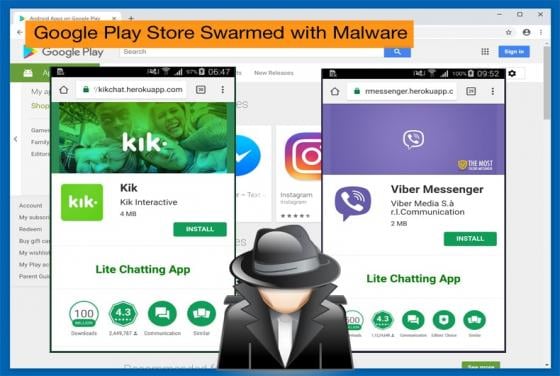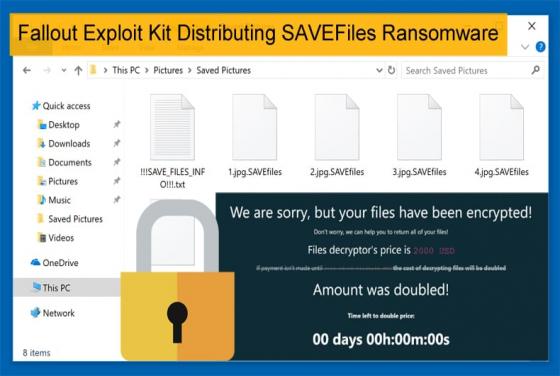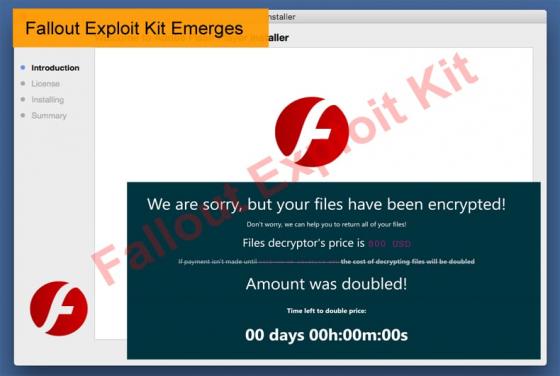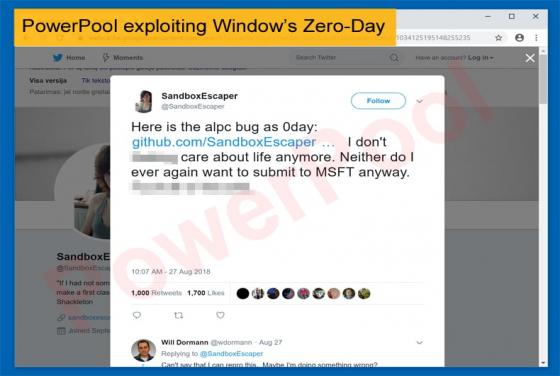

LoJax: First UEFI Malware seen in the Wild
Most hackers and threat actors are often content to copy the work of others. This means that most of the world’s cyber-attack campaigns are conducted using tried and tested tactics and already existing, if slightly modified, malware variants. When a new and original method of attack becomes apparent