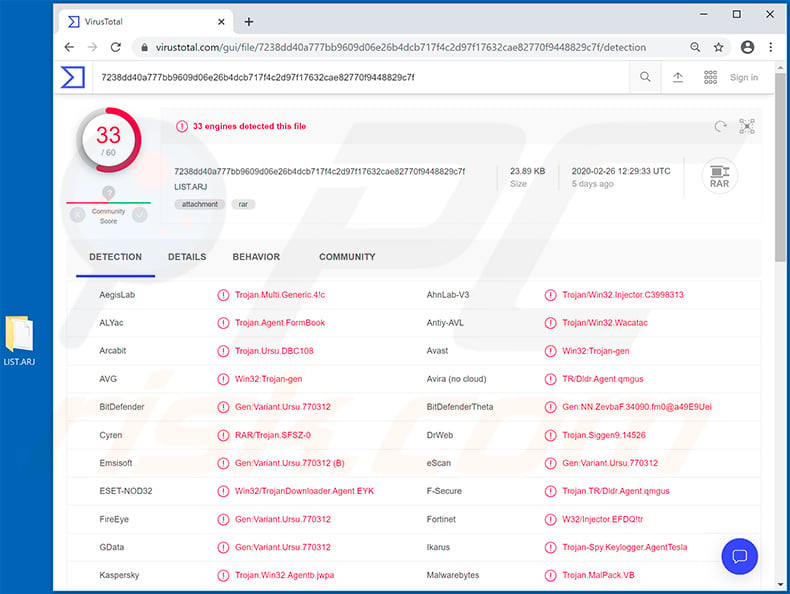
Screenshot of the malicious attachment's ("LIST.ARJ") detections in VirusTotal:
Yet another coronavirus-related spam email (in Italian) which distributes TrickBot trojan:
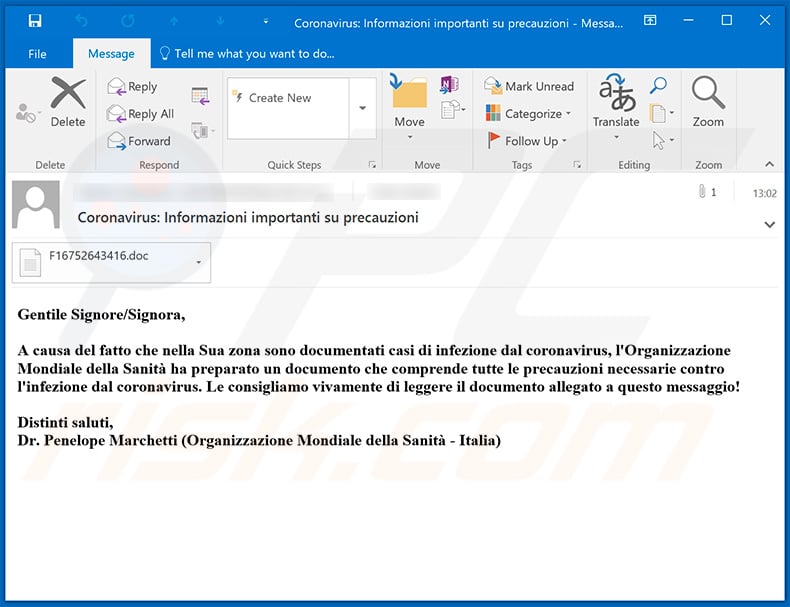
Text presented within this email:
Subject: Coronavirus: Informazioni importanti su precauzioni
Gentile Signore/Signora,
A causa del fatto che nella Sua zona sono documentati casi di infezione dal coronavirus, l'Organizzazione Mondiale della Sanità ha preparato un documento che comprende tutte le precauzioni necessarie contro l'infezione dal coronavirus. Le consigliamo vivamente di leggere il documento allegato a questo messaggio!
Distinti saluti,
Dr. Penelope Marchetti (Organizzazione Mondiale della Sanità - Italia)
Yet another variant of a spam email relating to the coronavirus. The email delivers a malicious MS Excel document ("COVID-19 Recomendaton_Precations_Desinfection.xlam") which injects Skidware RAT into the system:
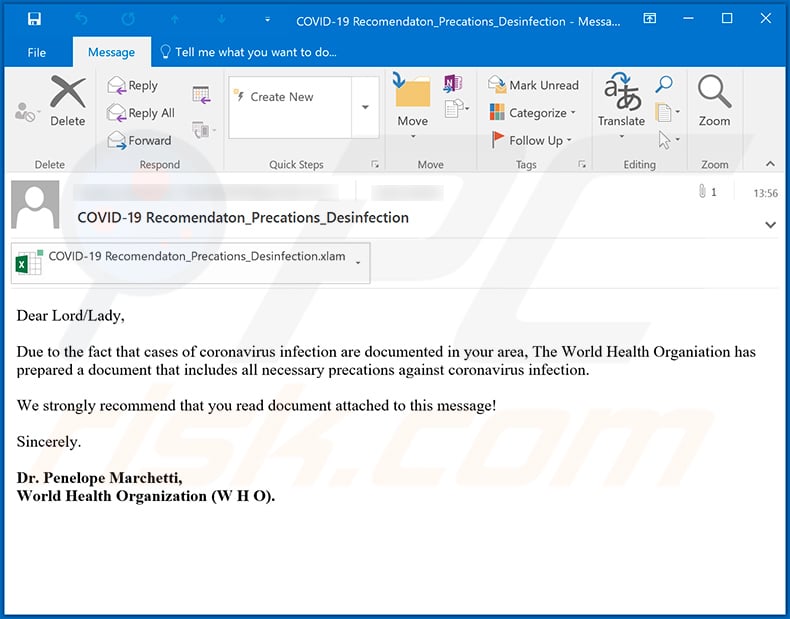
Text presented within this email:
Dear Lord/Lady,
Due to the fact that cases of coronavirus infection are documented in your area, The World Health Organiation has prepared a document that includes all necessary precations against coronavirus infection.
We strongly recommend that you read document attached to this message!
Sincerely.
Dr. Penelope Marchetti,
World Health Organization (W H O).
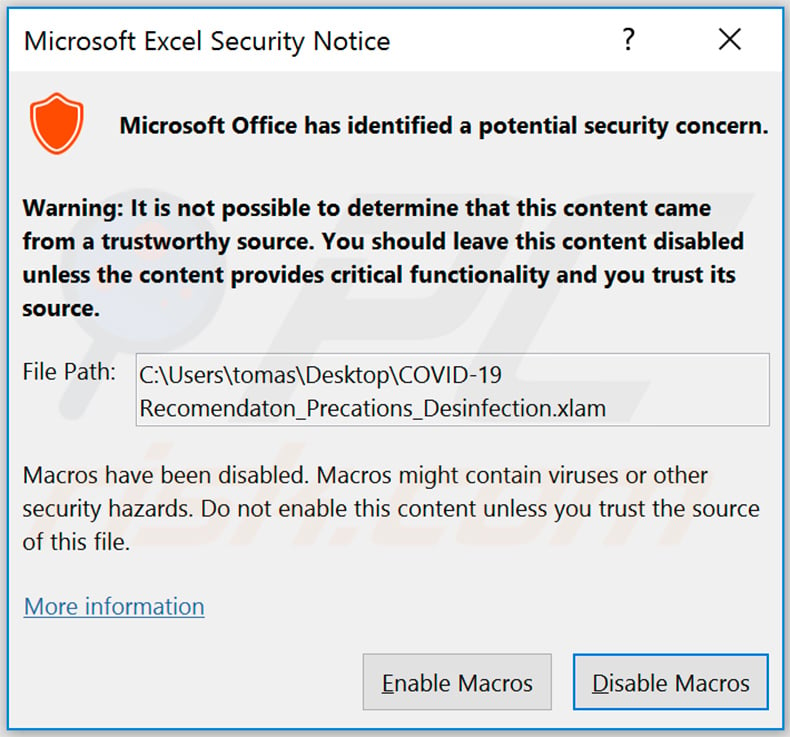
Pop-up window asking to enable macro commands once the malicious attachment is opened:
Yet another malicious Microsoft Excel document ("36978_1582552996_NHQEncl1.xls1") distributed using coronavirus-related spam email campaigns. This malicious document injects CrimsonRAT into the system using macro commands:
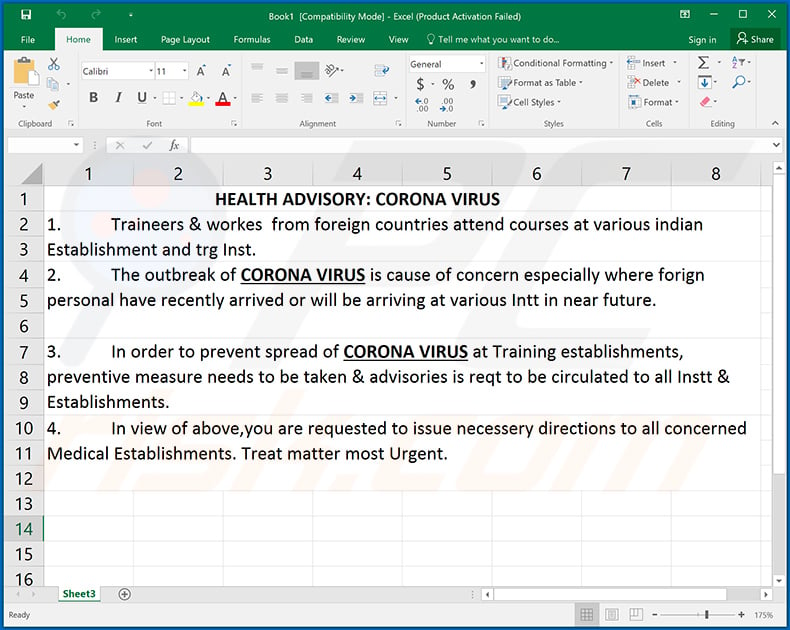
Text presented within the document:
HEALTH ADVISORY: CORONA VIRUS
1. Traineers & workes from foreign countries attend courses at various indian Establishment and trg Inst.
2. The outbreak of CORONA VIRUS is cause of concern especially where forign personal have recently arrived or will be arriving at various Intt in near future.
3. In order to prevent spread of CORONA VIRUS at Training establishments, preventive measure needs to be taken & advisories is reqt to be circulated to all Instt & Establishments.
4. In view of above,you are requested to issue necessery directions to all concerned Medical Establishments. Treat matter most Urgent.
Update 20 March 2020 - Cyber criminals have recently started a new spam email campaign to distribute RedLineStealer. They send thousands of deceptive emails asking for help to perform medical research relating to the coronavirus.
They ask users to install specific software that will supposedly use the recipient's computer to perform various calculations and, thus, help the researchers. The app they encourage users to install is called Folding@home.
Bear in mind that this application actually exists and it is legitimate, however, this spam campaign is simply a disguise: rather than installing the aforementioned Folding@home application, criminals inject RedLineStealer into the system. You can find more detail in Lawrence Abram's article posted in Bleeping Computer.
Appearance of a spam email used to distribute RedLineStealer by disguising it as the Folding@home application:
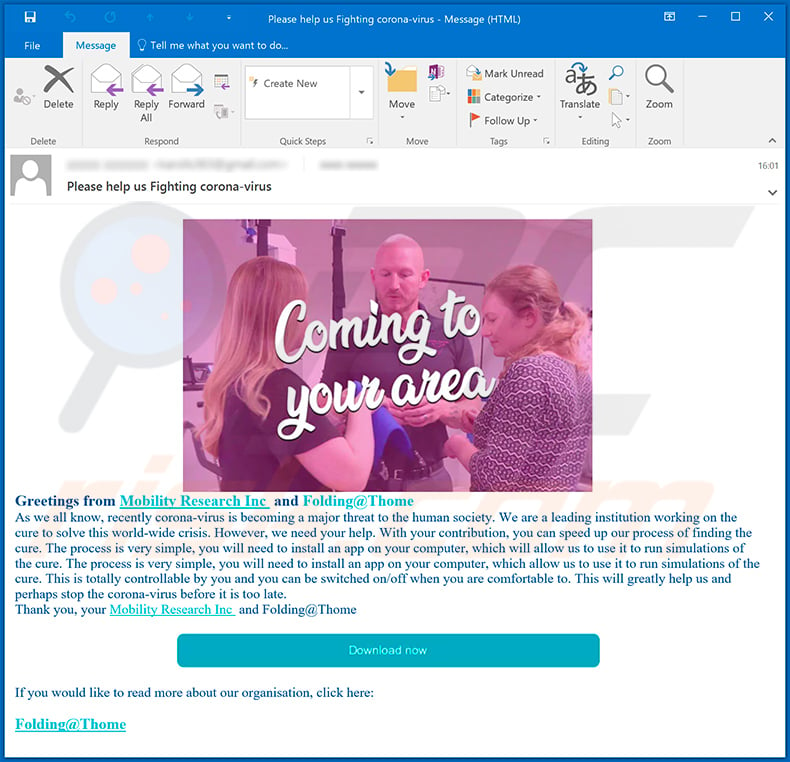
Text presented within this email:
Subject: Please help us Fighting corona-virus
Greetings from Mobility Research Inc and Folding@Thome As we all know, recently corona-virus is becoming a major threat to the human society. We are a leading institution working on the cure to solve this world-wide crisis. However, we need your help. With your contribution, you can speed up our process of finding the cure. The process is very simple, you will need to install an app on your computer, which will allow us to use it to run simulations of the cure. The process is very simple, you will need to install an app on your computer, which allow us to use it to run simulations of the cure. This is totally controllable by you and you can be switched on/off when you are comfortable to. This will greatly help us and perhaps stop the corona-virus before it is too late.
Thank you, your Mobility Research Inc and Folding@ThomeIf you would like to read more about our organisation, click here:
Folding@Thome
Example of a phishing email relating to the coronavirus:
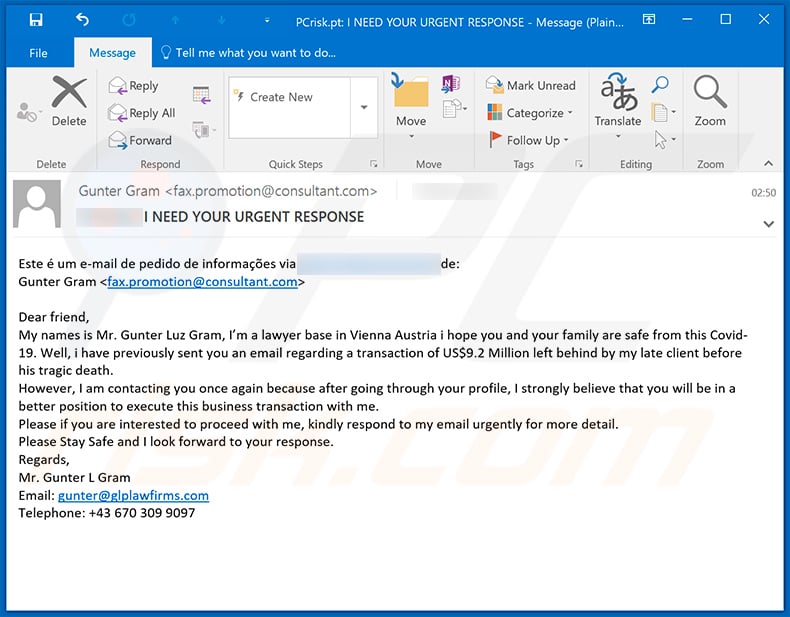
Text presented within this email:
Subject: **** I NEED YOUR URGENT RESPONSE
Este é um e-mail de pedido de informações via *** de:
Gunter Gram ;Dear friend,
My names is Mr. Gunter Luz Gram, I’m a lawyer base in Vienna Austria i hope you and your family are safe from this Covid-19. Well, i have previously sent you an email regarding a transaction of US$9.2 Million left behind by my late client before his tragic death.
However, I am contacting you once again because after going through your profile, I strongly believe that you will be in a better position to execute this business transaction with me.
Please if you are interested to proceed with me, kindly respond to my email urgently for more detail.
Please Stay Safe and I look forward to your response.
Regards,
Mr. Gunter L Gram
Email: gunter@glplawfirms.com
Telephone: +43 670 309 9097
Example of yet another Coronavirus-themed spam email used to spread TrickBot malware (the malicious attachment is a MS Excel document):
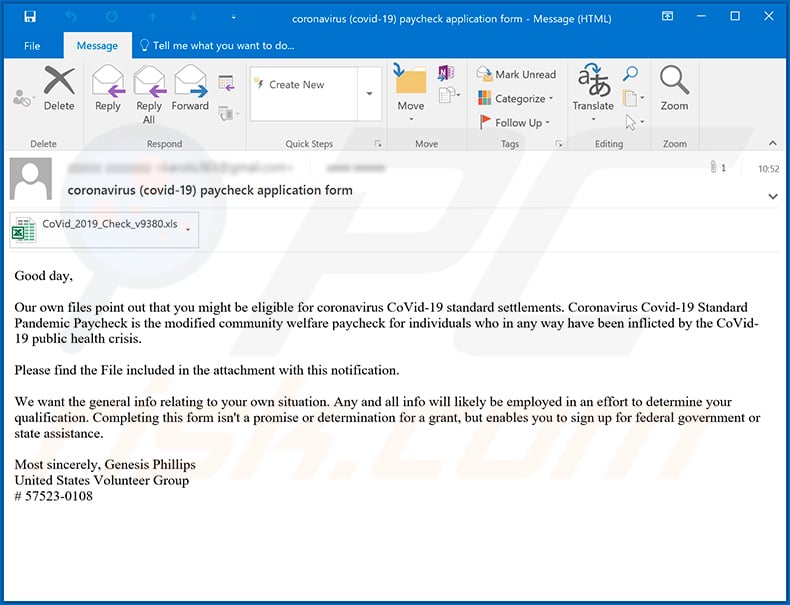
Text presented within:
Subject: coronavirus (covid-19) paycheck application form
Good day,
Our own files point out that you might be eligible for coronavirus CoVid-19 standard settlements. Coronavirus Covid-19 Standard Pandemic Paycheck is the modified community welfare paycheck for individuals who in any way have been inflicted by the CoVid-19 public health crisis.
Please find the File included in the attachment with this notification.
We want the general info relating to your own situation. Any and all info will likely be employed in an effort to determine your qualification. Completing this form isn't a promise or determination for a grant, but enables you to sign up for federal government or state assistance.
Most sincerely, Genesis Phillips
United States Volunteer Group
# 57523-0108
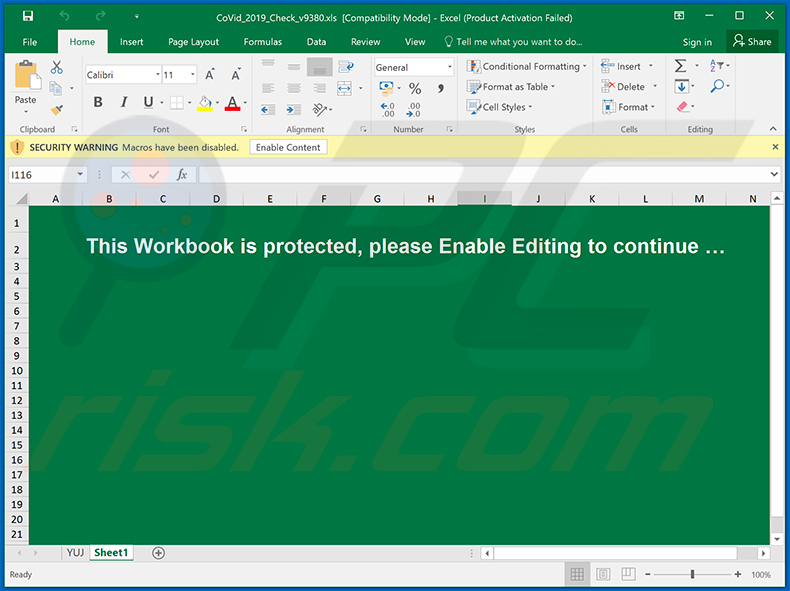
Screenshot of the malicious attachment:
Appearance of a spam email used to spread a coronavirus-themed PDF document which is used for phishing purposes:
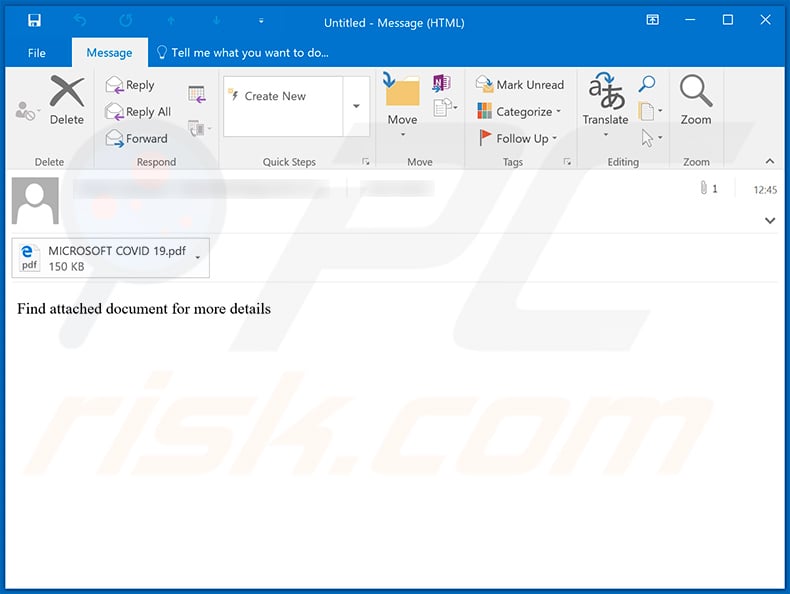
Text presented within:
Find attached document for more details
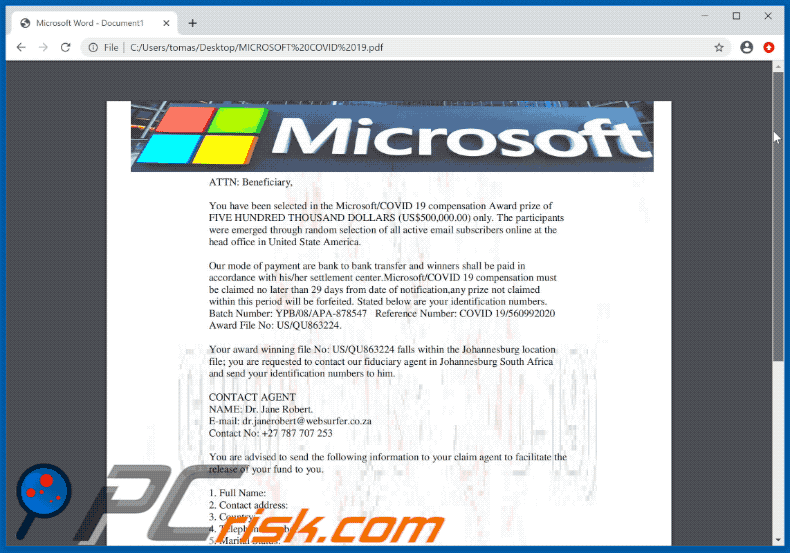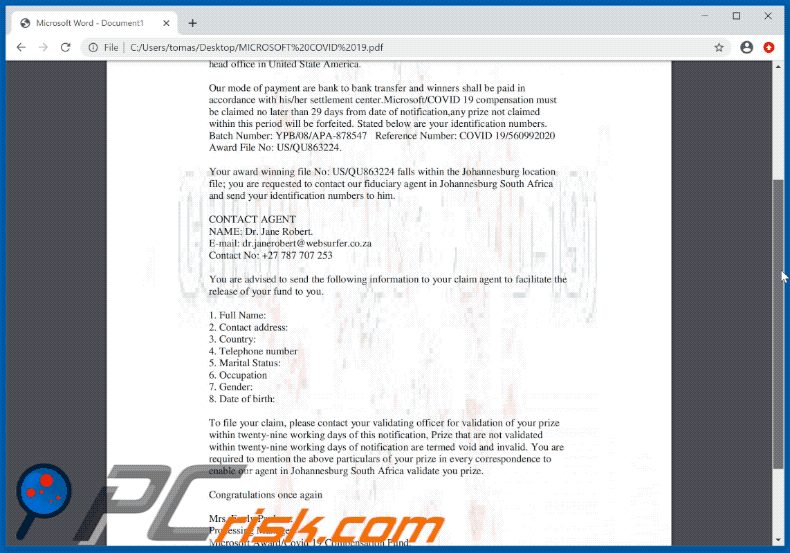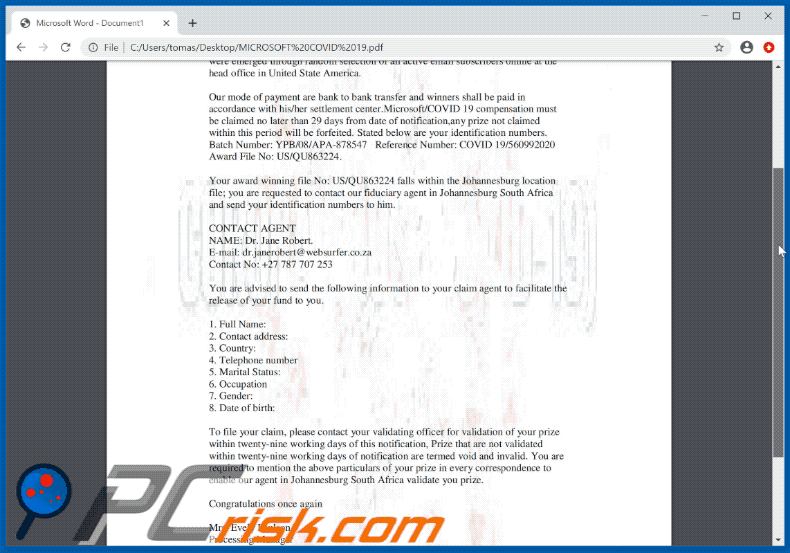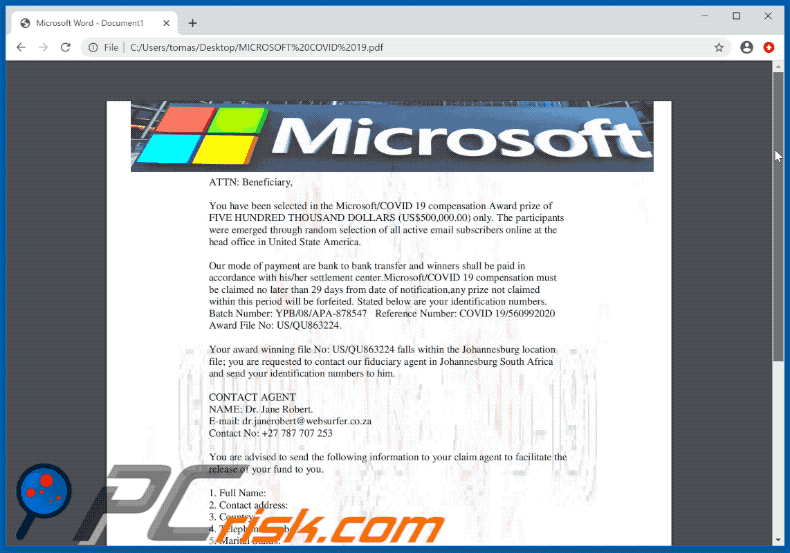
Appearance of the PDF document (GIF):
Text presented within:
ATTN: Beneficiary,
You have been selected in the Microsoft/COVID 19 compensation Award prize of
FIVE HUNDRED THOUSAND DOLLARS (US$500,000.00) only. The participants
were emerged through random selection of all active email subscribers online at the
head office in United State America.
Our mode of payment are bank to bank transfer and winners shall be paid in
accordance with his/her settlement center.Microsoft/COVID 19 compensation must
be claimed no later than 29 days from date of notification,any prize not claimed
within this period will be forfeited. Stated below are your identification numbers.
Batch Number: YPB/08/APA-878547 Reference Number: COVID 19/560992020
Award File No: US/QU863224.
Your award winning file No: US/QU863224 falls within the Johannesburg location
file; you are requested to contact our fiduciary agent in Johannesburg South Africa
and send your identification numbers to him.
CONTACT AGENT
NAME: Dr. Jane Robert.
E-mail: dr.janerobert@websurfer.co.za
Contact No: +27 787 707 253
You are advised to send the following information to your claim agent to facilitate the
release of your fund to you.
1. Full Name:
2. Contact address:
3. Country:
4. Telephone number
5. Marital Status:
6. Occupation
7. Gender:
8. Date of birth:
To file your claim, please contact your validating officer for validation of your prize
within twenty-nine working days of this notification, Prize that are not validated
within twenty-nine working days of notification are termed void and invalid. You are
required to mention the above particulars of your prize in every correspondence to
enable our agent in Johannesburg South Africa validate you prize.
Congratulations once again
Mrs. Evely Paulson.
Processing Manager
Microsoft Award/Covid 19 Compensation Fund.
NOTE: YOUR DETAILS ARE STRICTLY CONFIDENTIAL. SHOULD WE
OBSERVE DUAL CLAIMS WITH YOUR DETAILS, IT COULD LEAD TO
CANCELLATION OF YOUR FILE WITHOUT NOTIFICATION
Example of yet another coronavirus-themed spam email which is used to distribute a malicious MS Excel document designed to inject TrickBot trojan into the system:
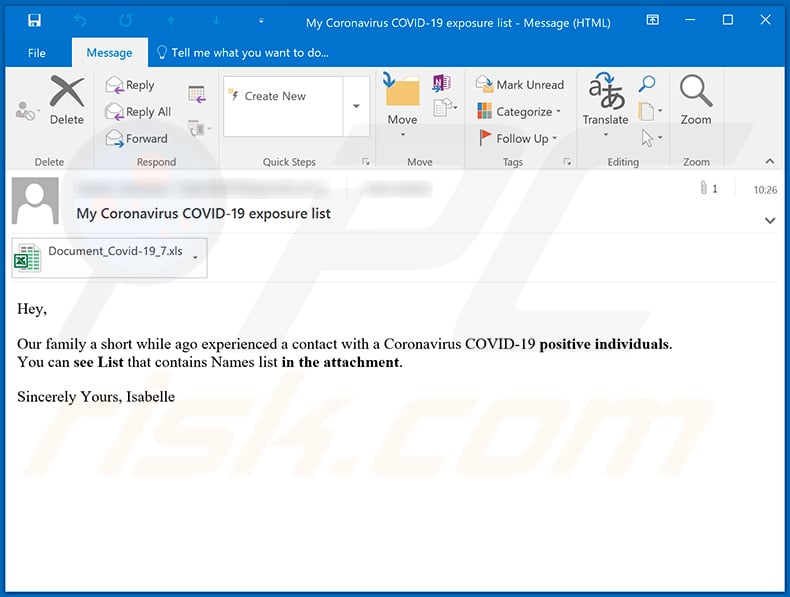
Text presented within:
Subject: My Coronavirus COVID-19 exposure list
Hey,
Our family a short while ago experienced a contact with a Coronavirus COVID-19 positive individuals.
You can see List that contains Names list in the attachment.Sincerely Yours, Isabelle
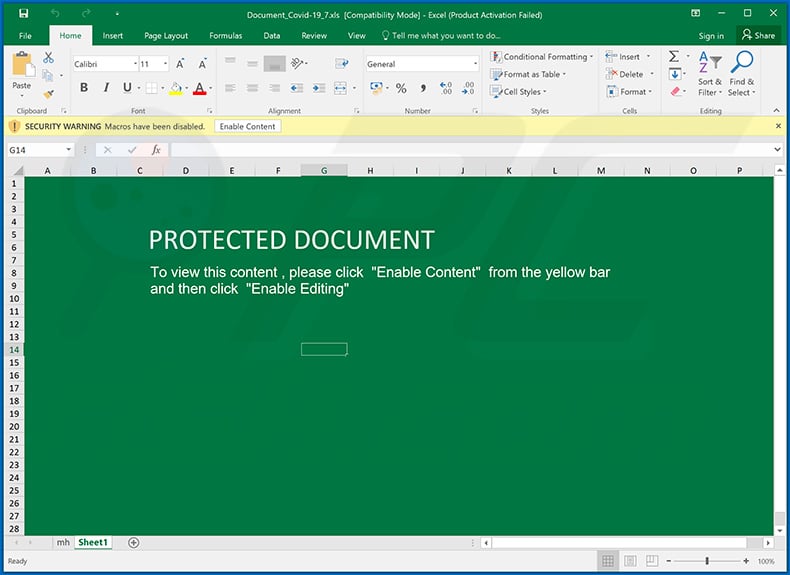
Screenshot of the attached MS Excel document:
Instant automatic malware removal:
Manual threat removal might be a lengthy and complicated process that requires advanced IT skills. Combo Cleaner is a professional automatic malware removal tool that is recommended to get rid of malware. Download it by clicking the button below:
DOWNLOAD Combo CleanerBy downloading any software listed on this website you agree to our Privacy Policy and Terms of Use. To use full-featured product, you have to purchase a license for Combo Cleaner. 7 days free trial available. Combo Cleaner is owned and operated by RCS LT, the parent company of PCRisk.com.
Quick menu:
- What is Coronavirus spam?
- Types of malicious emails.
- How to spot a malicious email?
- What to do if you fell for an email scam?
Types of malicious emails:
![]() Phishing Emails
Phishing Emails
Most commonly, cybercriminals use deceptive emails to trick Internet users into giving away their sensitive private information, for example, login information for various online services, email accounts, or online banking information.
Such attacks are called phishing. In a phishing attack, cybercriminals usually send an email message with some popular service logo (for example, Microsoft, DHL, Amazon, Netflix), create urgency (wrong shipping address, expired password, etc.), and place a link which they hope their potential victims will click on.
After clicking the link presented in such email message, victims are redirected to a fake website that looks identical or extremely similar to the original one. Victims are then asked to enter their password, credit card details, or some other information that gets stolen by cybercriminals.
![]() Emails with Malicious Attachments
Emails with Malicious Attachments
Another popular attack vector is email spam with malicious attachments that infect users' computers with malware. Malicious attachments usually carry trojans that are capable of stealing passwords, banking information, and other sensitive information.
In such attacks, cybercriminals' main goal is to trick their potential victims into opening an infected email attachment. To achieve this goal, email messages usually talk about recently received invoices, faxes, or voice messages.
If a potential victim falls for the lure and opens the attachment, their computers get infected, and cybercriminals can collect a lot of sensitive information.
While it's a more complicated method to steal personal information (spam filters and antivirus programs usually detect such attempts), if successful, cybercriminals can get a much wider array of data and can collect information for a long period of time.
![]() Sextortion Emails
Sextortion Emails
This is a type of phishing. In this case, users receive an email claiming that a cybercriminal could access the webcam of the potential victim and has a video recording of one's masturbation.
To get rid of the video, victims are asked to pay a ransom (usually using Bitcoin or another cryptocurrency). Nevertheless, all of these claims are false - users who receive such emails should ignore and delete them.
How to spot a malicious email?
While cyber criminals try to make their lure emails look trustworthy, here are some things that you should look for when trying to spot a phishing email:
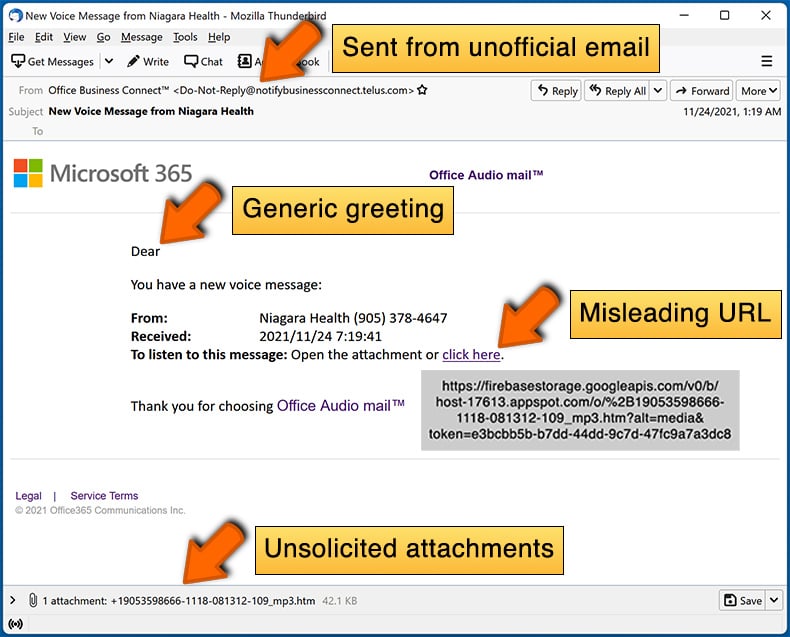
- Check the sender's ("from") email address: Hover your mouse over the "from" address and check if it's legitimate. For example, if you received an email from Microsoft, be sure to check if the email address is @microsoft.com and not something suspicious like @m1crosoft.com, @microsfot.com, @account-security-noreply.com, etc.
- Check for generic greetings: If the greeting in the email is "Dear user", "Dear @youremail.com", "Dear valued customer", this should raise suspiciousness. Most commonly, companies call you by your name. Lack of this information could signal a phishing attempt.
- Check the links in the email: Hover your mouse over the link presented in the email, if the link that appears seems suspicious, don't click it. For example, if you received an email from Microsoft and the link in the email shows that it will go to firebasestorage.googleapis.com/v0... you shouldn't trust it. It's best not to click any links in the emails but to visit the company website that sent you the email in the first place.
- Don't blindly trust email attachments: Most commonly, legitimate companies will ask you to log in to their website and to view any documents there; if you received an email with an attachment, it's a good idea to scan it with an antivirus application. Infected email attachments are a common attack vector used by cybercriminals.
To minimise the risk of opening phishing and malicious emails we recommend using Combo Cleaner Antivirus for Windows.
Example of a spam email:
What to do if you fell for an email scam?
- If you clicked on a link in a phishing email and entered your password - be sure to change your password as soon as possible. Usually, cybercriminals collect stolen credentials and then sell them to other groups that use them for malicious purposes. If you change your password in a timely manner, there's a chance that criminals won't have enough time to do any damage.
- If you entered your credit card information - contact your bank as soon as possible and explain the situation. There's a good chance that you will need to cancel your compromised credit card and get a new one.
- If you see any signs of identity theft - you should immediately contact the Federal Trade Commission. This institution will collect information about your situation and create a personal recovery plan.
- If you opened a malicious attachment - your computer is probably infected, you should scan it with a reputable antivirus application. For this purpose, we recommend using Combo Cleaner Antivirus for Windows.
- Help other Internet users - report phishing emails to Anti-Phishing Working Group, FBI’s Internet Crime Complaint Center, National Fraud Information Center and U.S. Department of Justice.
Share:

Tomas Meskauskas
Expert security researcher, professional malware analyst
I am passionate about computer security and technology. I have an experience of over 10 years working in various companies related to computer technical issue solving and Internet security. I have been working as an author and editor for pcrisk.com since 2010. Follow me on Twitter and LinkedIn to stay informed about the latest online security threats.
PCrisk security portal is brought by a company RCS LT.
Joined forces of security researchers help educate computer users about the latest online security threats. More information about the company RCS LT.
Our malware removal guides are free. However, if you want to support us you can send us a donation.
DonatePCrisk security portal is brought by a company RCS LT.
Joined forces of security researchers help educate computer users about the latest online security threats. More information about the company RCS LT.
Our malware removal guides are free. However, if you want to support us you can send us a donation.
Donate
▼ Show Discussion