Powerful Adware Variant Has a New Trick
A new version of the persistent and powerful adware program known as Shopperz has been spotted in the wild and this new version has security researchers wondering what other tricks may be in store for PC users in the future due to the sophistication of this new adware variant. Sometimes also referred to as Groover, Shopperz works by injecting ads into a PC users’ Web traffic using methods that are considered by security researchers to be both malicious and deceptive. Some of the techniques used by Shopperz to take over an infected PC include installing an extension in both Firefox and Internet Explorer and the creation of a Windows service that makes it extremely difficult for victims to remove the add-ons from both popular Web browsers. One such service is even designed to operate in Safe Mode - a Windows boot option that is often used to clean a PC of malware. Shopperz is also capable of creating a rogue Layered Service Provider (LSP) within the Window’s network stack.
This feature allows the malicious software to inject advertisements into Web traffic when a victim uses any Web browser. In other words, even if a victim is able to successfully remove the adware extensions from both Internet Explorer and Firefox, Shopperz can still inject ads into the browsing session using the LSP functionality. What makes Shopperz truly unique and dangerous, however, is the malware’s use of DNS hijacking. Basically DNS hijacking allows the adware to trick an infected PC into accessing servers that are controlled by the hackers behind this campaign when victims attempt to access legitimate websites. The Domain Name System (DNS) is the Internet’s phone book and is used to translate domain names written in English into the numerical Internet Protocol (IP) addresses that are actually used by computers when communicating with one another. Normally, a computer relies on DNS servers operated by the ISP to resolve host names but before doing this, the PC will check a list of static DNS entries. These entries are stored locally on the PC in a file called “hosts.”
If you consider DNS to be the Internet phone book, the hosts file would be akin to speed dial. Various malware threats often add rogue entries to the hosts file as a way to hijack requests to and from legitimate websites and since this tactic is so common within the malware world, the hosts file is often one of the first files checked by security tools when attempting to eliminate a malware infection.
This is where the hackers behind the Shopperz campaign have created a new technique in an attempt to hide the DNS hijacking capabilities of the adware from security tools that specifically look for changes in the hosts file.

Shopperz leaves the original hosts file, which is located in system32\drivers\etc\, and creates a copy of this file under a different name inside a directory with a path that has the same number of characters as the original hosts file. The malware then replaces every instance of a Windows system file known as dnsapi.dll. This file is used by the operating system to parse the hosts file with the modified version of the hosts file containing the rogue entries necessary for DNS hijacking to work. The rogue hosts file created using this trick contains DNS entries for connect.facebook.com, www.google-analytics.com, and google-analytics.com. These are legitimate domain names that are used by many Web-based services but because the hosts file contains rogue DNS entries, the victims are redirected to servers controlled by the cybercriminals behind the Shopperz campaign. This allows the hackers to inject ads into any Web page opened by the infected PC that uses the services found at the aforementioned legitimate domain names.
Although adware does not typically pose a huge threat to sensitive personal and financial data found on a PC infected with Shopperz or another adware variant, the additional bandwidth used to inject these rogue ads into an otherwise legitimate browsing session can make PCs run slower than normal.
Also, the fact that all DNS requests are routed through servers controlled by hackers instead of the legitimate DNS servers operated by the victim’s ISP, there is a possibility that these hijacked DNS requests could actually be used to redirect victims to phishing websites designed to steal login credentials for popular social media sites such as Facebook and Twitter. The only way to properly detect and remove a Shopperz infection is to use the Windows System File Checker SFC) tool. This tool is part of the Windows OS and is designed to identify and repair system files that have been modified. This tool needs to be run from the command line with administrative privileges. Instructions for running SFC can be found in the Microsoft Knowledge Base. The best way to prevent a Shopperz infection from occurring in the first place is to ensure that the Windows OS is updated regularly as well as all third party applications.
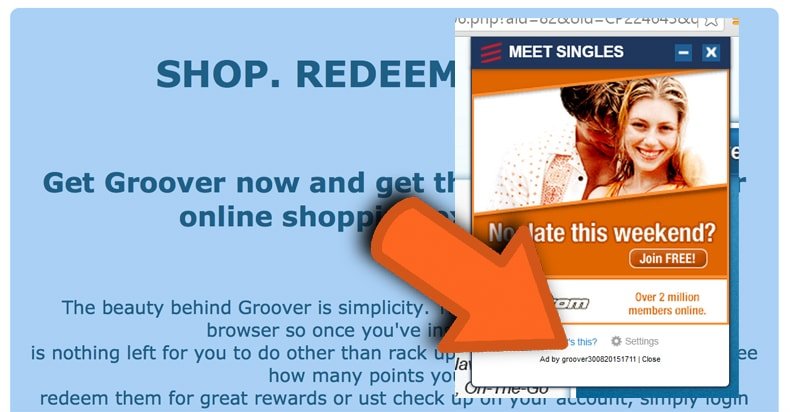
Shopperz is typically installed on a target PC via drive-by download from a malicious website that uses vulnerabilities in popular Web browser plugins including Java, Adobe Flash, and Microsoft Silverlight. These plugins should be removed from the PC is possible or at the very least, disabled until needed for some specific activity.
Shopperz has also been known to spread via email attachments as part of a spam email campaign in which the attachments appear to be invoices, past due bills, or other similar subjects that instill a sense of urgency in the recipient.
Once these attachments are opened, however, Shopperz is covertly installed on the PC and due to the clandestine nature of the DNS hijacking technique used in this latest campaign, most antivirus solutions will not detect the infection until it is too late (if the antivirus software is capable of detecting Shopperz at all). Although Shopperz doesn’t put your personal information immediately at risk, the hackers behind this campaign could begin using DNS hijacking techniques for other, more nefarious purposes in the near future. Only time will tell if this new technique was designed simply as a way to avoid detection for the existing adware or if DNS hijacking is merely the beginning of an entirely new malware campaign.
Share:

Karolis Liucveikis
Experienced software engineer, passionate about behavioral analysis of malicious apps
Author and general operator of PCrisk's News and Removal Guides section. Co-researcher working alongside Tomas to discover the latest threats and global trends in the cyber security world. Karolis has experience of over 8 years working in this branch. He attended Kaunas University of Technology and graduated with a degree in Software Development in 2017. Extremely passionate about technical aspects and behavior of various malicious applications.
PCrisk security portal is brought by a company RCS LT.
Joined forces of security researchers help educate computer users about the latest online security threats. More information about the company RCS LT.
Our malware removal guides are free. However, if you want to support us you can send us a donation.
DonatePCrisk security portal is brought by a company RCS LT.
Joined forces of security researchers help educate computer users about the latest online security threats. More information about the company RCS LT.
Our malware removal guides are free. However, if you want to support us you can send us a donation.
Donate
▼ Show Discussion