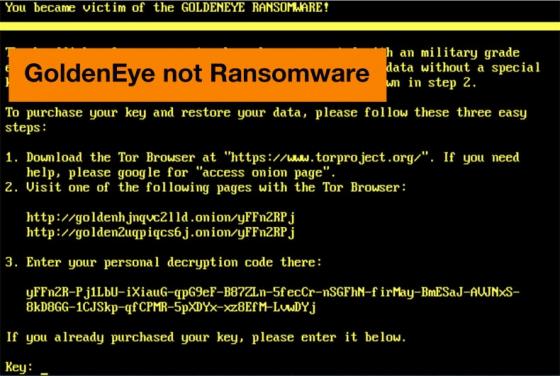
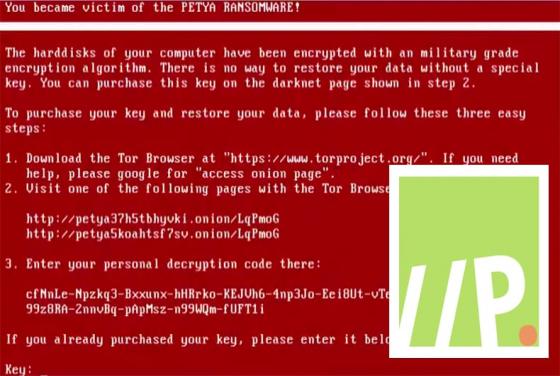
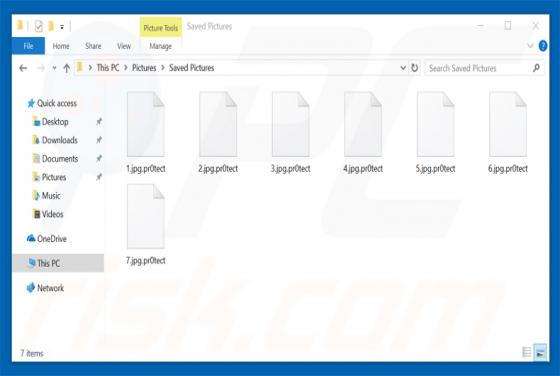
US Energy Sector Hack: Not the Apocalypse
When news broke on 6 July 2017, that companies who manage nuclear energy power stations within the US were hacked alarms were triggered. Rightly so, fears of what happened in Ukraine previously when its energy sector was essentially shut down by hackers must of being on many minds. On some other min