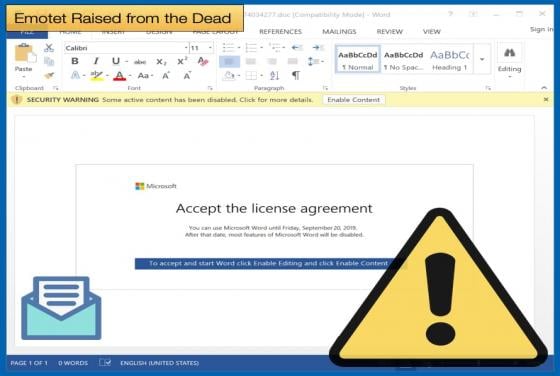
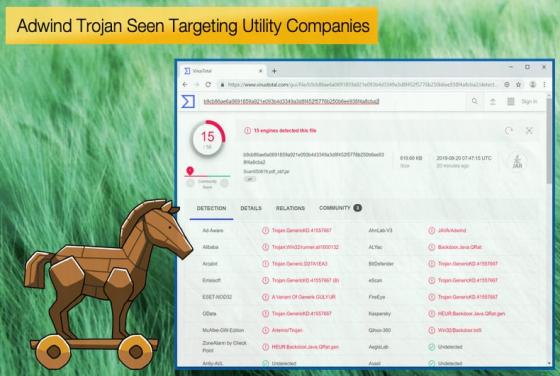
New Hacking Group Seen Laying Foundation for Supply Chain Attack
A new hacking group has emerged from the shadows, dubbed Tortoiseshell by researchers, the group has been seen targeting IT companies. The reason behind it, it appears the group is laying the foundation for a supply chain attack. Such attacks can be a nightmare for organizations as they often target