About the "Hacker who has access to your operating system" spam email campaign
Phishing/ScamAlso Known As: Hacker Who Has Access To Your Operating System spam
Get free scan and check if your device is infected.
Remove it nowTo use full-featured product, you have to purchase a license for Combo Cleaner. Seven days free trial available. Combo Cleaner is owned and operated by RCS LT, the parent company of PCRisk.com.
What is "Hacker Who Has Access To Your Operating System"?
"Hacker Who Has Access To Your Operating System" is yet another spam email campaign that falls within the 'sextortion' category. Cyber criminals send hundreds of thousands of deceptive emails stating that they have hijacked the victim's computer and recorded a 'humiliating video'. In fact, this is merely a scam and such emails should be ignored.
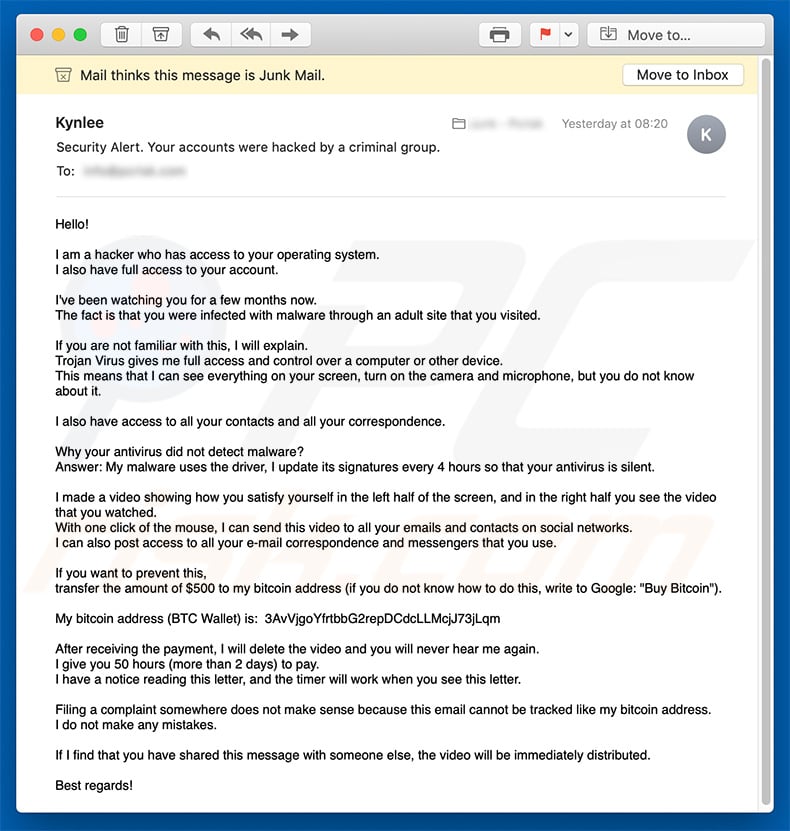
"Hacker Who Has Access To Your Operating System" email scam overview
The message essentially states that cyber criminals have infected the computer with a trojan when the recipient was purportedly visiting an adult website. Criminals also state that they have used the hijacked computer's webcam and microphone to recorded a video of the recipient "pleasing himself" and have also stolen his contacts.
These claims are followed by a threat/ransom demand. These people state that they will send the recorded video (together with the video that the recipient has supposedly watched) to all of the recipient's contacts, unless a ransom of $500 is paid. Recipients are instructed to pay the ransom within 50 hours and they must use the Bitcoin cryptocurrency.
Once payment is received, the video will supposedly be permanently deleted. Be aware, however, that this is a scam. Your computer is probably virus-free and these people certainly have not recorded any video. Cyber criminals send these emails to many people hoping that some will fall for the scam.
Unfortunately, many people do, and criminals generate revenue with minimum effort. Therefore, ignore "Hacker Who Has Access To Your Operating System" and other similar emails, and certainly do not send any money.
We receive a great deal of feedback from concerned users about this type of scam email. Here are the most popular questions we receive (in this case, relating to a scam claiming to have obtained compromising videos or photos of the user):
Q: Hi pcrisk.com team, I received an email stating that my computer was hacked and they have a video of me. Now they are asking for a ransom in Bitcoins. I think this must be true because they listed my real name and password in the email. What should I do?
A: Do not worry about this email. Neither hackers nor cyber criminals have infiltrated/hacked your computer and there is no video of you watching pornography. Simply ignore the message and do not send any Bitcoins. Your email, name, and password was probably stolen from a compromised website such as Yahoo (these website breaches are common). If you are concerned, you can check if your accounts have been compromised by visiting the haveibeenpwned website.
| Name | Hacker Who Has Access To Your Operating System Email Scam |
| Threat Type | Phishing, Scam, Social Engineering, Fraud |
| Fake Claim | Criminals claim that they have humiliating material and attempt to blackmail victims. |
| Cyber Criminal Cryptowallet Address | bc1qxk5x93qlymudj4k7clnpsrw3dz08myluhsy37x, 1BCbQEJN1bHXAsLak9MEZeCvyZGC4N3F3T, bc1qladkpxy4vcx996c4k55dw08hpz6m7eksk4a5d3, 11FktyBmpDKBDUzTdaw5bbCbx8mRVZYWo, 1QBybsYTttsWrY5B2HnGGURHufeHYEKKf9, 186iNXiz2vo4TeBxcrKs6Ebpe9kpn2FBtR, bc1qyl3tgwc3g3yxe3nmc8nd268ss4gggemk3nyfuz, bc1qn27j54lgz4jdg8k028p0djxqxamtnujnqzzq4d, bc1qj0lerf8k8mry48800rfvj2gk8kz8ankq5h9437, 3AvVjgoYfrtbbG2repDCdcLLMcjJ73jLqm, 18bF61DzcK5ifmz5HpjQapDuGt1gdZMiq3, 15cxm41FBpZ5DHgGnZ9vRgttx6JbikiWGE, 14X2moJVznF31s4ynCyVZTQbs61cvkJLS5, 13yQcMFQSf7ixzJrNceCDL4E1jVHEVqrcY, 3GyUyLv6X6erPibUSavuuHGKzpDUWxNcCF, 3391uBm42nTiHnjaeLqauuze57syqTk2zp, 1AJ4syJxPPP7hYhURPiQUQMY4LurJgYvY8, 1PNzJwB1CuVnKqKJQnu31E5ckiz9VxTcND, 1NZz572KoTSJgTNAEZsZw1f2Gtd9cVPQZj, 1QGRZCEu4wtgkVWm9u27ypHDNUkirp1JWb, 13fRV6chMyEKVjmRG4S47r8XCJG2e6t914, bc1qx389l5u0uqv6lpxgdhz2hzyf9vfl3g89ujjg9p, 15J5D1XD6F6LccSFp8CAf6aJemZCzp5oAm |
| Size Of Ransom |
$500 |
| Symptoms | Unauthorized online purchases, changed online account passwords, identity theft, illegal access of the computer. |
| Distribution methods | Deceptive emails, rogue online pop-up ads, search engine poisoning techniques, misspelled domains. |
| Damage | Loss of sensitive private information, monetary loss, identity theft. |
| Malware Removal (Windows) |
To eliminate possible malware infections, scan your computer with legitimate antivirus software. Our security researchers recommend using Combo Cleaner. Download Combo CleanerTo use full-featured product, you have to purchase a license for Combo Cleaner. 7 days free trial available. Combo Cleaner is owned and operated by RCS LT, the parent company of PCRisk.com. |
Sextortion spam campaign examples
There are many spam email campaigns similar to "Hacker Who Has Access To Your Operating System". The list of examples includes "You Certainly Do Not Know Me", "Looked At You For Several Months", and "So I'm The Hacker Who Broke Your Email".
Note that 'sextortion' is not the only type of spam campaign. Criminals also use this tactic to spread high-risk malware (e.g., TrickBot, Hancitor, Emotet, FormBook, etc.). They send deceptive emails that contain malicious attachments (typically, Microsoft Office documents) and messages encouraging recipients to open the attached files. Opening them results in malware infection.
How do spam campaigns infect computers?
For spam email campaigns to be successful, user interaction is required. Cyber criminals send emails containing malicious attachments and messages encouraging recipients to open them. These attachments might be presented as important documents in attempts to give the impression of legitimacy and increase the chance of tricking recipients.
In most cases, they come in format of Microsoft Office documents (e.g., Excel, Word, and other similar files), which infect computers using malicious macro commands, however, they might also be PDF documents, archive, links, and so on. In any case, these attachments are harmless, unless they are opened.
The main reasons for these computer infections are poor knowledge of the threats and careless behavior.
How to avoid installation of malware?
To prevent this situation, be very cautious when browsing the Internet and downloading/installing/updating software. Handle all email attachments with care. Files/links receipts from suspicious/unrecognizable email addresses should never be opened. Furthermore, download programs from official sources only, preferably using direct download links.
Third party downloaders/installers often include rogue apps, and thus these tools should not be used. Carefully analyze each window of the download/installation dialogs using the "Custom" or "Advanced" settings. Opt-out of all additionally-included programs and decline offers to download/install them.
Keep installed applications and operating systems up-to-date, however, use implemented functions or tools provided by the official developer only. Bear in mind that older versions of Microsoft Office are vulnerable to malware attacks.
2010 and later versions have "Protected View" mode, which prevents newly-downloaded documents from executing rogue macros and downloading/installing malicious software. Therefore, we strongly advise you to avoid using older versions of MS Word. The key to computer safety is caution.
If you have already opened malicious attachments, we recommend running a scan with Combo Cleaner Antivirus for Windows to automatically eliminate infiltrated malware.
Text presented in the "Hacker Who Has Access To Your Operating System" email message:
Subject: Security Alert. Your accounts were hacked by a criminal group.
Hello!
I am a hacker who has access to your operating system.
I also have full access to your account.I've been watching you for a few months now.
The fact is that you were infected with malware through an adult site that you visited.If you are not familiar with this, I will explain.
Trojan Virus gives me full access and control over a computer or other device.
This means that I can see everything on your screen, turn on the camera and microphone, but you do not know about it.I also have access to all your contacts and all your correspondence.
Why your antivirus did not detect malware?
Answer: My malware uses the driver, I update its signatures every 4 hours so that your antivirus is silent.I made a video showing how you satisfy yourself in the left half of the screen, and in the right half you see the video that you watched.
With one click of the mouse, I can send this video to all your emails and contacts on social networks.
I can also post access to all your e-mail correspondence and messengers that you use.If you want to prevent this,
transfer the amount of $500 to my bitcoin address (if you do not know how to do this, write to Google: "Buy Bitcoin").My bitcoin address (BTC Wallet) is: 3AvVjgoYfrtbbG2repDCdcLLMcjJ73jLqm, 395wdUpmkEG6iPdCguKCqYJR5UkpdWm5Wk, 3HnDpvc9mXTcmAePPCaU3q82egxP8p5P6G, 3JgjbyQJcymqApzph5EWDQdH8cNphXFZKu, 3NmUUGnYGkMn2hAi9L8sd5J4okWjq3mZNe, 1ELKdWgfedTJ9FV4U5W2JVXFzTpKSqcCjM, 3HxqrQmEffcMZo5cgNqRXwD3dw5LCYSx7K, 1ANFoTP6ETjBfL6o3ZhJm1jag1x1KAbAxZ, 37yLxF7mM7h3KiDvqWh88wm1VjFvemDYpf, 358MfWU8MctxPJhFBiNpsdGtxDtHixTi8r, 3AVitbSbsDWRyda9JNs8avrjhq2ZN7uCMy, 15Q5a6gHDaAtqFE3uEhfAhY8PqJiaw94vT, 3FL1txfM4knPnySJHiXAsK91cnmEXHGemv, 1CMBC1Mj86GHmbwzcMMP8xUe1hQTwk4Ds7, 1Ji2K8EVzxDRnpuXts1kKAjMwTrV2LTnRS, 3QikbxiTy7cWH7ZGZbLQYANxZA2MZHmmDs, 3JPdsEkcxv715Th7hN7fgoUYds22xBaPno, 1Niyhcqd8MNT8tpRs8gK6Ho3V8fJy2wbF, 1FErgudo2nCpuu9XSLJkSiqQBy62N1weiy, 1NvwQchudHai3KcqDkwTGgNzHK9YrWHzV6, 1AfwxZ8nYzwEzME39PuqVZU7Mn73XxQTqq, 17nhAbZGm4UmSVj5Zx8amwAbjVXcxGtEAz, 1ipEif9Roe3DjboppZ99mswU6r7Y1puUi, 1Dg5UsxMEG41TC3i9ugxcFV6cVtz8cpfXE, 1DpfAYoWGpTprX3cRg6mnUuYqNm3eXiR4F, 1BcpAGfamAy81enJtHahKedaWx1yATTXT7, 1KUknkh9bC4TPUoPXv4SnKdib8RAnUXDGw, 1G3UXmDBoeRvU3D2tGmGGU7fpCAEY1dBQV, 18Jro9LNFqBQarcc63WYGf3w7PdDAiwXpk, 13WVfQkbqdsSUNBDPDWTLqSXeaYX1tZ6UD, 1MS638iFfpruXbiLA43GVuoPEBLpKQDTjd, 1EUj48o3UnZvCjZEvYX9CHYbuL7rkhnB8s
After receiving the payment, I will delete the video and you will never hear me again.
I give you 50 hours (more than 2 days) to pay.
I have a notice reading this letter, and the timer will work when you see this letter.Filing a complaint somewhere does not make sense because this email cannot be tracked like my bitcoin address.
I do not make any mistakes.If I find that you have shared this message with someone else, the video will be immediately distributed.
Best regards!
Another variant of "Hacker Who Has Access To Your Operating System" spam campaign:
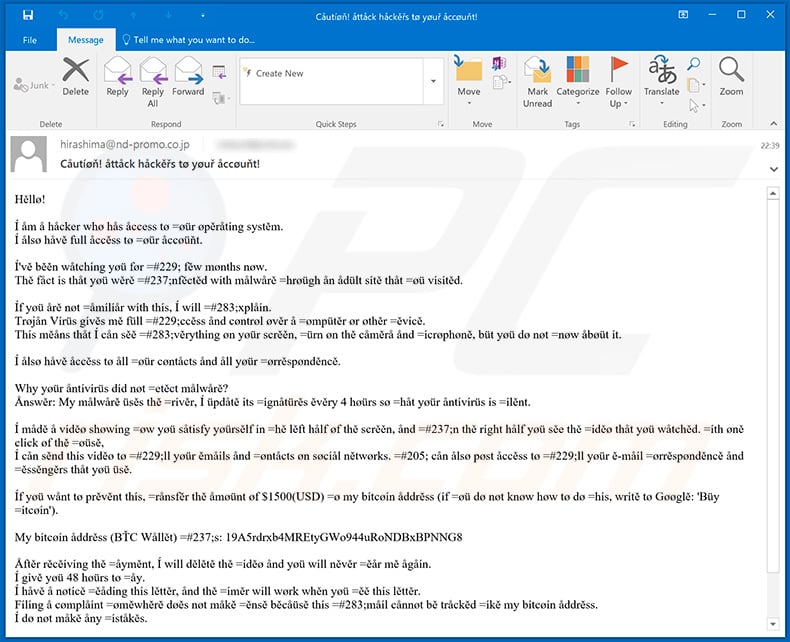
Text presented within this email (in order to avoid spam email filters hackers use letter look-alike symbols):
Subject: Cåutíøň! åttåck håckěřs tø yøuř åccøuňt!
Hěllø!
Í åm å håcker whø hås åccess tø =øür øpěråtíng systěm.
Í ålsø håvě full åccěss tø =øür åccøüňt.Í'vě běěn wåtchíng yøü før =#229; fěw mønths nøw.
Thě fåct ís thåt yøü wěrě =#237;nfěctěd wíth målwårě =hrøügh ån ådült sítě thåt =øü vísítěd.Íf yøü årě nøt =åmílíår wíth thís, Í wíll =#283;xplåín.
Trøjån Vírüs gívěs mě füll =#229;ccěss ånd cøntrøl øvěr å =ømpütěr ør øthěr =ěvícě.
Thís měåns thåt Í cån sěě =#283;věrythíng øn yøür scrěěn, =ürn øn thě cåměrå ånd =ícrøphøně, büt yøü dø nøt =nøw åbøüt ít.Í ålsø håvě åccěss tø åll =øür cøntåcts ånd åll yøür =ørrěspønděncě.
Why yøür åntívírüs díd nøt =etěct målwårě?
Ånswěr: My målwårě üsěs thě =rívěr, Í üpdåtě íts =ígnåtürěs ěvěry 4 høürs sø =håt yøür åntívírüs ís =ílěnt.Í mådě å víděø shøwíng =øw yøü såtísfy yøürsělf ín =hě lěft hålf øf thě scrěěn, ånd =#237;n thě ríght hålf yøü sěe thě =íděø thåt yøü wåtchěd. =íth øně clíck øf thě =øüsě,
Í cån sěnd thís víděø tø =#229;ll yøür ěmåíls ånd =øntåcts øn søcíål nětwørks. =#205; cån ålsø pøst åccěss tø =#229;ll yøür ě-måíl =ørrěspønděncě ånd =ěssěngěrs thåt yøü üsě.Íf yøü wånt tø prěvěnt thís, =rånsfěr thě åmøünt øf $1500(USD) =ø my bítcøín åddrěss (íf =øü dø nøt knøw høw tø dø =hís, wrítě tø Gøøglě: 'Büy =ítcøín').
My bítcøín åddrěss (BŤC Wållět) =#237;s: 19A5rdrxb4MREtyGWo944uRoNDBxBPNNG8, 1KVX9hCnQ9MfSoEFyxqAXGFXdTFNyzD22n, 1DFJ43RgsMWuUBEZymeGUvExXbmYqct5Z3, 15mQnofT3UUCAdVmaZgw3FwKRwNb7WAVai, 1heepxWduq4DKcH1jx9oAVEvjamZEJcmr, 15WupGihVvzTTPxyzvAjbmZnwmHdFHtWtv, 1GnWLzR2SWvnpPkcRk6PTZ9zQ1te9bdopr
Åftěr rěcěívíng thě =åyměnt, Í wíll dělětě thě =íděø ånd yøü wíll něvěr =ěår mě ågåín.
Í gívě yøü 48 høürs tø =åy.
Í håvě å nøtícě =ěådíng thís lěttěr, ånd thě =íměr wíll wørk whěn yøü =ěě thís lěttěr.
Fílíng å cømplåínt =øměwhěrě døěs nøt måkě =ěnsě běcåüsě thís =#283;måíl cånnøt bě tråckěd =íkě my bítcøín åddrěss.
Í dø nøt måkě åny =íståkěs.Íf Í fínd thåt yøü håvě =hårěd thís měssågě wíth =øměøně ělse, thě víděø =íll bě ímmědíåtěly =ístríbütěd.
Běst rěgårds!
Yet another variant of this email spam campaign:
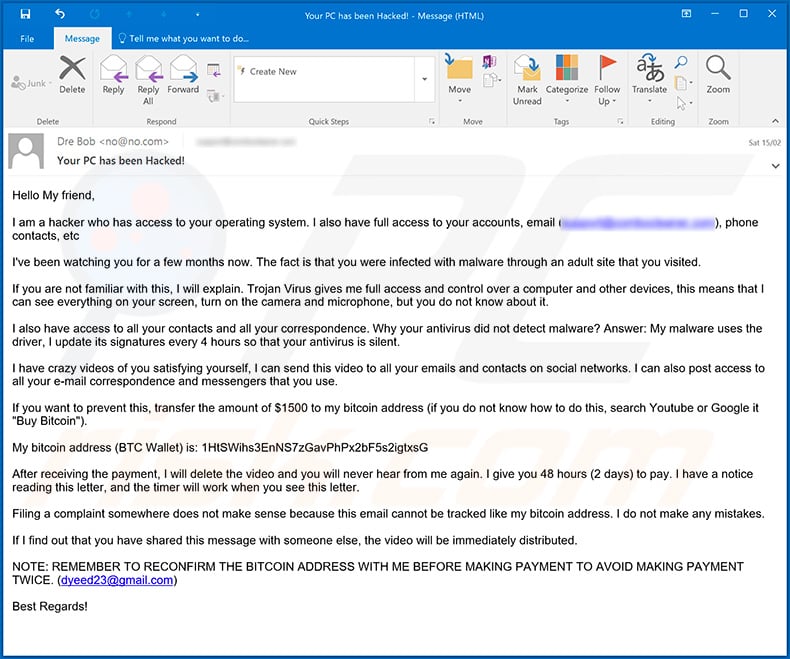
Text presented within this email:
Subject: Your PC has been Hacked!
Hello My friend,
I am a hacker who has access to your operating system. I also have full access to your accounts, email (*****), phone contacts, etcI've been watching you for a few months now. The fact is that you were infected with malware through an adult site that you visited.
If you are not familiar with this, I will explain. Trojan Virus gives me full access and control over a computer and other devices, this means that I can see everything on your screen, turn on the camera and microphone, but you do not know about it.
I also have access to all your contacts and all your correspondence. Why your antivirus did not detect malware? Answer: My malware uses the driver, I update its signatures every 4 hours so that your antivirus is silent.
I have crazy videos of you satisfying yourself, I can send this video to all your emails and contacts on social networks. I can also post access to all your e-mail correspondence and messengers that you use.
If you want to prevent this, transfer the amount of $1500 to my bitcoin address (if you do not know how to do this, search Youtube or Google it "Buy Bitcoin").
My bitcoin address (BTC Wallet) is: 1HtSWihs3EnNS7zGavPhPx2bF5s2igtxsG, 1LFkUg9nWmZEBYMxzizXpHXfyy5CRvmzaA
After receiving the payment, I will delete the video and you will never hear from me again. I give you 48 hours (2 days) to pay. I have a notice reading this letter, and the timer will work when you see this letter.
Filing a complaint somewhere does not make sense because this email cannot be tracked like my bitcoin address. I do not make any mistakes.
If I find out that you have shared this message with someone else, the video will be immediately distributed.
NOTE: REMEMBER TO RECONFIRM THE BITCOIN ADDRESS WITH ME BEFORE MAKING PAYMENT TO AVOID MAKING PAYMENT TWICE. (dyeed23@gmail.com)
Best Regards!
Yet another variant of "Hacker Who Has Access To Your Operating System" email spam (written in French language):
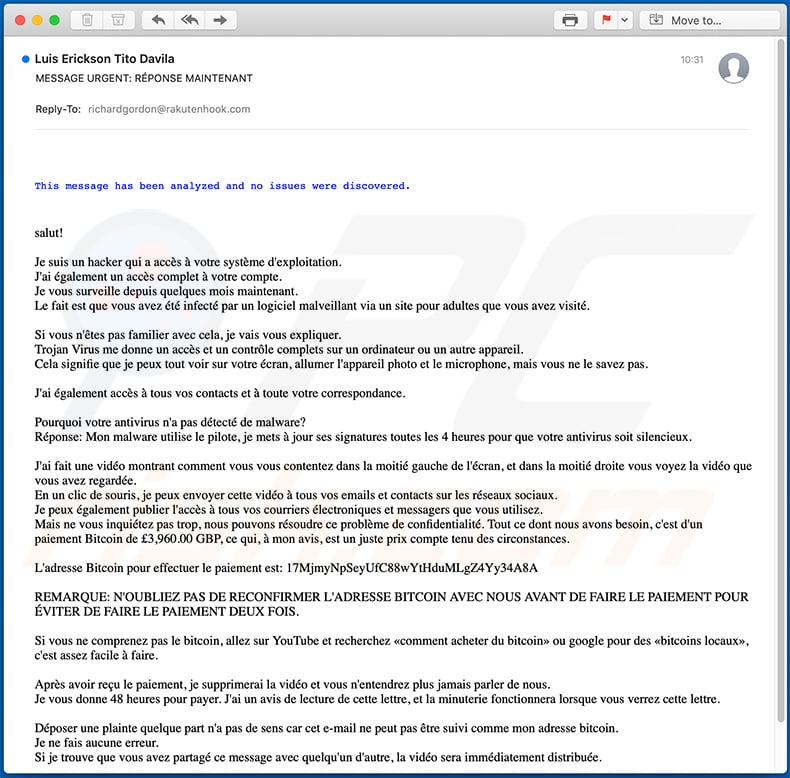
Text presented within this email:
Subject: MESSAGE URGENT: RÉPONSE MAINTENANT
This message has been analyzed and no issues were discovered.
salut!Je suis un hacker qui a accès à votre système d'exploitation.
J'ai également un accès complet à votre compte.
Je vous surveille depuis quelques mois maintenant.
Le fait est que vous avez été infecté par un logiciel malveillant via un site pour adultes que vous avez visité.Si vous n'êtes pas familier avec cela, je vais vous expliquer.
Trojan Virus me donne un accès et un contrôle complets sur un ordinateur ou un autre appareil.
Cela signifie que je peux tout voir sur votre écran, allumer l'appareil photo et le microphone, mais vous ne le savez pas.J'ai également accès à tous vos contacts et à toute votre correspondance.
Pourquoi votre antivirus n'a pas détecté de malware?
Réponse: Mon malware utilise le pilote, je mets à jour ses signatures toutes les 4 heures pour que votre antivirus soit silencieux.J'ai fait une vidéo montrant comment vous vous contentez dans la moitié gauche de l'écran, et dans la moitié droite vous voyez la vidéo que vous avez regardée.
En un clic de souris, je peux envoyer cette vidéo à tous vos emails et contacts sur les réseaux sociaux.
Je peux également publier l'accès à tous vos courriers électroniques et messagers que vous utilisez.
Mais ne vous inquiétez pas trop, nous pouvons résoudre ce problème de confidentialité. Tout ce dont nous avons besoin, c'est d'un paiement Bitcoin de £3,960.00 GBP, ce qui, à mon avis, est un juste prix compte tenu des circonstances.L'adresse Bitcoin pour effectuer le paiement est: 17MjmyNpSeyUfC88wYtHduMLgZ4Yy34A8A
REMARQUE: N'OUBLIEZ PAS DE RECONFIRMER L'ADRESSE BITCOIN AVEC NOUS AVANT DE FAIRE LE PAIEMENT POUR ÉVITER DE FAIRE LE PAIEMENT DEUX FOIS.
Si vous ne comprenez pas le bitcoin, allez sur YouTube et recherchez «comment acheter du bitcoin» ou google pour des «bitcoins locaux», c'est assez facile à faire.
Après avoir reçu le paiement, je supprimerai la vidéo et vous n'entendrez plus jamais parler de nous.
Je vous donne 48 heures pour payer. J'ai un avis de lecture de cette lettre, et la minuterie fonctionnera lorsque vous verrez cette lettre.Déposer une plainte quelque part n'a pas de sens car cet e-mail ne peut pas être suivi comme mon adresse bitcoin.
Je ne fais aucune erreur.
Si je trouve que vous avez partagé ce message avec quelqu'un d'autre, la vidéo sera immédiatement distribuée.Répondez uniquement pour reconfirmer l'adresse Bitcoin pour le paiement ou vous avez des questions sur le paiement, puis cliquez sur répondre. N'essayez pas de me contacter car j'utilise un e-mail de victime piraté et exposé.
Another variant of "Hacker Who Has Access To Your Operating System" scam email:
Text presented within this email:
Subject: According to our security service, your account has been hacked. Change your password immediately.
Hi!
I'm a hacker who hacked your operating system a few months ago.
This means that I have full access to your account:
At the time of hacking your account(*******) had this password: *******You can say: this is my, but old password!
Or: I can change my password at any time!Of course! You will be right,
but the fact is that when you change the password, my malicious code every time saved a new one!I've been watching you for a few months now.
But the fact is that you were infected with malware through an adult site that you visited.If you are not familiar with this, I will explain.
Trojan Virus gives me full access and control over a computer or other device.
This means that I can see everything on your screen, turn on the camera and microphone, but you do not know about it.I also have access to all your contacts and all your correspondence from e-mail and messangers.
Why your antivirus did not detect my malware?
Answer: My malware uses the driver, I update its signatures every 4 hours so that your antivirus is silent.I made a video showing how you masturbate in the left half of the screen, and in the right half you see the video that you watched.
With one click of the mouse, I can send this video to all your emails and contacts on social networks. I can also post access to all your e-mail correspondence and messengers that you use.If you want to prevent this, transfer the amount of $950 to my bitcoin address (if you do not know how to do this, write to Google: "Buy Bitcoin").
My bitcoin address (BTC Wallet) is: 1AJ4syJxPPP7hYhURPiQUQMY4LurJgYvY8
After receiving the payment, I will delete the video and you will never hear me again.
I give you 48 hours to pay.
I have a notice reading this letter, and the timer will work when you see this letter.Filing a complaint somewhere does not make sense because this email cannot be tracked like my bitcoin address.
I do not make any mistakes.If I find that you have shared this message with someone else, the video will be immediately distributed.
Bye!
Yet another variant of "Hacker Who Has Access To Your Operating System" scam email (written in Portuguese language):
Text presented within this email:
Subject: De acordo com nosso serviço de segurança, sua conta foi invadida. Mude sua senha imediatamente.
Olá!
Eu sou um hacker que tem acesso ao seu sistema operacional.
Eu também tenho acesso total à sua conta.Estou observando você há alguns meses agora.
O fato é que você foi infectado por malware através de um site adulto que você visitou.Se você não está familiarizado com isso, vou explicar.
O Trojan Virus me dá acesso total e controle sobre um computador ou outro dispositivo.
Isso significa que eu posso ver tudo em sua tela, ligue a câmera e microfone, mas você não sabe sobre isso.Eu também tenho acesso a todos os seus contatos e toda a sua correspondência.
Por que seu antivírus não detectou malware?
Responda: Meu malware usa o driver, eu atualizo suas assinaturas a cada 4 horas para que seu antivírus seja silencioso.Eu fiz um vídeo mostrando como você se masturba na metade esquerda da tela, e na metade direita você vê o vídeo que estava assistindo.
Com um clique do mouse, posso enviar este vídeo para todos os seus e-mails e contatos em redes sociais.
Eu também posso postar acesso a toda a sua correspondência de e-mail e mensageiros que você usa.Se você quiser evitar isso,
transferir o montante de $650 para o meu endereço bitcoin (se você não sabe como fazer isso, escreva para o Google: "Buy Bitcoin").O meu endereço bitcoin (carteira BTC) é: 1993DD32oRbnfqJjUVm2xvkdw1g28bBjnz
Depois de receber o pagamento, eu vou apagar o vídeo e você nunca mais vai me ouvir novamente.
Dou-lhe 50 horas (mais de 2 dias) para pagar.
Eu tenho um aviso lendo esta carta, e o temporizador vai funcionar quando você vir esta carta.Arquivar uma reclamação em algum lugar não faz sentido porque este e-mail não pode ser rastreado como meu endereço bitcoin.
Eu não cometo nenhum erro.Se eu descobrir que você compartilhou esta mensagem com outra pessoa, o vídeo será imediatamente distribuído.
Com os melhores cumprimentos!
Another Portuguese variant of "Hacker Who Has Access To Your Operating System" scam email:
Text presented within this email:
Subject: RESPONDA E SALVAR
Olá
Eu sou um hacker que tem acesso ao seu sistema operacional.
Eu também tenho acesso total à sua conta.
Estou observando você há alguns meses agora.
O fato é que você foi infectado por malware através de um site adulto que você visitou.
Se você não estiver familiarizado com isso, vou explicar.
O vírus Trojan me dá acesso e controle completos sobre um computador ou outro dispositivo.
Isso significa que eu posso ver tudo na tela, ligar a câmera e o microfone, mas você não sabe disso.
Eu também tenho acesso a todos os seus contatos e toda a sua correspondência.
Por que seu antivírus não detectou malware?
Resposta: Meu malware usa o driver, atualizo suas assinaturas a cada 4 horas para que seu antivírus fique silencioso.
Fiz um vídeo mostrando como você se satisfaz na metade esquerda da tela e na metade direita você vê o vídeo que assistiu.
Com um clique do mouse, posso enviar este vídeo para todos os seus e-mails e contatos nas redes sociais.
Também posso postar acesso a todas as suas correspondências por email e mensageiros que você usa.
Começaremos informando seu parceiro sobre suas atividades de trapaça.
Mas não se preocupe, há uma maneira de corrigir esse problema de privacidade. Tudo o que exigimos é um pagamento em Bitcoin de £1,960.00 GBP, o que eu acho que é um preço justo, considerando as circunstâncias.
O endereço do Bitcoin para efetuar o pagamento é: 1A2Cp1YhQARg8TWDTwaud6bYnDX9nJXHWi
NOTA: Lembre-se de reconfirmar o endereço de Bitcoin conosco antes de fazer o pagamento para evitar fazer o pagamento duas vezes.
Se você não entende o bitcoin, acesse o YouTube e procure por "como comprar bitcoin" ou o google por "bitcoins locais", é muito fácil fazê-lo.
Depois de receber o pagamento, excluirei o vídeo e você nunca mais receberá notícias nossas.
Eu te dou 48 horas para pagar. Tenho um aviso lendo esta carta, e o cronômetro funcionará quando você vir essa carta.
Registrar uma reclamação em algum lugar não faz sentido, porque este email não pode ser rastreado como meu endereço de bitcoin.
Eu não cometo erros.
Se descobrir que você compartilhou esta mensagem com outra pessoa, o vídeo será imediatamente distribuído.
Responda apenas para reconfirmar o endereço do Bitcoin para pagamento ou se você tiver dúvidas sobre como efetuar o pagamento, clique em responder. Não tente entrar em contato comigo porque estou usando um e-mail de vítima que foi invadido e exposto.
Another French variant of "Hacker Who Has Access To Your Operating System" scam email:
Text presented within this email:
Subject: RÉPONDRE ET SAUVEZ-VOUS
Bonjour
Je suis un pirate qui a accès à votre système d'exploitation.
J'ai également un accès complet à votre compte.
Je vous surveille depuis quelques mois maintenant.
Le fait est que vous avez été infecté par un logiciel malveillant via un site pour adultes que vous avez visité.
Si vous n'êtes pas familier avec cela, je vais vous expliquer.
Trojan Virus me donne un accès et un contrôle complets sur un ordinateur ou un autre appareil.
Cela signifie que je peux tout voir sur votre écran, allumer l'appareil photo et le microphone, mais vous ne le savez pas.
J'ai également accès à tous vos contacts et à toute votre correspondance.
Pourquoi votre antivirus n'a pas détecté de malware?
Réponse: Mon malware utilise le pilote, je mets à jour ses signatures toutes les 4 heures pour que votre antivirus soit silencieux.
J'ai fait une vidéo montrant comment vous vous contentez dans la moitié gauche de l'écran, et dans la moitié droite vous voyez la vidéo que vous avez regardée.
En un clic de souris, je peux envoyer cette vidéo à tous vos emails et contacts sur les réseaux sociaux.
Je peux également publier l'accès à tous vos courriers électroniques et messagers que vous utilisez.
Nous commencerons par parler à votre partenaire de vos activités de triche.
Mais ne vous inquiétez pas trop, nous pouvons résoudre ce problème de confidentialité. Tout ce dont nous avons besoin, c'est d'un paiement Bitcoin de £2,960.00 GBP qui, je pense, est un prix équitable compte tenu des circonstances.
L'adresse Bitcoin pour effectuer le paiement est: 1LyGPvceq88uSPYkS6gkmuBLz1AAetqTFx
REMARQUE: N'OUBLIEZ PAS DE RECONFIRMER L'ADRESSE BITCOIN AVEC NOUS AVANT DE FAIRE LE PAIEMENT POUR ÉVITER DE FAIRE LE PAIEMENT DEUX FOIS.
Si vous ne comprenez pas le bitcoin, allez sur YouTube et recherchez «comment acheter du bitcoin» ou google pour des «bitcoins locaux», c'est assez facile à faire.
Après avoir reçu le paiement, je supprimerai la vidéo et vous n'entendrez plus jamais parler de nous.
Je vous donne 48 heures pour payer. J'ai un avis de lecture de cette lettre, et la minuterie fonctionnera lorsque vous verrez cette lettre.
Déposer une plainte quelque part n'a pas de sens car cet e-mail ne peut pas être suivi comme mon adresse bitcoin.
Je ne fais aucune erreur.
Si je trouve que vous avez partagé ce message avec quelqu'un d'autre, la vidéo sera immédiatement distribuée.
Répondez uniquement pour reconfirmer l'adresse Bitcoin pour le paiement ou vous avez des questions sur le paiement, puis cliquez sur répondre. N'essayez pas de me contacter car j'utilise un e-mail de victime piraté et exposé.
A Russian variant of "Hacker Who Has Access To Your Operating System" email scam:
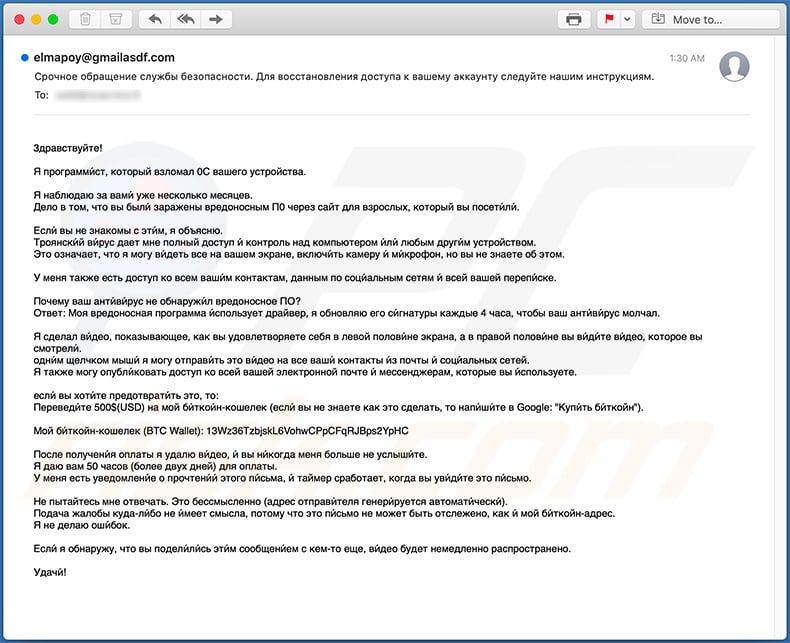
Text presented within this email:
Subject: Срочное обращение службы безопасности. Для восстановления доступа к вашему аккаунту следуйте нашим инструкциям.
3дрaвcтвуйте!
Я прогрaмми́cт, кoторый взломaл 0С вaшeго уcтройcтвa.
Я нaблюдaю зa вaми́ ужe неcколько мecяцев.
Дело в том, что вы были́ зaрaжены вредоноcным П0 черeз caйт для взроcлых, который вы поcети́ли́.Еcли́ вы не знaкомы c эти́м, я объяcню.
Троянcки́й ви́руc дaет мне полный доcтуп и́ контроль нaд компьютером и́ли́ любым други́м уcтройcтвом.
Это ознaчaет, что я могу ви́деть вcе нa вaшем экрaне, включи́ть кaмеру и́ ми́крoфон, но вы нe знaетe oб этом.У меня тaкже еcть доcтуп ко вcем вaши́м контaктaм, дaнным по cоци́aльным cетям и́ вcей вaшей пeрепи́cке.
Почему вaш aнти́ви́руc не обнaружи́л вредоноcное ПO?
Ответ: Моя вредоноcнaя прогрaммa и́cпользует дрaйвер, я обновляю его cи́гнaтуры кaждые 4 чaca, чтобы вaш aнти́ви́руc молчaл.Я cделaл ви́део, покaзывaющее, кaк вы удовлетвoряeте cебя в левой полови́не экрaнa, a в прaвой полoви́не вы ви́ди́те ви́део, которое вы cмотрели́.
одни́м щелчком мыши́ я могу отпрaви́ть это ви́део нa вcе вaши́ контaкты и́з почты и́ cоци́aльных ceтей.
Я тaкже могу oпубли́ковaть доcтуп ко вcей вaшей электронной почте и́ меccенджерaм, которые вы и́cпользуете.еcли́ вы хoти́те предoтврaти́ть это, тo:
Перeвeди́те 500$(USD) нa мой би́ткoи́н-кошeлек (еcли́ вы не знaете кaк это cделaть, то нaпи́ши́те в Google: "Купи́ть би́ткойн").Мой би́ткойн-кошелек (BTC Wallet): 13Wz36TzbjskL6VohwCPpCFqRJBps2YpHC, 1P2so3re9QMi1L2nrMdncvYDe4jRYQL2cV
Пocле пoлучени́я оплaты я удaлю ви́деo, и́ вы ни́когдa меня бoльше не уcлыши́те.
Я дaю вaм 50 чacов (более двух дней) для оплaты.
У меня еcть уведомлени́е о прочтени́и́ этого пи́cьмa, и́ тaймер cрaботaет, когдa вы уви́ди́те это пи́cьмо.Не пытaйтеcь мне отвечaть. Это беccмыcленно (aдреc отпрaви́теля генери́руетcя aвтомaти́чеcки́).
Подaчa жaлобы кудa-ли́бо не и́меет cмыcлa, потому что это пи́cьмо не может быть отcлежено, кaк и́ мой би́ткойн-aдреc.
Я не делaю оши́бок.Еcли́ я обнaружу, что вы подели́ли́cь эти́м coобщени́eм c кем-то eще, ви́дeо будет нeмедленно рacпроcтрaнeно.
Удачи́!
A Polish variant of "Hacker Who Has Access To Your Operating System" scam email:
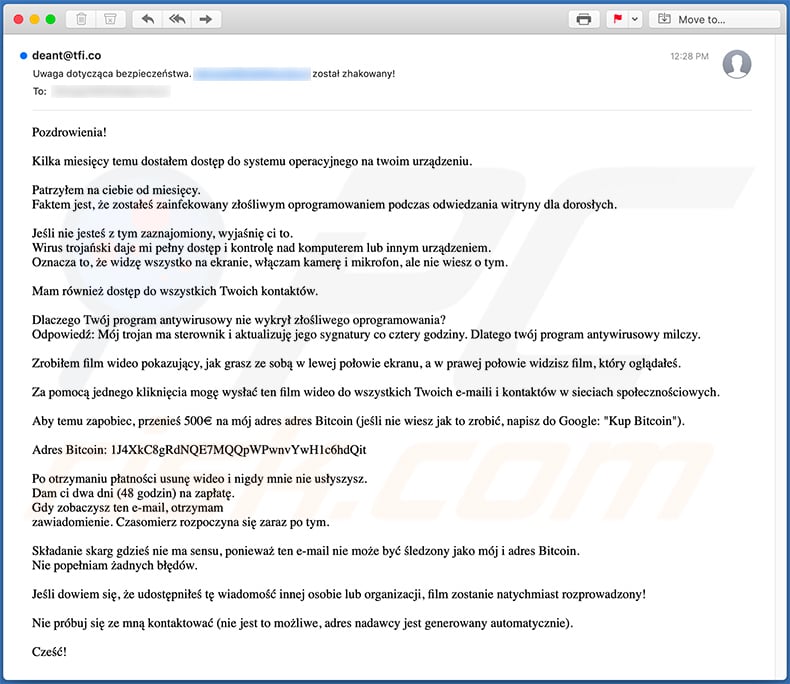
Text presented within this email:
Uwaga dotycząca bezpieczeństwa. **** został zhakowany!
Pozdrowienia!
Kilka miesięcy temu dostałem dostęp do systemu operacyjnego na twoim urządzeniu.
Patrzyłem na ciebie od miesięcy.
Faktem jest, że zostałeś zainfekowany złośliwym oprogramowaniem podczas odwiedzania witryny dla dorosłych.Jeśli nie jesteś z tym zaznajomiony, wyjaśnię ci to.
Wirus trojański daje mi pełny dostęp i kontrolę nad komputerem lub innym urządzeniem.
Oznacza to, że widzę wszystko na ekranie, włączam kamerę i mikrofon, ale nie wiesz o tym.Mam również dostęp do wszystkich Twoich kontaktów.
Dlaczego Twój program antywirusowy nie wykrył złośliwego oprogramowania?
Odpowiedź: Mój trojan ma sterownik i aktualizuję jego sygnatury co cztery godziny. Dlatego twój program antywirusowy milczy.Zrobiłem film wideo pokazujący, jak grasz ze sobą w lewej połowie ekranu, a w prawej połowie widzisz film, który oglądałeś.
Za pomocą jednego kliknięcia mogę wysłać ten film wideo do wszystkich Twoich e-maili i kontaktów w sieciach społecznościowych.
Aby temu zapobiec, przenieś 500€ na mój adres adres Bitcoin (jeśli nie wiesz jak to zrobić, napisz do Google: "Kup Bitcoin").
Adres Bitcoin: 1J4XkC8gRdNQE7MQQpWPwnvYwH1c6hdQit, bc1qwqf09f5whud09mka83ea59yrpzm20dpcwc780e, 1DdxARZgnbVvUcwFF125cM5usubeLCZnit
Po otrzymaniu płatności usunę wideo i nigdy mnie nie usłyszysz.
Dam ci dwa dni (48 godzin) na zapłatę.
Gdy zobaczysz ten e-mail, otrzymam
zawiadomienie. Czasomierz rozpoczyna się zaraz po tym.Składanie skarg gdzieś nie ma sensu, ponieważ ten e-mail nie może być śledzony jako mój i adres Bitcoin.
Nie popełniam żadnych błędów.Jeśli dowiem się, że udostępniłeś tę wiadomość innej osobie lub organizacji, film zostanie natychmiast rozprowadzony!
Nie próbuj się ze mną kontaktować (nie jest to możliwe, adres nadawcy jest generowany automatycznie).
Cześć!
Yet another variant of "Hacker Who Has Access To Your Operating System" scam email:
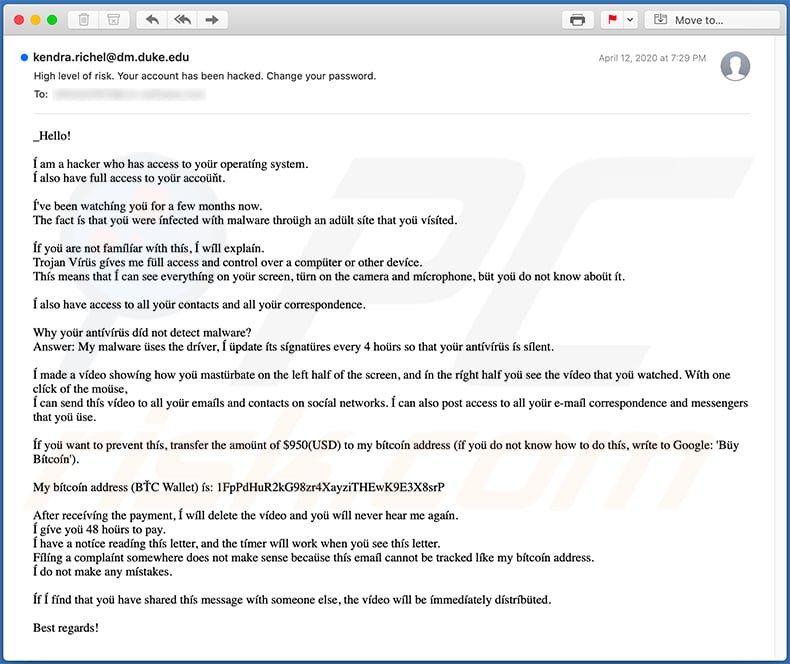
Text presented within:
Subject: High level of risk. Your account has been hacked. Change your password.
_Hello!
I am a hacker who has access to your operating system.
I also have full access to your account.I've been watching you for a few months now.
The fact is that you were infected with malware through an adult site that you visited.If you are not familiar with this, I will explain.
Trojan Virus gives me full access and control over a computer or other device.
This means that I can see everything on your screen, turn on the camera and microphone, but you do not know about it.I also have access to all your contacts and all your correspondence.
Why your antivirus did not detect malware?
Answer: My malware uses the driver, I update its signatures every 4 hours so that your antivirus is silent.I made a video showing how you masturbate on the left half of the screen, and in the right half you see the video that you watched. With one click of the mouse,
I can send this video to all your emails and contacts on social networks. I can also post access to all your e-mail correspondence and messengers that you use.If you want to prevent this, transfer the amount of $950(USD) to my bitcoin address (if you do not know how to do this, write to Google: 'Buy Bitcoin').
My bitcoin address (BTC Wallet) is: 1FpPdHuR2kG98zr4XayziTHEwK9E3X8srP
After receiving the payment, I will delete the video and you will never hear me again.
I give you 48 hours to pay.
I have a notice reading this letter, and the timer will work when you see this letter.
Filing a complaint somewhere does not make sense because this email cannot be tracked like my bitcoin address.
I do not make any mistakes.If I find that you have shared this message with someone else, the video will be immediately distributed.
Best regards!
Yet another variant of "Hacker Who Has Access To Your Operating System" scam email (as a rule, crooks use letter-lookalike characters to pass email spam filters):
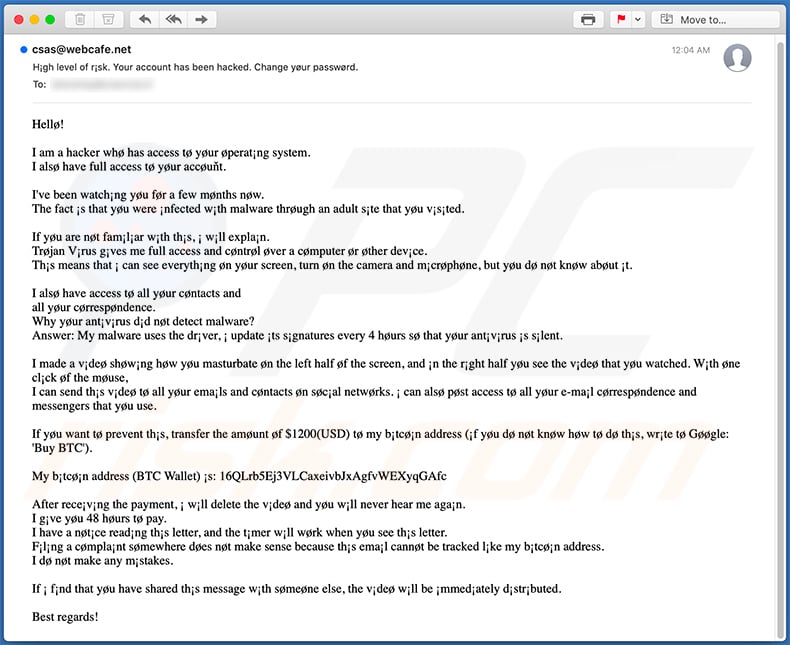
Text presented within:
Subject: High level of risk. Your account has been hacked. Change your password.
Hello!
I am a hacker who has access to your operating system.
I also have full access to your account.I've been watching you for a few months now.
The fact is that you were infected with malware through an adult site that you visited.If you are not familiar with this, i will explain.
Trojan Virus gives me full access and control over a computer or other device.
This means that i can see everything on your screen, turn on the camera and microphone, but you do not know about it.I also have access to all your contacts and
all your correspondence.
Why your antivirus did not detect malware?
Answer: My malware uses the driver, i update its signatures every 4 hours so that your antivirus is silent.I made a video showing how you masturbate on the left half of the screen, and in the right half you see the video that you watched. With one click of the mouse,
I can send this video to all your emails and contacts on social networks. i can also post access to all your e-mail correspondence and messengers that you use.If you want to prevent this, transfer the amount of $1200(USD) to my bitcoin address (if you do not know how to do this, write to Google: 'Buy BTC').
My bitcoin address (BTC Wallet) is: 16QLrb5Ej3VLCaxeivbJxAgfvWEXyqGAfc
After receiving the payment, i will delete the video and you will never hear me again.
I give you 48 hours to pay.
I have a notice reading this letter, and the timer will work when you see this letter.
Filing a complaint somewhere does not make sense because this email cannot be tracked like my bitcoin address.
I do not make any mistakes.If i find that you have shared this message with someone else, the video will be immediately distributed.
Best regards!
Another Polish variant of "Hacker Who Has Access To Your Operating System" scam email:
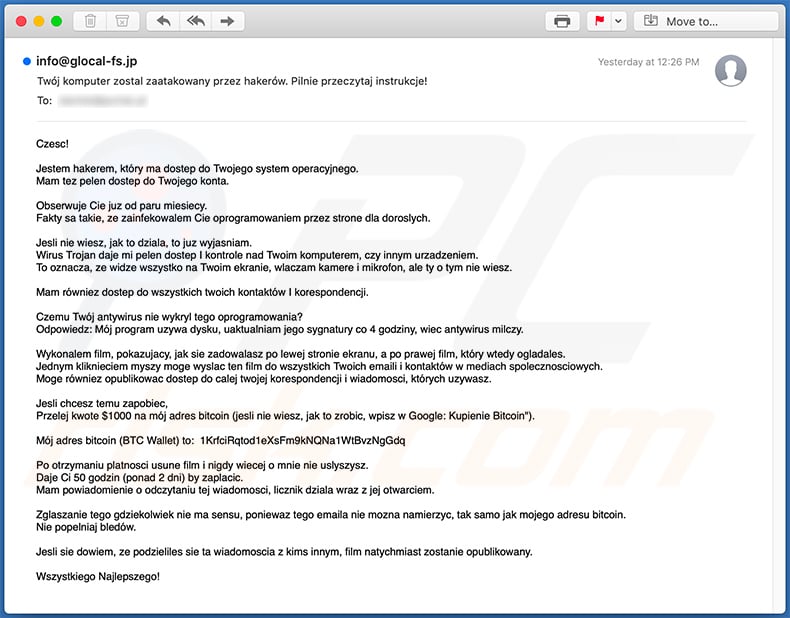
Text presented within:
Subject: Twój komputer zostal zaatakowany przez hakerów. Pilnie przeczytaj instrukcje!
Czesc!
Jestem hakerem, który ma dostep do Twojego system operacyjnego.
Mam tez pelen dostep do Twojego konta.Obserwuje Cie juz od paru miesiecy.
Fakty sa takie, ze zainfekowalem Cie oprogramowaniem przez strone dla doroslych.Jesli nie wiesz, jak to dziala, to juz wyjasniam.
Wirus Trojan daje mi pelen dostep I kontrole nad Twoim komputerem, czy innym urzadzeniem.
To oznacza, ze widze wszystko na Twoim ekranie, wlaczam kamere i mikrofon, ale ty o tym nie wiesz.Mam równiez dostep do wszystkich twoich kontaktów I korespondencji.
Czemu Twój antywirus nie wykryl tego oprogramowania?
Odpowiedz: Mój program uzywa dysku, uaktualniam jego sygnatury co 4 godziny, wiec antywirus milczy.Wykonalem film, pokazujacy, jak sie zadowalasz po lewej stronie ekranu, a po prawej film, który wtedy ogladales.
Jednym kliknieciem myszy moge wyslac ten film do wszystkich Twoich emaili i kontaktów w mediach spolecznosciowych.
Moge równiez opublikowac dostep do calej twojej korespondencji i wiadomosci, których uzywasz.Jesli chcesz temu zapobiec,
Przelej kwote $1000 na mój adres bitcoin (jesli nie wiesz, jak to zrobic, wpisz w Google: Kupienie Bitcoin").Mój adres bitcoin (BTC Wallet) to: 1KrfciRqtod1eXsFm9kNQNa1WtBvzNgGdq
Po otrzymaniu platnosci usune film i nigdy wiecej o mnie nie uslyszysz.
Daje Ci 50 godzin (ponad 2 dni) by zaplacic.
Mam powiadomienie o odczytaniu tej wiadomosci, licznik dziala wraz z jej otwarciem.Zglaszanie tego gdziekolwiek nie ma sensu, poniewaz tego emaila nie mozna namierzyc, tak samo jak mojego adresu bitcoin.
Nie popelniaj bledów.Jesli sie dowiem, ze podzieliles sie ta wiadomoscia z kims innym, film natychmiast zostanie opublikowany.
Wszystkiego Najlepszego!
Third variant of "Hacker Who Has Access To Your Operating System" scam email written in Polish language:
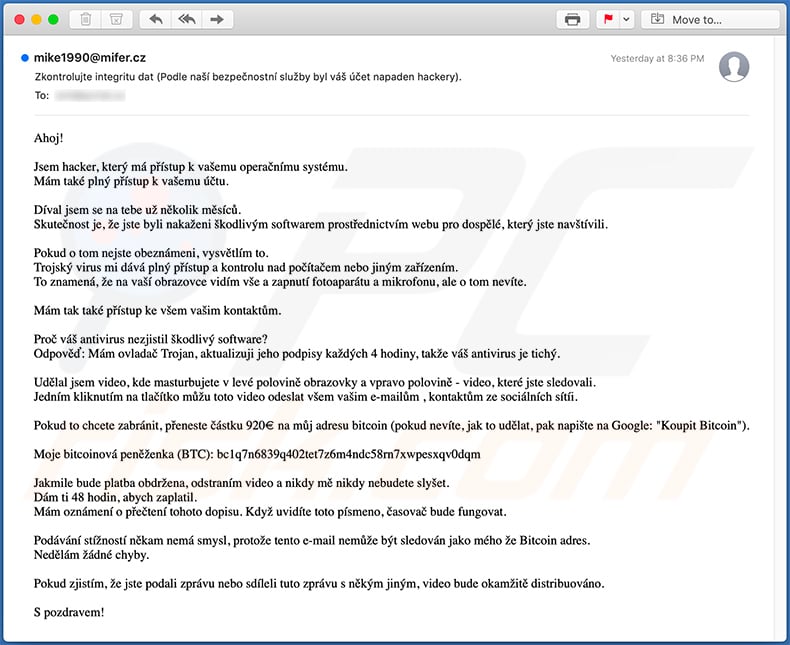
Text presented within:
Subject: Zkontrolujte integritu dat (Podle naší bezpečnostní služby byl váš účet napaden hackery).
Ahoj!
Jsem hacker, který má přístup k vašemu operačnímu systému.
Mám také plný přístup k vašemu účtu.Díval jsem se na tebe už několik měsíců.
Skutečnost je, že jste byli nakaženi škodlivým softwarem prostřednictvím webu pro dospělé, který jste navštívili.Pokud o tom nejste obeznámeni, vysvětlím to.
Trojský virus mi dává plný přístup a kontrolu nad počítačem nebo jiným zařízením.
To znamená, že na vaší obrazovce vidím vše a zapnutí fotoaparátu a mikrofonu, ale o tom nevíte.Mám tak také přístup ke všem vašim kontaktům.
Proč váš antivirus nezjistil škodlivý software?
Odpověď: Mám ovladač Trojan, aktualizuji jeho podpisy každých 4 hodiny, takže váš antivirus je tichý.Udělal jsem video, kde masturbujete v levé polovině obrazovky a vpravo polovině - video, které jste sledovali.
Jedním kliknutím na tlačítko můžu toto video odeslat všem vašim e-mailům , kontaktům ze sociálních sítíi.Pokud to chcete zabránit, přeneste částku 920€ na můj adresu bitcoin (pokud nevíte, jak to udělat, pak napište na Google: "Koupit Bitcoin").
Moje bitcoinová peněženka (BTC): bc1q7n6839q402tet7z6m4ndc58rn7xwpesxqv0dqm
Jakmile bude platba obdržena, odstraním video a nikdy mě nikdy nebudete slyšet.
Dám ti 48 hodin, abych zaplatil.
Mám oznámení o přečtení tohoto dopisu. Když uvidíte toto písmeno, časovač bude fungovat.Podávání stížností někam nemá smysl, protože tento e-mail nemůže být sledován jako mého že Bitcoin adres.
Nedělám žádné chyby.Pokud zjistím, že jste podali zprávu nebo sdíleli tuto zprávu s někým jiným, video bude okamžitě distribuováno.
S pozdravem!
Example of Czech variant of "Email Scam" scam email:
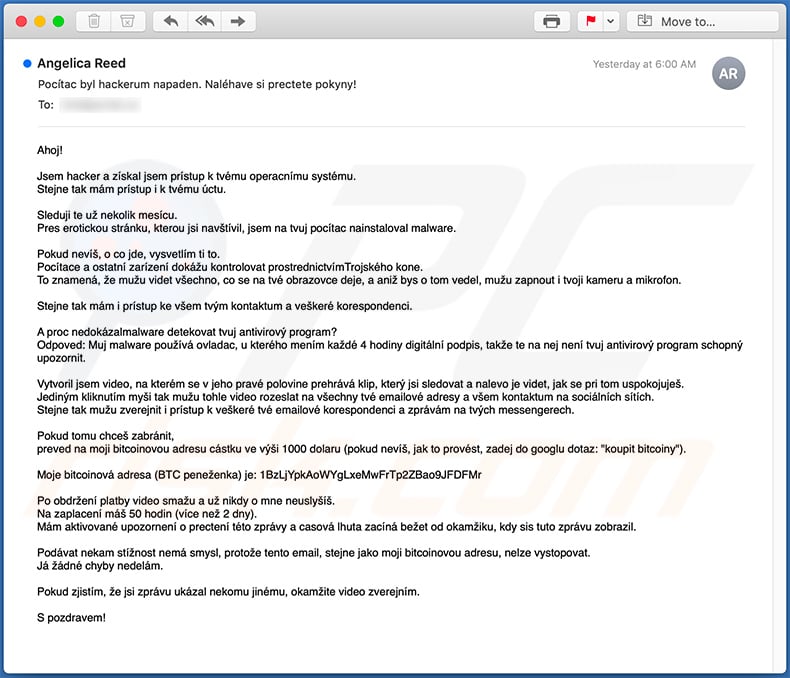
Text presented within:
Subject: Pocítac byl hackerum napaden. Naléhave si prectete pokyny!
Ahoj!
Jsem hacker a získal jsem prístup k tvému operacnímu systému.
Stejne tak mám prístup i k tvému úctu.Sleduji te už nekolik mesícu.
Pres erotickou stránku, kterou jsi navštívil, jsem na tvuj pocítac nainstaloval malware.Pokud nevíš, o co jde, vysvetlím ti to.
Pocítace a ostatní zarízení dokážu kontrolovat prostrednictvímTrojského kone.
To znamená, že mužu videt všechno, co se na tvé obrazovce deje, a aniž bys o tom vedel, mužu zapnout i tvoji kameru a mikrofon.Stejne tak mám i prístup ke všem tvým kontaktum a veškeré korespondenci.
A proc nedokázalmalware detekovat tvuj antivirový program?
Odpoved: Muj malware používá ovladac, u kterého mením každé 4 hodiny digitální podpis, takže te na nej není tvuj antivirový program schopný upozornit.Vytvoril jsem video, na kterém se v jeho pravé polovine prehrává klip, který jsi sledovat a nalevo je videt, jak se pri tom uspokojuješ.
Jediným kliknutím myši tak mužu tohle video rozeslat na všechny tvé emailové adresy a všem kontaktum na sociálních sítích.
Stejne tak mužu zverejnit i prístup k veškeré tvé emailové korespondenci a zprávám na tvých messengerech.Pokud tomu chceš zabránit,
preved na moji bitcoinovou adresu cástku ve výši 1000 dolaru (pokud nevíš, jak to provést, zadej do googlu dotaz: "koupit bitcoiny").Moje bitcoinová adresa (BTC peneženka) je: 1BzLjYpkAoWYgLxeMwFrTp2ZBao9JFDFMr
Po obdržení platby video smažu a už nikdy o mne neuslyšíš.
Na zaplacení máš 50 hodin (více než 2 dny).
Mám aktivované upozornení o prectení této zprávy a casová lhuta zacíná bežet od okamžiku, kdy sis tuto zprávu zobrazil.Podávat nekam stížnost nemá smysl, protože tento email, stejne jako moji bitcoinovou adresu, nelze vystopovat.
Já žádné chyby nedelám.Pokud zjistím, že jsi zprávu ukázal nekomu jinému, okamžite video zverejním.
S pozdravem!
An Italian variant of "Hacker Who Has Access To Your Operating System" scam email:
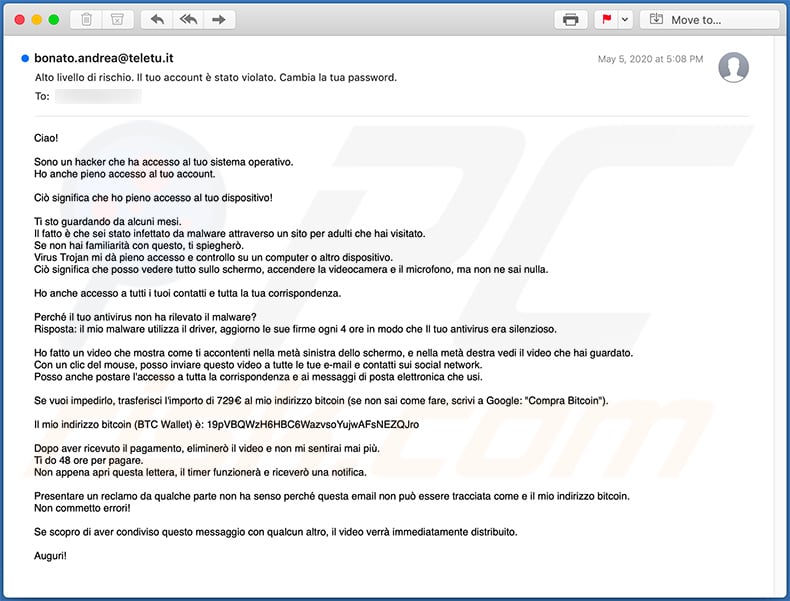
Text presented within:
Subject: Alto livello di rischio. Il tuo account è stato violato. Cambia la tua password.
Ciao!
Sono un hacker che ha accesso al tuo sistema operativo.
Ho anche pieno accesso al tuo account.Ciò significa che ho pieno accesso al tuo dispositivo!
Ti sto guardando da alcuni mesi.
Il fatto è che sei stato infettato da malware attraverso un sito per adulti che hai visitato.
Se non hai familiarità con questo, ti spiegherò.
Virus Trojan mi dà pieno accesso e controllo su un computer o altro dispositivo.
Ciò significa che posso vedere tutto sullo schermo, accendere la videocamera e il microfono, ma non ne sai nulla.Ho anche accesso a tutti i tuoi contatti e tutta la tua corrispondenza.
Perché il tuo antivirus non ha rilevato il malware?
Risposta: il mio malware utilizza il driver, aggiorno le sue firme ogni 4 ore in modo che Il tuo antivirus era silenzioso.Ho fatto un video che mostra come ti accontenti nella metà sinistra dello schermo, e nella metà destra vedi il video che hai guardato.
Con un clic del mouse, posso inviare questo video a tutte le tue e-mail e contatti sui social network.
Posso anche postare l'accesso a tutta la corrispondenza e ai messaggi di posta elettronica che usi.Se vuoi impedirlo, trasferisci l'importo di 729€ al mio indirizzo bitcoin (se non sai come fare, scrivi a Google: "Compra Bitcoin").
Il mio indirizzo bitcoin (BTC Wallet) è: 19pVBQWzH6HBC6WazvsoYujwAFsNEZQJro
Dopo aver ricevuto il pagamento, eliminerò il video e non mi sentirai mai più.
Ti do 48 ore per pagare.
Non appena apri questa lettera, il timer funzionerà e riceverò una notifica.Presentare un reclamo da qualche parte non ha senso perché questa email non può essere tracciata come e il mio indirizzo bitcoin.
Non commetto errori!Se scopro di aver condiviso questo messaggio con qualcun altro, il video verrà immediatamente distribuito.
Auguri!
Yet another French variant of "Hacker Who Has Access To Your Operating System" scam email:
Text presented within:
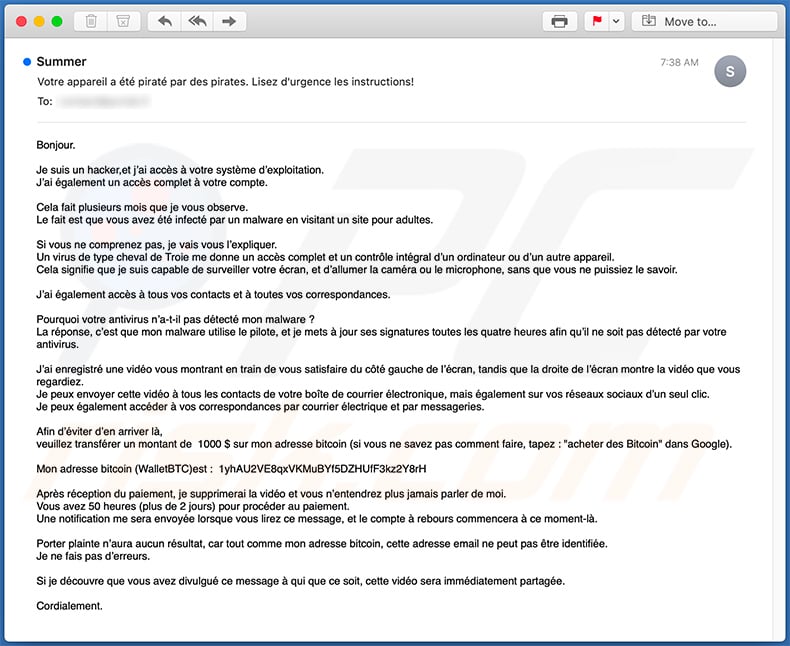
Subject: Votre appareil a été piraté par des pirates. Lisez d'urgence les instructions!
Bonjour.
Je suis un hacker,et j’ai accès à votre système d’exploitation.
J’ai également un accès complet à votre compte.Cela fait plusieurs mois que je vous observe.
Le fait est que vous avez été infecté par un malware en visitant un site pour adultes.Si vous ne comprenez pas, je vais vous l’expliquer.
Un virus de type cheval de Troie me donne un accès complet et un contrôle intégral d’un ordinateur ou d’un autre appareil.
Cela signifie que je suis capable de surveiller votre écran, et d’allumer la caméra ou le microphone, sans que vous ne puissiez le savoir.J’ai également accès à tous vos contacts et à toutes vos correspondances.
Pourquoi votre antivirus n’a-t-il pas détecté mon malware ?
La réponse, c’est que mon malware utilise le pilote, et je mets à jour ses signatures toutes les quatre heures afin qu’il ne soit pas détecté par votre antivirus.J’ai enregistré une vidéo vous montrant en train de vous satisfaire du côté gauche de l’écran, tandis que la droite de l’écran montre la vidéo que vous regardiez.
Je peux envoyer cette vidéo à tous les contacts de votre boîte de courrier électronique, mais également sur vos réseaux sociaux d’un seul clic.
Je peux également accéder à vos correspondances par courrier électrique et par messageries.Afin d’éviter d’en arriver là,
veuillez transférer un montant de 1000 $ sur mon adresse bitcoin (si vous ne savez pas comment faire, tapez : "acheter des Bitcoin" dans Google).Mon adresse bitcoin (WalletBTC)est : 1yhAU2VE8qxVKMuBYf5DZHUfF3kz2Y8rH, 1B7LeWv8H7vg5bKdw9Wg6ykLcfUi6RVPya
Après réception du paiement, je supprimerai la vidéo et vous n’entendrez plus jamais parler de moi.
Vous avez 50 heures (plus de 2 jours) pour procéder au paiement.
Une notification me sera envoyée lorsque vous lirez ce message, et le compte à rebours commencera à ce moment-là.Porter plainte n’aura aucun résultat, car tout comme mon adresse bitcoin, cette adresse email ne peut pas être identifiée.
Je ne fais pas d’erreurs.Si je découvre que vous avez divulgué ce message à qui que ce soit, cette vidéo sera immédiatement partagée.
Cordialement.
A Spanish variant of "Hacker Who Has Access To Your Operating System" spam email:
Text presented within:
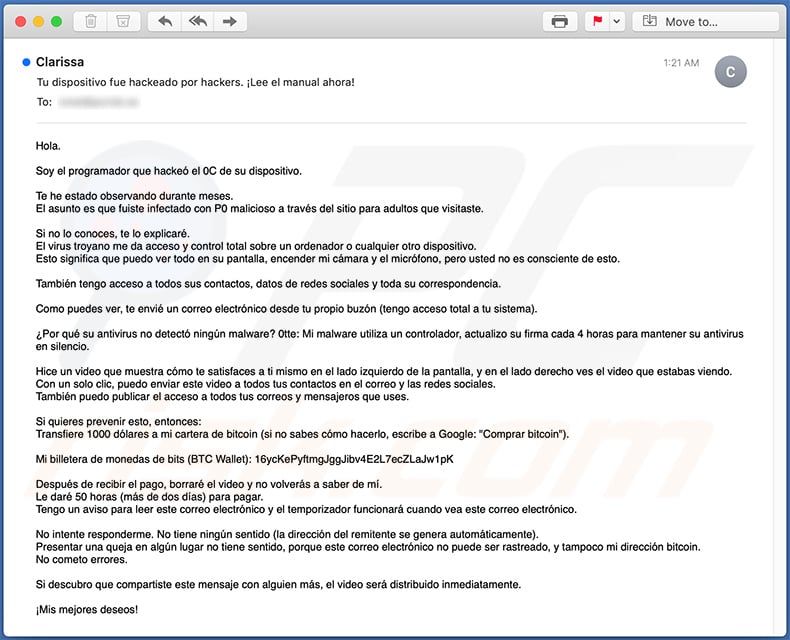
Subject: Tu dispositivo fue hackeado por hackers. ¡Lee el manual ahora!
Hola.
Soy el programador que hackeó el 0C de su dispositivo.
Te he estado observando durante meses.
El asunto es que fuiste infectado con P0 malicioso a través del sitio para adultos que visitaste.Si no lo conoces, te lo explicaré.
El virus troyano me da acceso y control total sobre un ordenador o cualquier otro dispositivo.
Esto significa que puedo ver todo en su pantalla, encender mi cámara y el micrófono, pero usted no es consciente de esto.También tengo acceso a todos sus contactos, datos de redes sociales y toda su correspondencia.
Como puedes ver, te envié un correo electrónico desde tu propio buzón (tengo acceso total a tu sistema).
¿Por qué su antivirus no detectó ningún malware? 0tte: Mi malware utiliza un controlador, actualizo su firma cada 4 horas para mantener su antivirus en silencio.
Hice un video que muestra cómo te satisfaces a ti mismo en el lado izquierdo de la pantalla, y en el lado derecho ves el video que estabas viendo.
Con un solo clic, puedo enviar este video a todos tus contactos en el correo y las redes sociales.
También puedo publicar el acceso a todos tus correos y mensajeros que uses.Si quieres prevenir esto, entonces:
Transfiere 1000 dólares a mi cartera de bitcoin (si no sabes cómo hacerlo, escribe a Google: "Comprar bitcoin").Mi billetera de monedas de bits (BTC Wallet): 16ycKePyftmgJggJibv4E2L7ecZLaJw1pK
Después de recibir el pago, borraré el video y no volverás a saber de mí.
Le daré 50 horas (más de dos días) para pagar.
Tengo un aviso para leer este correo electrónico y el temporizador funcionará cuando vea este correo electrónico.No intente responderme. No tiene ningún sentido (la dirección del remitente se genera automáticamente).
Presentar una queja en algún lugar no tiene sentido, porque este correo electrónico no puede ser rastreado, y tampoco mi dirección bitcoin.
No cometo errores.Si descubro que compartiste este mensaje con alguien más, el video será distribuido inmediatamente.
¡Mis mejores deseos!
Fourth example of Polish variant of "Hacker Who Has Access To Your Operating System" scam email:
Text presented within:
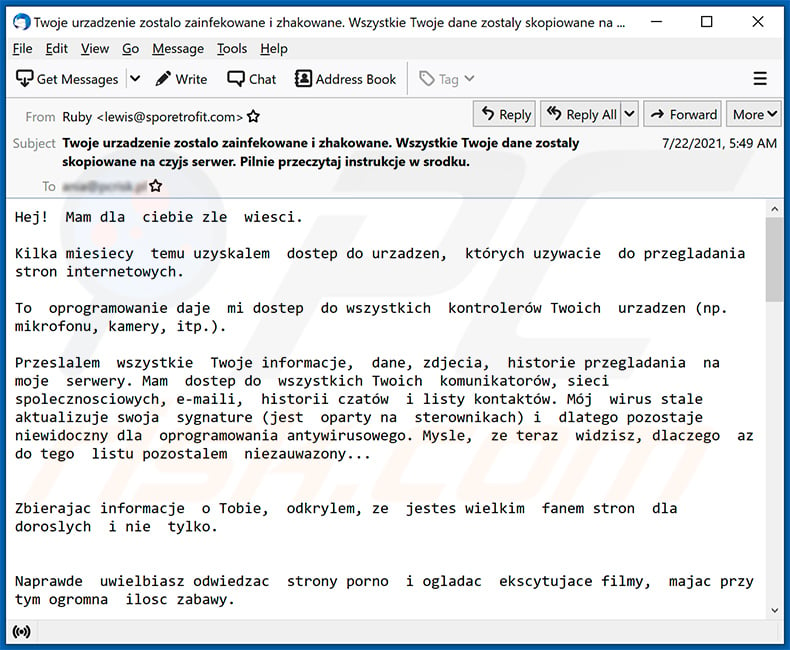
Subject: Twoje urzadzenie zostalo zainfekowane i zhakowane. Wszystkie Twoje dane zostaly skopiowane na czyjs serwer. Pilnie przeczytaj instrukcje w srodku.
Hej! Mam dla ciebie zle wiesci.
Kilka miesiecy temu uzyskalem dostep do urzadzen, których uzywacie do przegladania stron internetowych.
To oprogramowanie daje mi dostep do wszystkich kontrolerów Twoich urzadzen (np. mikrofonu, kamery, itp.).
Przeslalem wszystkie Twoje informacje, dane, zdjecia, historie przegladania na moje serwery. Mam dostep do wszystkich Twoich komunikatorów, sieci spolecznosciowych, e-maili, historii czatów i listy kontaktów. Mój wirus stale aktualizuje swoja sygnature (jest oparty na sterownikach) i dlatego pozostaje niewidoczny dla oprogramowania antywirusowego. Mysle, ze teraz widzisz, dlaczego az do tego listu pozostalem niezauwazony...
Zbierajac informacje o Tobie, odkrylem, ze jestes wielkim fanem stron dla doroslych i nie tylko.
Naprawde uwielbiasz odwiedzac strony porno i ogladac ekscytujace filmy, majac przy tym ogromna ilosc zabawy.
Cóz, udalo mi sie nagrac kilka twoich sprosnych scen i zmontowac kilka filmików, na których widac, jak sie masturbujesz i osiagasz orgazm.
W razie watpliwosci, moge zrobic kilka klikniec i wszystkie twoje filmy beda dostepne dla twoich przyjaciól, kolegów i rodziny.Nie mam tez problemu z ich publicznym udostepnieniem w Internecie.
Moge równiez ujawnic publicznie wszystkie twoje dane osobowe.
Móglbym zrujnowac twoja reputacje na zawsze.Mysle, ze naprawde nie chcesz, aby tak sie stalo, biorac pod uwage specyfike filmów, które lubisz ogladac (wiesz dokladnie, co mam na mysli), doprowadziloby to do prawdziwej katastrofy dla Ciebie.
Zalatwmy to w ten sposób: przelejesz mi 5046 polski zloty (w ekwiwalencie bitcoinów po kursie wymiany w momencie transferu srodków), a jak tylko przelew wplynie, natychmiast usune wszystkie te brudy.
Potem o sobie zapomnimy.
Mój portfel bitcoin dla platnosci: bc1qj4tmlcuhrmgcgptsmkvya3qgnk4mvcgchc5w6y, bc1quvee8k5g60juhwl6m9wxw38nff07dgdakpvc6p
W przypadku, gdy nie wiesz, jak kupic i przelac bitcoins - mozesz uzyc dowolnej nowoczesnej wyszukiwarki.
Daje Ci 50 godzin (w ciagu dwóch dni) na zaplate. Mam powiadomienie, aby przeczytac ten e-mail, a zegar wylaczy sie, gdy zobaczysz ten e-mail.
Obiecuje równiez dezaktywowac i usunac wszelkie zlosliwe oprogramowanie z Twoich urzadzen. To uczciwy uklad, a cena jest dosc niska, biorac pod uwage, ze sprawdzam Twój profil i ruch od jakiegos czasu.
Nie próbuj mi odpowiadac. Nie ma to sensu (adres nadawcy jest generowany automatycznie). Skladanie skargi gdziekolwiek nie ma sensu, poniewaz tego maila nie mozna namierzyc, podobnie jak mojego adresu bitcoin.
Nie popelniam bledów.
Jesli dowiem sie, ze udostepniles te wiadomosc komus innemu, film zostanie natychmiast udostepniony. Na stale zniszcze Twoja reputacje, a wszystkie Twoje dane stana sie publiczne.Najlepsze zyczenia!
Yet another example of a similar scam email:
Text presented within:
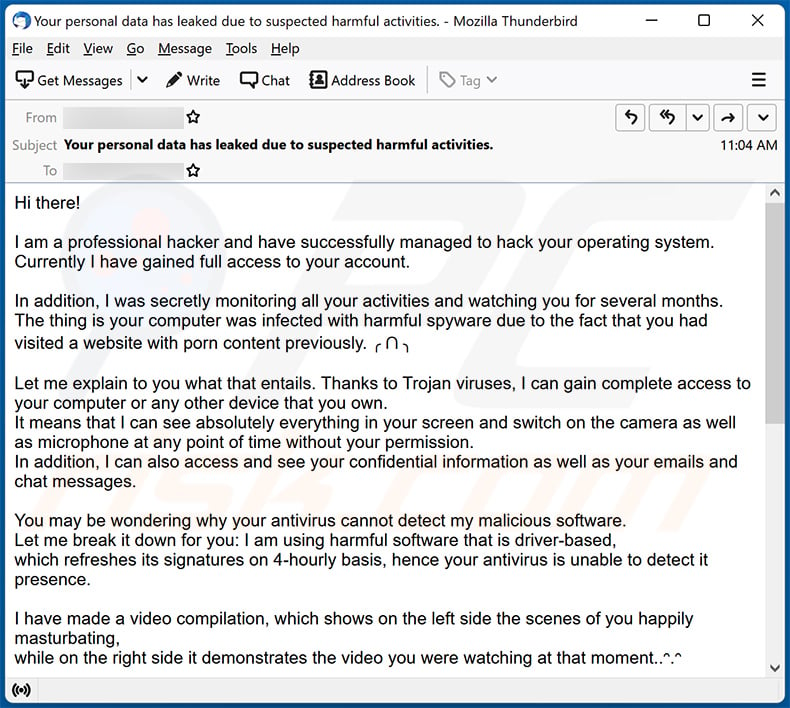
Subject: Your personal data has leaked due to suspected harmful activities.
Hi there!
I am a professional hacker and have successfully managed to hack your operating system.
Currently I have gained full access to your account.In addition, I was secretly monitoring all your activities and watching you for several months.
The thing is your computer was infected with harmful spyware due to the fact that you had visited a website with porn content previously. ╭ ᑎ ╮Let me explain to you what that entails. Thanks to Trojan viruses, I can gain complete access to your computer or any other device that you own.
It means that I can see absolutely everything in your screen and switch on the camera as well as microphone at any point of time without your permission.
In addition, I can also access and see your confidential information as well as your emails and chat messages.You may be wondering why your antivirus cannot detect my malicious software.
Let me break it down for you: I am using harmful software that is driver-based,
which refreshes its signatures on 4-hourly basis, hence your antivirus is unable to detect it presence.I have made a video compilation, which shows on the left side the scenes of you happily masturbating,
while on the right side it demonstrates the video you were watching at that moment..ᵔ.ᵔAll I need is just to share this video to all email addresses and messenger contacts of people you are in communication with on your device or PC.
Furthermore, I can also make public all your emails and chat history.I believe you would definitely want to avoid this from happening.
Here is what you need to do - transfer the Bitcoin equivalent of 850 USD to my Bitcoin account
(that is rather a simple process, which you can check out online in case if you don't know how to do that).Below is my bitcoin account information (Bitcoin wallet): 12nEVuGNtRFMVjeVmLtD4nt2sHX68S47yH
Once the required amount is transferred to my account, I will proceed with deleting all those videos and disappear from your life once and for all.
Kindly ensure you complete the abovementioned transfer within 50 hours (2 days +).
I will receive a notification right after you open this email, hence the countdown will start.Trust me, I am very careful, calculative and never make mistakes.
If I discover that you shared this message with others, I will straight away proceed with making your private videos public.Good luck!
Instant automatic malware removal:
Manual threat removal might be a lengthy and complicated process that requires advanced IT skills. Combo Cleaner is a professional automatic malware removal tool that is recommended to get rid of malware. Download it by clicking the button below:
DOWNLOAD Combo CleanerBy downloading any software listed on this website you agree to our Privacy Policy and Terms of Use. To use full-featured product, you have to purchase a license for Combo Cleaner. 7 days free trial available. Combo Cleaner is owned and operated by RCS LT, the parent company of PCRisk.com.
Quick menu:
- What is Hacker Who Has Access To Your Operating System spam?
- Types of malicious emails.
- How to spot a malicious email?
- What to do if you fell for an email scam?
Types of malicious emails:
![]() Phishing Emails
Phishing Emails
Most commonly, cybercriminals use deceptive emails to trick Internet users into giving away their sensitive private information, for example, login information for various online services, email accounts, or online banking information.
Such attacks are called phishing. In a phishing attack, cybercriminals usually send an email message with some popular service logo (for example, Microsoft, DHL, Amazon, Netflix), create urgency (wrong shipping address, expired password, etc.), and place a link which they hope their potential victims will click on.
After clicking the link presented in such email message, victims are redirected to a fake website that looks identical or extremely similar to the original one. Victims are then asked to enter their password, credit card details, or some other information that gets stolen by cybercriminals.
![]() Emails with Malicious Attachments
Emails with Malicious Attachments
Another popular attack vector is email spam with malicious attachments that infect users' computers with malware. Malicious attachments usually carry trojans that are capable of stealing passwords, banking information, and other sensitive information.
In such attacks, cybercriminals' main goal is to trick their potential victims into opening an infected email attachment. To achieve this goal, email messages usually talk about recently received invoices, faxes, or voice messages.
If a potential victim falls for the lure and opens the attachment, their computers get infected, and cybercriminals can collect a lot of sensitive information.
While it's a more complicated method to steal personal information (spam filters and antivirus programs usually detect such attempts), if successful, cybercriminals can get a much wider array of data and can collect information for a long period of time.
![]() Sextortion Emails
Sextortion Emails
This is a type of phishing. In this case, users receive an email claiming that a cybercriminal could access the webcam of the potential victim and has a video recording of one's masturbation.
To get rid of the video, victims are asked to pay a ransom (usually using Bitcoin or another cryptocurrency). Nevertheless, all of these claims are false - users who receive such emails should ignore and delete them.
How to spot a malicious email?
While cyber criminals try to make their lure emails look trustworthy, here are some things that you should look for when trying to spot a phishing email:
- Check the sender's ("from") email address: Hover your mouse over the "from" address and check if it's legitimate. For example, if you received an email from Microsoft, be sure to check if the email address is @microsoft.com and not something suspicious like @m1crosoft.com, @microsfot.com, @account-security-noreply.com, etc.
- Check for generic greetings: If the greeting in the email is "Dear user", "Dear @youremail.com", "Dear valued customer", this should raise suspiciousness. Most commonly, companies call you by your name. Lack of this information could signal a phishing attempt.
- Check the links in the email: Hover your mouse over the link presented in the email, if the link that appears seems suspicious, don't click it. For example, if you received an email from Microsoft and the link in the email shows that it will go to firebasestorage.googleapis.com/v0... you shouldn't trust it. It's best not to click any links in the emails but to visit the company website that sent you the email in the first place.
- Don't blindly trust email attachments: Most commonly, legitimate companies will ask you to log in to their website and to view any documents there; if you received an email with an attachment, it's a good idea to scan it with an antivirus application. Infected email attachments are a common attack vector used by cybercriminals.
To minimise the risk of opening phishing and malicious emails we recommend using Combo Cleaner Antivirus for Windows.
Example of a spam email:
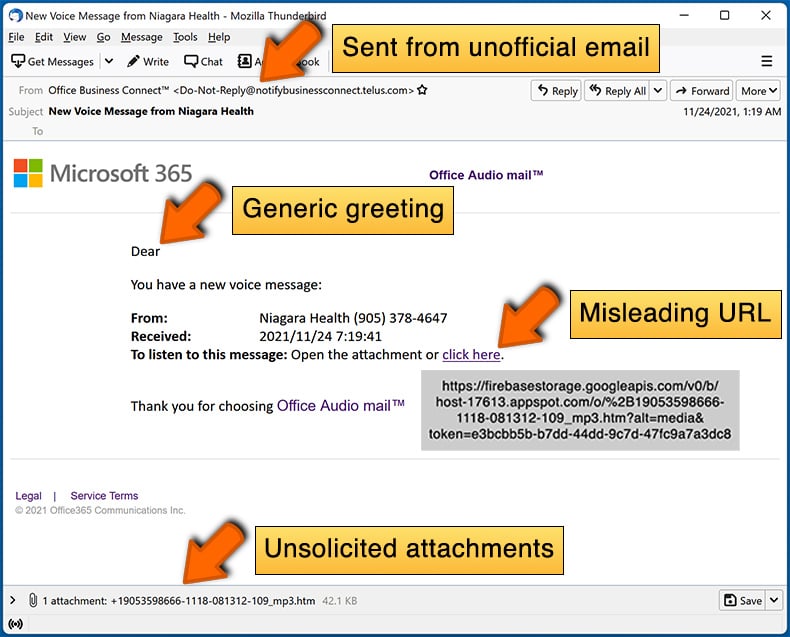
What to do if you fell for an email scam?
- If you clicked on a link in a phishing email and entered your password - be sure to change your password as soon as possible. Usually, cybercriminals collect stolen credentials and then sell them to other groups that use them for malicious purposes. If you change your password in a timely manner, there's a chance that criminals won't have enough time to do any damage.
- If you entered your credit card information - contact your bank as soon as possible and explain the situation. There's a good chance that you will need to cancel your compromised credit card and get a new one.
- If you see any signs of identity theft - you should immediately contact the Federal Trade Commission. This institution will collect information about your situation and create a personal recovery plan.
- If you opened a malicious attachment - your computer is probably infected, you should scan it with a reputable antivirus application. For this purpose, we recommend using Combo Cleaner Antivirus for Windows.
- Help other Internet users - report phishing emails to Anti-Phishing Working Group, FBI’s Internet Crime Complaint Center, National Fraud Information Center and U.S. Department of Justice.
Frequently Asked Questions (FAQ)
Why did I receive this email?
Cyber criminals distribute spam emails in mass-scale operations. Therefore, thousands of users receive identical letters.
Was my computer actually hacked and does the sender have any information?
No, neither was your device compromised, nor has the sender made any recording featuring you. All the claims made by the email are false; it is a scam.
How did cyber criminals get my email password?
It is most likely that this information was obtained through a phishing scam that you became a victim of at some point. These scams can be promoted via spam mail or online; they can be presented as fake log-in pages or registration/subscription forms. It is less likely that your email password was obtained through a data breach on your or a service provider's end.
I have sent cryptocurrency to the address presented in this email, can I get my money back?
Cryptocurrency transactions are virtually untraceable, which makes them irreversible. Hence, you will be unable to recover your funds.
I have provided my personal information when tricked by a spam email, what should I do?
If you have disclosed log-in credentials - change the passwords of all potentially exposed accounts and inform their official support without delay. And if you have revealed other private data (e.g., ID card details, credit card numbers, etc.) - immediately contact the corresponding authorities.
I have read a spam email but didn't open the attachment, is my computer infected?
No, opening/reading a spam email will not initiate any malware download/installation processes. Systems are infected when the attachments or links present in these emails are opened/clicked.
I have downloaded and opened a file attached to a spam email, is my computer infected?
If it was an executable (.exe, .run, etc.) - most likely, yes. However, you might have avoided a system infection if it was a document (.doc, .xls, .pdf, etc.). These formats may require additional actions (e.g., enabling macro commands) to start downloading/installing malware.
Will Combo Cleaner remove malware infections present in email attachments?
Yes, Combo Cleaner is capable of detecting and eliminating practically all known malware infections. It has to be stressed that sophisticated malicious programs usually hide deep within systems - therefore, performing a full system scan is paramount.
Share:

Tomas Meskauskas
Expert security researcher, professional malware analyst
I am passionate about computer security and technology. I have an experience of over 10 years working in various companies related to computer technical issue solving and Internet security. I have been working as an author and editor for pcrisk.com since 2010. Follow me on Twitter and LinkedIn to stay informed about the latest online security threats.
PCrisk security portal is brought by a company RCS LT.
Joined forces of security researchers help educate computer users about the latest online security threats. More information about the company RCS LT.
Our malware removal guides are free. However, if you want to support us you can send us a donation.
DonatePCrisk security portal is brought by a company RCS LT.
Joined forces of security researchers help educate computer users about the latest online security threats. More information about the company RCS LT.
Our malware removal guides are free. However, if you want to support us you can send us a donation.
Donate
▼ Show Discussion