Emotet is Back
Once referred to as the “world’s most dangerous malware,” after almost a year hiatus Emotet is back. This is not the first time the infamous botnet has resurfaced after a long hiatus.
This time the reemergence of the botnet has happened after significant law enforcement efforts bring down the botnet’s infrastructure.
If you thought horror movies had the sole rights to bad sequels, malware developers may have them beat.
The discovery was made by Cyber WTF, who posted the following in a blog post,
“On Sunday, November 14, at around 9:26pm UTC we observed on several of our Trickbot trackers that the bot tried to download a DLL to the system. According to internal processing, these DLLs have been identified as Emotet. However, since the botnet was taken down earlier this year, we were suspicious about the findings and conducted an initial manual verification. Please find the first results and IOCs below. Currently, we have high confidence that the samples indeed seem to be a re-incarnation of the infamous Emotet. We are still conducting more in-depth analyses to raise the confidence even further. New information will be provided as they become available.”
Subsequently, this discovery has been confirmed by security researchers at both AdvIntel and Cryptolaemus. Further, it would appear that the new incarnation of Emotet has adopted a new encryption method, and rather than redistributing itself it is relying on TrickBot for new infections.
Emotet is essentially piggybacking on TrickBOt infections by being dropped onto already compromised machines. Speaking to ZDNet James Shank, chief architect of community services and senior security evangelist at Team Cymru, a cybersecurity company that was among those that helped disrupt Emotet in January, noted,
“The relationship between this new variant and the old Emotet shows code overlap and technique overlap...It will take some time to see how Emotet rebuilds, and whether it can become the 'world's most dangerous malware' again. You can be sure that those that helped to take it down the first time are keeping watch. It doesn't come as a surprise that Emotet resurfaced. In fact, more may wonder why it took so long,”
Reputation Earned
Given that Emotet is still in the rebuilding phase, some might question if this is as big of a deal as media houses are making it out to be. Back in January 2021 news broke that Emotet operations had been disrupted.
The law enforcement operation was a collaborative effort between authorities in the Netherlands, Germany, the United States, the United Kingdom, France, Lithuania, Canada, and Ukraine to disrupt operations and seize infrastructure. The operation was two years in the making but that does not describe why Emotet was deemed such a high-value target for law enforcement.
Emotet began life in 2014 as a banking trojan, malware designed to steal banking credentials, but soon evolved to become the go-to solution for other cybercriminals. The botnet infrastructure of the malware was primarily used to create back doors onto infected machines that would allow other threat actors to drop varying strains of malware including ransomware.
In summary, Emotet operators sold high-level access to infected machines to other threat actors. For several malware strains, Emotet served as their primary vehicle for gaining initial access to a victim.
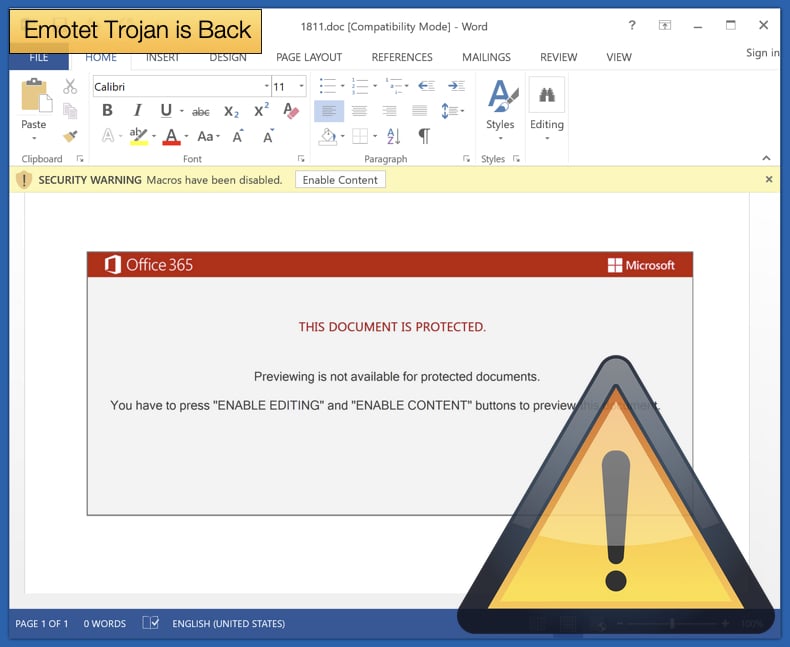
Emotet’s favored distribution method was through malicious Microsoft Word documents. Europol notes,
“The EMOTET group managed to take email as an attack vector to a next level. Through a fully automated process, EMOTET malware was delivered to the victims’ computers via infected e-mail attachments. A variety of different lures were used to trick unsuspecting users into opening these malicious attachments. In the past, EMOTET email campaigns have also been presented as invoices, shipping notices and information about COVID-19.”
The emails contained malicious Word documents that were either served as attachments or downloaded via clickable links within the email itself. Once the document was opened the user would be asked to “enable macros” which would enable the malicious code hidden in the document to be run and the infection chain would begin.
The enabling of macros would often be done under the auspices of a thin veil of legitimacy. For example, an alert would say that an update needed to be downloaded to view the document. If the user clicked through, rather than an update, macros would be enabled.
Emotet’s functionality as being used as a backdoor for hire reached its most dangerous level when it partnered with TrickBot and the ransomware gang behind the Ryuk ransomware strain. Emotet would compromise the victim then drop TrickBot onto the compromised machine. TrickBot would then steal banking credentials and other sensitive information.
Once TrickBot’s operations were completed, Ryuk would be dropped. From there the machine would have its data encrypted and a ransom note instructing the victim how to pay the ransom and receive a decryption key would be displayed. This combo of malware infections beginning with Emotet is one of the reasons the malware was labeled as one of the world’s most dangerous strains.
Over the years the infrastructure employed by Emotet grew into a sophisticated network of hundreds of servers located around the world.
Certain servers would only be used for specific tasks including functions as varied as managing the computers of the infected victims, spreading to new ones, serving other criminal groups, and ultimately making the network more resilient against takedown attempts. To disrupt Emotet operations Europol noted,
“To severely disrupt the EMOTET infrastructure, law enforcement teamed up together to create an effective operational strategy. It resulted in this week’s action whereby law enforcement and judicial authorities gained control of the infrastructure and took it down from the inside. The infected machines of victims have been redirected towards this law enforcement-controlled infrastructure. This is a unique and new approach to effectively disrupt the activities of the facilitators of cybercrime.”
It is hoped that law enforcement and security researchers, now armed with a treasure trove of information relating to Emotet’s past tactics and techniques, can keep the spread of the malware down to a minimum so that it cannot reach its previous threat level.
Share:

Karolis Liucveikis
Experienced software engineer, passionate about behavioral analysis of malicious apps
Author and general operator of PCrisk's News and Removal Guides section. Co-researcher working alongside Tomas to discover the latest threats and global trends in the cyber security world. Karolis has experience of over 8 years working in this branch. He attended Kaunas University of Technology and graduated with a degree in Software Development in 2017. Extremely passionate about technical aspects and behavior of various malicious applications.
PCrisk security portal is brought by a company RCS LT.
Joined forces of security researchers help educate computer users about the latest online security threats. More information about the company RCS LT.
Our malware removal guides are free. However, if you want to support us you can send us a donation.
DonatePCrisk security portal is brought by a company RCS LT.
Joined forces of security researchers help educate computer users about the latest online security threats. More information about the company RCS LT.
Our malware removal guides are free. However, if you want to support us you can send us a donation.
Donate
▼ Show Discussion