Get free scan and check if your device is infected.
Remove it nowTo use full-featured product, you have to purchase a license for Combo Cleaner. Seven days free trial available. Combo Cleaner is owned and operated by RCS LT, the parent company of PCRisk.com.
What is "Fund Release email scam"?
Scammers often use email as a channel to trick people into providing sensitive information (e.g., login credentials, credit card details, social security numbers), sending money and installing malware onto their computers. Scammers usually disguise their emails as important, official messages from legitimate companies.
They use the names of well-known entities, logos, names of real people, take advantage of real events, etc., to add authenticity to their emails. This email is disguised as a message regarding fund release - scammers spread with the aim to extort money from recipients.
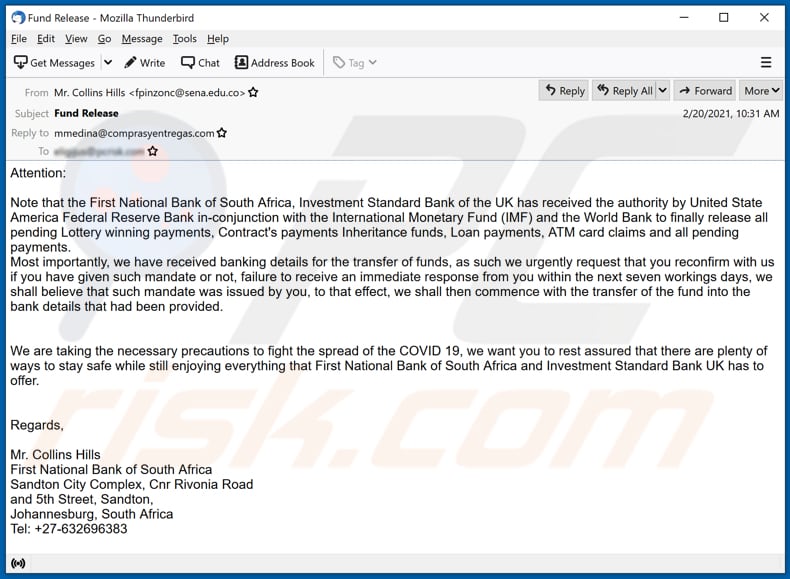
"Fund Release" email scam overview
Scammers spread an email claiming that South Africa's First National and United Kingdom's Investment Standard banks have received authority from the America's Federal Reserve Bank, International Monetary Fund (IMF), and The World Bank to "release" pending lottery winnings, contract payments, inheritance funds, loan payments, ATM card claims, and other pending payments.
Their main goal is to trick recipients into believing that one of the banks has their banking details and that recipients need to confirm if those details are correct. In this way, scammers attempt to trick recipients into providing their credit card details.
It is likely that scammers may ask to pay a "transaction" or "processing" or some other fee (pay upfront fees for "financial services", which are never provided). Therefore, this is either a prepayment scam or a phishing email and, therefore, cannot be trusted.
Scammers could use provided details (credit card details) to steal identities, make fraudulent transactions, purchases, or to sell them to other cyber criminals. Typically, when recipients fall for these scams, they lose money, become victims of identity theft, and encounter other issues relating to finances.
| Name | Fund Release Email Scam |
| Threat Type | Phishing, Scam, Social Engineering, Fraud |
| Fake Claim | Funds ready for release |
| Disguise | Email from First National Bank of South Africa |
| Symptoms | Unauthorized online purchases, changed online account passwords, identity theft, illegal access of the computer. |
| Distribution methods | Deceptive emails, rogue online pop-up ads, search engine poisoning techniques, misspelled domains. |
| Damage | Loss of sensitive private information, monetary loss, identity theft. |
| Malware Removal (Windows) |
To eliminate possible malware infections, scan your computer with legitimate antivirus software. Our security researchers recommend using Combo Cleaner. Download Combo CleanerTo use full-featured product, you have to purchase a license for Combo Cleaner. 7 days free trial available. Combo Cleaner is owned and operated by RCS LT, the parent company of PCRisk.com. |
Similar spam campaign examples
More examples of similar scams are "INTERNATIONAL MONETARY FUND (IMF) Email Scam", "U.S Army Special Operations Command Consignment Email Scam", and "EMPLOYEE BENEFITS Email Scam".
Most claim to be emails from legitimate companies, organizations, or other entities, and ask to provide personal information or make small payments. Note that email can also be used as a channel to deliver malware.
How do spam campaigns infect computers?
Phishing emails that are used to deliver malware generally contain a download link for a malicious file or attachment. Typically, cyber criminals attempt to trick recipients into opening a PDF or Microsoft Office document, JavaScript file, an executable file (.exe), ZIP, RAR, or other archive file that is designed to install specific malicious software.
Note that malicious MS Office documents can install malware only when users enable editing/content (macros commands). If the documents are opened with MS Office versions prior to 2010, however, the documents install malicious software automatically, since these older versions do not include "Protected View" mode.
How to avoid installation of malware
You are advised to research all software before download/installation. Use only official and verified download channels. Unofficial and free file-hosting websites, Peer-to-Peer sharing networks (BitTorrent, Gnutella, eMule), and other third party downloaders commonly offer harmful and bundled content, and are therefore untrusted and should be avoided.
When downloading/installing, read the terms, study all possible options, use the "Custom/Advanced" settings and opt-out of additional apps, tools, features, and so on.
Intrusive advertisements typically seem legitimate, however, they can redirect to dubious and malicious sites (e.g. gambling, pornography, adult-dating, and many others). If you encounter ads or redirects of this kind, inspect the system and remove all dubious applications and browser extensions/plug-ins immediately.
Installed programs must be activated and updated with tools or implemented functions that are provided by the official developers. No other third party, unofficial tools should be used.
Note that it is illegal to activate licensed software with ‘cracking’ tools. Files and programs should be downloaded from official websites and via direct download links. Avoid third party installers and the tools/sources mentioned above.
Do not open website links or files in irrelevant emails that are received from unknown, suspicious addresses. These bogus emails are often disguised as official and important. Regularly, scan your computer with reputable, up-to-date antivirus or anti-spyware software.
If you have already opened malicious attachments, we recommend running a scan with Combo Cleaner Antivirus for Windows to automatically eliminate infiltrated malware.
Text presented in the Fund Release scam email:
Subject: Fund Release
Attention:
Note that the First National Bank of South Africa, Investment Standard Bank of the UK has received the authority by United State America Federal Reserve Bank in-conjunction with the International Monetary Fund (IMF) and the World Bank to finally release all pending Lottery winning payments, Contract's payments Inheritance funds, Loan payments, ATM card claims and all pending payments.
Most importantly, we have received banking details for the transfer of funds, as such we urgently request that you reconfirm with us if you have given such mandate or not, failure to receive an immediate response from you within the next seven workings days, we shall believe that such mandate was issued by you, to that effect, we shall then commence with the transfer of the fund into the bank details that had been provided.
We are taking the necessary precautions to fight the spread of the COVID 19, we want you to rest assured that there are plenty of ways to stay safe while still enjoying everything that First National Bank of South Africa and Investment Standard Bank UK has to offer.
Regards,
Mr. Collins Hills
First National Bank of South Africa
Sandton City Complex, Cnr Rivonia Road
and 5th Street, Sandton,
Johannesburg, South Africa
Tel: +27-632696383
Other examples of fund release-themed spam emails:
Sample 1:
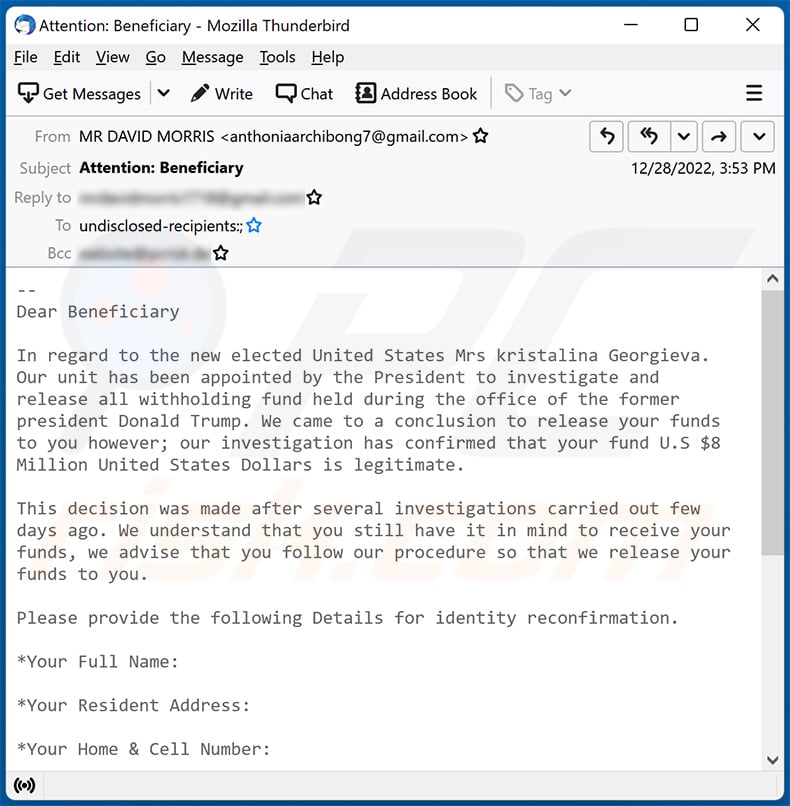
Text presented within:
Dear Beneficiary
In regard to the new elected United States Mrs kristalina Georgieva.
Our unit has been appointed by the President to investigate and
release all withholding fund held during the office of the former
president Donald Trump. We came to a conclusion to release your funds
to you however; our investigation has confirmed that your fund U.S $8
Million United States Dollars is legitimate.This decision was made after several investigations carried out few
days ago. We understand that you still have it in mind to receive your
funds, we advise that you follow our procedure so that we release your
funds to you.Please provide the following Details for identity reconfirmation.
*Your Full Name:
*Your Resident Address:
*Your Home & Cell Number:
*Your Date Of Birth:
*Your Occupation:
*Copy Of ID: Driver's license (Front & Back) Or Passport
We will provide you with further details on the release of your funds
only after we have reconfirmed the above listed information.Please send all information to this EMail: Mrdavidmorris1718@gmail.com
my Whatsapp phone number +13189255380
Sample 2:
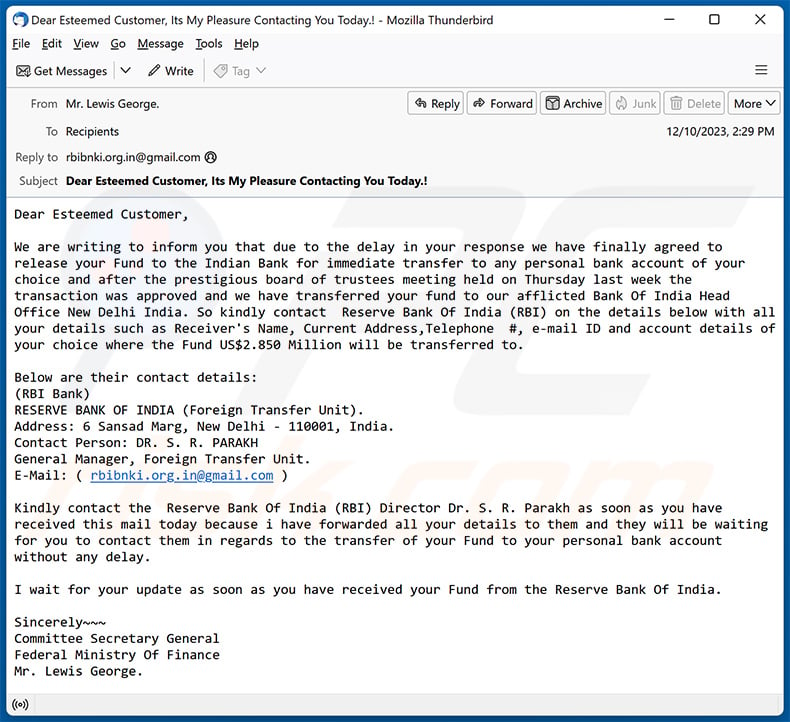
Text presented within:
Subject: Dear Esteemed Customer, Its My Pleasure Contacting You Today.!
Dear Esteemed Customer,
We are writing to inform you that due to the delay in your response we have finally agreed to release your Fund to the Indian Bank for immediate transfer to any personal bank account of your choice and after the prestigious board of trustees meeting held on Thursday last week the transaction was approved and we have transferred your fund to our afflicted Bank Of India Head Office New Delhi India. So kindly contact Reserve Bank Of India (RBI) on the details below with all your details such as Receiver's Name, Current Address,Telephone #, e-mail ID and account details of your choice where the Fund US$2.850 Million will be transferred to.
Below are their contact details:
(RBI Bank)
RESERVE BANK OF INDIA (Foreign Transfer Unit).
Address: 6 Sansad Marg, New Delhi - 110001, India.
Contact Person: DR. S. R. PARAKH
General Manager, Foreign Transfer Unit.
E-Mail: ( rbibnki.org.in@gmail.com )Kindly contact the Reserve Bank Of India (RBI) Director Dr. S. R. Parakh as soon as you have received this mail today because i have forwarded all your details to them and they will be waiting for you to contact them in regards to the transfer of your Fund to your personal bank account without any delay.
I wait for your update as soon as you have received your Fund from the Reserve Bank Of India.
Sincerely~~~
Committee Secretary General
Federal Ministry Of Finance
Mr. Lewis George.
Sample 3:
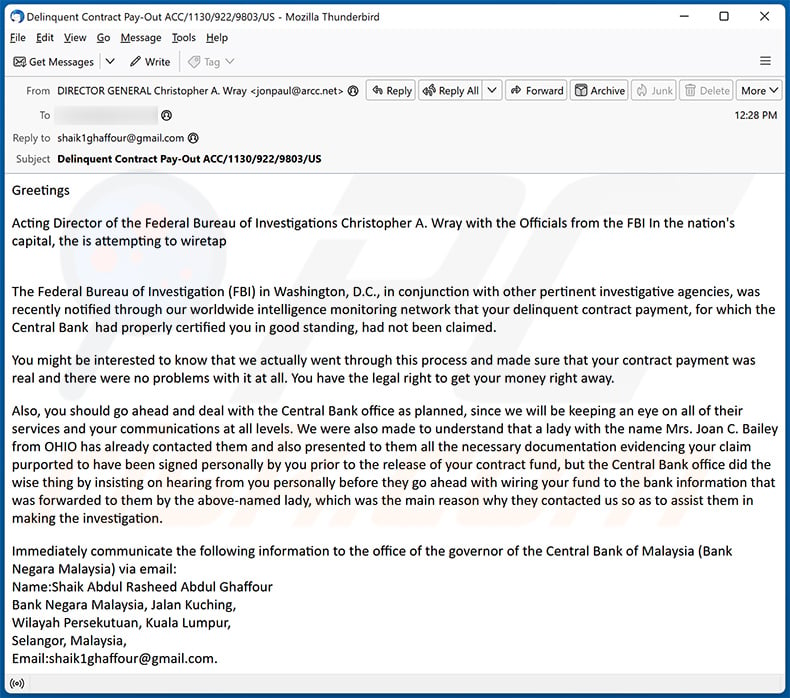
Text presented within:
Subject: Delinquent Contract Pay-Out ACC/1130/922/9803/US
GreetingsActing Director of the Federal Bureau of Investigations Christopher A. Wray with the Officials from the FBI In the nation's capital, the is attempting to wiretap
The Federal Bureau of Investigation (FBI) in Washington, D.C., in conjunction with other pertinent investigative agencies, was recently notified through our worldwide intelligence monitoring network that your delinquent contract payment, for which the Central Bank had properly certified you in good standing, had not been claimed.
You might be interested to know that we actually went through this process and made sure that your contract payment was real and there were no problems with it at all. You have the legal right to get your money right away.
Also, you should go ahead and deal with the Central Bank office as planned, since we will be keeping an eye on all of their services and your communications at all levels. We were also made to understand that a lady with the name Mrs. Joan C. Bailey from OHIO has already contacted them and also presented to them all the necessary documentation evidencing your claim purported to have been signed personally by you prior to the release of your contract fund, but the Central Bank office did the wise thing by insisting on hearing from you personally before they go ahead with wiring your fund to the bank information that was forwarded to them by the above-named lady, which was the main reason why they contacted us so as to assist them in making the investigation.
Immediately communicate the following information to the office of the governor of the Central Bank of Malaysia (Bank Negara Malaysia) via email:
Name:Shaik Abdul Rasheed Abdul Ghaffour
Bank Negara Malaysia, Jalan Kuching,
Wilayah Persekutuan, Kuala Lumpur,
Selangor, Malaysia,
Email:shaik1ghaffour@gmail.com.Please call the Governor of the Central Bank right away at the above email address and ask them to take care of your payment file as instructed to ensure you can get your contract fund.
In order to ensure the processing and release of your funds with confidence and to prevent us from being held liable for any incorrect payments, you are required to verify and authenticate the information provided below.
COMPLETE NAMES: _________________________
CITY: _____________________________
ZIP: _____________
COURT NATION ____________________________
SEX:___________
FAX: __________________________
Age: _______________
Telephone Number: _____________________
You should fulfill all their processes as requested to speed up the transfer of your funds to you. Additionally, bear in mind that the Central Bank of Malaysia operates according to its own protocol, which is detailed in its banking terms; therefore, any delay could be extremely hazardous.We sincerely appreciate your anticipated cooperation in advance and are eagerly anticipating your prompt response to this issue.
Sincere Regards,
Christopher Wray Director, (Federal Bureau of Investigation),
935 Pennsylvania Avenue Northwest, J.
Edgar Hoover Building,
Washington, D.C.
Sample 4:
Text presented within:
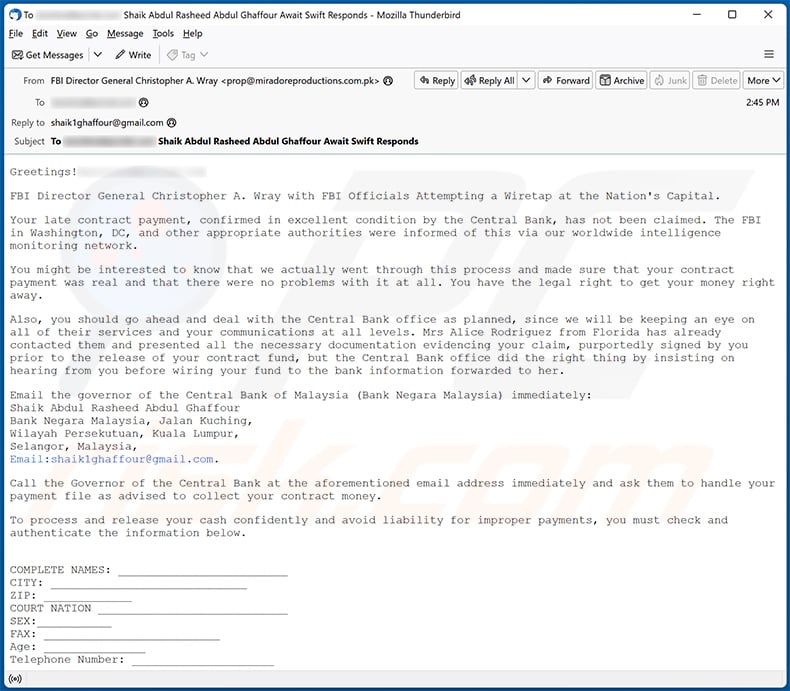
Subject: To ******** Shaik Abdul Rasheed Abdul Ghaffour Await Swift Responds
Greetings!********
FBI Director General Christopher A. Wray with FBI Officials Attempting a Wiretap at the Nation's Capital.
Your late contract payment, confirmed in excellent condition by the Central Bank, has not been claimed. The FBI in Washington, DC, and other appropriate authorities were informed of this via our worldwide intelligence monitoring network.
You might be interested to know that we actually went through this process and made sure that your contract payment was real and that there were no problems with it at all. You have the legal right to get your money right away.
Also, you should go ahead and deal with the Central Bank office as planned, since we will be keeping an eye on all of their services and your communications at all levels. Mrs Alice Rodriguez from Florida has already contacted them and presented all the necessary documentation evidencing your claim, purportedly signed by you prior to the release of your contract fund, but the Central Bank office did the right thing by insisting on hearing from you before wiring your fund to the bank information forwarded to her.
Email the governor of the Central Bank of Malaysia (Bank Negara Malaysia) immediately:
Shaik Abdul Rasheed Abdul Ghaffour
Bank Negara Malaysia, Jalan Kuching,
Wilayah Persekutuan, Kuala Lumpur,
Selangor, Malaysia,
Email:shaik1ghaffour@gmail.com.Call the Governor of the Central Bank at the aforementioned email address immediately and ask them to handle your payment file as advised to collect your contract money.
To process and release your cash confidently and avoid liability for improper payments, you must check and authenticate the information below.
COMPLETE NAMES: _________________________
CITY: _____________________________
ZIP: _____________
COURT NATION ____________________________
SEX:___________
FAX: __________________________
Age: _______________
Telephone Number: _____________________Please complete all their requests to speed up your money transfer. Remember that the Central Bank of Malaysia follows its own process, which is stated in its banking conditions, so any delay might be detrimental.
We appreciate your early cooperation and greatly await your timely solution to this matter.
Best regards,
--
Christopher Wray Director, Federal Bureau of Investigation,
935 Pennsylvania Avenue Northwest, J.
Edgar Hoover Building,
Washington, D.C.
Sample 5:
Text presented within:
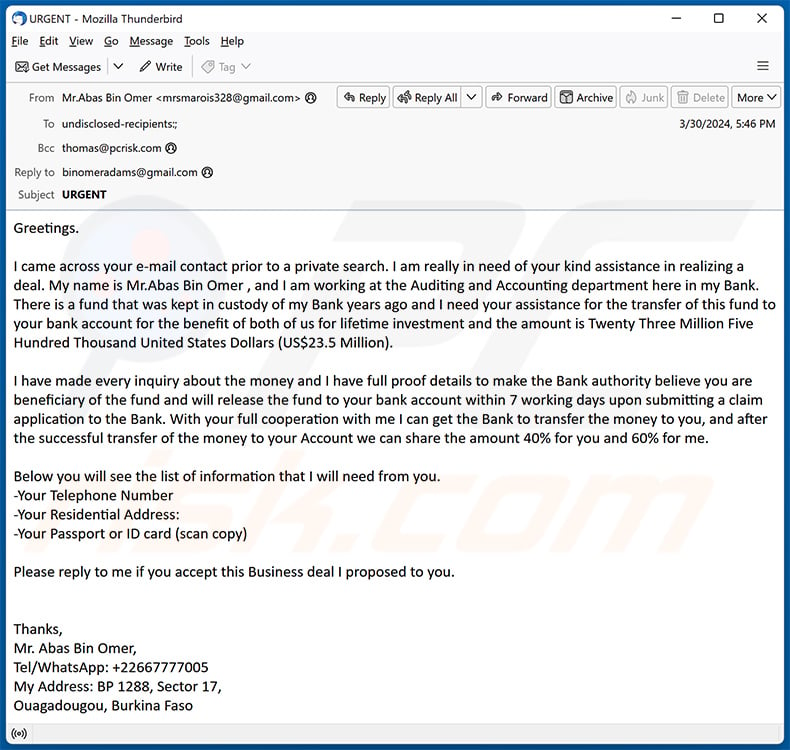
Subject: URGENT
Greetings.I came across your e-mail contact prior to a private search. I am really in need of your kind assistance in realizing a deal. My name is Mr.Abas Bin Omer , and I am working at the Auditing and Accounting department here in my Bank. There is a fund that was kept in custody of my Bank years ago and I need your assistance for the transfer of this fund to your bank account for the benefit of both of us for lifetime investment and the amount is Twenty Three Million Five Hundred Thousand United States Dollars (US$23.5 Million).
I have made every inquiry about the money and I have full proof details to make the Bank authority believe you are beneficiary of the fund and will release the fund to your bank account within 7 working days upon submitting a claim application to the Bank. With your full cooperation with me I can get the Bank to transfer the money to you, and after the successful transfer of the money to your Account we can share the amount 40% for you and 60% for me.
Below you will see the list of information that I will need from you.
-Your Telephone Number
-Your Residential Address:
-Your Passport or ID card (scan copy)Please reply to me if you accept this Business deal I proposed to you.
Thanks,
Mr. Abas Bin Omer,
Tel/WhatsApp: +22667777005
My Address: BP 1288, Sector 17,
Ouagadougou, Burkina Faso
Sample 6:
Text presented within:
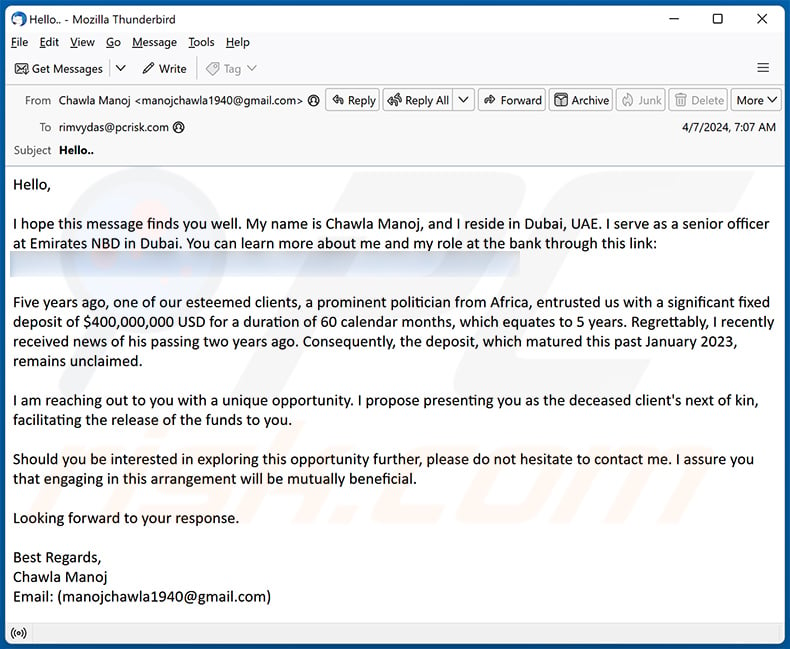
Subject: Hello..
Hello,I hope this message finds you well. My name is Chawla Manoj, and I reside in Dubai, UAE. I serve as a senior officer at Emirates NBD in Dubai. You can learn more about me and my role at the bank through this link: -
Five years ago, one of our esteemed clients, a prominent politician from Africa, entrusted us with a significant fixed deposit of $400,000,000 USD for a duration of 60 calendar months, which equates to 5 years. Regrettably, I recently received news of his passing two years ago. Consequently, the deposit, which matured this past January 2023, remains unclaimed.
I am reaching out to you with a unique opportunity. I propose presenting you as the deceased client's next of kin, facilitating the release of the funds to you.
Should you be interested in exploring this opportunity further, please do not hesitate to contact me. I assure you that engaging in this arrangement will be mutually beneficial.
Looking forward to your response.
Best Regards,
Chawla Manoj
Email: (manojchawla1940@gmail.com)
Sample 7:
Text presented within:
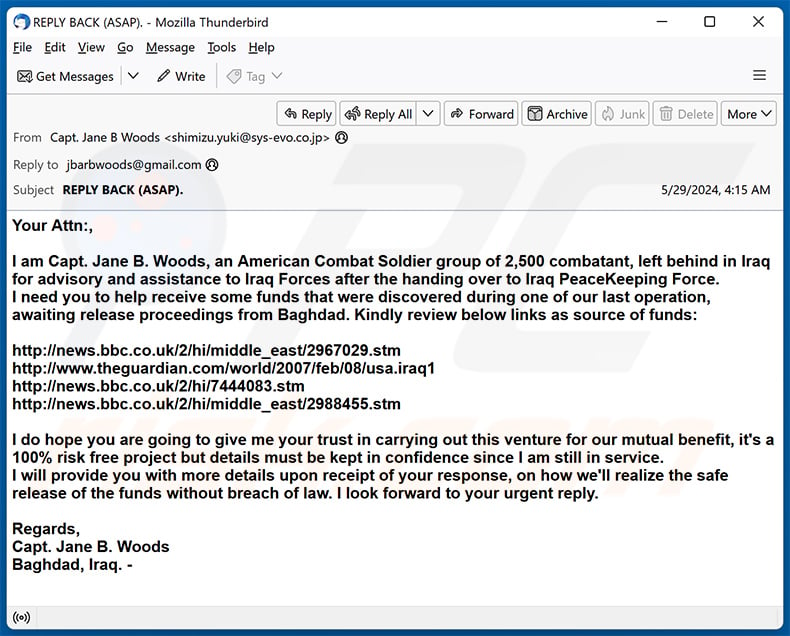
Subject: REPLY BACK (ASAP).
Your Attn:,
I am Capt. Jane B. Woods, an American Combat Soldier group of 2,500 combatant, left behind in Iraq for advisory and assistance to Iraq Forces after the handing over to Iraq PeaceKeeping Force.
I need you to help receive some funds that were discovered during one of our last operation, awaiting release proceedings from Baghdad. Kindly review below links as source of funds:
-
I do hope you are going to give me your trust in carrying out this venture for our mutual benefit, it's a 100% risk free project but details must be kept in confidence since I am still in service.
I will provide you with more details upon receipt of your response, on how we'll realize the safe release of the funds without breach of law. I look forward to your urgent reply.
Regards,
Capt. Jane B. Woods
Baghdad, Iraq. -
Sample 8:
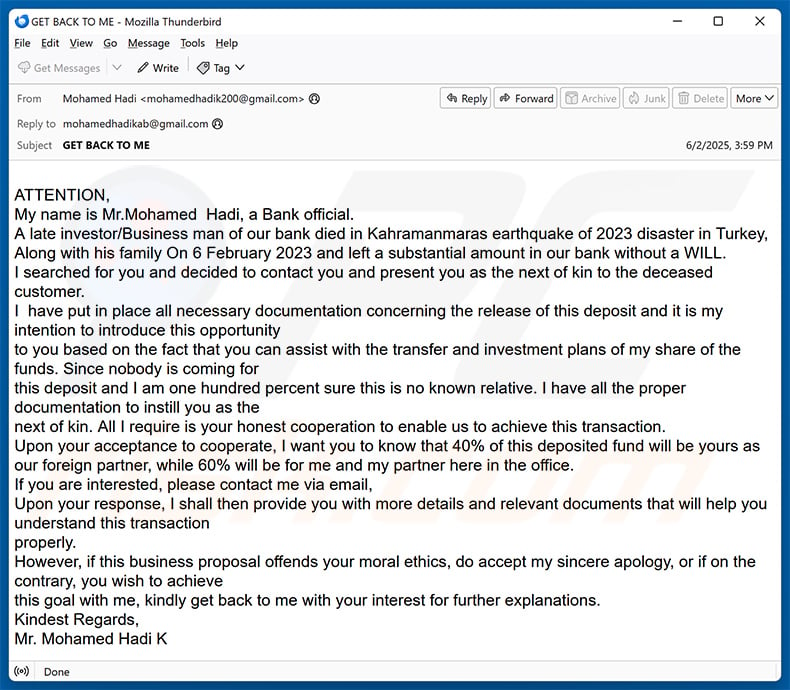
Text presented within:
Subject: GET BACK TO ME
ATTENTION,
My name is Mr.Mohamed Hadi, a Bank official.
A late investor/Business man of our bank died in Kahramanmaras earthquake of 2023 disaster in Turkey,
Along with his family On 6 February 2023 and left a substantial amount in our bank without a WILL.
I searched for you and decided to contact you and present you as the next of kin to the deceased customer.
I have put in place all necessary documentation concerning the release of this deposit and it is my intention to introduce this opportunity to you based on the fact that you can assist with the transfer and investment plans of my share of the funds. Since nobody is coming for this deposit and I am one hundred percent sure this is no known relative. I have all the proper documentation to instill you as the next of kin. All I require is your honest cooperation to enable us to achieve this transaction.
Upon your acceptance to cooperate, I want you to know that 40% of this deposited fund will be yours as our foreign partner, while 60% will be for me and my partner here in the office.
If you are interested, please contact me via email,
Upon your response, I shall then provide you with more details and relevant documents that will help you understand this transaction properly.
However, if this business proposal offends your moral ethics, do accept my sincere apology, or if on the contrary, you wish to achieve this goal with me, kindly get back to me with your interest for further explanations.
Kindest Regards,
Mr. Mohamed Hadi K
Sample 9:
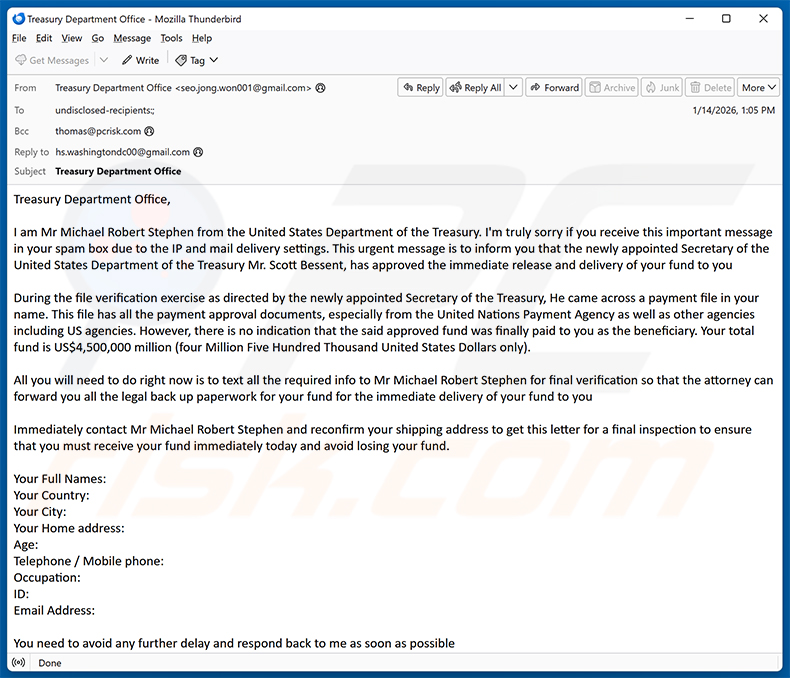
Text presented within:
Treasury Department Office,
I am Mr Michael Robert Stephen from the United States Department of the Treasury. I'm truly sorry if you receive this important message in your spam box due to the IP and mail delivery settings. This urgent message is to inform you that the newly appointed Secretary of the United States Department of the Treasury Mr. Scott Bessent, has approved the immediate release and delivery of your fund to you
During the file verification exercise as directed by the newly appointed Secretary of the Treasury, He came across a payment file in your name. This file has all the payment approval documents, especially from the United Nations Payment Agency as well as other agencies including US agencies. However, there is no indication that the said approved fund was finally paid to you as the beneficiary. Your total fund is US$4,500,000 million (four Million Five Hundred Thousand United States Dollars only).
All you will need to do right now is to text all the required info to Mr Michael Robert Stephen for final verification so that the attorney can forward you all the legal back up paperwork for your fund for the immediate delivery of your fund to you
Immediately contact Mr Michael Robert Stephen and reconfirm your shipping address to get this letter for a final inspection to ensure that you must receive your fund immediately today and avoid losing your fund.
Your Full Names:
Your Country:
Your City:
Your Home address:
Age:
Telephone / Mobile phone:
Occupation:
ID:
Email Address:You need to avoid any further delay and respond back to me as soon as possible
Mr Michael Robert Stephen
Instant automatic malware removal:
Manual threat removal might be a lengthy and complicated process that requires advanced IT skills. Combo Cleaner is a professional automatic malware removal tool that is recommended to get rid of malware. Download it by clicking the button below:
DOWNLOAD Combo CleanerBy downloading any software listed on this website you agree to our Privacy Policy and Terms of Use. To use full-featured product, you have to purchase a license for Combo Cleaner. 7 days free trial available. Combo Cleaner is owned and operated by RCS LT, the parent company of PCRisk.com.
Quick menu:
- What is Fund Release spam?
- Types of malicious emails.
- How to spot a malicious email?
- What to do if you fell for an email scam?
Types of malicious emails:
![]() Phishing Emails
Phishing Emails
Most commonly, cybercriminals use deceptive emails to trick Internet users into giving away their sensitive private information, for example, login information for various online services, email accounts, or online banking information.
Such attacks are called phishing. In a phishing attack, cybercriminals usually send an email message with some popular service logo (for example, Microsoft, DHL, Amazon, Netflix), create urgency (wrong shipping address, expired password, etc.), and place a link which they hope their potential victims will click on.
After clicking the link presented in such email message, victims are redirected to a fake website that looks identical or extremely similar to the original one. Victims are then asked to enter their password, credit card details, or some other information that gets stolen by cybercriminals.
![]() Emails with Malicious Attachments
Emails with Malicious Attachments
Another popular attack vector is email spam with malicious attachments that infect users' computers with malware. Malicious attachments usually carry trojans that are capable of stealing passwords, banking information, and other sensitive information.
In such attacks, cybercriminals' main goal is to trick their potential victims into opening an infected email attachment. To achieve this goal, email messages usually talk about recently received invoices, faxes, or voice messages.
If a potential victim falls for the lure and opens the attachment, their computers get infected, and cybercriminals can collect a lot of sensitive information.
While it's a more complicated method to steal personal information (spam filters and antivirus programs usually detect such attempts), if successful, cybercriminals can get a much wider array of data and can collect information for a long period of time.
![]() Sextortion Emails
Sextortion Emails
This is a type of phishing. In this case, users receive an email claiming that a cybercriminal could access the webcam of the potential victim and has a video recording of one's masturbation.
To get rid of the video, victims are asked to pay a ransom (usually using Bitcoin or another cryptocurrency). Nevertheless, all of these claims are false - users who receive such emails should ignore and delete them.
How to spot a malicious email?
While cyber criminals try to make their lure emails look trustworthy, here are some things that you should look for when trying to spot a phishing email:
- Check the sender's ("from") email address: Hover your mouse over the "from" address and check if it's legitimate. For example, if you received an email from Microsoft, be sure to check if the email address is @microsoft.com and not something suspicious like @m1crosoft.com, @microsfot.com, @account-security-noreply.com, etc.
- Check for generic greetings: If the greeting in the email is "Dear user", "Dear @youremail.com", "Dear valued customer", this should raise suspiciousness. Most commonly, companies call you by your name. Lack of this information could signal a phishing attempt.
- Check the links in the email: Hover your mouse over the link presented in the email, if the link that appears seems suspicious, don't click it. For example, if you received an email from Microsoft and the link in the email shows that it will go to firebasestorage.googleapis.com/v0... you shouldn't trust it. It's best not to click any links in the emails but to visit the company website that sent you the email in the first place.
- Don't blindly trust email attachments: Most commonly, legitimate companies will ask you to log in to their website and to view any documents there; if you received an email with an attachment, it's a good idea to scan it with an antivirus application. Infected email attachments are a common attack vector used by cybercriminals.
To minimise the risk of opening phishing and malicious emails we recommend using Combo Cleaner Antivirus for Windows.
Example of a spam email:
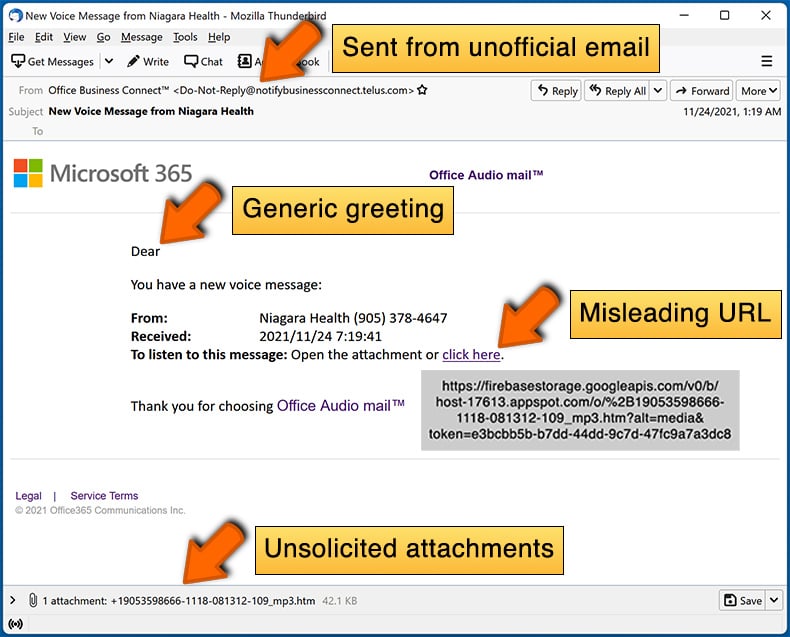
What to do if you fell for an email scam?
- If you clicked on a link in a phishing email and entered your password - be sure to change your password as soon as possible. Usually, cybercriminals collect stolen credentials and then sell them to other groups that use them for malicious purposes. If you change your password in a timely manner, there's a chance that criminals won't have enough time to do any damage.
- If you entered your credit card information - contact your bank as soon as possible and explain the situation. There's a good chance that you will need to cancel your compromised credit card and get a new one.
- If you see any signs of identity theft - you should immediately contact the Federal Trade Commission. This institution will collect information about your situation and create a personal recovery plan.
- If you opened a malicious attachment - your computer is probably infected, you should scan it with a reputable antivirus application. For this purpose, we recommend using Combo Cleaner Antivirus for Windows.
- Help other Internet users - report phishing emails to Anti-Phishing Working Group, FBI’s Internet Crime Complaint Center, National Fraud Information Center and U.S. Department of Justice.
Frequently Asked Questions (FAQ)
Why did I receive this email?
Cyber criminals distribute spam emails in large-scale campaigns – therefore, thousands of users receive identical messages.
I have provided my personal information when tricked by this spam email, what should I do?
If you have provided your account credentials – immediately change the passwords of all possibly exposed accounts and inform their official support. However, if the disclosed information was of a different personal nature (e.g., ID card details, passport scans/photos, credit card numbers, etc.) – contact the corresponding authorities without delay.
I have read a spam email but didn't open the attachment, is my computer infected?
Devices are infected when malicious attachments or links are opened; merely reading an email is harmless.
I have downloaded and opened a file attached to a spam email, is my computer infected?
If the opened file was an executable (.exe, .run, etc.) – most likely, yes – since these formats cause infections almost without fail. However, you might have avoided compromising the system if it was a document (.doc, .xls, .pdf, .one, etc.). Document formats can require additional interaction (e.g., enabling macro commands, clicking embedded files/links, etc.) to start downloading/installing malware.
Will Combo Cleaner remove malware infections present in email attachments?
Yes, Combo Cleaner is capable of detecting and eliminating practically all known malware infections. It must be stressed that performing a full system scan is essential since high-end malicious software typically hides deep within systems.
Share:

Tomas Meskauskas
Expert security researcher, professional malware analyst
I am passionate about computer security and technology. I have an experience of over 10 years working in various companies related to computer technical issue solving and Internet security. I have been working as an author and editor for pcrisk.com since 2010. Follow me on Twitter and LinkedIn to stay informed about the latest online security threats.
PCrisk security portal is brought by a company RCS LT.
Joined forces of security researchers help educate computer users about the latest online security threats. More information about the company RCS LT.
Our malware removal guides are free. However, if you want to support us you can send us a donation.
DonatePCrisk security portal is brought by a company RCS LT.
Joined forces of security researchers help educate computer users about the latest online security threats. More information about the company RCS LT.
Our malware removal guides are free. However, if you want to support us you can send us a donation.
Donate
▼ Show Discussion