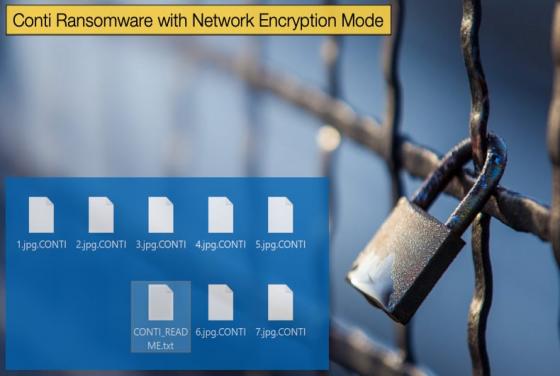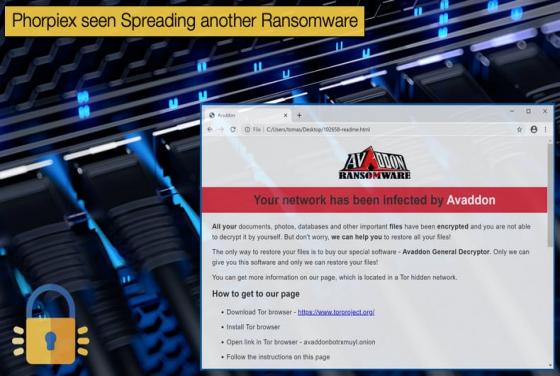

Phorpiex seen Spreading another Ransomware
The last time this publication covered Phorpiex it was seen distributing the Nemty across its botnet infrastructure. In the past the botnet was seen distributing GandCrab, however, researchers discovered that the botnet was seen distributing a new ransomware called Avaddon during the preceding month