Get free scan and check if your device is infected.
Remove it nowTo use full-featured product, you have to purchase a license for Combo Cleaner. Seven days free trial available. Combo Cleaner is owned and operated by RCS LT, the parent company of PCRisk.com.
What kind of malware is Enigma?
Enigma is an information stealer written in the C# programming language. It is a variation of another stealer known as Stealerium. It is important to note that Enigma is also the name of a legitimate company that offers business intelligence and data services, which has no association with the information stealer.
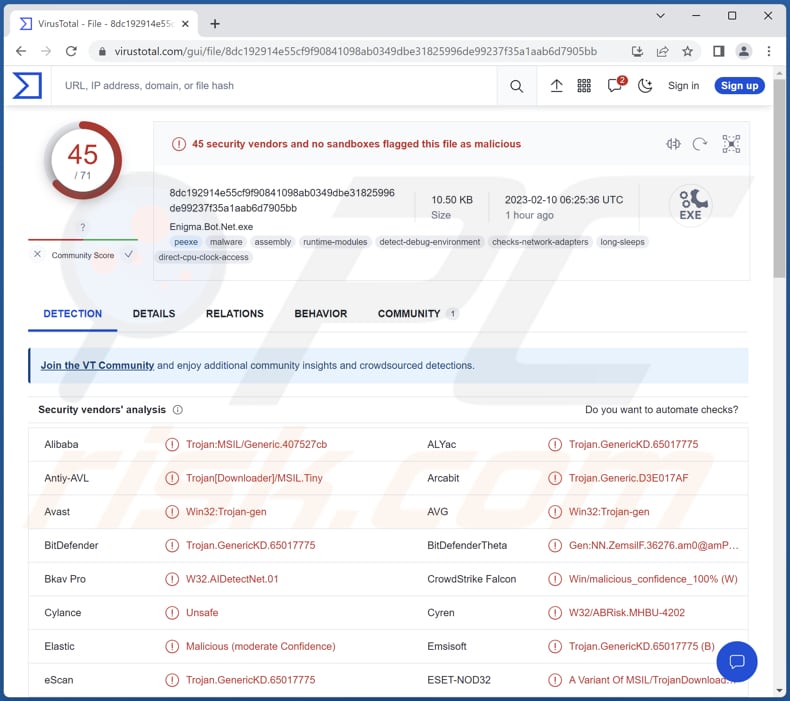
More about Enigma
The Enigma stealer is created with the intention of gathering information from a target system, as well as stealing sensitive information like tokens, passwords, and usernames from various sources such as Google Chrome, Microsoft Edge, Microsoft Outlook, Telegram, Signal, OpenVPN, and others.
In addition, it has the ability to take screenshots, gather information from the clipboard, and extract VPN configurations. Enigma also includes a keylogger module enabling it to record keyboard input. This stealer sends all obtained information to threat actors via Telegram.
It is known that cybercriminals behind Enigma stealer target individuals involved in the cryptocurrency industry.
The information obtained by the Enigma stealer can be sold on the dark web to third parties and used for identity theft, unauthorized access to the victim's accounts, theft of funds, and other malicious activities. Thus, malware of this type should be removed from compromised computers as soon as possible.
| Name | Enigma information stealer |
| Threat Type | Trojan, password-stealing virus, banking malware, spyware. |
| Detection Names (Enigma Loader) | Avast (Win64:PWSX-gen [Trj]), Combo Cleaner (Trojan.Generic.33196003), ESET-NOD32 (A Variant Of Generik.GESYDIZ), Kaspersky (Trojan.Win32.Agent.xatfjt), Microsoft (Trojan:Win32/Casdet!rfn), Full List (VirusTotal) |
| Detection Names (Enigma) | Avast (Win32:Trojan-gen), Combo Cleaner (Trojan.GenericKD.65017775), ESET-NOD32 (A Variant Of MSIL/TrojanDownloader.Tiny.AAU), Kaspersky (HEUR:Trojan.MSIL.Agent.gen), Microsoft (Trojan:Win32/Casdet!rfn), Full List (VirusTotal) |
| Symptoms | Information stealers often to stealthily infiltrate the victim's computer and remain silent, and thus no particular symptoms are clearly visible on an infected machine. |
| Distribution methods | Infected email attachments, malicious online advertisements, social engineering, software 'cracks'. |
| Damage | Stolen passwords and banking information, identity theft, the victim's computer added to a botnet. |
| Malware Removal (Windows) |
To eliminate possible malware infections, scan your computer with legitimate antivirus software. Our security researchers recommend using Combo Cleaner. Download Combo CleanerTo use full-featured product, you have to purchase a license for Combo Cleaner. 7 days free trial available. Combo Cleaner is owned and operated by RCS LT, the parent company of PCRisk.com. |
Information stealers in general
Information stealer is a type of malicious software that is designed to steal sensitive information from a victim's computer. Typically, cybercriminals behind information stealers aim to obtain credit card details, ID card information, login credentials, social security numbers, seed phrases, and other data.
The stolen information can then be used for various malicious purposes, such as identity theft, financial fraud, etc. Examples of different stealers are Graphiron Stealer, Creal Stealer, and RL Stealer.
How did Enigma infiltrate my computer?
Cybercriminals are spreading the Enigma stealer using a harmful RAR archive that is sent to potential victims through phishing emails or via social media platforms. The archive consists of two files: "Interview questions.txt" and "Interview conditions.word.exe" (the names of these files may vary).
The latter is an executable file designed to trick unsuspecting victims into running the loader and infecting their computers with Enigma information stealer.
How to avoid installation of malware?
Exercise caution when downloading files and software from the web. Always download them from trustworthy sources, such as official pages or verified stores. Stay alert when opening email attachments or clicking on links, especially in unexpected emails from unknown senders.
Ensure your operating system and installed programs are up to date. Never use untrusted tools to update or activate any software. Also, be wary of clicking on ads on dubious websites, use trustworthy antivirus software, and frequently scan your device for threats.
If you believe that your computer is already infected, we recommend running a scan with Combo Cleaner Antivirus for Windows to automatically eliminate infiltrated malware.
Fake employment document ("Interview questions.txt") alongside with the malicious executable disguised as a MS Word document:
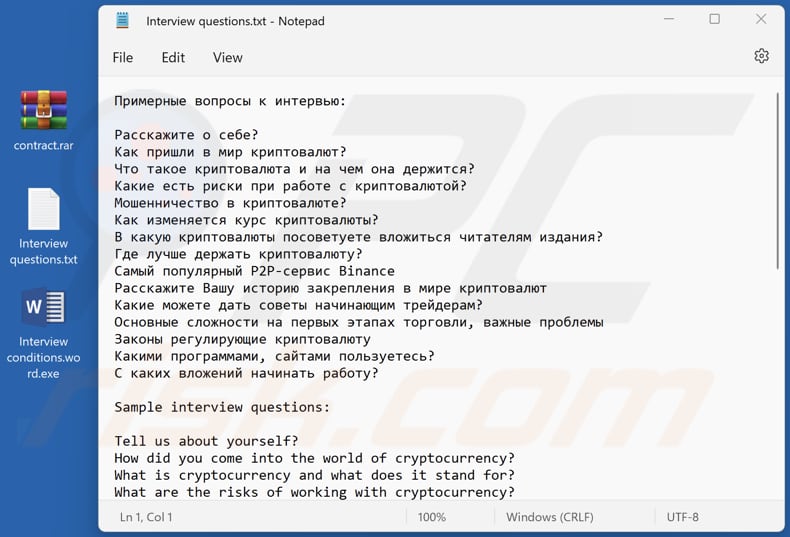
Text in this file:
Примерные вопросы к интервью:
Расскажите о себе?
Как пришли в мир криптовалют?
Что такое криптовалюта и на чем она держится?
Какие есть риски при работе с криптовалютой?
Мошенничество в криптовалюте?
Как изменяется курс криптовалюты?
В какую криптовалюты посоветуете вложиться читателям издания?
Где лучше держать криптовалюту?
Самый популярный P2P-сервис Binance
Расскажите Вашу историю закрепления в мире криптовалют
Какие можете дать советы начинающим трейдерам?
Основные сложности на первых этапах торговли, важные проблемы
Законы регулирующие криптовалюту
Какими программами, сайтами пользуетесь?
С каких вложений начинать работу?
Sample interview questions:
Tell us about yourself?
How did you come into the world of cryptocurrency?
What is cryptocurrency and what does it stand for?
What are the risks of working with cryptocurrency?
Cryptocurrency fraud?
How does the rate of cryptocurrency change?
What cryptocurrency would you advise readers to invest in?
Where is the best place to keep cryptocurrency?
The most popular P2P service Binance
What is your story about getting a foothold in the cryptocurrency world?
What advice can you give to beginner traders?
Main difficulties at the first stages of trading, important problems
Laws regulating Cryptocurrency
What programs, websites do you use?
What investment should I start with?
Приблизні запитання до інтерв’ю:
Розкажіть про себе?
Як прийшли у світ криптовалют?
Що таке криптовалюта і на чому вона тримається?
Які є ризики при роботі з криптовалютою?
Шахрайство в криптовалюті?
Як змінюється курс криптовалюти?
У яку криптовалюту порадите вкластися читачам видання?
Де краще тримати криптовалюту?
Найпопулярніший P2P-сервіс Binance
Розкажіть Вашу історію закріплення у світі криптовалют
Які можете дати поради трейдерам-початківцям?
Основні складнощі на перших етапах торгівлі, важливі проблеми
Закони, що регулюють криптовалюту
Якими програмами, сайтами користуєтеся?
З яких вкладень починати роботу?
Administration panel login page:
Instant automatic malware removal:
Manual threat removal might be a lengthy and complicated process that requires advanced IT skills. Combo Cleaner is a professional automatic malware removal tool that is recommended to get rid of malware. Download it by clicking the button below:
DOWNLOAD Combo CleanerBy downloading any software listed on this website you agree to our Privacy Policy and Terms of Use. To use full-featured product, you have to purchase a license for Combo Cleaner. 7 days free trial available. Combo Cleaner is owned and operated by RCS LT, the parent company of PCRisk.com.
Quick menu:
How to remove malware manually?
Manual malware removal is a complicated task - usually it is best to allow antivirus or anti-malware programs to do this automatically. To remove this malware we recommend using Combo Cleaner Antivirus for Windows.
If you wish to remove malware manually, the first step is to identify the name of the malware that you are trying to remove. Here is an example of a suspicious program running on a user's computer:
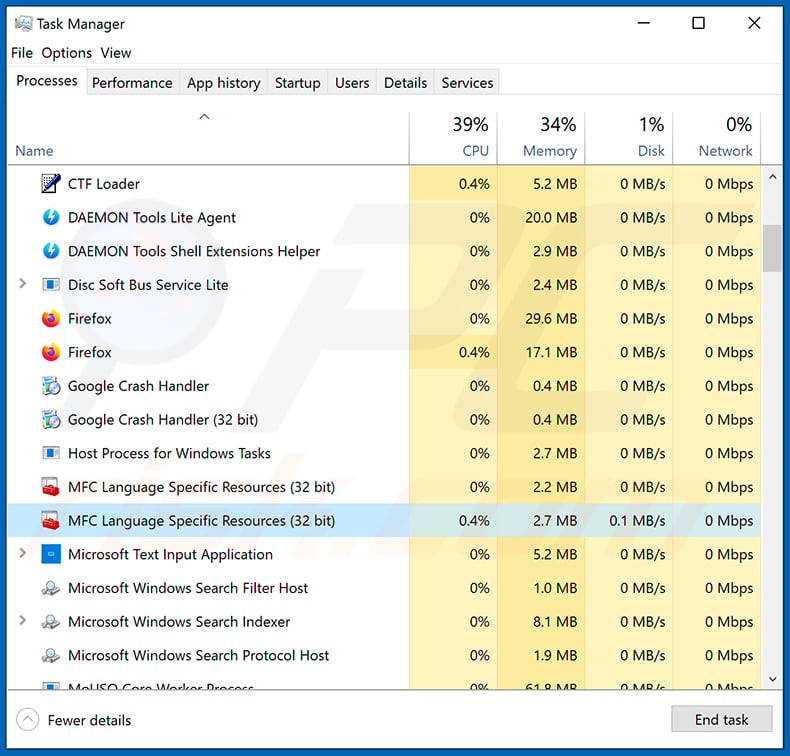
If you checked the list of programs running on your computer, for example, using task manager, and identified a program that looks suspicious, you should continue with these steps:
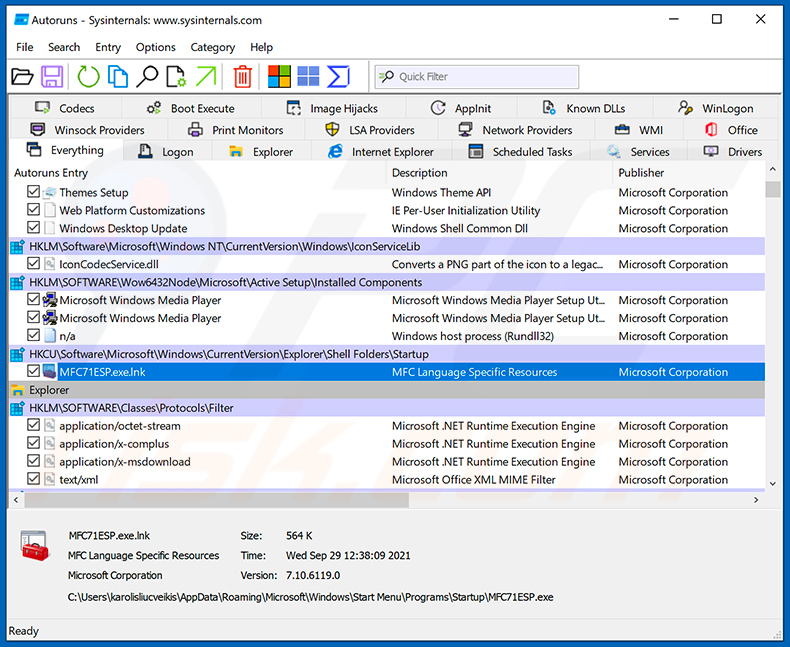
 Download a program called Autoruns. This program shows auto-start applications, Registry, and file system locations:
Download a program called Autoruns. This program shows auto-start applications, Registry, and file system locations:
 Restart your computer into Safe Mode:
Restart your computer into Safe Mode:
Windows XP and Windows 7 users: Start your computer in Safe Mode. Click Start, click Shut Down, click Restart, click OK. During your computer start process, press the F8 key on your keyboard multiple times until you see the Windows Advanced Option menu, and then select Safe Mode with Networking from the list.
Video showing how to start Windows 7 in "Safe Mode with Networking":
Windows 8 users: Start Windows 8 is Safe Mode with Networking - Go to Windows 8 Start Screen, type Advanced, in the search results select Settings. Click Advanced startup options, in the opened "General PC Settings" window, select Advanced startup.
Click the "Restart now" button. Your computer will now restart into the "Advanced Startup options menu". Click the "Troubleshoot" button, and then click the "Advanced options" button. In the advanced option screen, click "Startup settings".
Click the "Restart" button. Your PC will restart into the Startup Settings screen. Press F5 to boot in Safe Mode with Networking.
Video showing how to start Windows 8 in "Safe Mode with Networking":
Windows 10 users: Click the Windows logo and select the Power icon. In the opened menu click "Restart" while holding "Shift" button on your keyboard. In the "choose an option" window click on the "Troubleshoot", next select "Advanced options".
In the advanced options menu select "Startup Settings" and click on the "Restart" button. In the following window you should click the "F5" button on your keyboard. This will restart your operating system in safe mode with networking.
Video showing how to start Windows 10 in "Safe Mode with Networking":
 Extract the downloaded archive and run the Autoruns.exe file.
Extract the downloaded archive and run the Autoruns.exe file.
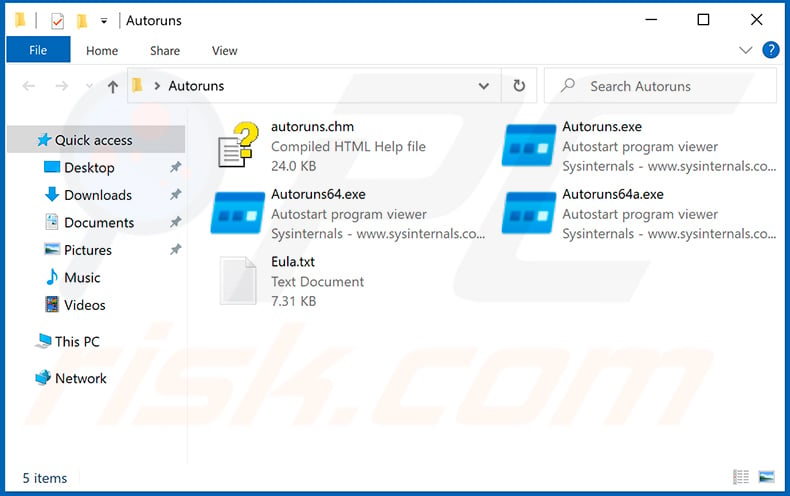
 In the Autoruns application, click "Options" at the top and uncheck "Hide Empty Locations" and "Hide Windows Entries" options. After this procedure, click the "Refresh" icon.
In the Autoruns application, click "Options" at the top and uncheck "Hide Empty Locations" and "Hide Windows Entries" options. After this procedure, click the "Refresh" icon.
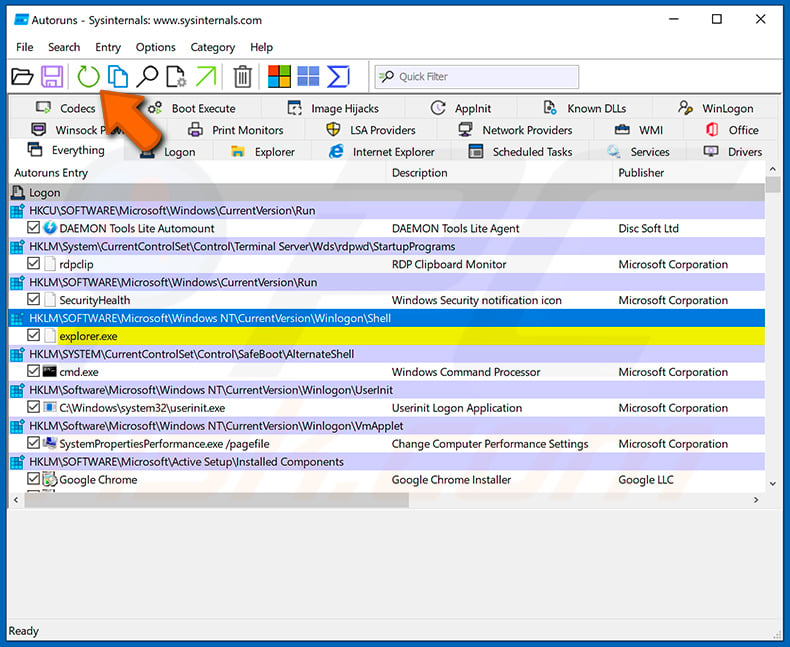
 Check the list provided by the Autoruns application and locate the malware file that you want to eliminate.
Check the list provided by the Autoruns application and locate the malware file that you want to eliminate.
You should write down its full path and name. Note that some malware hides process names under legitimate Windows process names. At this stage, it is very important to avoid removing system files. After you locate the suspicious program you wish to remove, right click your mouse over its name and choose "Delete".
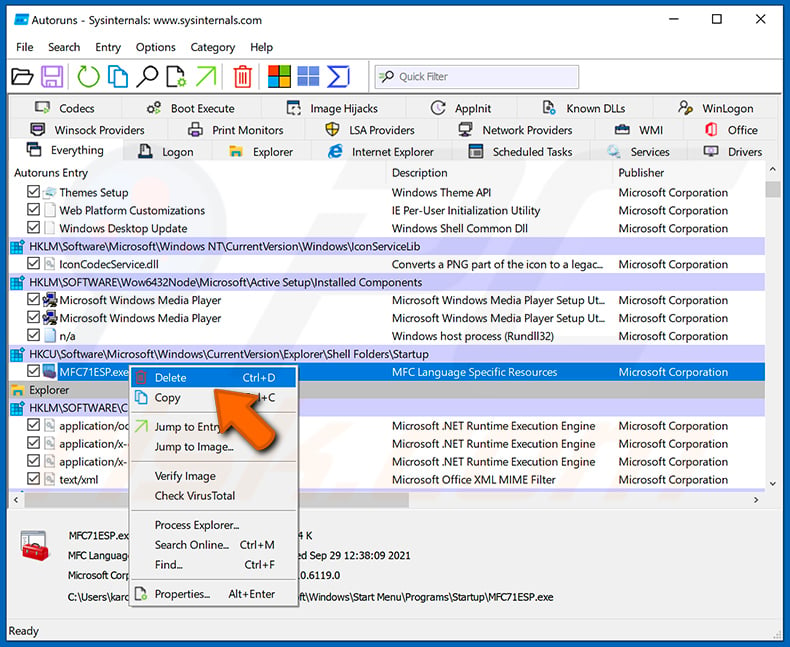
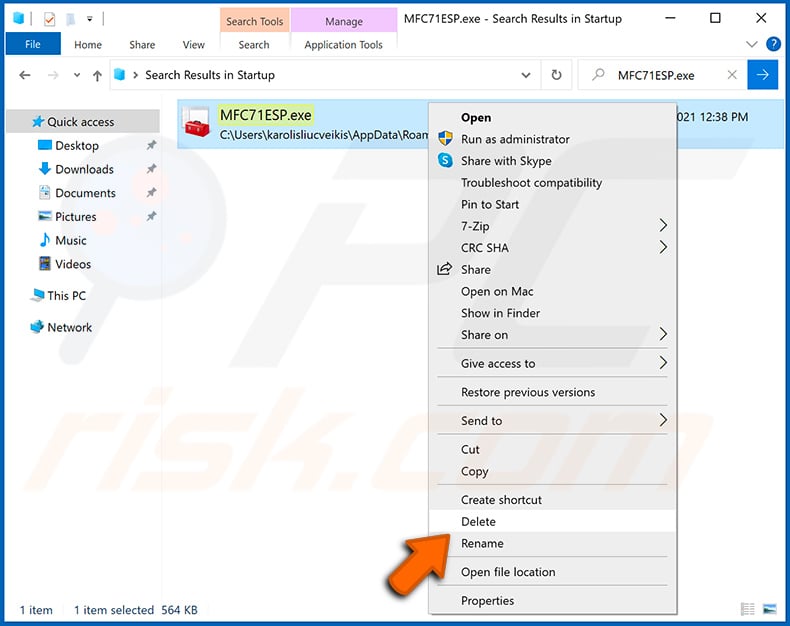
After removing the malware through the Autoruns application (this ensures that the malware will not run automatically on the next system startup), you should search for the malware name on your computer. Be sure to enable hidden files and folders before proceeding. If you find the filename of the malware, be sure to remove it.
Reboot your computer in normal mode. Following these steps should remove any malware from your computer. Note that manual threat removal requires advanced computer skills. If you do not have these skills, leave malware removal to antivirus and anti-malware programs.
These steps might not work with advanced malware infections. As always it is best to prevent infection than try to remove malware later. To keep your computer safe, install the latest operating system updates and use antivirus software. To be sure your computer is free of malware infections, we recommend scanning it with Combo Cleaner Antivirus for Windows.
Frequently Asked Questions (FAQ)
My computer is infected with malware, should I format my storage device to get rid of it?
Formatting a storage device is a drastic measure and is usually not necessary to remove malware. There are other methods that can be used to remove malicious software, such as using antivirus software or manually deleting infected files.
What are the biggest issues that malware can cause?
The most common problems caused by malware include data and identity theft, network disruption, financial loss, data encryption, loss of privacy, and system damage.
What is the purpose of Enigma stealer?
The purpose of the Enigma stealer is to gather information from a target system and to steal sensitive data such as tokens, usernames, and passwords from various sources like Google Chrome, Microsoft Edge, Microsoft Outlook, Telegram, Signal, OpenVPN, among others. It can also take screenshots, collect data from the clipboard, and extract VPN configurations.
How did Enigma malware infiltrate my computer?
Threat actors are spreading the Enigma stealer by sending a malicious RAR archive through phishing emails or social media platforms. The archive contains two files: "Interview questions.txt" and "Interview conditions.word.exe". The infection chain starts after opening the executable file.
Will Combo Cleaner protect me from malware?
Yes, Combo Cleaner can detect and remove a wide range of malware infections. However, it is important to note that some highly advanced malware may hide deep within a system, which is why it is recommended to perform a full system scan to ensure that all potential threats are detected and eliminated.
Share:

Tomas Meskauskas
Expert security researcher, professional malware analyst
I am passionate about computer security and technology. I have an experience of over 10 years working in various companies related to computer technical issue solving and Internet security. I have been working as an author and editor for pcrisk.com since 2010. Follow me on Twitter and LinkedIn to stay informed about the latest online security threats.
PCrisk security portal is brought by a company RCS LT.
Joined forces of security researchers help educate computer users about the latest online security threats. More information about the company RCS LT.
Our malware removal guides are free. However, if you want to support us you can send us a donation.
DonatePCrisk security portal is brought by a company RCS LT.
Joined forces of security researchers help educate computer users about the latest online security threats. More information about the company RCS LT.
Our malware removal guides are free. However, if you want to support us you can send us a donation.
Donate
▼ Show Discussion