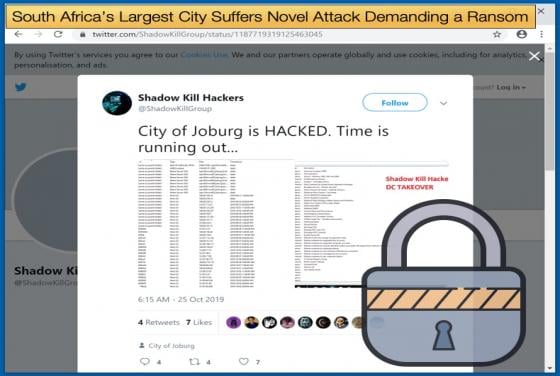
North Korean Malware Found in Indian Nuclear Power Station
On Monday 28, 2019, news began emerging on Twitter that the Kudankulam Nuclear Power Plant (KNPP) might have been infected with a dangerous strain of malware. Pukhraj Singh, a former security analyst for India's National Technical Research Organization (NTRO) and researcher closely following the mat