Get free scan and check if your device is infected.
Remove it nowTo use full-featured product, you have to purchase a license for Combo Cleaner. Seven days free trial available. Combo Cleaner is owned and operated by RCS LT, the parent company of PCRisk.com.
What kind of malware is MacSync?
MacSync is a piece of malicious software that is a rebranded and upgraded version of the mac.c stealer. mac.c was developed in the spring of 2025, and a month later, the rebrand occurred. MacSync retains the data-stealer functionalities but also has backdoor capabilities. While the stealer was written in the C programming language, the backdoor module is based on the Go language.
MacSync activity is global; most infections were detected in Ukraine, the US, Germany, the UK, and Spain. This malware has been spread through ClickFix scams.
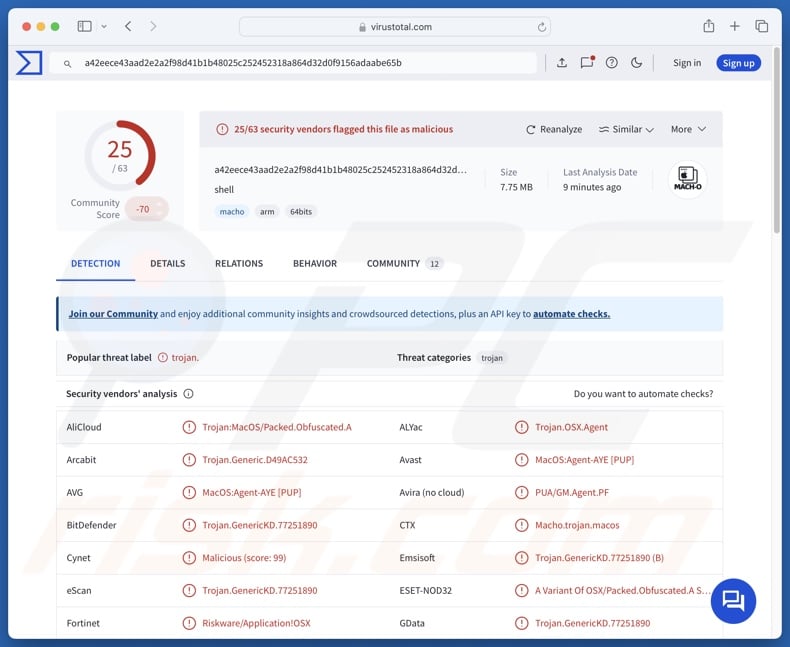
MacSync malware overview
The known MacSync infections originated from ClickFix scams that tricked victims into executing a malicious command on their devices, thus triggering the malware download/installation. Upon successful infiltration, MacSync displays a fake prompt requesting users to provide the device password.
The infection then progresses to the infiltration of the Go-based backdoor module. The backdoor seeks to connect to its C&C (Command and Control) server, and the stealer works on collecting data of interest. MacSync's measures against analysis and detection include code obfuscation and deletion of associated temporary files.
The information targeted by MacSync (e.g., personal files, log-in credentials, cryptowallets, etc.) and the methods for obtaining it remain the same as in its original mac.c stealer iteration. More information on this can be found in our dedicated article on mac.c stealer.
Backdoors are a type of malware designed to open a "backdoor" into systems. Usually, the goal is to prepare the device for further infection and possibly even carry it out. MacSync's backdoor component can receive and execute commands from its C&C server. As this malware has moved towards a modular approach, it might be used to introduce other modules in order to expand its functionalities.
To summarize, the presence of malicious software like MacSync on devices can lead to multiple system infections, serious privacy issues, financial losses, and identity theft.
| Name | MacSync virus |
| Threat Type | Mac malware, Mac virus, stealer, password-stealing virus, backdoor. |
| Detection Names | Avast (MacOS:Agent-AYE [PUP]), Combo Cleaner (Trojan.GenericKD.77251890), ESET-NOD32 (A Variant Of OSX/Packed.Obfuscated.A Susp), Kaspersky (HEUR:Trojan.OSX.Agent.gen), Full List Of Detections (VirusTotal) |
| Symptoms | Malware is designed to stealthily infiltrate the victim's computer and remain silent, and thus no particular symptoms are clearly visible on an infected machine. |
| Distribution Methods | Infected email attachments, malicious online advertisements, social engineering, software 'cracks'. |
| Damage | Stolen passwords and banking information, identity theft, the victim's computer added to a botnet. |
| Malware Removal (Windows) |
To eliminate possible malware infections, scan your computer with legitimate antivirus software. Our security researchers recommend using Combo Cleaner. Download Combo CleanerTo use full-featured product, you have to purchase a license for Combo Cleaner. 7 days free trial available. Combo Cleaner is owned and operated by RCS LT, the parent company of PCRisk.com. |
Similar malware examples
We have investigated countless malicious programs; Shamos, Odyssey, Cthulhu – are merely a few of our articles on Mac-targeting stealers, and NokNok, RShell, macOS.Macma – on backdoors.
To expand on these malicious programs, stealers can target specific details only or a broad range of information. Theoretically, backdoors and similar software can cause just about any type of infection – trojans, ransomware, cryptocurrency miners, etc. Yet in practice, these programs tend to operate within certain specifications or limitations.
It must be emphasized that regardless of how malware operates – its presence on a system endangers device integrity and user safety. Therefore, all threats must be eliminated immediately upon detection.
How did MacSync infiltrate my computer?
MacSync has been observed being proliferated via Cloudflare-themed ClickFix scams. More details can be found in our dedicated article for the Mac-specific version of these scams. However, other methods are possible.
Phishing and social engineering tactics are standard in malware distribution. Malicious software is often disguised as or bundled with ordinary content.
The most prevalent malware proliferation techniques include: online scams, malvertising, drive-by (stealthy/deceptive) downloads, suspicious download sources (e.g., freeware and third-party websites, Peer-to-Peer sharing networks, etc.), malicious attachments or links in spam mail (e.g., emails, PMs/DMs, etc.), illegal software activation ("cracking") tools, and fake updates.
Furthermore, some malicious programs can self-spread through local networks and removable storage devices (e.g., USB flash drives, external hard drives, etc.).
How to avoid installation of malware?
We strongly advise downloading only from official and verified sources. All programs must be activated and updated using functions/tools provided by legitimate developers, as those acquired from third-parties can contain malware.
Additionally, be vigilant when browsing since the Internet is full of deceptive and dangerous content. Incoming emails and other messages must be approached with caution. Attachments or links present in suspicious/irrelevant mail must not be opened, as they can be virulent.
It is essential to have a reputable antivirus installed and kept up-to-date. Security software must be used to run regular system scans and to remove threats and issues. If your computer is already infected, we recommend running a scan with Combo Cleaner Antivirus for Windows to automatically eliminate infiltrated malware.
Update January 13, 2026 – new MacSync variant has been discovered. Unlike in the past, this malware did not proliferate through ClickFix scams or the "Drag-to-Terminal" execution, both of which require a higher level of user interaction. This version eschewed any Terminal interaction on the victim's part.
The MacSync iteration arrived onto systems via a digitally signed and notarized Swift application (DMG – Apple Disk Image file), the certificate of which has since been revoked. Thus, the program was able to bypass Gatekeeper – Mac's security feature. Other observed anti-detection techniques included checking whether it was executed in a sandbox environment and inflation of the DMG file with LibreOffice-related PDF documents.
Instant automatic malware removal:
Manual threat removal might be a lengthy and complicated process that requires advanced IT skills. Combo Cleaner is a professional automatic malware removal tool that is recommended to get rid of malware. Download it by clicking the button below:
DOWNLOAD Combo CleanerBy downloading any software listed on this website you agree to our Privacy Policy and Terms of Use. To use full-featured product, you have to purchase a license for Combo Cleaner. 7 days free trial available. Combo Cleaner is owned and operated by RCS LT, the parent company of PCRisk.com.
Quick menu:
Video showing how to remove adware and browser hijackers from a Mac computer:
Potentially unwanted applications removal:
Remove potentially unwanted applications from your "Applications" folder:
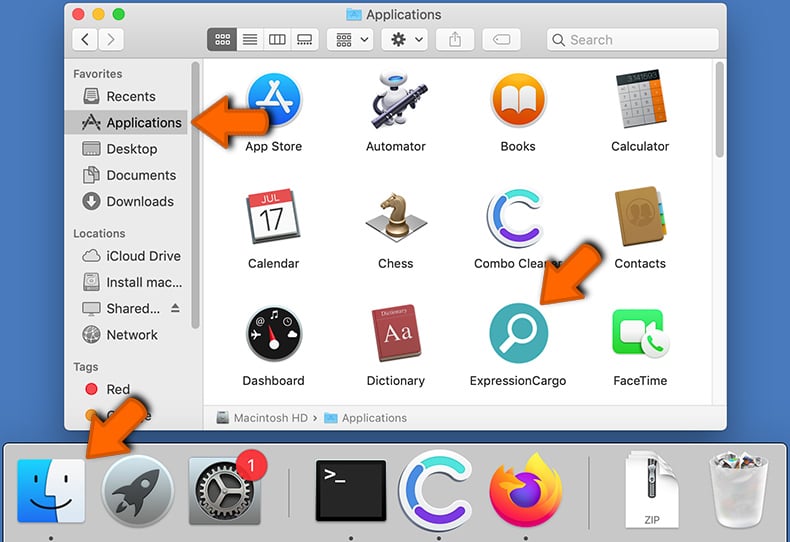
Click the Finder icon. In the Finder window, select "Applications". In the applications folder, look for "MPlayerX","NicePlayer", or other suspicious applications and drag them to the Trash. After removing the potentially unwanted application(s) that cause online ads, scan your Mac for any remaining unwanted components.
DOWNLOAD remover for malware infections
Combo Cleaner checks if your computer is infected with malware. To use full-featured product, you have to purchase a license for Combo Cleaner. 7 days free trial available. Combo Cleaner is owned and operated by RCS LT, the parent company of PCRisk.com.
Frequently Asked Questions (FAQ)
My computer is infected with MacSync malware, should I format my storage device to get rid of it?
No, malware removal rarely necessitates formatting.
What are the biggest issues that MacSync malware can cause?
The dangers posed by an infection differ depending on the malware's abilities and the attackers' goals. MacSync can open a "backdoor" to systems, execute various commands, and gather sensitive data. Generally, malware of this kind can cause multiple system infections, severe privacy issues, financial losses, and identity theft.
What is the purpose of MacSync malware?
Typically, malware is used to generate revenue. Aside from financial gain, other motivations behind malware attacks include the cyber criminals seeking amusement or the realization of personal grudges, process disruption (e.g., sites, services, companies, etc.), hacktivism, and political/geopolitical reasons.
How did MacSync malware infiltrate my computer?
MacSync has been proliferated via ClickFix scams, but other methods are not unlikely. The most prevalent malware distribution techniques include: drive-by downloads, malvertising, trojans, malspam, online scams, suspicious download channels (e.g., freeware and third-party websites, P2P sharing networks, etc.), fake updaters, and illegal software activation tools ("cracks"). Some malicious programs can self-spread through local networks and removable storage devices.
Will Combo Cleaner protect me from malware?
Yes, Combo Cleaner is capable of detecting and eliminating practically all known malware infections. Keep in mind that performing a complete system scan is paramount since sophisticated malicious software usually hides deep within systems.
Share:

Tomas Meskauskas
Expert security researcher, professional malware analyst
I am passionate about computer security and technology. I have an experience of over 10 years working in various companies related to computer technical issue solving and Internet security. I have been working as an author and editor for pcrisk.com since 2010. Follow me on Twitter and LinkedIn to stay informed about the latest online security threats.
PCrisk security portal is brought by a company RCS LT.
Joined forces of security researchers help educate computer users about the latest online security threats. More information about the company RCS LT.
Our malware removal guides are free. However, if you want to support us you can send us a donation.
DonatePCrisk security portal is brought by a company RCS LT.
Joined forces of security researchers help educate computer users about the latest online security threats. More information about the company RCS LT.
Our malware removal guides are free. However, if you want to support us you can send us a donation.
Donate
▼ Show Discussion