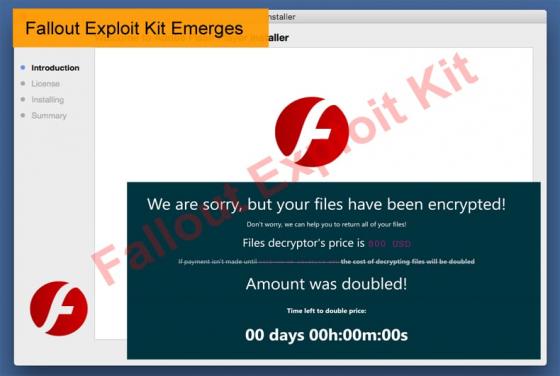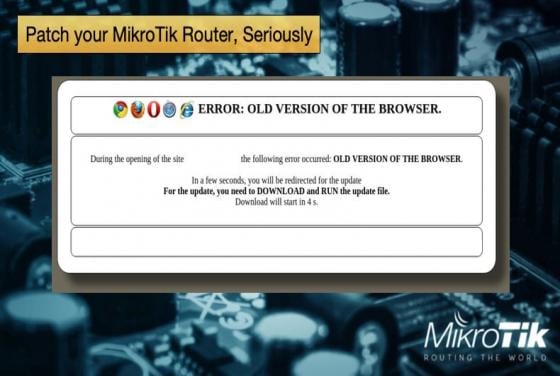

Patch your MikroTik Router, Seriously
Security experts often sound like the worst stuck record ever. “Update your software,” “update your hardware,” “update your operating system,” are said verbatim and on repeat constantly. The reason for all the repetition is that users to do not follow this simple advice. Updates are seen as an incon