Do not get scammed by :Coloquei malware no site adulto email
Phishing/ScamAlso Known As: Coloquei Malware No Site Adulto spam
Get free scan and check if your device is infected.
Remove it nowTo use full-featured product, you have to purchase a license for Combo Cleaner. Seven days free trial available. Combo Cleaner is owned and operated by RCS LT, the parent company of PCRisk.com.
What is "Coloquei malware no site adulto" email?
"Coloquei malware no site adulto" ("I put malware on the adult site") is an email scam targeting Portuguese users. The scheme uses the sextortion scam model to extort money from recipients through blackmailing them with threats to expose their sexual activity.
The message claims that the user's device has been hacked and exploited to obtain compromising material (via the webcam). It warns victims that should they fail to pay a specified sum, this content will be publicized. "Coloquei malware no site adulto" is simply a scam, the alleged material (videos) does not exist, and the user's system has not been infected.
According to a rough translation, the message urges recipients not to ignore it, if they value their privacy. It claims that users' devices have been infected with malware (spyware to be exact), which has originated from an adult-themed site. The individuals responsible for this infection state that they have recorded users via their webcams while they were visiting adult websites.
Additionally, the scammers have apparently made screenshots of the content, which was being viewed at the time. After this blackmail material had been gathered, the (nonexistent) malware had supposedly collected the user's email, messenger and social media contact lists.
The message declares that as this compromising content has already been exfiltrated and cannot be deleted by reinstalling the OS (Operating System).
The scam demands that recipients pay 7,690 GBP (approximately equivalent to 10,000 USD at the time of writing) in the Bitcoin cryptocurrency, otherwise the videos will be sent to all of their contacts (email, messaging platform, Facebook and other social media accounts).
Furthermore, the recorded material will be published online: YouTube and similar sites. The message recommends that victims search YouTube and/or use a search engine (e.g. Google, Yahoo, Bing, etc.) to find out how to acquire Bitcoins, if they are unfamiliar with this digital currency.
The recipients supposedly have eight hours to make the transaction from the moment they open the email. If they pay, the (fictitious) content is destroyed and the scammers promise to never contact them again. Users are warned that reporting this to the authorities can block the cryptowallet, which will allegedly force publication of videos made of all victims who are yet to pay.
Thus implying that the recipient will be responsible for compromising not only their integrity, but others as well. The scammers inform users to only make contact to reconfirm the Bitcoin address and/or to make similar queries, since they are supposedly using a hacked and compromised email account.
Note: all claims made in "Coloquei malware no site adulto" are false. Recipients' devices have not been hacked/infected, no data has been stolen and no compromising material exists.
This email is merely a scam and should be ignored. Regardless of the validity of claims made by cyber criminals, you are strongly advised against meeting their ransom demands. They cannot be trusted and there are no guarantees that these criminals will hold up their end of the bargain.
| Name | Coloquei malware no site adulto email scam |
| Threat Type | Phishing, Scam, Social Engineering, Fraud. |
| Fake Claim | Email claims that cyber criminals have made compromising videos of the recipient and will publicize them, unless they are paid. |
| Ransom Amount | £7,690.00 GBP in Bitcoin (~10,000 USD). |
| Cyber Criminal Cryptowallet Address | 13j2z2t6F59qndXekHwqvazgnFDNsUyqkt (Bitcoin). |
| Symptoms | Unauthorized online purchases, changed online account passwords, identity theft, illegal access of the computer. |
| Distribution methods | Deceptive emails, rogue online pop-up ads, search engine poisoning techniques, misspelled domains. |
| Damage | Loss of sensitive private information, monetary loss, identity theft. |
| Malware Removal (Windows) |
To eliminate possible malware infections, scan your computer with legitimate antivirus software. Our security researchers recommend using Combo Cleaner. Download Combo CleanerTo use full-featured product, you have to purchase a license for Combo Cleaner. 7 days free trial available. Combo Cleaner is owned and operated by RCS LT, the parent company of PCRisk.com. |
Deceptive emails are sent during mass scale scam campaigns. A wide variety of scam models are used to trick users into performing certain tasks such as making monetary transactions, revealing personal information, downloading/installing/purchasing untrustworthy or malicious software and so on.
"I KNOW YOU OPENED MY LAST MAIL", "The last time you visited a Porn website", "Hacker Who Has Access To Your Operating System" and "Looked at you for several months" are some examples of other email scams similar to "Coloquei malware no site adulto".
How do spam campaigns infect computers?
Systems are infected via dangerous files attached to and/or linked in deceptive emails. The messages are usually disguised as "urgent", "official", "important" or otherwise marked as priority mail. These files can be in various formats including Microsoft Office and PDF documents, executables (.exe, .run) and archives (RAR, ZIP), JavaScript, etc.
Once an infectious file is opened, the infection process is initiated and it begins downloading/installing malware. For example, MS Office docs cause infections by executing malicious macro commands. Opening these documents with MS versions released prior to 2010 is enough to start the infection.
Newer versions ask users permission to enable macros (i.e., enable editing) - the malicious software installation begins only if they are enabled.
How to avoid installation of malware
Do not open suspicious and/or irrelevant emails, especially those received from unknown addresses. Any attachments or links present in suspect messages must never be opened, as these files are potential sources of infection.
Use only official and verified download channels, as opposed to Peer-to-Peer sharing networks, free file-hosting websites, third party downloaders and other untrustworthy sources. Programs must be activated and updated with tools/functions provided by legitimate developers.
Illegal activation ("cracking") tools and third party updaters are high-risk and should not be used. Have a reputable anti-virus/anti-spyware suite installed and kept up-to-date. This software is to be used for regular system scans and removal of detected threats.
If you have already opened malicious attachments, we recommend running a scan with Combo Cleaner Antivirus for Windows to automatically eliminate infiltrated malware.
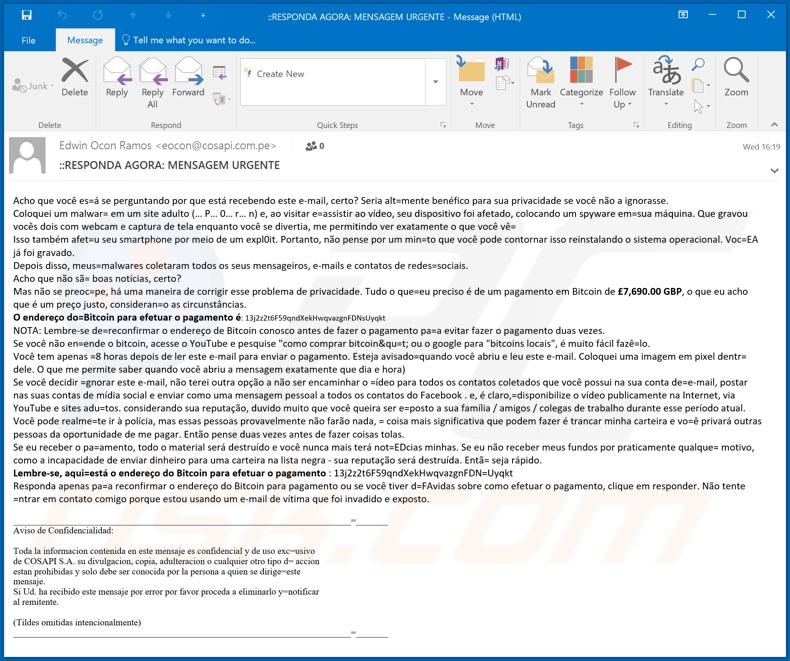
Text presented in the "Coloquei malware no site adulto" email message:
Subject: ::RESPONDA AGORA: MENSAGEM URGENTE
Acho que você es=á se perguntando por que está recebendo este e-mail, certo? Seria alt=mente benéfico para sua privacidade se você não a ignorasse.
Coloquei um malwar= em um site adulto (… P… 0… r… n) e, ao visitar e=assistir ao vídeo, seu dispositivo foi afetado, colocando um spyware em=sua máquina. Que gravou vocês dois com webcam e captura de tela enquanto você se divertia, me permitindo ver exatamente o que você vê=
Isso também afet=u seu smartphone por meio de um expl0it. Portanto, não pense por um min=to que você pode contornar isso reinstalando o sistema operacional. Voc=EA já foi gravado.
Depois disso, meus=malwares coletaram todos os seus mensageiros, e-mails e contatos de redes=sociais.
Acho que não sã= boas notícias, certo?
Mas não se preoc=pe, há uma maneira de corrigir esse problema de privacidade. Tudo o que=eu preciso é de um pagamento em Bitcoin de £7,690.00 GBP, o que eu acho que é um preço justo, consideran=o as circunstâncias.
O endereço do=Bitcoin para efetuar o pagamento é: 13j2z2t6F59qndXekHwqvazgnFDNsUyqkt
NOTA: Lembre-se de=reconfirmar o endereço de Bitcoin conosco antes de fazer o pagamento pa=a evitar fazer o pagamento duas vezes.
Se você não en=ende o bitcoin, acesse o YouTube e pesquise "como comprar bitcoin&qu=t; ou o google para "bitcoins locais", é muito fácil fazê=lo.
Você tem apenas =8 horas depois de ler este e-mail para enviar o pagamento. Esteja avisado=quando você abriu e leu este e-mail. Coloquei uma imagem em pixel dentr= dele. O que me permite saber quando você abriu a mensagem exatamente que dia e hora)
Se você decidir =gnorar este e-mail, não terei outra opção a não ser encaminhar o =ídeo para todos os contatos coletados que você possui na sua conta de=e-mail, postar nas suas contas de mídia social e enviar como uma mensagem pessoal a todos os contatos do Facebook . e, é claro,=disponibilize o vídeo publicamente na Internet, via YouTube e sites adu=tos. considerando sua reputação, duvido muito que você queira ser e=posto a sua família / amigos / colegas de trabalho durante esse período atual.
Você pode realme=te ir à polícia, mas essas pessoas provavelmente não farão nada, = coisa mais significativa que podem fazer é trancar minha carteira e vo=ê privará outras pessoas da oportunidade de me pagar. Então pense duas vezes antes de fazer coisas tolas.
Se eu receber o pa=amento, todo o material será destruído e você nunca mais terá not=EDcias minhas. Se eu não receber meus fundos por praticamente qualque= motivo, como a incapacidade de enviar dinheiro para uma carteira na lista negra - sua reputação será destruída. Entã= seja rápido.
Lembre-se, aqui=está o endereço do Bitcoin para efetuar o pagamento : 13j2z2t6F59qndXekHwqvazgnFDN=Uyqkt
Responda apenas pa=a reconfirmar o endereço do Bitcoin para pagamento ou se você tiver d=FAvidas sobre como efetuar o pagamento, clique em responder. Não tente =ntrar em contato comigo porque estou usando um e-mail de vítima que foi invadido e exposto.Aviso de Confidencialidad:
Toda la informacion contenida en este mensaje es confidencial y de uso exc=usivo
de COSAPI S.A. su divulgacion, copia, adulteracion o cualquier otro tipo d= accion
estan prohibidas y solo debe ser conocida por la persona a quien se dirige=este
mensaje.
Si Ud. ha recibido este mensaje por error por favor proceda a eliminarlo y=notificar
al remitente.(Tildes omitidas intencionalmente)
Another variant of "Coloquei Malware No Site Adulto" scam email:
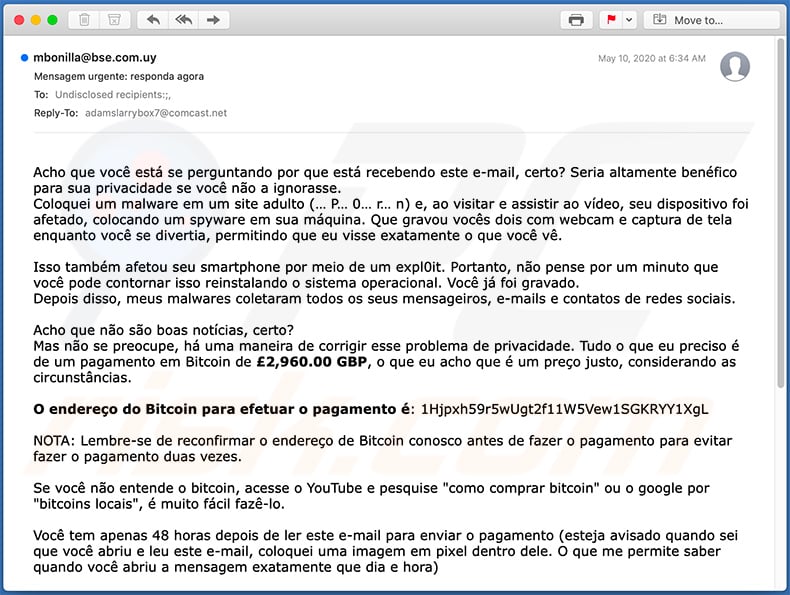
Text presented within:
Subject: Mensagem urgente: responda agora
Acho que você está se perguntando por que está recebendo este e-mail, certo? Seria altamente benéfico para sua privacidade se você não a ignorasse.
Coloquei um malware em um site adulto (… P… 0… r… n) e, ao visitar e assistir ao vídeo, seu dispositivo foi afetado, colocando um spyware em sua máquina. Que gravou vocês dois com webcam e captura de tela enquanto você se divertia, permitindo que eu visse exatamente o que você vê.
Isso também afetou seu smartphone por meio de um expl0it. Portanto, não pense por um minuto que você pode contornar isso reinstalando o sistema operacional. Você já foi gravado.
Depois disso, meus malwares coletaram todos os seus mensageiros, e-mails e contatos de redes sociais.
Acho que não são boas notícias, certo?
Mas não se preocupe, há uma maneira de corrigir esse problema de privacidade. Tudo o que eu preciso é de um pagamento em Bitcoin de £2,960.00 GBP, o que eu acho que é um preço justo, considerando as circunstâncias.
O endereço do Bitcoin para efetuar o pagamento é: 1Hjpxh59r5wUgt2f11W5Vew1SGKRYY1XgL
NOTA: Lembre-se de reconfirmar o endereço de Bitcoin conosco antes de fazer o pagamento para evitar fazer o pagamento duas vezes.
Se você não entende o bitcoin, acesse o YouTube e pesquise "como comprar bitcoin" ou o google por "bitcoins locais", é muito fácil fazê-lo.
Você tem apenas 48 horas depois de ler este e-mail para enviar o pagamento (esteja avisado quando sei que você abriu e leu este e-mail, coloquei uma imagem em pixel dentro dele. O que me permite saber quando você abriu a mensagem exatamente que dia e hora)
Se você decidir ignorar este e-mail, não terei outra opção a não ser encaminhar o vídeo para todos os contatos coletados que você possui na sua conta de e-mail, postar nas suas contas de mídia social e enviar como uma mensagem pessoal a todos os contatos do Facebook . e, é claro, disponibilize o vídeo publicamente na Internet, via YouTube e sites adultos. considerando sua reputação, duvido muito que você queira ser exposto a sua família / amigos / colegas de trabalho durante esse período atual.
Você pode realmente ir à polícia, mas essas pessoas provavelmente não farão nada, a coisa mais importante que podem fazer é trancar minha carteira e você privará outras pessoas da oportunidade de me pagar. Então pense duas vezes antes de fazer coisas tolas.
Se eu receber o pagamento, todo o material será destruído e você nunca mais terá notícias minhas. Se eu não receber meus fundos por praticamente qualquer motivo, como a incapacidade de enviar dinheiro para uma carteira na lista negra - sua reputação será destruída. Então seja rápido.
Lembre-se, aqui está o endereço do Bitcoin para efetuar o pagamento - 1Hjpxh59r5wUgt2f11W5Vew1SGKRYY1XgL
Responda apenas para reconfirmar o endereço de Bitcoin para pagamento ou se você tiver dúvidas sobre como efetuar o pagamento, clique em responder. Não tente entrar em contato comigo porque estou usando um e-mail de vítima que foi hackeado e exposto.
Instant automatic malware removal:
Manual threat removal might be a lengthy and complicated process that requires advanced IT skills. Combo Cleaner is a professional automatic malware removal tool that is recommended to get rid of malware. Download it by clicking the button below:
DOWNLOAD Combo CleanerBy downloading any software listed on this website you agree to our Privacy Policy and Terms of Use. To use full-featured product, you have to purchase a license for Combo Cleaner. 7 days free trial available. Combo Cleaner is owned and operated by RCS LT, the parent company of PCRisk.com.
Quick menu:
- What is Coloquei Malware No Site Adulto spam?
- Types of malicious emails.
- How to spot a malicious email?
- What to do if you fell for an email scam?
Types of malicious emails:
![]() Phishing Emails
Phishing Emails
Most commonly, cybercriminals use deceptive emails to trick Internet users into giving away their sensitive private information, for example, login information for various online services, email accounts, or online banking information.
Such attacks are called phishing. In a phishing attack, cybercriminals usually send an email message with some popular service logo (for example, Microsoft, DHL, Amazon, Netflix), create urgency (wrong shipping address, expired password, etc.), and place a link which they hope their potential victims will click on.
After clicking the link presented in such email message, victims are redirected to a fake website that looks identical or extremely similar to the original one. Victims are then asked to enter their password, credit card details, or some other information that gets stolen by cybercriminals.
![]() Emails with Malicious Attachments
Emails with Malicious Attachments
Another popular attack vector is email spam with malicious attachments that infect users' computers with malware. Malicious attachments usually carry trojans that are capable of stealing passwords, banking information, and other sensitive information.
In such attacks, cybercriminals' main goal is to trick their potential victims into opening an infected email attachment. To achieve this goal, email messages usually talk about recently received invoices, faxes, or voice messages.
If a potential victim falls for the lure and opens the attachment, their computers get infected, and cybercriminals can collect a lot of sensitive information.
While it's a more complicated method to steal personal information (spam filters and antivirus programs usually detect such attempts), if successful, cybercriminals can get a much wider array of data and can collect information for a long period of time.
![]() Sextortion Emails
Sextortion Emails
This is a type of phishing. In this case, users receive an email claiming that a cybercriminal could access the webcam of the potential victim and has a video recording of one's masturbation.
To get rid of the video, victims are asked to pay a ransom (usually using Bitcoin or another cryptocurrency). Nevertheless, all of these claims are false - users who receive such emails should ignore and delete them.
How to spot a malicious email?
While cyber criminals try to make their lure emails look trustworthy, here are some things that you should look for when trying to spot a phishing email:
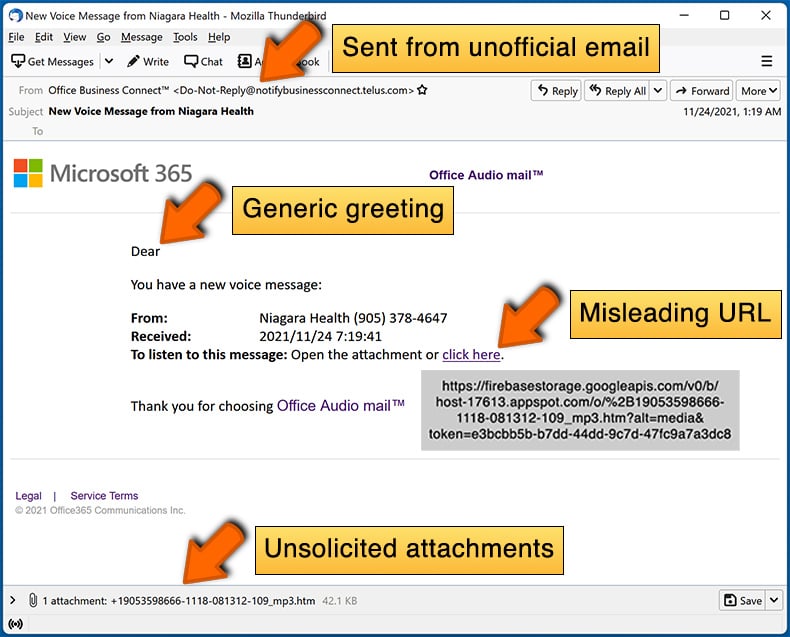
- Check the sender's ("from") email address: Hover your mouse over the "from" address and check if it's legitimate. For example, if you received an email from Microsoft, be sure to check if the email address is @microsoft.com and not something suspicious like @m1crosoft.com, @microsfot.com, @account-security-noreply.com, etc.
- Check for generic greetings: If the greeting in the email is "Dear user", "Dear @youremail.com", "Dear valued customer", this should raise suspiciousness. Most commonly, companies call you by your name. Lack of this information could signal a phishing attempt.
- Check the links in the email: Hover your mouse over the link presented in the email, if the link that appears seems suspicious, don't click it. For example, if you received an email from Microsoft and the link in the email shows that it will go to firebasestorage.googleapis.com/v0... you shouldn't trust it. It's best not to click any links in the emails but to visit the company website that sent you the email in the first place.
- Don't blindly trust email attachments: Most commonly, legitimate companies will ask you to log in to their website and to view any documents there; if you received an email with an attachment, it's a good idea to scan it with an antivirus application. Infected email attachments are a common attack vector used by cybercriminals.
To minimise the risk of opening phishing and malicious emails we recommend using Combo Cleaner Antivirus for Windows.
Example of a spam email:
What to do if you fell for an email scam?
- If you clicked on a link in a phishing email and entered your password - be sure to change your password as soon as possible. Usually, cybercriminals collect stolen credentials and then sell them to other groups that use them for malicious purposes. If you change your password in a timely manner, there's a chance that criminals won't have enough time to do any damage.
- If you entered your credit card information - contact your bank as soon as possible and explain the situation. There's a good chance that you will need to cancel your compromised credit card and get a new one.
- If you see any signs of identity theft - you should immediately contact the Federal Trade Commission. This institution will collect information about your situation and create a personal recovery plan.
- If you opened a malicious attachment - your computer is probably infected, you should scan it with a reputable antivirus application. For this purpose, we recommend using Combo Cleaner Antivirus for Windows.
- Help other Internet users - report phishing emails to Anti-Phishing Working Group, FBI’s Internet Crime Complaint Center, National Fraud Information Center and U.S. Department of Justice.
Share:

Tomas Meskauskas
Expert security researcher, professional malware analyst
I am passionate about computer security and technology. I have an experience of over 10 years working in various companies related to computer technical issue solving and Internet security. I have been working as an author and editor for pcrisk.com since 2010. Follow me on Twitter and LinkedIn to stay informed about the latest online security threats.
PCrisk security portal is brought by a company RCS LT.
Joined forces of security researchers help educate computer users about the latest online security threats. More information about the company RCS LT.
Our malware removal guides are free. However, if you want to support us you can send us a donation.
DonatePCrisk security portal is brought by a company RCS LT.
Joined forces of security researchers help educate computer users about the latest online security threats. More information about the company RCS LT.
Our malware removal guides are free. However, if you want to support us you can send us a donation.
Donate
▼ Show Discussion