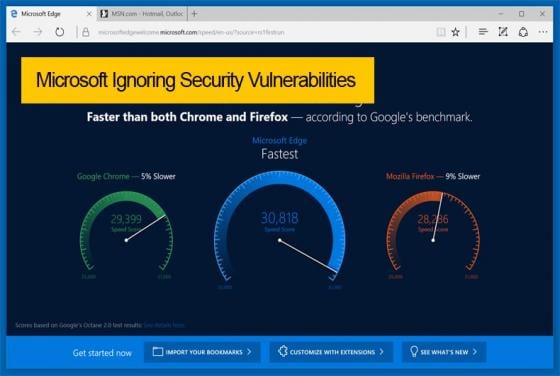

Equifax Suffers Gigantic Data Breach
When news of hacks, data breaches, and malware attacks break on mainstream media one knows that the seriousness of the situation can be rarely questioned. When it happens to a company responsible for generating a large portion of credit scores for the American public and advertises the latest advanc