Get free scan and check if your device is infected.
Remove it nowTo use full-featured product, you have to purchase a license for Combo Cleaner. Seven days free trial available. Combo Cleaner is owned and operated by RCS LT, the parent company of PCRisk.com.
What is TrickBot?
TrickBot is trojan-type malware designed to steal users' private data. Research shows that, in most cases, developers proliferate TrickBot using spam emails, however, it might also be distributed using fake Adobe Flash Player updates. This virus was first identified in late 2016 targeting various financial institutions, banks, and credit card providers (for more information click here).
In late 2017, cryptomining became very popular, and for this reason, TrickBot was updated and now also targets cryptowallets. Besides, TrickBot can spread itself further and infect as many computers as possible.
TrickBot malware overview
This malware essentially hijacks web browsers and modifies websites displayed by them. The sites are modified such that entered logins and passwords are recorded and sent to a remote server controlled by cyber criminals. This is a significant issue regarding users' privacy.
By stealing login details and passwords for cryptocurrency wallets, PayPal, bank accounts, and other personal accounts, cyber criminals cause serious problems and transfer money without consent, thus leading to financial loss. More recent versions of TrickBot are capable of locking victim's computer screen.
Cyber criminals can use this feature to force people to pay a ransom so they could access their computers again. Also, this virus is capable of hijacking various applications (such as WinSCP, Microsoft Outlook, Filezilla, Mozilla Firefox, Google Chrome, Microsoft Edge, Internet Explorer) and stealing saved passwords, autofill data and a number of other information types.
It is designed to steal this data with a implemented module called "pwgrab". Aside from stealing credentials, TrickBot also records information relating to web browsing (e.g., history, cookies, and so forth), as well as the system itself (CPU, operating system, running processes, etc.). To steal data from browsers it uses a cookies-grabbing module.
This module is used to steal web browser cookies which help cyber criminals to create a better profile of each victim and to optimize the attack in a better way. Newer versions of TrickBot are also capable of stealing PIN codes from people who use services of Verizon Wireless, T-Mobile, and Sprint.
This feature allows cyber criminals to take control over victim's phone numbers. To achieve it, TrickBot alters web content of visited websites (like Verizon Wireless) using new dynamic webinjects. It can add or remove various fields, change texts and so on, depending on what cyber criminals willing to achieve.
It can also be used to get access to previously infected networks (bots) and allows other threat actors to further infiltrate the network and drop their payloads.
Note that this virus is capable of updating itself after the infection. In other words, each victim (if there's an Internet connection, of course) will have the newest version of TrickBot, no matter when this malware has firstly infiltrated the system.
This malware should be eliminated immediately, however, TrickBot is notorious for hiding itself - on initial inspection, it is virtually impossible to determine if this malware is present. It's detection avoiding capabilities have increased significantly. Besides, it is capable of disabling Windows Defender.
Fortunately, most legitimate anti-virus suites are capable of detecting and removing TrickBot. If you have recently downloaded/opened suspicious email attachments or used third party Adobe Flash Player update tools, you should immediately use a reputable anti-virus software to scan the entire system and eliminate all listed threats.
In addition, check the list of installed applications/browser plug-ins and uninstall any suspicious entries (fake updaters are also likely to include potentially unwanted adware-type programs).
| Name | TrickBot malware |
| Threat Type | Trojan, Password stealing virus, Banking malware, Spyware |
| Detection Names | Avast (Win32:Malware-gen), BitDefender (Trojan.Agent.CWSV), ESET-NOD32 (Win32/TrickBot.AJ), Kaspersky (Trojan.Win32.Mansabo.awr), Full List (VirusTotal) |
| Symptoms | Trojans are designed to stealthily infiltrate victim's computer and remain silent thus no particular symptoms are clearly visible on an infected machine. |
| Distribution methods | Infected email attachments, malicious online advertisements, social engineering, software cracks. |
| Damage | Stolen banking information, passwords, identity theft, victim's computer added to a botnet. |
| Malware Removal (Windows) |
To eliminate possible malware infections, scan your computer with legitimate antivirus software. Our security researchers recommend using Combo Cleaner. Download Combo CleanerTo use full-featured product, you have to purchase a license for Combo Cleaner. 7 days free trial available. Combo Cleaner is owned and operated by RCS LT, the parent company of PCRisk.com. |
Similar malware examples
TrickBot shares many similarities with Adwind, Pony, FormBook, and a number of other trojans. Although these viruses work in different ways, their purpose is identical - to gather personal information. Malware such as TrickBot is released simply to generate revenue - developers literally steal other users' money.
Potentially unwanted programs are also designed to help developers generate passive revenue - most deliver intrusive advertisements (via the "Pay Per Click" [PPC] advertising model), cause unwanted redirects (promotion of dubious sites), and gather data (e.g., IP addresses, websites visited, pages viewed, search queries, etc.).
PUPs are also known to offer various 'useful features', however, these claims are merely attempts to give the impression of legitimacy - they deliver no real value for regular users.
How did TrickBot infect my computer?
As mentioned above, TrickBot is promoted using spam emails and fake Adobe Flash Player updaters.
Spam emails contain various malicious attachments (e.g., PDF files, MS Office documents, etc.) By opening these attachments, users execute scripts that stealthily download and install viruses such as TrickBot, whilst Fake updaters infect the system by exploiting outdated software bugs/flaws or simply downloading and installing malware/PUPs rather than updates.
Essentially, the main reasons for computer infections are poor knowledge and careless behavior.
How to avoid installation of malware?
To prevent computer infections, be very cautious when browsing the Internet. Think twice before opening email attachments. If you suspect that an email is irrelevant and is sent from a suspicious/unrecognizable email address, immediately delete it and certainly do NOT open any attachments.
Note that cyber criminals use various tactics to make these emails seem legitimate - they imitate bank notifications, job offers, and so on. Therefore, if you receive any unexpected/suspicious emails, delete them immediately. As with updating software, remember that criminals proliferate malware via fake updaters.
Therefore, software should be updated using implemented functions or tools provided by the official developer only. The same rule applies to software download/installation. Criminals monetize third party downloaders/installers by promoting ("bundling") PUPs. Therefore, software should be downloaded from official sources only, using direct download links.
When downloading, opt-out of all additionally-included programs and if you are unable to do so, cancel the entire process. The key to computer safety is caution. If your computer is already infected with TrickBot, we recommend running a scan with Combo Cleaner Antivirus for Windows to automatically eliminate infiltrated malware.
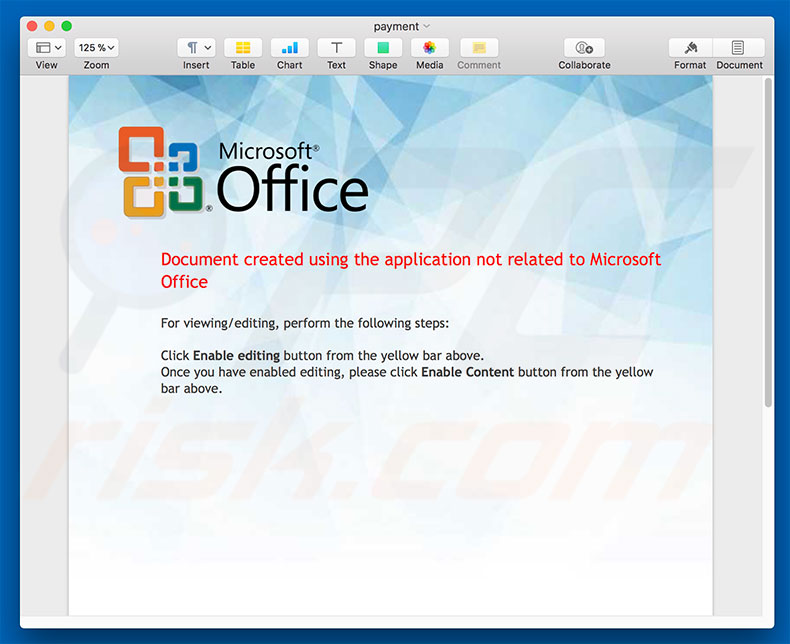
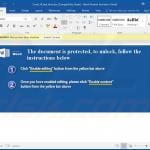
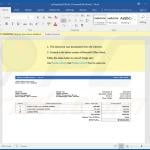
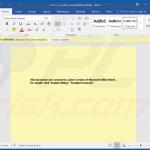
Update September 13, 2019 - Cyber criminals have recently started using an interesting technique to distribute TrickBot trojan. They use email spam campaigns to spread a malicious Microsoft Word document. The tricky part is that the content of the said document is JavaScript code - it contains tens of thousands of JavaScript code lines within.
In order to hide them, cyber criminals change the text color to white and, since the background is also white, the text becomes invisible, thereby tricking inattentive users into thinking that the document is empty.
Once opened, the document runs a macro command which extracts the its content to a local file and the entire JavaScript code (which injects TrickBot into the system) is eventually executed. Now it is worth mentioning that even though there are thousands of code lines, only a small portion is actually used.
Cyber criminals simply insert lots of code lines with an intention of making it troublesome for malware researchers to analyze the code.
Screenshot of a malicious MS Word document containing JavaScript code (notice the underlined "invisible" words at the bottom of the document):
Update November 25, 2019 - TrickBot trojan has been recently updated and now contains a new feature allowing cyber criminals to steal OpenSSH private keys, as well as OpenVPN passwords and configuration files. At this current moment, however, TrickBot's data exfiltration function is not fully developed, meaning that this stolen information is not sent anywhere.
Therefore, it is safe to assume that developers are merely testing this function. One way or another, the problem will probably be fixed eventually and the data will actually be sent to the Command & Control (C&C) server.
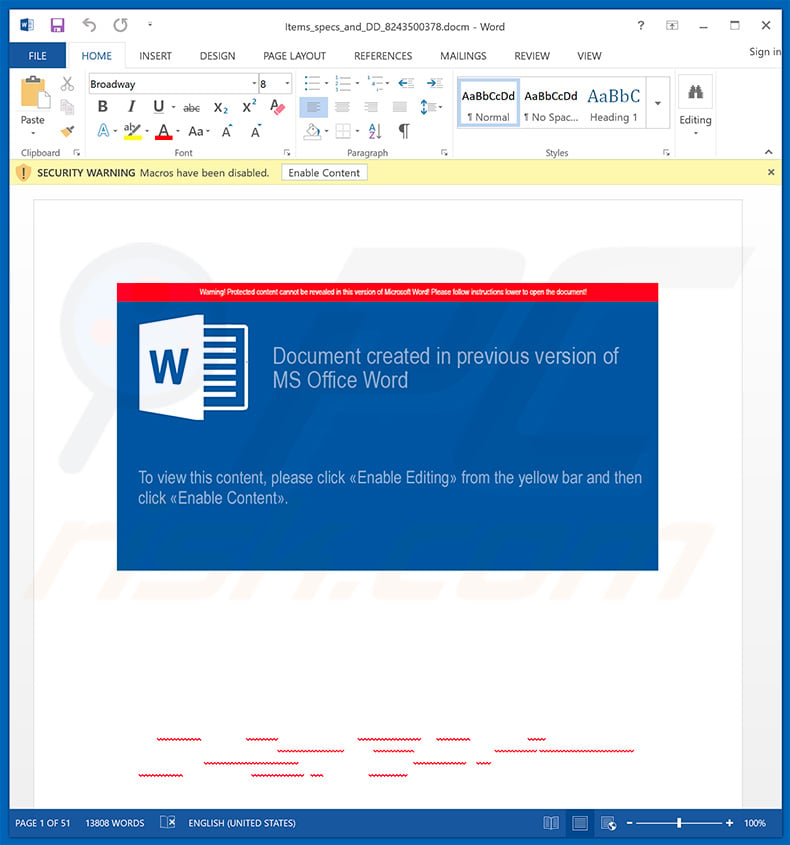
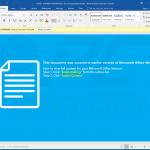
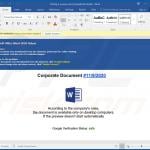
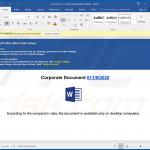
Update December 10, 2019 - Cyber criminals have recently started yet another email spam campaign which is used to spread TrickBot trojan. In this case, crooks use hijacked .edu email addresses to send deceptive emails containing notifications/details regarding some sort of "annual bonuses". These emails encourage user to download a form, print it and sign it.
It also contains download links. However, the problem is that these links eventually lead to a malicious executable which drops TrickBot into the system. In order to avoid email security detections, crooks employ a variety of legitimate services to hide traces of the malicious executable.
Once opened, the file displays a pop-up message encouraging users to update Microsoft Word or to either run open the document on another computer. At the same time, the executable drops a payload - TrickBot trojan. You can find more information regarding this spam campaign in Sergiu Gatlan's article.
Example of an email from this spam campaign:
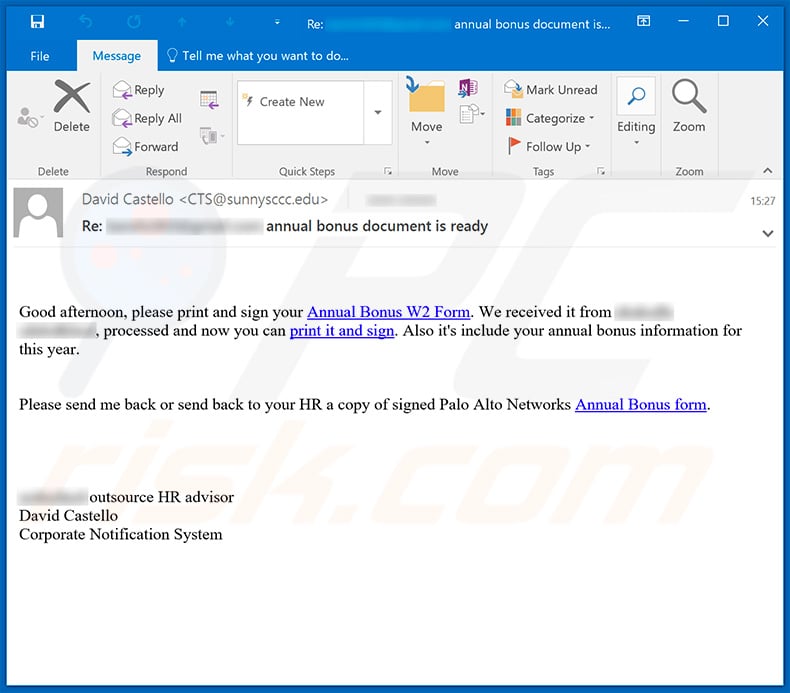
Text presented within this email:
Subject: Re: ******* annual bonus document is ready
Good afternoon, please print and sign your Annual Bonus W2 Form. We received it from ******* ***********, processed and now you can print it and sign. Also it's include your annual bonus information for this year.
Please send me back or send back to your HR a copy of signed Palo Alto Networks Annual Bonus form.
******* outsource HR advisor
David Castello
Corporate Notification System
Update January 14, 2020 - The developers of TrickBot trojan have recently developed a post-exploitation tool called PowerTrick. The purpose of this tool is to inject TrickBot (and other malware) into all computers that are connected to the same network as the infected host is connected to.
PowerTrick infects systems via reverse shell - it performs a number of PowerShell commands that download and install certain malicious software (e.g., TrickBot Anchor Malware, More_Eggs JavaScript backdoor) into the systems. You can find more information in Bleeping Computer's article written by Lawrence Abrams.
Update January 17, 2020 - Cyber criminals have released yet another update of TrickBot trojan. It has been implemented with a feature that allows to bypass Windows UAC (User Account Control) and run the malicious executable with administrative privileges, without prompting the user and asking for a permission. Depending on the infiltrated system (Windows 7 or Windows 10), TrickBot uses different methods to bypass the Windows UAC. You can find more information in Bleeping Computer's article written by Lawrence Abrams.
Update January 27, 2020 - Crooks have released yet another updated version of TrickBot trojan and it is now capable of stealing databases from Windows Active Directory (AD).
In order to steal AD databases stored on compromised Windows domain controllers TrickBot abuses the "Install from Media" (ifm) command, which allows it to dump an entire database (as well as some Registry hives straight into the %TEMP% folder.
This data is then compressed and uploaded to a remote server controlled by the cyber criminals. You can find detailed explanation in Lawrence Abrams' article on Bleeping Computer.
Update January 31, 2020 - TrickBot has started using yet another technique to bypass Windows UAC (User Account Control) and run with administrative privileges without user's consent on computers running Windows 10 operating system. To achieve this, TrickBot now abuses Wsreset (wsreset.exe) - a legitimate Microsoft tool designed to reset Windows Store cache.
TrickBot forces the Wsreset tool to execute a command stored in Windows Registry which executes the malicious executable without prompting the message which asks for user's permission to run the app.
By doing so, TrickBot sneaks into the system without performing any actions that would draw user's attention. More information about this TrickBot's method can be found in Arnold Osipov's article on Morphisec.
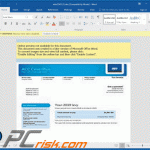
Update March 09, 2020 - Cyber criminals are taking advantage of the recent outbreak of the Coronavirus. They're continually starting various email spam campaigns which are used for phishing and malware-distributing purposes. The list of distributed malware is long. Yet it also includes TrickBot.
Here's an example of a Italy-targeted Coronavirus-related spam campaign which spreads TrickBot via malicious attachment - Microsoft Word document:
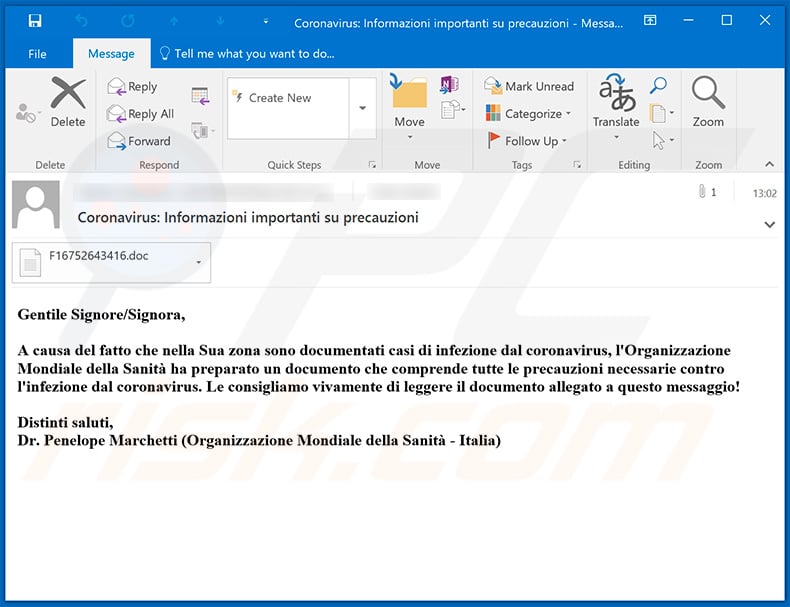
Text presented within this email:
Subject: Coronavirus: Informazioni importanti su precauzioni
Gentile Signore/Signora,
A causa del fatto che nella Sua zona sono documentati casi di infezione dal coronavirus, l'Organizzazione Mondiale della Sanità ha preparato un documento che comprende tutte le precauzioni necessarie contro l'infezione dal coronavirus. Le consigliamo vivamente di leggere il documento allegato a questo messaggio!
Distinti saluti,
Dr. Penelope Marchetti (Organizzazione Mondiale della Sanità - Italia)
Update March 18, 2020 - TrickBot has recently received yet another update. One of its modules is designed to bruteforce Remote Desktop Protocol (RDP) connections on targets selected by cyber criminals. Research results show that most of the victims are based in US and Hong Kong.
It is also worth noting that most of the targeted victims are telecommunication service providers. Since the mentioned attacks are selective, it is very common for cyber criminals of any kind to target various companies and businesses. That's because victims of this type are way more juicy - revenue generated from a single home user is way lower than that of a huge company.
Update March 19, 2020 - TrickBot and Emotet developers are taking advantage of the current situation regarding Coronavirus in order to make the malicious files "less detectable".
What cyber criminals do is insert quotes from various speeches about the Coronavirus (e.g., quoting Donald Trump, CNN articles, etc.) into the description of each malicious file. By doing so, crooks decrease the chance of anti-virus suites detecting malware. You can find more details in Lawrence Abram's article posted in Bleeping Computer.
Update March 25, 2020 - The developers of TrickBot trojan have recently released a malicious Android application (named TrickMo by IBM X-Force researchers) which allows them to bypass two-factor authentication (2FA). At this current moment the malicious application disguises as the "Avast Security Control" application or either "Deutsche Bank Security Control" utility.
The application is designed to gather data which ultimately allows cyber criminals to bypass 2FA and, thus, enables them to perform fraudulent transactions. This means that having such malicious app installed on your device may lead to huge financial losses. You can find more details in Sergiou Gatlan's article posted in Bleeping Computer.
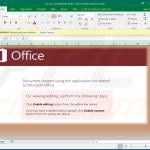
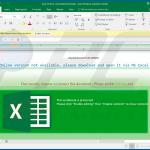
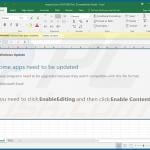
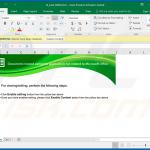
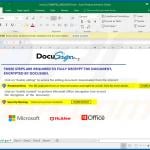
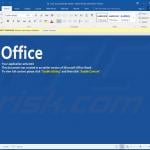
Examples of malicious Microsoft Excel documents designed to inject TrickBot trojan into the system:
Examples of malicious Microsoft Word documents designed to inject TrickBot trojan into the system:
Update June 23, 2020 - TrickBot trojan has been observed being used to deliver the data-encrypting Ryuk ransomware. The deployment of said ransomware is not immediate, typically taking two weeks following the initial TrickBot infection (in some researched cases Ryuk was injected after several months).
During this period, the trojan investigates the infected network in order the evaluate the potential worth of the target. If the gathered data proves to be of interest and significant value, Ryuk ransomware is loaded. More information concerning these developments can be in found in an article by Ionut Ilascu on Bleeping Computer.
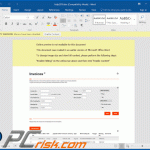
Example of yet another spam email used to spread TrickBot trojan via attached MS Excel document:
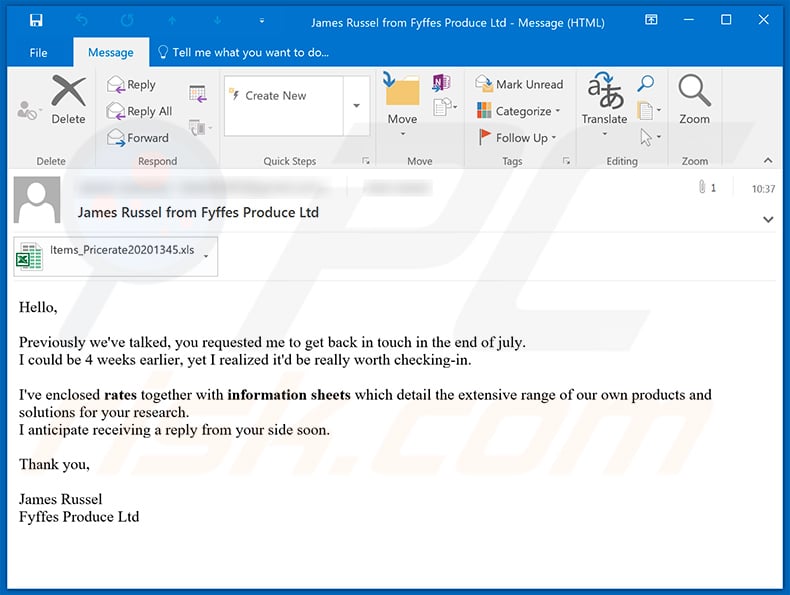
Text presented within:
Subject: James Russel from Fyffes Produce Ltd
Hello,
Previously we've talked, you requested me to get back in touch in the end of july.
I could be 4 weeks earlier, yet I realized it'd be really worth checking-in.I've enclosed rates together with information sheets which detail the extensive range of our own products and solutions for your research.
I anticipate receiving a reply from your side soon.Thank you,
James Russel
Fyffes Produce Ltd
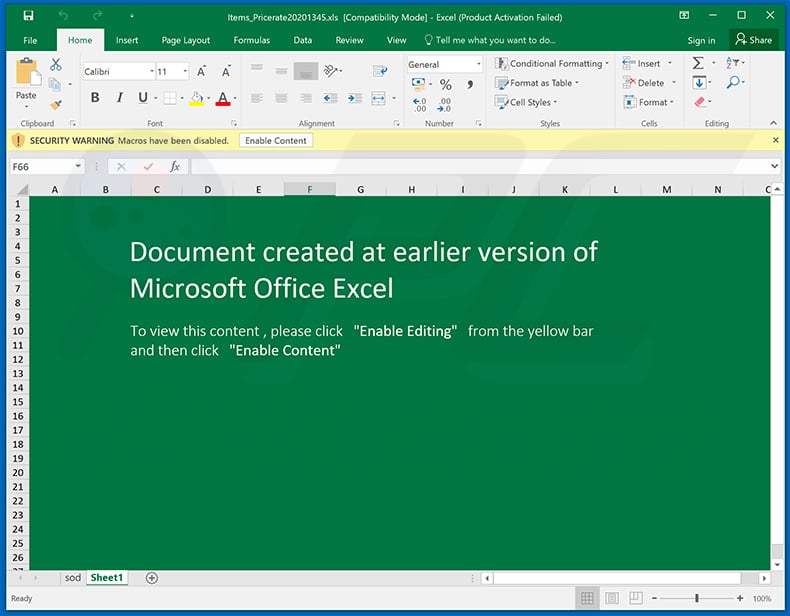
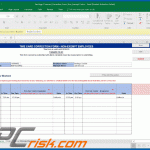
Screenshot of the attached MS Excel document:
Update July 13, 2020 - The developers of TrickBot have accidentally "released" a test version of this malware which warns victims about the infection.
After infiltrating the system, this TrickBot's sample opens a browser and connects to a local network in order to open an HTML file, which delivers a message warning victims about some stolen information. This message indicates presence of TrickBot malware.
Screenshot of TrickBot's warning message in localhost:
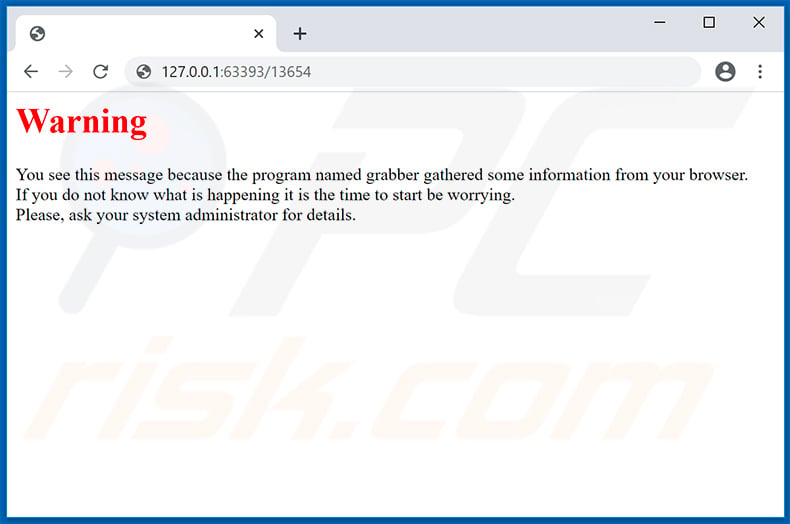
Text presented within:
Warning
You see this message because the program named grabber gathered some information from your browser.
If you do not know what is happening it is the time to start be worrying.
Please, ask your system administrator for details.
Update September 16, 2020 - TrickBot authors now have created a new TrickBot model called BazarLoader which injects its payload into a certain system process (e.g.m "svchost", "explorer.exe" or “cmd.exe".).
For persistence this loader creates a registry key in system Registry. Like most malware loaders, BazarLoader it is used to load a second-stage malware payload onto the infected computer. It downloads malicious files from .bazar domain C2 servers.
Yet another example of a spam email used to spread a malicious MS Excel document that injects TrickBot trojan into the system:
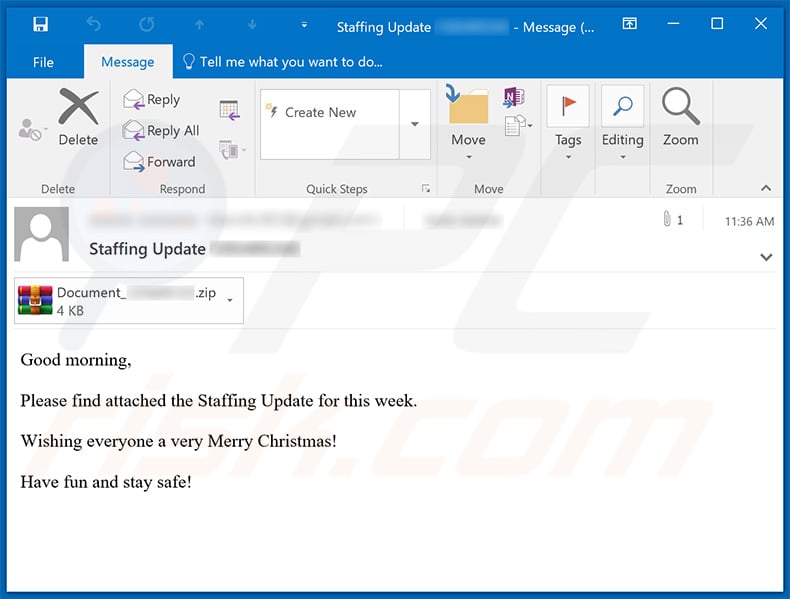
Text presented within:
Subject: Staffing Update ********
Good morning,
Please find attached the Staffing Update for this week.
Wishing everyone a very Merry Christmas!
Have fun and stay safe!
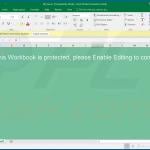
Screenshot of the attached document:
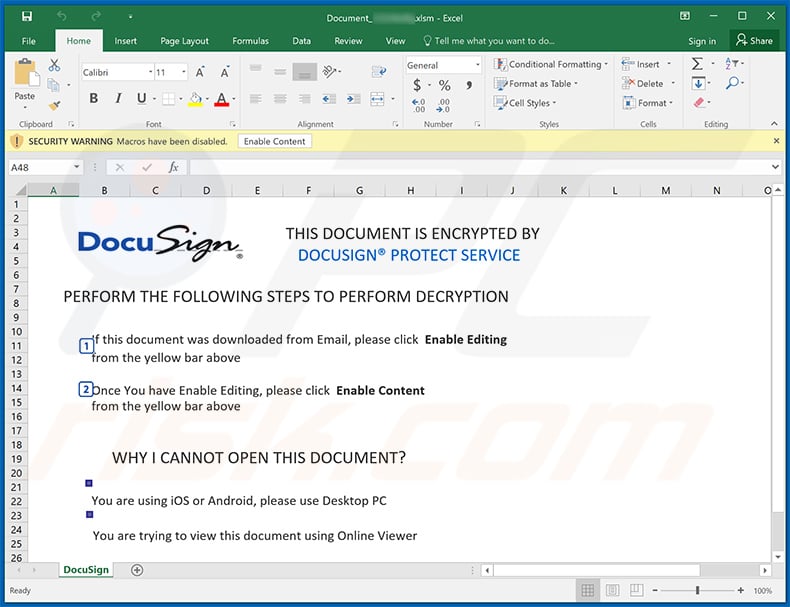
Instant automatic malware removal:
Manual threat removal might be a lengthy and complicated process that requires advanced IT skills. Combo Cleaner is a professional automatic malware removal tool that is recommended to get rid of malware. Download it by clicking the button below:
DOWNLOAD Combo CleanerBy downloading any software listed on this website you agree to our Privacy Policy and Terms of Use. To use full-featured product, you have to purchase a license for Combo Cleaner. 7 days free trial available. Combo Cleaner is owned and operated by RCS LT, the parent company of PCRisk.com.
Quick menu:
- What is TrickBot?
- STEP 1. Manual removal of TrickBot malware.
- STEP 2. Check if your computer is clean.
How to remove malware manually?
Manual malware removal is a complicated task - usually it is best to allow antivirus or anti-malware programs to do this automatically. To remove this malware we recommend using Combo Cleaner Antivirus for Windows.
If you wish to remove malware manually, the first step is to identify the name of the malware that you are trying to remove. Here is an example of a suspicious program running on a user's computer:
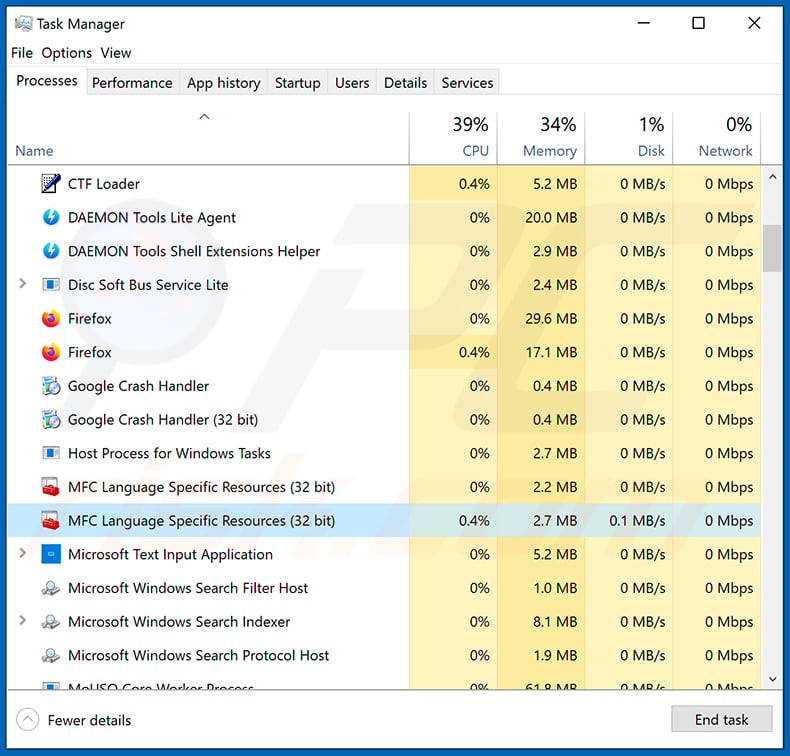
If you checked the list of programs running on your computer, for example, using task manager, and identified a program that looks suspicious, you should continue with these steps:
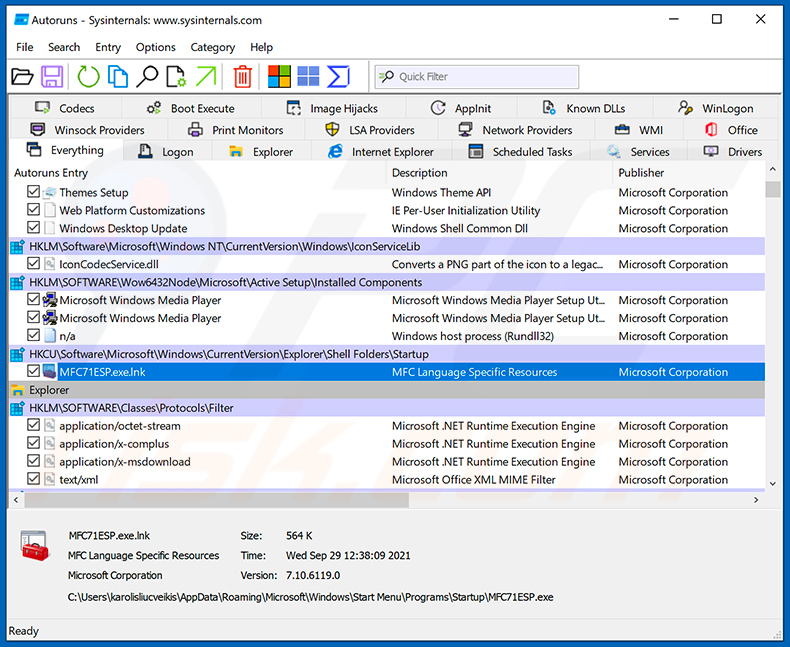
 Download a program called Autoruns. This program shows auto-start applications, Registry, and file system locations:
Download a program called Autoruns. This program shows auto-start applications, Registry, and file system locations:
 Restart your computer into Safe Mode:
Restart your computer into Safe Mode:
Windows XP and Windows 7 users: Start your computer in Safe Mode. Click Start, click Shut Down, click Restart, click OK. During your computer start process, press the F8 key on your keyboard multiple times until you see the Windows Advanced Option menu, and then select Safe Mode with Networking from the list.
Video showing how to start Windows 7 in "Safe Mode with Networking":
Windows 8 users: Start Windows 8 is Safe Mode with Networking - Go to Windows 8 Start Screen, type Advanced, in the search results select Settings. Click Advanced startup options, in the opened "General PC Settings" window, select Advanced startup.
Click the "Restart now" button. Your computer will now restart into the "Advanced Startup options menu". Click the "Troubleshoot" button, and then click the "Advanced options" button. In the advanced option screen, click "Startup settings".
Click the "Restart" button. Your PC will restart into the Startup Settings screen. Press F5 to boot in Safe Mode with Networking.
Video showing how to start Windows 8 in "Safe Mode with Networking":
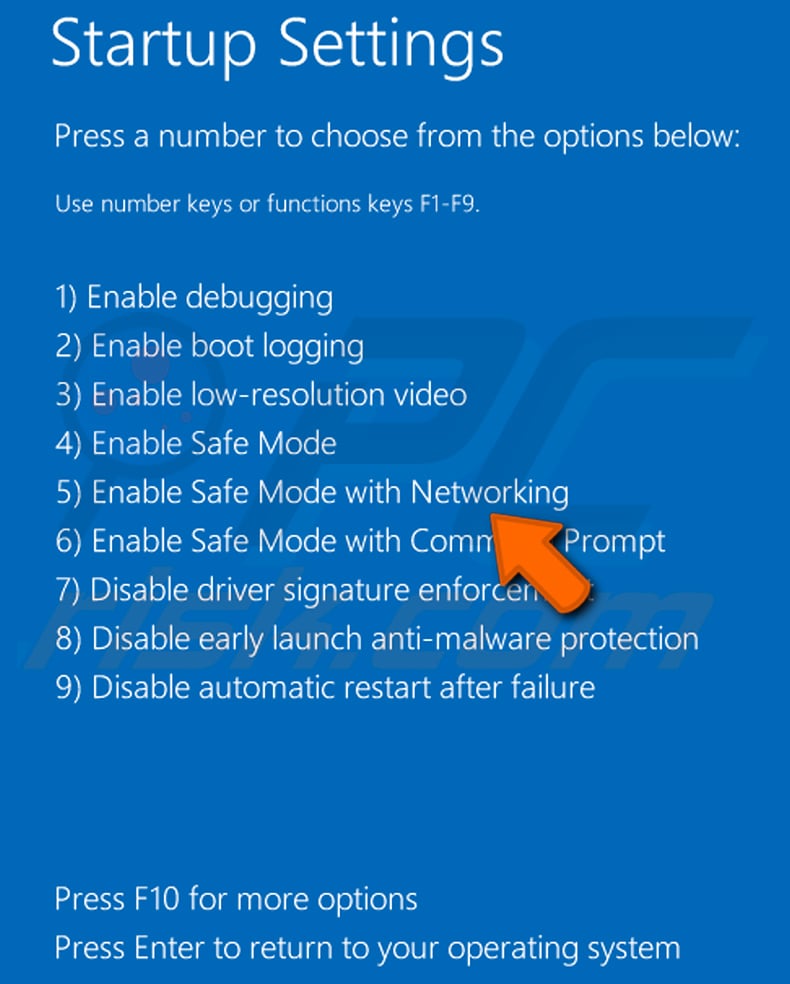
Windows 10 users: Click the Windows logo and select the Power icon. In the opened menu click "Restart" while holding "Shift" button on your keyboard. In the "choose an option" window click on the "Troubleshoot", next select "Advanced options".
In the advanced options menu select "Startup Settings" and click on the "Restart" button. In the following window you should click the "F5" button on your keyboard. This will restart your operating system in safe mode with networking.
Video showing how to start Windows 10 in "Safe Mode with Networking":
 Extract the downloaded archive and run the Autoruns.exe file.
Extract the downloaded archive and run the Autoruns.exe file.
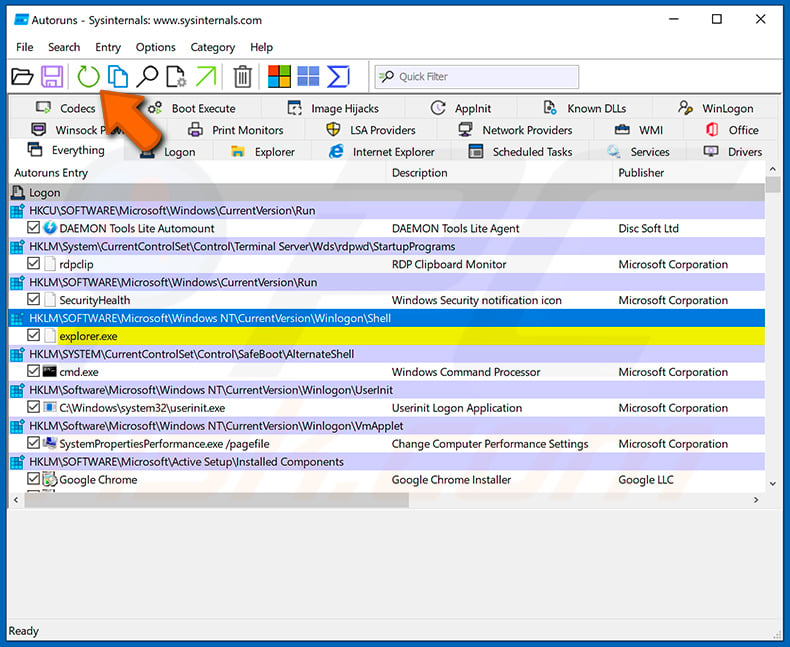
 In the Autoruns application, click "Options" at the top and uncheck "Hide Empty Locations" and "Hide Windows Entries" options. After this procedure, click the "Refresh" icon.
In the Autoruns application, click "Options" at the top and uncheck "Hide Empty Locations" and "Hide Windows Entries" options. After this procedure, click the "Refresh" icon.
 Check the list provided by the Autoruns application and locate the malware file that you want to eliminate.
Check the list provided by the Autoruns application and locate the malware file that you want to eliminate.
You should write down its full path and name. Note that some malware hides process names under legitimate Windows process names. At this stage, it is very important to avoid removing system files. After you locate the suspicious program you wish to remove, right click your mouse over its name and choose "Delete".
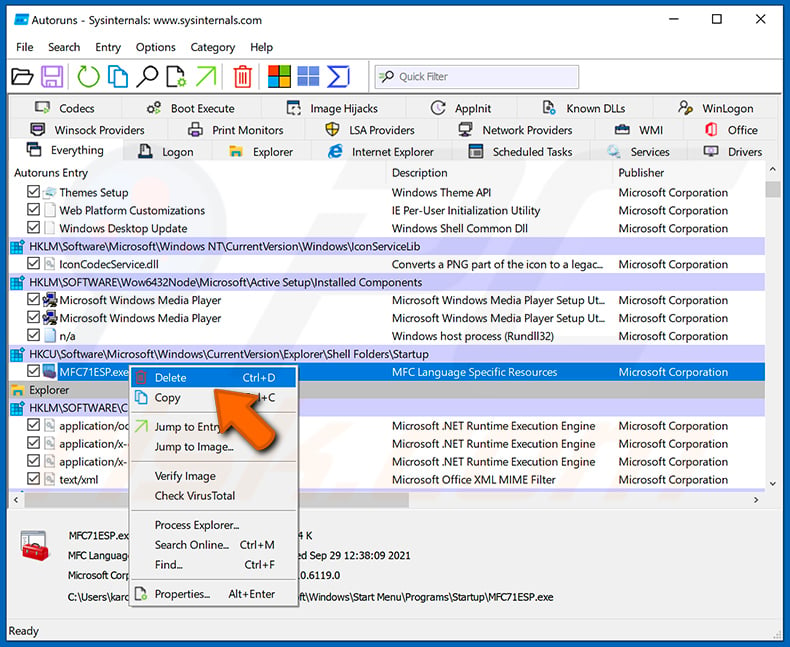
After removing the malware through the Autoruns application (this ensures that the malware will not run automatically on the next system startup), you should search for the malware name on your computer. Be sure to enable hidden files and folders before proceeding. If you find the filename of the malware, be sure to remove it.
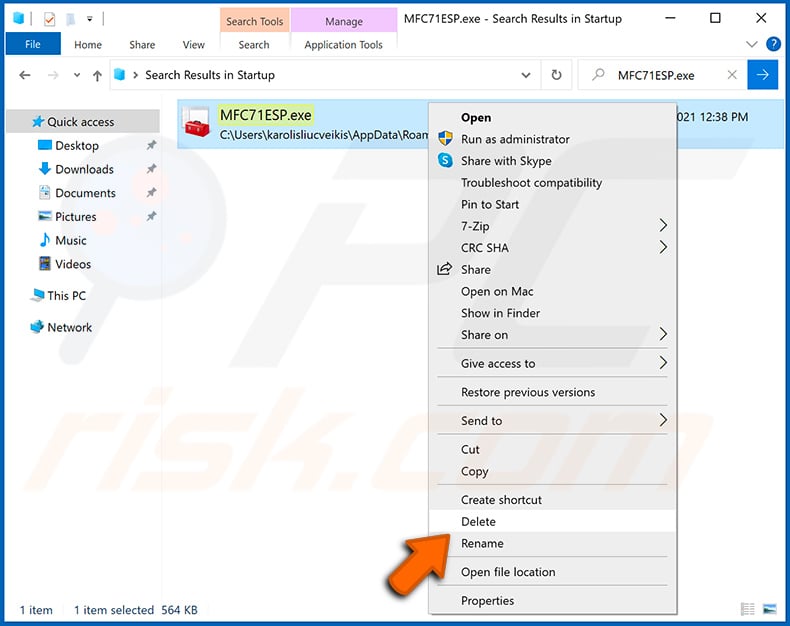
Reboot your computer in normal mode. Following these steps should remove any malware from your computer. Note that manual threat removal requires advanced computer skills. If you do not have these skills, leave malware removal to antivirus and anti-malware programs.
These steps might not work with advanced malware infections. As always it is best to prevent infection than try to remove malware later. To keep your computer safe, install the latest operating system updates and use antivirus software. To be sure your computer is free of malware infections, we recommend scanning it with Combo Cleaner Antivirus for Windows.
Frequently Asked Questions (FAQ)
My computer is infected with TrickBot malware, should I format my storage device to get rid of it?
Most malicious programs can be removed without restoring to formatting.
What are the biggest issues that TrickBot malware can cause?
The threats posed by an infection depend on the malware's functionalities and the cyber criminals' goal. TrickBot is a versatile piece of software with sophisticated data-stealing capabilities, and it can download/install additional malware (e.g., trojans, ransomware, etc.). Generally, high-risk infections can lead to decreased system performance or failure, data loss, severe privacy issues, financial losses, and identity theft.
What is the purpose of TrickBot malware?
Most infections are motivated by financial gain. However, cyber criminals can also use malware to amuse themselves, carry out personal grudges, disrupt processes (e.g., websites, services, companies, etc.), and even launch politically/geopolitically motivated attacks.
How did TrickBot malware infiltrate my computer?
Malware is primarily spread via drive-by downloads, spam emails/messages, online scams, malvertising, untrustworthy download sources (e.g., freeware and third-party websites, P2P sharing networks, etc.), illegal activation tools ("cracks"), and fake updates. Furthermore, some malicious programs can self-proliferate via local networks and removable storage devices (e.g., external hard drives, USB flash drives, etc.).
Will Combo Cleaner protect me from malware?
Yes, Combo Cleaner is capable of detecting and eliminating nearly all known malware infections. It must be mentioned that running a full system scan is essential since high-end malicious software usually hides deep within systems.
Share:

Tomas Meskauskas
Expert security researcher, professional malware analyst
I am passionate about computer security and technology. I have an experience of over 10 years working in various companies related to computer technical issue solving and Internet security. I have been working as an author and editor for pcrisk.com since 2010. Follow me on Twitter and LinkedIn to stay informed about the latest online security threats.
PCrisk security portal is brought by a company RCS LT.
Joined forces of security researchers help educate computer users about the latest online security threats. More information about the company RCS LT.
Our malware removal guides are free. However, if you want to support us you can send us a donation.
DonatePCrisk security portal is brought by a company RCS LT.
Joined forces of security researchers help educate computer users about the latest online security threats. More information about the company RCS LT.
Our malware removal guides are free. However, if you want to support us you can send us a donation.
Donate

▼ Show Discussion