NetWalker Ransomware nets $25 million since March
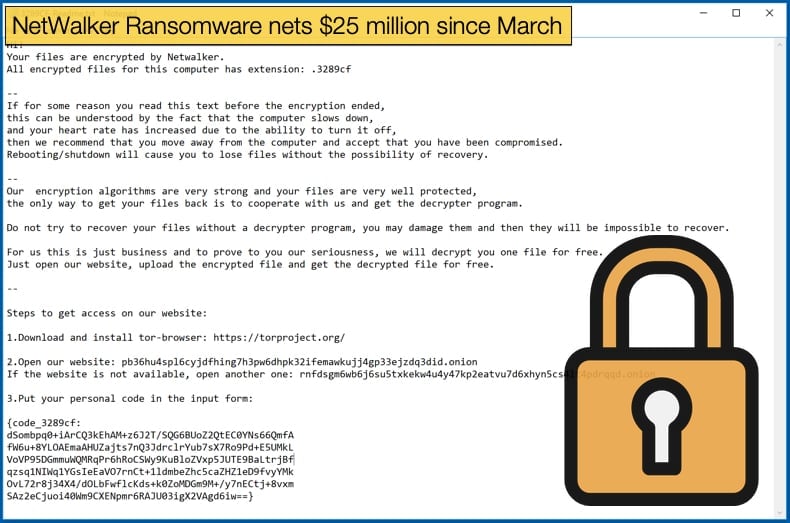
Based on research published by security firm McAfee has confirmed that the gang behind the NetWalker ransomware have established themselves as one of the most dangerous ransomware operators on the threat landscape. The research conducted by the firm reveals that the gang has potentially netted 25 million USD in ransomware payments since March 2020, proving the profitability of well organized and skilled ransomware gangs can generate as well as the danger posed by such gangs. While the 25 million USD figure is an estimate as it is not like these gangs have to report earnings to auditors or revenue services, it does mean that the gang ranks amongst some of the most successful gangs today including Dharma, Sodinokibi, and Ryuk. It is also noted by some that the figure of 25 million may be conservative due to the security firm’s limited view of the entire ransomware operation.
NetWalker began its life initially called Mailto and was first detected in August 2019, the name NetWalker was adopted late into 2019. The gang has operated as a Ransomware-as-a-Service (RaaS) for the entire length of its young life. The typical business model applied involves hackers applying for access to the ransomware’s portal, before access is granted hackers need to be vetted. Once access is granted they will be able to create new versions of the ransomware. From the research conducted it would seem that distribution is left to a second tier of affiliates rather than the developers of the ransomware.
Further, these affiliates seem to form semi-independent gangs who distribute and deploy the ransomware as they see fit. Since March there has been a drastic uptick in activity associated with the ransomware, including an ever-growing victims list. This surge in activity seems to coincide with operators making a concerted effort to select affiliates specializing in targeting larger enterprises, so-called big game hunting, rather than those looking to distribute the ransomware via mass spam email campaigns, for example.
The report published goes into a lot of detail regarding the ransomware itself as well as previous versions seen distributed. That being said, it is how the gang operates that may be seen in the future as the real value behind the research. The uptick in activity and targeted hiring seems to have kicked off with a post by a hacker going by the name “Bugatti” posting on two popular underground hacker forums. Based on the data it would seem that Bugatti had been active on said forums since February 2020 but researchers believe that the name has been adopted to replace another, with Bugatti assumed to be an experienced ransomware operator. This view is supported by how quickly NetWalker has earned a respected reputation amongst the underground and in a relatively short time. As well as potentially been an old hand at the ransomware game, Bugatti is willing to self-promote as posts were seen with Bitcoin addresses and US dollar amounts in a display of the ransomware’s financial success. Further researchers noted,
“Bugatti provides regular updates on the improvements in the ransomware, such as the popular Invoke-ReflectivePEInjection method, also commonly used by Sodinokibi. In addition to the improvements in the ransomware, open slots for new affiliates are advertised. Bugatti strongly emphasized that they are primarily looking for experienced affiliates that focus on compromising the complete networks of organizations as opposed to end users. NetWalker is clearly following in the footsteps of its illustrious targeted ransomware peers like Sodinokibi, Maze and Ryuk.”
Money Trail
By mentioning the Bitcoin addresses researchers were given the first clue in uncovering the potential amount of money extorted from victims. This is possible as Bitcoin consists of a publically accessible ledger tracking all transactions. The researchers believe with a high degree of certainty that the addresses mentioned in the self-promotion post are under the control of those behind NetWalker operations. The following key points were also uncovered during subsequent investigations:
- The first incoming transaction occurs on 1 March 2020.
- On 30 March 2020, the first incoming transaction appears where the amount is split between 4 different bitcoin addresses. A split like this is typically seen in Ransomware-as-a-Service, where the ransom payment is split between the RaaS operators and the affiliate who caused the infection. In this first transaction, the split is 80%, 10%, and two 5% portions. This split matches the advertisement on the underground forum (80% – 20%).
- The two 5% portions of the ransom payments that are split, seem to be consistently transferred to the two bitcoin addresses we revealed earlier (bc1q98 and 1DgLhG).
- While the beneficiaries of the 5% cuts remain the same, the beneficiary of the 10% cut seems to change over time. Based on the forum post we assume these addresses also belong to the NetWalker actors.
- Payments to the bc1q98 and 1DgLhG addresses that are not being split continue up until the end of May. Possibly the initial NetWalker operators added a RaaS operation while continuing to cause NetWalker infections themselves.
- While analyzing the bitcoin addresses that received 80% or more of the transaction amount, we noticed that some addresses receive payments multiple times. A possible explanation could be that the address is configured as payout addresses for a certain campaign or affiliate. We identified 30 unique bitcoin addresses that seem to be the beneficiary of this larger portion of the ransom transaction. Some of these only received one payment but there are several that received multiple payments.
- In the two addresses uncovered by tracing the transactions a total of 641 bitcoin is held on 27 July 2020. Which at the current market value of bitcoin is worth well over 7 million USD.
Further, researchers were able to determine specific amounts extorted. According to the researchers:
- They found that 23 transactions where the ransom payments were not split up and the beneficiaries are the two bitcoin addresses found by following the transactions mentioned in the underground forum post. The total amount of bitcoin extorted this way between 1 March 2020 and 27 July 2020 is 677 Bitcoin (BTC). Additionally, the amount received from remaining transactions following the Ransomware-as-a-Service scheme by these addresses between 1 March 2020 and 27 July 2020 is 188 BTC.
- In the transactions that are split, the largest amount (usually 80% to 90% of the total transaction value) is presumably transferred to the affiliate that caused the infection. When we summed up these largest portions, we saw a total of 1723 BTC being transferred to affiliates.
- The total amount of extorted bitcoin that has been uncovered by tracing transactions to these NetWalker related addresses is 2795 BTC between 1 March 2020 and 27 July 2020. By using historic bitcoin to USD exchange rates, we estimate a total of 25 million USD was extorted with these NetWalker related transactions.
FBI Alert
It is not only security firms that have been keeping tabs on NetWalker activity. The Federal Bureau of Investigation (FBI) recently published an alert warning those responsible for network administration and security that there was a surge in the ransomware’s activity. The alert details how the ransomware operates and what data is targeted for encryption. What was interesting about the alert is the details about how ransomware affiliates gain a foothold onto the victim’s network. Historically, NetWalker has carried out intrusion by using exploits in Oracle WebLogic and Apache Tomcat servers, by entering into networks via RDP endpoints with weak credentials, or by spear-phishing staff at important companies. According to the alert, affiliates have expanded the methods used to initially compromise networks including exploits for Pulse Secure VPN servers (CVE-201911510) and exploits for web apps that use the Telerik UI component (CVE-2019-18935).
The alert further warns US companies and government organizations to make sure to update their systems, as the bureau saw an uptick in activity from the NetWalker gang, which even hit some government networks. To help mitigate and prevent becoming a NetWalker victim the FBI advises:
- Backup critical data offline;
- Ensure that copies of critical data are stored in the cloud or on an external hard drive;
- Secure back-ups and ensure data is not accessible for modification or deletion;
- Install updated anti-virus software on all devices;
- Use only secure networks and VPNs and avoiding public WiFi networks;
- Use two-factor authentication with strong passwords.
- Keep devices and applications patched.
The alert also advises victims not to pay the ransom, stating,
“Paying a ransom may embolden adversaries to target additional organizations, encourage other criminal actors to engage in the distribution of ransomware, and/or may fund illicit activities. Paying the ransom also does not guarantee that a victim's files will be recovered.”
Share:

Karolis Liucveikis
Experienced software engineer, passionate about behavioral analysis of malicious apps
Author and general operator of PCrisk's News and Removal Guides section. Co-researcher working alongside Tomas to discover the latest threats and global trends in the cyber security world. Karolis has experience of over 8 years working in this branch. He attended Kaunas University of Technology and graduated with a degree in Software Development in 2017. Extremely passionate about technical aspects and behavior of various malicious applications.
PCrisk security portal is brought by a company RCS LT.
Joined forces of security researchers help educate computer users about the latest online security threats. More information about the company RCS LT.
Our malware removal guides are free. However, if you want to support us you can send us a donation.
DonatePCrisk security portal is brought by a company RCS LT.
Joined forces of security researchers help educate computer users about the latest online security threats. More information about the company RCS LT.
Our malware removal guides are free. However, if you want to support us you can send us a donation.
Donate
▼ Show Discussion