Emotet Blunders through Attack Campaign
In a campaign that started at the beginning of September, those operating the Emotet botnet have hampered the campaign's effectiveness through blunders they made. Emotet is typically in the news for when its creators decide to bring it back to life for yet another campaign, then it is placed in the cyber equivalent of hibernation. In 2019, Emotet activity dropped off sharply in May of that year only to surge in September for yet another campaign. Then again in 2020, the malware was placed into hibernation for roughly five months only to be brought back from near death in July. Rather than the successful awakening the malware is in the news once more but for more embarrassing reasons.
The latest campaign makes use of a change in tactics involving the malware’s operators distributing password-protected archives via spam emails in an attempt to bypass anti-spam filters and other security measures placed on email gateways. The latest campaign began on Friday it appears with security researcher Cryptolaemus noting a massive spike in Emotet activity. Once the spam emails are used to distribute Emotet bypass security measures is when the mistake made by the operators is made apparent. Like with previous campaigns the spam emails contain malicious Microsoft Office documents that attempt to trick the user into enabling macros. Once this is done a script can be run that fetches the main malware payload and the infection of the machine can begin in earnest. A lot rides on this ability to trick the recipient into enabling macros. This is where the massive mistake occurs.
The trick is to convince user that the document was created on a different operating system, in this case, Windows 10 Mobile, and it needs to convert the document by enabling editing. Once this is done macros are enabled. However, Windows 10 Mobile received end of life status in January of this year, so it is unlikely that this would be the reason for not being able to view the document and a clear attempt to trick users. Windows declared their Mobile OS end of life due to a failure to gain any significant market share over its competitors.
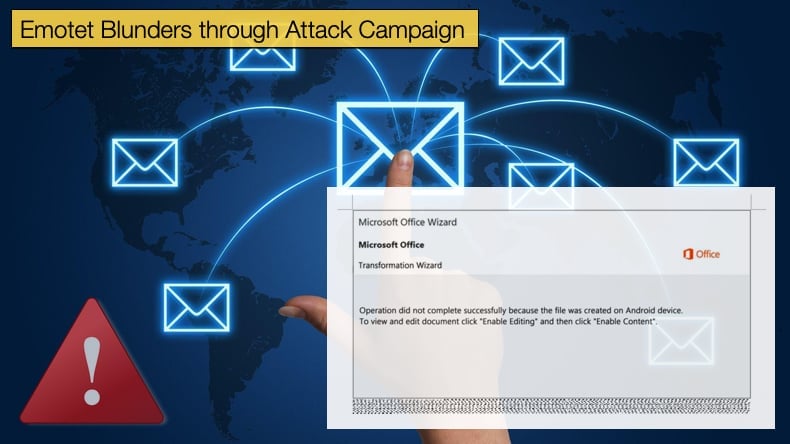
Emotet’s operators made yet another error in using outdated text to “inform” the user that the document could not be opened. With both mistakes, it makes it a lot easier to spot the attempt at infecting the machine and for security teams to quickly inform employees as to what to look for. This further decreases the chances of pulling off a successful infection.
Change in Tactics
To further hamper the chances of a successful Emotet infection Microsoft took to Twitter to inform users of the campaign and include several screenshots to make detecting a spam email even easier. Microsoft’s Security Intelligence Team noted,
“Emotet joined the password-protected attachment bandwagon with a campaign starting Friday. The campaign slowed down over the weekend (typical of Emotet) but was back today in even larger volumes of emails in English, as well as in some European languages.…Earlier this week we started seeing a spike in the use of password-protected documents in multiple malware campaigns, including Trickbot. These documents are attached to emails that use varying social engineering lures like the typical "order", "invoice", "documents"…If the recipient enters the password, which is in the email body, the document tricks users into enabling the malicious macro by claiming the that the file was created on “Windows 10 Mobile” (Friday’s campaign) or “Android device” (today’s campaign)…”
It may be that either the increased coverage of the campaign or by realizing it themselves, but changes were made to the content of the emails. No longer did newer email samples reference Windows 10 Mobile but had begun saying the document was created on Android rather. Despite the change of supposed OS the messages used are obsolete dating back to 2013 and 2014. This can further be used to detect suspicious emails and prevent infection. Emails have been seen written in English, French, and Italian with themes varying from meetings and order confirmations to reports. All of which are compressed into a password-protected archive. After recipients extracted the attached document using the password provided in the email body and opened it, they launched the embedded malicious macro that downloads the Emotet payload.
TrendMicro has confirmed that the campaign which Cryptolaemus has code-named Operation Zip Lock, is using password-protected compressed files to bypass security measures. It also appears that Emotet’s operators have gone all-in on the campaign with more and more resources being dedicated to the campaign. Researchers have split Emotet activity in “Epochs'' with there currently being three epochs known to be used. Each epoch can be differentiated in that different resources and infrastructure are used. Since the start of September, the campaign utilized only two of the three epochs. The third was added to the campaign on September 14.
Further, it would seem that it is not only Emotet looking to spread itself via compressed password protected files. Reports have emerged that TrickBot, the banking trojan turned do it all malware has also started distributing such files this time with a COVID-19 lure as well as the typical abuse of so-called invoices, documents, and orders.
Another Page in the Book of Emotet
First identified by security researchers in 2014 Emotet, like TrickBot, was originally developed as a banking trojan. Over the years its creators have added the ability to drop other strains of malware onto infected machines, further updates saw Emotet be upgraded to use infected machines to assist in sending spam emails. This effectively turned Emotet from banking trojan to botnet overnight. In providing a more detailed summary of Emotet, Malwarebytes has seen the malware evolve from the banking trojan to what it is now by adopting a range of tactics. These include:
“Emotet uses several tricks to try and prevent detection and analysis. Notably, Emotet knows if it’s running inside a virtual machine (VM) and will lay dormant if it detects a sandbox environment, which is a tool cybersecurity researchers use to observe malware within a safe, controlled space.
Emotet also uses C&C servers to receive updates. This works in the same way as the operating system updates on your PC and can happen seamlessly and without any outward signs. This allows the attackers to install updated versions of the software, install additional malware such as other banking Trojans, or to act as a dumping ground for stolen information such as financial credentials, usernames and passwords, and email addresses.”
Emotet began drawing a lot of attention, and the ire of banks, in 2017 when the first US banks were added to the victims' list. The campaign which targeted US banks shred many similarities to an earlier campaign targeting UK banks but rather than malicious Microsoft Office documents as seen in the latest campaign malicious PDF files were used. These files once opened and a link clicked on a JavaScript file would be executed which would communicate to a command and control server.
Once this communication channel was opened the malware payload would be dropped. Again in 2019, Emotet would see a significant change in tactics and begin to target healthcare organisations and using Internet of Things devices to remain undetected on victims’ networks for extended periods. These events showed the InfoSec community that the malware’s operators were willing to change tactics quickly. This was not only done with speed but was effective and kept those defending networks constantly on the back foot. Another point to be made is that it showed that Emotet was willing to target anyone irrelevant to the various economic sectors.
Also worth mentioning is Emotet’s partnership with ransomware operators. In July 2019, Emotet successfully infiltrated Lake City in Florida’s network. Once the initial compromise was done a piece of ransomware was dropped onto the network which successfully encrypted files. It cost the city nearly half a million USD to recover from the incident. The incident showed another side to hackers in that Emotet initially dropped TrickBot which then dropped the Ryuk ransomware. This showed a high level of co-operation amongst groups some assumed to be rivals. At least the latest campaign shows that the group is not free from making mistakes but this is by far the last time we hear from Emotet and one of the few featuring a mistake.
Share:

Karolis Liucveikis
Experienced software engineer, passionate about behavioral analysis of malicious apps
Author and general operator of PCrisk's News and Removal Guides section. Co-researcher working alongside Tomas to discover the latest threats and global trends in the cyber security world. Karolis has experience of over 8 years working in this branch. He attended Kaunas University of Technology and graduated with a degree in Software Development in 2017. Extremely passionate about technical aspects and behavior of various malicious applications.
PCrisk security portal is brought by a company RCS LT.
Joined forces of security researchers help educate computer users about the latest online security threats. More information about the company RCS LT.
Our malware removal guides are free. However, if you want to support us you can send us a donation.
DonatePCrisk security portal is brought by a company RCS LT.
Joined forces of security researchers help educate computer users about the latest online security threats. More information about the company RCS LT.
Our malware removal guides are free. However, if you want to support us you can send us a donation.
Donate
▼ Show Discussion