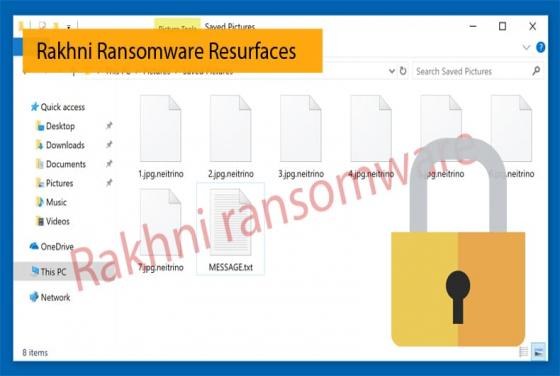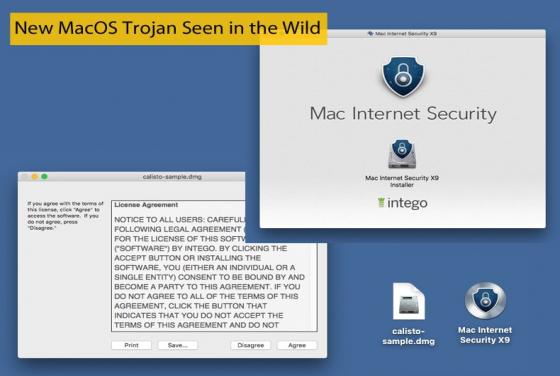

New MacOS Trojan Seen in the Wild
While malware targeting Mac users is far from common when compared to other platforms, Mac users should be aware that they are not immune to malware infections. Security researchers at Kaspersky last week detected a new variant of the Mac malware Proton, which they have called Calisto. According to