GandCrab Version 5.1 Rewrites the Rules
The malware authors behind the GandCrab ransomware are continually giving law enforcement and security researcher headache after a headache. Not only does the author’s continually evolve the malware to include newer features, but they also keep evolving their business, if it can be called one, model. Despite setbacks, the group seems to come back stronger. In a combined effort Europol and Bitdefender released a decryption tool for many of the versions of GandCrab seen in the wild. Such a concerted effort to thwart GandCrab operators left them bruised but not out. The latest version, 5.1, has no decryption as of yet, although a removal guide is available on this platform. Further, the business model has now included measures to help dishonest data recovery firms hide costs to bump up their margins.
In a recent report published by security firm, Coveware illustrated how dishonest data-recovery firms have found a business ally in the malware authors behind GandCrab. In essence, the GandCrab TOR website allows dishonest data-recovery companies to hide the actual ransom cost from victims. This is done in a variety of ways but one such method includes the awarding of coupons to recovery firms who frequently access GandCrab's TOR site.
Another method open to exploitation involves the use of a private and hidden chat function. Which can be used, by no stretch of the imagination, to hide the final cost of the GandCrab decryption process from its customers.
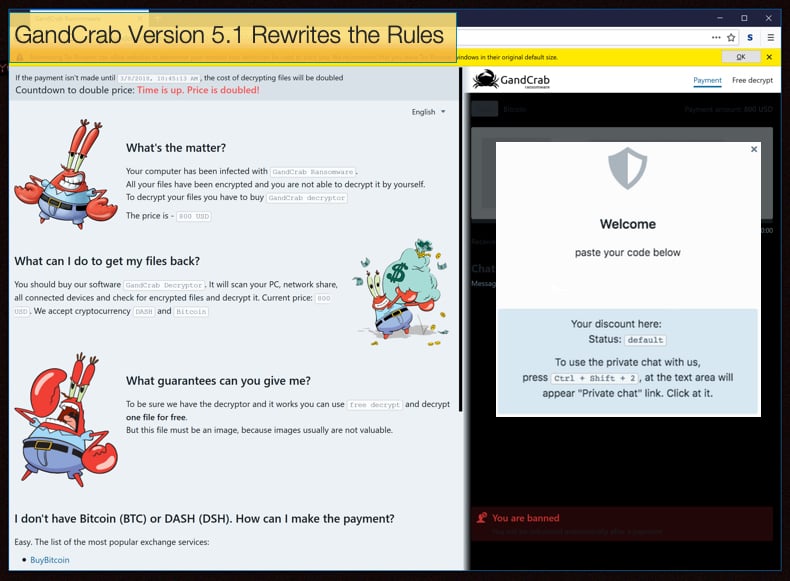
To enable this private chat feature one needs simply to follow the below procedure:
- While in the plain chat, you click on the chat box and press SHIFT+CTRL+2
- Click on the Private link that appears in the chat box
- Enter promo code and slide the toggle, and, if the code is right, the chat will be tied to that promo code and can't be seen by the normal client.
Then if are one of those favored data-recovery firms and have received a coupon it can be entered by entering Shift+Ctrl+1, the user will then be presented with a dialog box where the coupon’s code can be entered. This allows such firms the ability to reduce the price of the ransom amount by whatever discount, giving access to the victim to see one price, while the shady recovery firm can pay a lower one increasing profit margins, albeit dishonestly. According to Coveware,
“After entering the code, the applicable discount is displayed and the USD ransom amount on the payment pages is automatically adjusted. Discounts range from 5-20% depending on the size of the ransom.”
It is not only Coveware warning users about dishonest data-recovery firms. Checkpoint published an article detailing a real-world example involving a Russian company called Dr. Shifro. The company advertised itself has been able to decrypt encrypted data caused by a variety of ransomware families. Researchers at Checkpoint, however, were able to prove otherwise and discovered that Dr. Shifro was lying to his customers. He was actually just paying hackers bitcoin for decryption keys without client consent or knowledge. The security researchers were posing as both customer and hacker, thus been able to confirm both sides of Dr. Shifro’s scam. This further proves that it is better not to pay the ransom and rather backup data regularly.
RaaS Business Model
Since 2018 GandCrab has been an incredibly active ransomware strain. Its activity is proportional to its popularity amongst cybercriminals. This popularity has seen an increase in ransom amounts charged to victims with ransoms often reaching the 3000 USD mark in cryptocurrency been demanded. This is possible because of the Ransomware as a Business (RaaS) model employed by the malware authors. RaaS typically is a perversion of the Software as a Service model and involves malware authors providing an online platform used by “customers” for the deployment of ransomware to a victim’s computer. Such operations lower the technical knowledge bar needed by cybercriminals to conduct ransomware campaigns for a price of course.
Another factor which enables the ransomware’s popularity amongst hackers is the list of features and use of numerous exploit kits in order to gain a foothold on the targeted system. As of the time of writing Gandcrab can be spread via malvertising campaigns, and by exploiting the Struts, JBoss, Weblogic, and Apache Tomcat vulnerabilities. Further, it camouflages itself as an apparently harmless app or as a cracked utility in an attempt to bypass a systems security, or GandCrab can be used in a brute force attack when stealth fails. That is not all GandCrab offers, the ransomware can be distributed by exploiting RIG, GrandSoft, and Fallout via automated malware campaigns, as well as deploying other malware strains such as Emotet and Vidar to carry out its illegal mission.
This evolution is giving researchers and law enforcement headache upon a headache in the sense that it increases the sheer amount of ransomware IDs detected on each infected system. In a report concluded that,
“Prior to the exploit kits gaining popularity, a single attack would typically have one or two unique IDs (file extensions). Each ID had its own TOR page, with a ransom amount scaled to the perceived value of the underlying machine. Since the more automated exploit kits have gained popularity, the number of unique IDs in a single infection has skyrocketed. Some victims have dozens of ID’s to contend with. Each ID tends to have the same ransom amount, indicating a ‘spray and pray’ methodology vs a more surgical attack.”
It was believed that ransomware and its operators had adopted a more focussed approach, only going after specific targets. This is true to a large extent but it is equally true that the original “spray and pray” approach is still effective even if business models need to be adjusted in order to develop new partnerships with those sharing the same immoral ideals.
Share:

Karolis Liucveikis
Experienced software engineer, passionate about behavioral analysis of malicious apps
Author and general operator of PCrisk's News and Removal Guides section. Co-researcher working alongside Tomas to discover the latest threats and global trends in the cyber security world. Karolis has experience of over 8 years working in this branch. He attended Kaunas University of Technology and graduated with a degree in Software Development in 2017. Extremely passionate about technical aspects and behavior of various malicious applications.
PCrisk security portal is brought by a company RCS LT.
Joined forces of security researchers help educate computer users about the latest online security threats. More information about the company RCS LT.
Our malware removal guides are free. However, if you want to support us you can send us a donation.
DonatePCrisk security portal is brought by a company RCS LT.
Joined forces of security researchers help educate computer users about the latest online security threats. More information about the company RCS LT.
Our malware removal guides are free. However, if you want to support us you can send us a donation.
Donate
▼ Show Discussion