How to avoid falling for scam like "APPLE SECURITY BREACH"
Mac VirusAlso Known As: "APPLE SECURITY BREACH!!" virus
Get free scan and check if your device is infected.
Remove it nowTo use full-featured product, you have to purchase a license for Combo Cleaner. Seven days free trial available. Combo Cleaner is owned and operated by RCS LT, the parent company of PCRisk.com.
What kind of scam is "APPLE SECURITY BREACH"?
"APPLE SECURITY BREACH" is a fake error similar to AppleCare And Warranty, Apple Security Alert, Critical Security Warning!, and many others. This error is displayed by a malicious website to which users are redirected by various unwanted programs.
These applications commonly infiltrate systems without consent. Furthermore, they deliver intrusive advertisements, collect personal information, and reduce system performance.
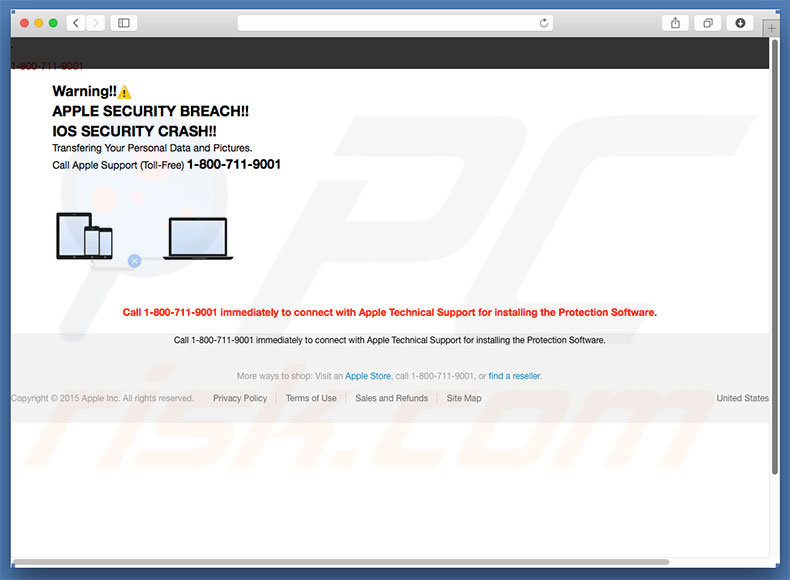
"APPLE SECURITY BREACH" scam overview
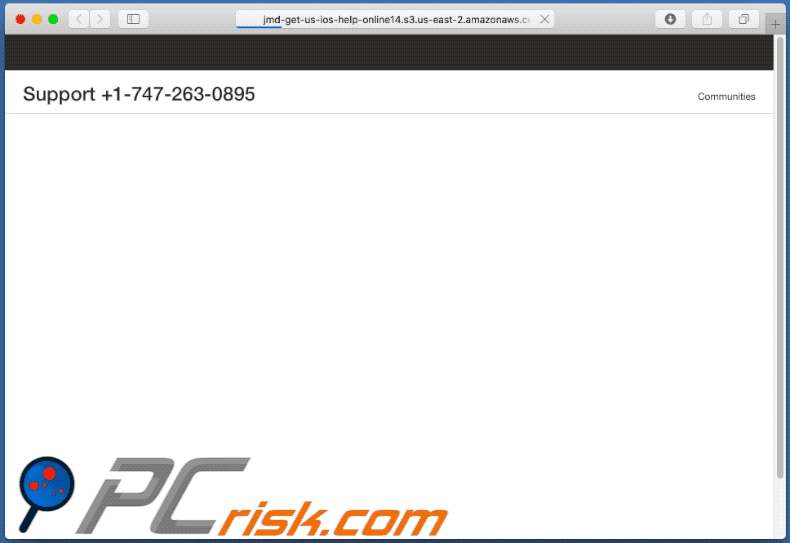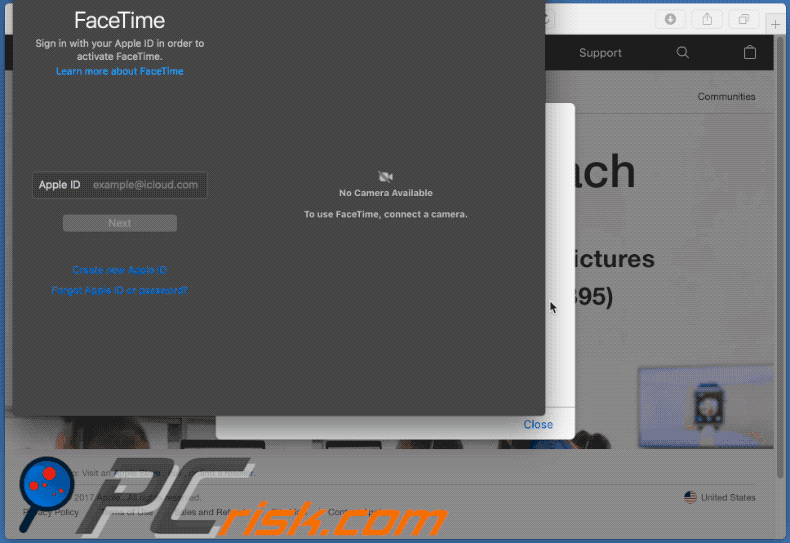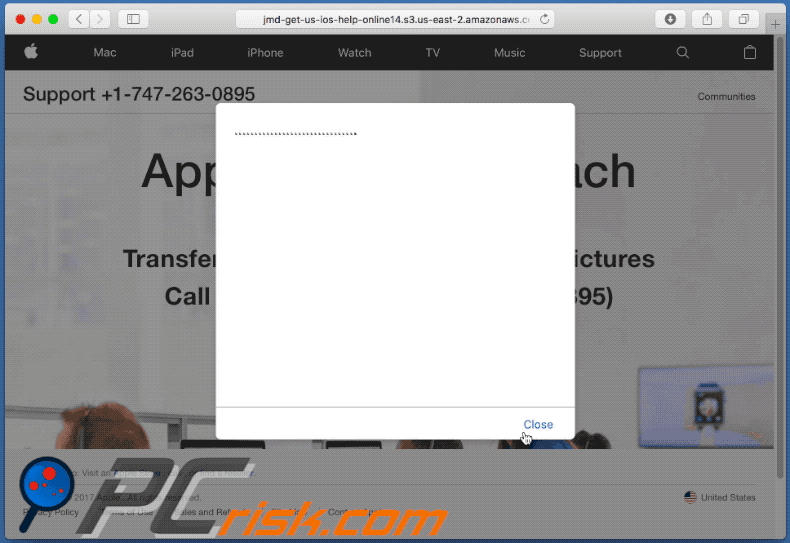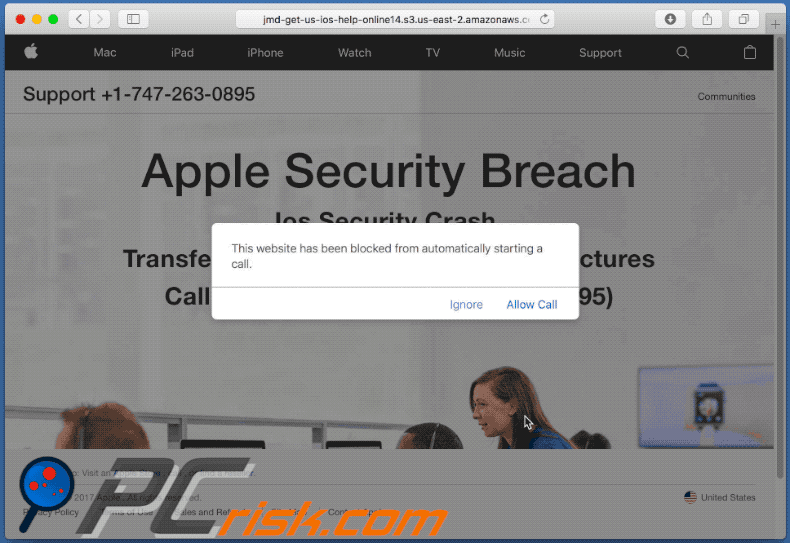
The "APPLE SECURITY BREACH" error claims that the security system has crashed and encourages users to immediately call Apple Technical Support (telephone number: "1-800-711-9001") to receive instructions on how to install protection software. Furthermore, this website displays a fake FaceTime Apple login screen.
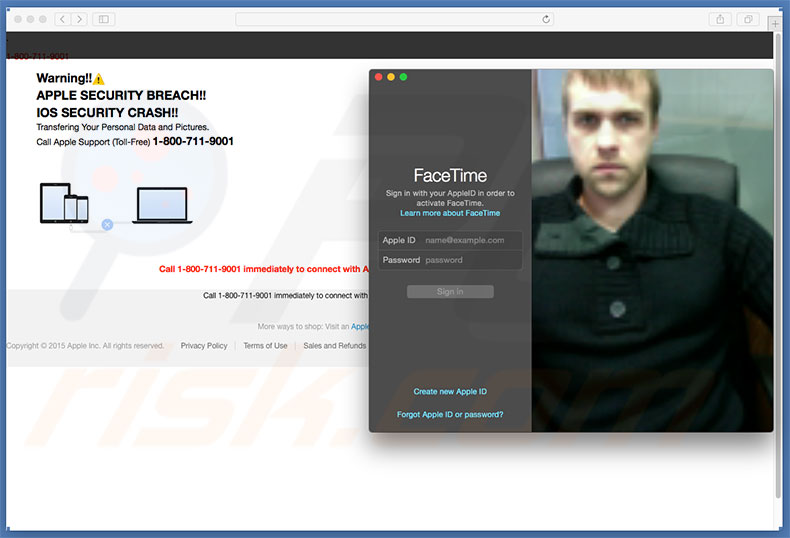
In addition, the website activates the user's webcam and displays the camera view in the login screen. Bear in mind, however, that "APPLE SECURITY BREACH" error is fake. It is a scam and has nothing to do with Apple. Cyber criminals generate revenue by tricking users into paying for technical support that is not required - the stated issues simply do not exist.
These people are also likely to request remote access to users' computers. Once connected, they stealthily install malware and/or change system settings. They then claim to "detect" further issues and offer their help for an additional fee. Furthermore, the login screen contains Apple ID (email) and Password fields.
Entering this information might result in it being sent directly to cyber criminals. We strongly advise you to ignore this fake error - never attempt to contact these people or enter account information. "APPLE SECURITY BREACH" can be removed either by closing the browser or restarting the system.
More about unwanted programs promoting scams
Unwanted programs often generate various types of intrusive advertisements (coupons, banners, pop-ups, etc.) These are generated using tools designed to enable placement of third party graphical content on any site. Therefore, the ads often conceal visited website content, significantly diminishing the Internet browsing experience.
Furthermore, they may redirect to malicious sites and/or even run scripts that infect the system with malware (or install other shady apps). Thus, clicking intrusive ads risks computer infection. Another downside is information tracking. Most rogue programs gather various information (mostly relating to Internet browsing habits).
Collected data typically includes personal details. Unwanted software developers later sell this data to third parties, thereby putting users' privacy at risk. In some cases, potentially unwanted programs also mine cryptocurrency or run other processes without permission. As a result, rogue apps significantly diminish overall computer performance.
| Name | "APPLE SECURITY BREACH!!" virus |
| Threat Type | Mac malware, Mac virus |
| Cyber Criminals' Telephone Numbers | +1-844-944-4111, +1-747-263-0895, +1-800-711-9001, +1-844-445-8771, +1-805-318-8844, + 1(833) 716-8022 |
| Related Domains | monitrcmp[.]com, theapplesupport[.]com |
| Symptoms | Your Mac became slower than normal, you see unwanted pop-up ads, you get redirected to shady websites. |
| Distribution methods | Deceptive pop-up ads, free software installers (bundling), fake flash player installers, torrent file downloads. |
| Damage | Internet browsing tracking (potential privacy issues), displaying of unwanted ads, redirects to shady websites, loss of private information. |
| Malware Removal (Windows) |
To eliminate possible malware infections, scan your computer with legitimate antivirus software. Our security researchers recommend using Combo Cleaner. Download Combo CleanerTo use full-featured product, you have to purchase a license for Combo Cleaner. 7 days free trial available. Combo Cleaner is owned and operated by RCS LT, the parent company of PCRisk.com. |
Similar scams in general
As mentioned above, "APPLE SECURITY BREACH" is virtually identical to many other errors. As with "APPLE SECURITY BREACH", all claim that the system is damaged (for instance, missing files, infected, etc.), however, these claims are simply attempts to extort money from unsuspecting users. Potentially unwanted programs also share many similarities.
Most offer useful functionality, however, they deliver no value for regular users. These programs are designed only to generate revenue for the developers. They typically cause unwanted redirects, gather information, deliver ads, and misuse system resources, thereby posing a threat to your privacy and Internet browsing safety.
How did unwanted programs install on my computer?
Some dubiou apps have official download/promotion websites, however, research shows that, in most cases, they infiltrate systems without permission. The reasons for this are poor knowledge and careless behavior by many users.
Be aware that shady apps are distributed using intrusive advertisements and a deceptive marketing method called "bundling" - stealth installation of unwanted programs with regular apps.
Developers hide "bundled" apps within various sections (typically the "Custom/Advanced" settings) of the download/installation processes. Many users rush these processes and skip steps. Furthermore, they click various ads. In doing so, they expose their systems to risk of various infections.
How to avoid installation of unwanted applications?
To prevent this situation, pay close attention when browsing the Internet, and downloading/installing programs. Intrusive ads usually look legitimate, however, they redirect to gambling, pornography, survey, and other dubious websites. If you encounter such redirects, immediately remove all dubious programs and browser plug-ins.
Furthermore, closely analyze each download/installation step and opt-out of all additionally-included programs. The key to computer safety is caution.
The appearance of this fake tech support scam pop-up:

Text presented in this pop-up scam:
Warning!!
APPLE SECURITY BREACH!!
IOS SECURITY CRASH!!
Your Apple Device Has Been Locked Due to Security Reasons.
Contact Apple Technical Support (Toll-Free) +1-877-314-0111
Call +1-877-314-0111 immediately to connect with Apple Technical Support for installing the Protection Software.
More ways to shop: Visit an Apple Store, call +1-877-314-0111, or find a reseller.
United States
Copyright © 2017 Apple Inc. All rights reserved.Privacy Policy Terms of Use Sales and Refunds Site Map
"APPLE SECURITY BREACH" pop-up automatically opens FaceTime application:
Update October 7, 2019 - Crooks have recently released an updated variant of this scam message:
Screenshot of the initial pop-up window:
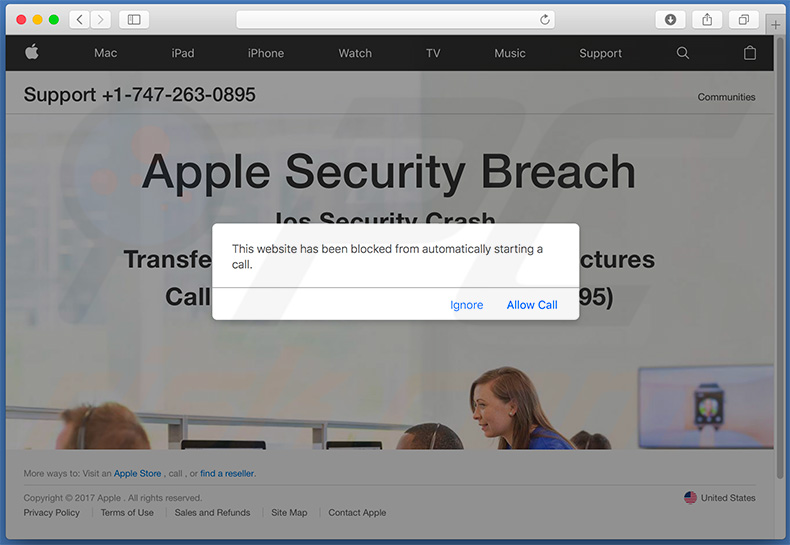
Text presented within this pop-up:
This website has been blocked from automatically starting a call.
Screenshot of FaceTime window displayed after clicking "Allow Call":
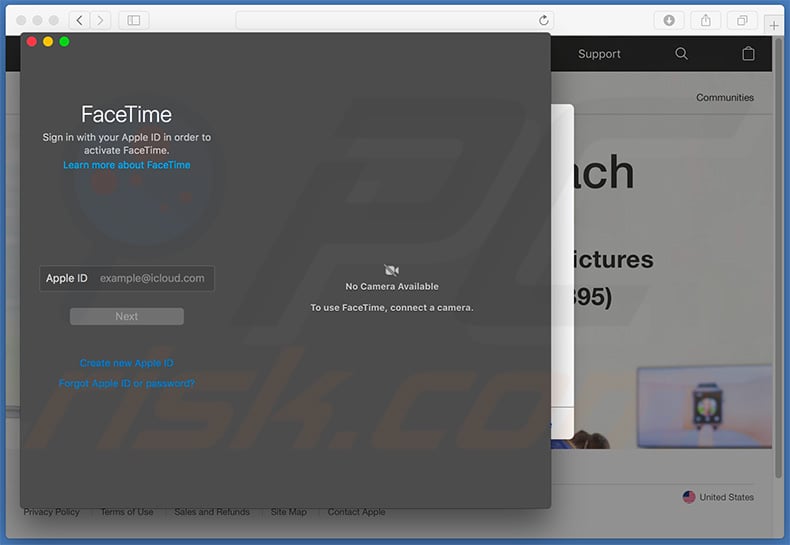
Screenshot of the background website:
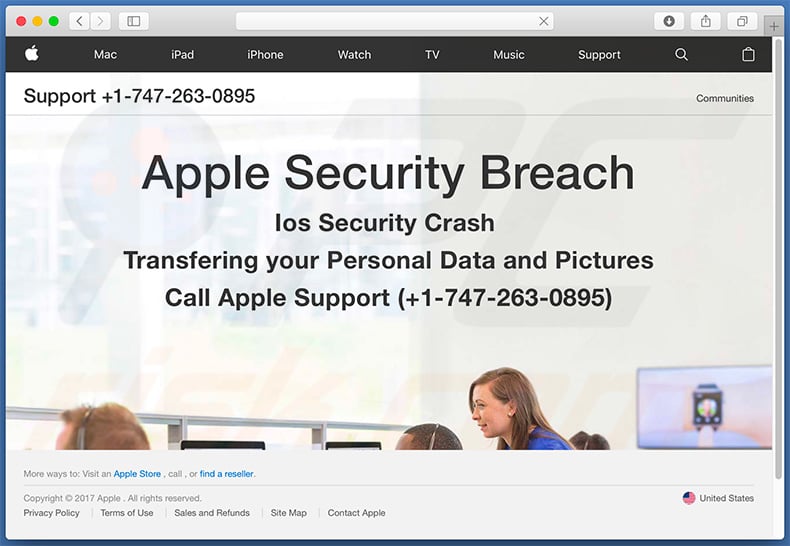
Text presented within this page:
Support +1-747-263-0895
Communities
Apple Security Breach
Ios Security Crash
Transfering your Personal Data and Pictures
Call Apple Support (+1-747-263-0895)
More ways to: Visit an Apple Store , call , or find a reseller .
United States
Copyright © 2017 Apple . All rights reserved.
Privacy Policy Terms of Use Sales and Refunds Site Map Contact Apple
Appearance of this pop-up scam (GIF):
Yet another example of "APPLE SECURITY BREACH" pop-up scam:

Text presented within:
Warning!!
APPLE SECURITY BREACH!!
IOS SECURITY CRASH!!
Your Apple Device Has Been Locked Due to Security Reasons.
Contact Apple Technical Support (Toll-Free) +1-805-318-8844
Call +1-805-318-8844 immediately to connect with Apple Technical Support for installing the Protection Software.More ways to shop: Visit an Apple Store, call + 1(833) 716-8022, or find a reseller.
United States
Copyright © 2017 Apple Inc. All rights reserved.Privacy Policy Terms of Use Sales and Refunds Site Map
Yet another variant of "APPLE SECURITY BREACH" pop-up scam:
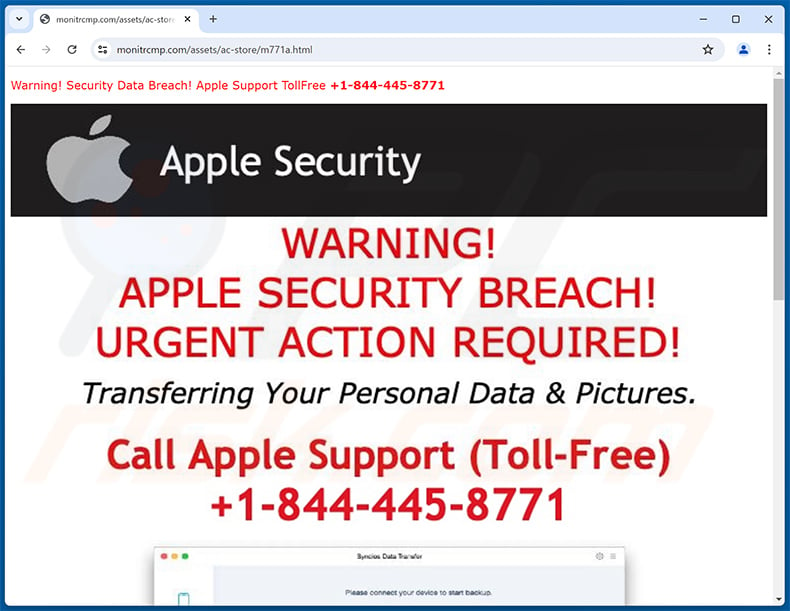
Text presented within:
Warning! Security Data Breach! Apple Support TollFree +1-844-445-8771
Apple Security
WARNING!
APPLE SECURITY BREACH!
URGENT ACTION REQUIRED!Transferring Your Personal Data & Pictures.
Call Apple Support (Toll-Free)
+1-844-445-8771
Call +1-844-445-8771 immediately to connect with Apple Technical Support for installing the Protection
Instant automatic malware removal:
Manual threat removal might be a lengthy and complicated process that requires advanced IT skills. Combo Cleaner is a professional automatic malware removal tool that is recommended to get rid of malware. Download it by clicking the button below:
DOWNLOAD Combo CleanerBy downloading any software listed on this website you agree to our Privacy Policy and Terms of Use. To use full-featured product, you have to purchase a license for Combo Cleaner. 7 days free trial available. Combo Cleaner is owned and operated by RCS LT, the parent company of PCRisk.com.
Quick menu:
- What is "APPLE SECURITY BREACH!!" virus?
- How to identify a pop-up scam?
- How do pop-up scams work?
- How to remove fake pop-ups?
- How to prevent fake pop-ups?
- What to do if you fell for a pop-up scam?
How to identify a pop-up scam?
Pop-up windows with various fake messages are a common type of lures cybercriminals use. They collect sensitive personal data, trick Internet users into calling fake tech support numbers, subscribe to useless online services, invest in shady cryptocurrency schemes, etc.
While in the majority of cases these pop-ups don't infect users' devices with malware, they can cause direct monetary loss or could result in identity theft.
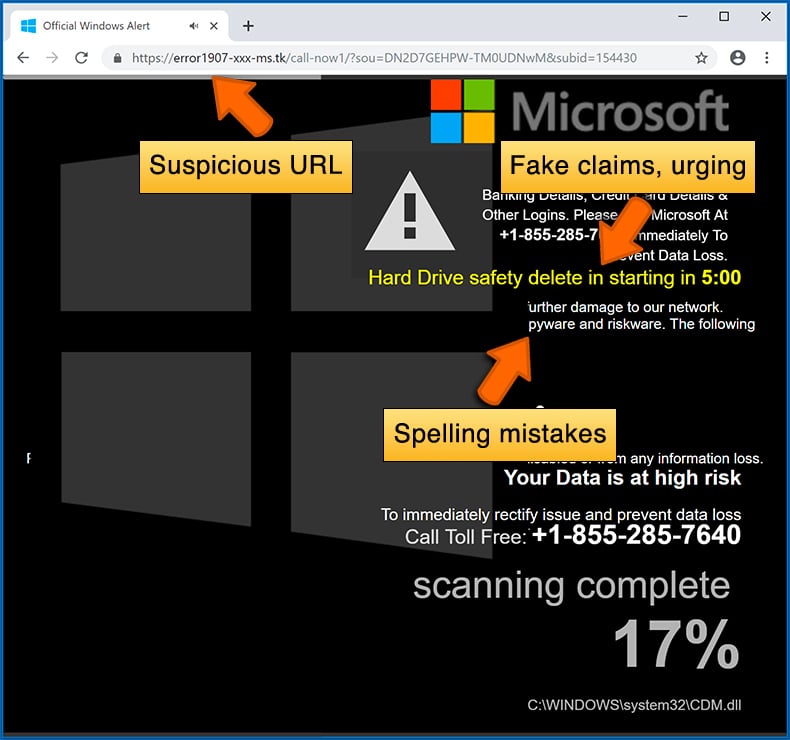
Cybercriminals strive to create their rogue pop-up windows to look trustworthy, however, scams typically have the following characteristics:
- Spelling mistakes and non-professional images - Closely inspect the information displayed in a pop-up. Spelling mistakes and unprofessional images could be a sign of a scam.
- Sense of urgency - Countdown timer with a couple of minutes on it, asking you to enter your personal information or subscribe to some online service.
- Statements that you won something - If you haven't participated in a lottery, online competition, etc., and you see a pop-up window stating that you won.
- Computer or mobile device scan - A pop-up window that scans your device and informs of detected issues - is undoubtedly a scam; webpages cannot perform such actions.
- Exclusivity - Pop-up windows stating that only you are given secret access to a financial scheme that can quickly make you rich.
Example of a pop-up scam:
How do pop-up scams work?
Cybercriminals and deceptive marketers usually use various advertising networks, search engine poisoning techniques, and shady websites to generate traffic to their pop-ups. Users land on their online lures after clicking on fake download buttons, using a torrent website, or simply clicking on an Internet search engine result.
Based on users' location and device information, they are presented with a scam pop-up. Lures presented in such pop-ups range from get-rich-quick schemes to fake virus scans.
How to remove fake pop-ups?
In most cases, pop-up scams do not infect users' devices with malware. If you encountered a scam pop-up, simply closing it should be enough. In some cases scam, pop-ups may be hard to close; in such cases - close your Internet browser and restart it.
In extremely rare cases, you might need to reset your Internet browser. For this, use our instructions explaining how to reset Internet browser settings.
How to prevent fake pop-ups?
To prevent seeing pop-up scams, you should visit only reputable websites. Torrent, Crack, free online movie streaming, YouTube video download, and other websites of similar reputation commonly redirect Internet users to pop-up scams.
To minimize the risk of encountering pop-up scams, you should keep your Internet browsers up-to-date and use reputable anti-malware application. For this purpose, we recommend Combo Cleaner Antivirus for Windows.
What to do if you fell for a pop-up scam?
This depends on the type of scam that you fell for. Most commonly, pop-up scams try to trick users into sending money, giving away personal information, or giving access to one's device.
- If you sent money to scammers: You should contact your financial institution and explain that you were scammed. If informed promptly, there's a chance to get your money back.
- If you gave away your personal information: You should change your passwords and enable two-factor authentication in all online services that you use. Visit Federal Trade Commission to report identity theft and get personalized recovery steps.
- If you let scammers connect to your device: You should scan your computer with reputable anti-malware (we recommend Combo Cleaner Antivirus for Windows) - cyber criminals could have planted trojans, keyloggers, and other malware, don't use your computer until removing possible threats.
- Help other Internet users: report Internet scams to Federal Trade Commission.
Frequently Asked Questions (FAQ)
What is a pop-up scam?
A pop-up scam is a deceptive tactic where a fraudulent or malicious website generates pop-up windows that mimic legitimate alerts, warnings, or other messages.
What is the purpose of a pop-up scam?
Scammers use pop-up scams to gain remote access to computers, distribute malware, steal sensitive information, and (or) extract money.
Why do I encounter fake pop-ups?
Typically, users land on websites hosting pop-up scams via sites associated with rogue advertising networks (e.g., torrent sites or illegal movie streaming pages), notifications from shady pages, deceptive ads, pop-ups, and similar channels.
Will Combo Cleaner protect me from pop-up scams?
Combo Cleaner scans websites you visit and detects and flags malicious sites, including those that propagate pop-up scams. If such a site is identified, you will receive an immediate warning, and access will be restricted.
Share:

Tomas Meskauskas
Expert security researcher, professional malware analyst
I am passionate about computer security and technology. I have an experience of over 10 years working in various companies related to computer technical issue solving and Internet security. I have been working as an author and editor for pcrisk.com since 2010. Follow me on Twitter and LinkedIn to stay informed about the latest online security threats.
PCrisk security portal is brought by a company RCS LT.
Joined forces of security researchers help educate computer users about the latest online security threats. More information about the company RCS LT.
Our malware removal guides are free. However, if you want to support us you can send us a donation.
DonatePCrisk security portal is brought by a company RCS LT.
Joined forces of security researchers help educate computer users about the latest online security threats. More information about the company RCS LT.
Our malware removal guides are free. However, if you want to support us you can send us a donation.
Donate
▼ Show Discussion