Emotet surges back to Life
After an extended hiatus of nearly five months, Emotet has surged back to life with a new campaign sending out malicious emails to users worldwide. Historically the malware has been spread via malicious emails containing documents, often Word or Excel being the favored platforms to exploit, containing malicious macros that will install Emotet on the machine. From there the malware can include the infected machine into the malware’s botnet to send more malicious emails out, spread laterally across a network, and be used to drop other types of malware. Emotet is known to drop ransomware as well as info-stealing malware once it has infected a machine.
In an article published by Bleeping Computer and a technical blog post published by Malwarebytes details of the new campaign have been released to the public. In the first-mentioned article, researchers confirmed that Emotet activity seemed to fall off the map on February 7, 2020. An Emotet tracking group Cryptolaemus noted that while there was no spamming activity for the 5 month period, the malware’s developers were actively adding malicious modules to the code. It was also noted that a couple of days before July 17, the day activity surged back to life, a few test emails were distributed across the network.
Once malicious activity did start it was clear that Emotet was back to its old tricks of sending emails masquerading as reply-chain, shipping, payment, and invoice emails delivering malicious Word documents. Security researcher and Emotet expert Joseph Roosen (https://twitter.com/JRoosen) further noted that the malicious documents were using old URLs associated with those behind the malware. Roosen also discovered new URLs were being used that link to commonly hacked WordPress sites.
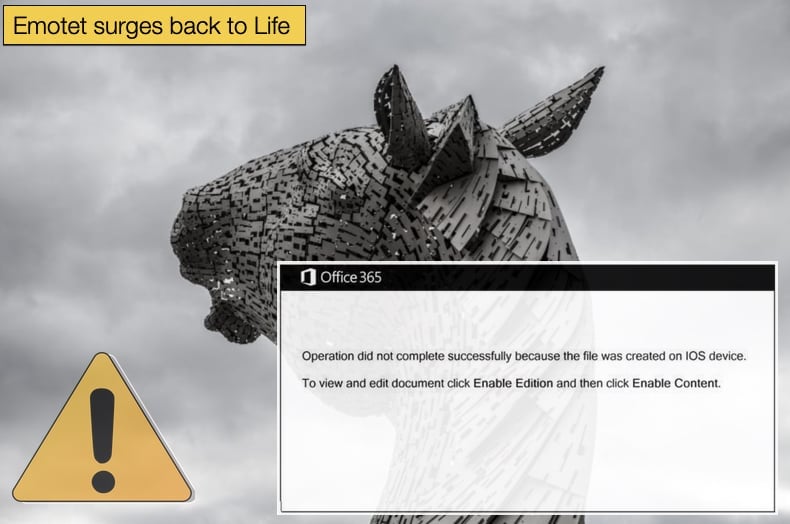
How Emotet is distributed is just part of the story, the other part being how the malware executes, installs, and carries out its mission are the other parts of the chapter. As mentioned above the malware pivots around malicious Microsoft Office documents once the emails have been sent. The document will contain malicious macros that if enabled by the end-user the infection process will begin in earnest. This is the way it is advised never to enable macros, as it will prevent malware infection and all the stress associated with it. To get end-users to enable macros the user is presented with an alert stating that the document cannot be opened as it was created on an iOS device and the user must “Enable Edition” to open the document. It should read “Enable Editing” so this is a clear typo on the half of the attacker, but typos and grammatical errors are often seen in cyberattacks and spam email campaigns, this doesn’t mean they won’t be successful.
If the user enables editing, or in this case “Enable Edition”, a PowerShell command will be executed that will download and install the actual malware payload which contains Emotet. The malware is downloaded from the hacked WordPress websites alluded to above and after several stages, the malware is stored in the following location, %UserProfile%\AppData\Local\dwmapi\certmgr.exe. The malware can also remain persistent on an infected machine by creating an autorun Registry Key, meaning it will run even after the computer has been restarted. Once this is complete Emotet will then run through its code modules to steal the victim’s email address so that it can be used to spread more spam emails, or it can spread laterally across a network if it finds itself on an enterprise network for example.
The Dreaded Emotet
Often when writing about an infamous malware re-emerging onto the threat landscape it is tempting to portray the malware a horror villain returning to take their toll. Malwarebytes used the headline “It’s baaaack…” to show it was not only this writer tempted to do the same thing. While the temptation is there, it is not always warranted and can come off as being alarmist. However, in the case of Emotet, the comparisons to a horror villain may be warranted. The above paragraphs showed how Emotet operates but little as to the damage it can cause, or at the very least allow to cause. As to the potential to cause damage Emotet is not the one that often makes the headlines, rather it is the malware that it drops later that hog the limelight. Emotet is well-known for distributing both TrickBot, a banking trojan, and Ryuk, one of the most prevalent ransomware threats enterprises have to try and deal with.
In the last quarter of 2018, an Emotet campaign was seen dropping TrickBot. The campaign would see hundreds of thousands of spam emails being sent to initially drop Emotet, those infected would later find themselves infected by TrickBot and have sensitive personal and banking information liable to land in the wrong hands. Why the developers of TrickBot would want to partner with Emotet can be confidently assumed. The partnership allows TrickBot to infect more devices with a successful malware that gets it’s foot in the backdoor effectively. Another reason is Emotet’s dwell time, or put differently how long it can stay on the infected machine. In many cases, Emotet was undetected for days, while in others it was months. This gives a partnering malware family multiple opportunities to strike on an already compromised machine. This makes defending against Emotet a critical consideration when defending against cyber threats in general. To this extent, researchers advised the following during the 2018 campaign regarding best defensive practices, and they are still pertinent today,
“Staying safe from the current Emotet campaign is not particularly difficult since it is spread through malicious spam. However, users who don’t have a keen eye or little training in common phishing techniques might fall victim. One of the easiest ways to stay protected against Emotet is simply to keep a keen eye out for shady emails, especially if they have one of the subject lines mentioned above, include an Office document or PDF attachment, and come from unrecognizable email addresses. However, when it comes to social engineering, there is no guarantee someone won’t be fooled.”
Emotet’s Relationship with Ryuk
Ryuk was first detected in August 2018, where it was abusing RDP connections to infect machines. It is one of the major contributors to the phenomenon of human-operated ransomware targeting major corporations and demanding exorbitant ransoms in return from victims. When Emotet, TrickBot, and Ryuk are used in conjunction with one another, Emotet acts as the dropper for the other two, as previously mentioned. Once TrickBot has stolen the information it hunts for, Ryuk is then dropped so that it can steal files, to be released if no ransom is paid, and encrypt data rendering business operations severely stunted. In some instances the Ryuk strain is downloaded directly from known TrickBot command and control servers. The reasons for the relationship between Emotet and Ryuk are exactly the same as for TrickBot, or at the very least can be assumed to be so with a high degree of confidence.
It is also important to note that this relationship is not one based on the goodwill of one party. It is a business relationship based off of profit and being mutually beneficial to the parties involved. Emotet will receive a cut of profits or be paid for renting out their botnet by either or both TrickBot and Ryuk. In providing useful information about the relationship and steps to take to prevent falling victim to this triple threat Intel471 advises,
“The first order of business for any organization is to have good security hygiene, including but not limited to ongoing security monitoring, a detection strategy, and response and recovery. There are at least two opportunities to stop both Emotet and TrickBot before a Ryuk outbreak occurs. The first is to stop Emotet from downloading TrickBot. The second is to stop TrickBot from spreading across the network, or at least stop it from communicating back to its command and control servers.
Once TrickBot has identified a domain controller on the network, the network defender is racing against the clock. If the infected machine is on a small-to-medium-sized business network, there is a very good chance threat actors will attack the domain controller and deploy Ryuk. Unfortunately, defensive measures such as anti-virus agents are unlikely to stop Ryuk, since the attacker can easily disable them (i.e., via a group policy object (GPO).”
This partnership has come to symbolize the difficulty of facing modern threats without sufficient and clear threat intelligence. A victim may have successfully thwarted an attack, or at least thinking they did, only to find funds missing from a bank account and important data encrypted.
Share:

Karolis Liucveikis
Experienced software engineer, passionate about behavioral analysis of malicious apps
Author and general operator of PCrisk's News and Removal Guides section. Co-researcher working alongside Tomas to discover the latest threats and global trends in the cyber security world. Karolis has experience of over 8 years working in this branch. He attended Kaunas University of Technology and graduated with a degree in Software Development in 2017. Extremely passionate about technical aspects and behavior of various malicious applications.
PCrisk security portal is brought by a company RCS LT.
Joined forces of security researchers help educate computer users about the latest online security threats. More information about the company RCS LT.
Our malware removal guides are free. However, if you want to support us you can send us a donation.
DonatePCrisk security portal is brought by a company RCS LT.
Joined forces of security researchers help educate computer users about the latest online security threats. More information about the company RCS LT.
Our malware removal guides are free. However, if you want to support us you can send us a donation.
Donate
▼ Show Discussion