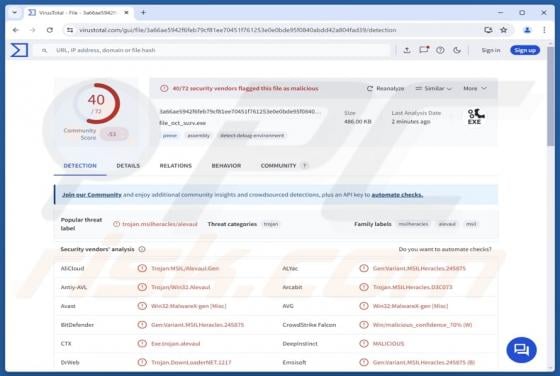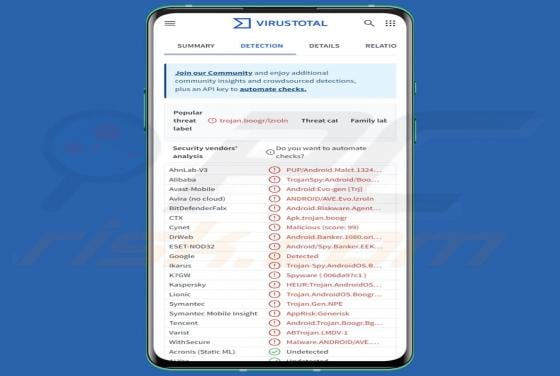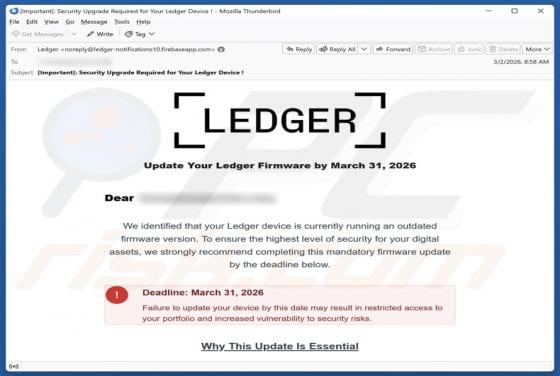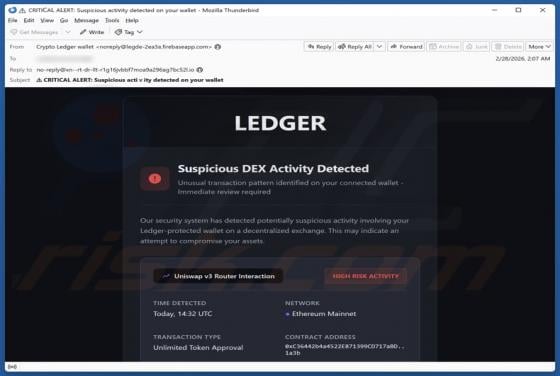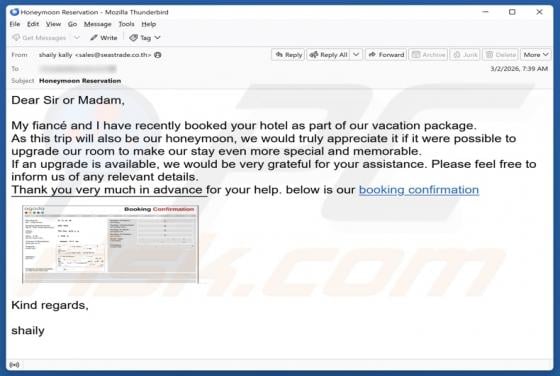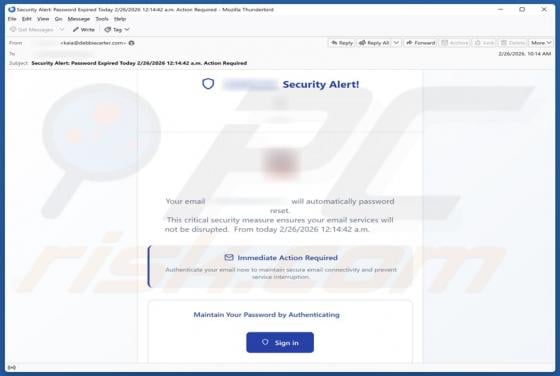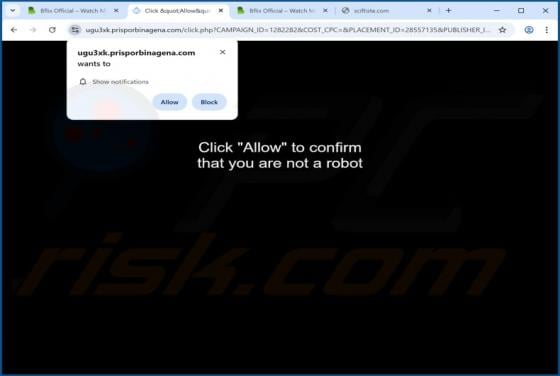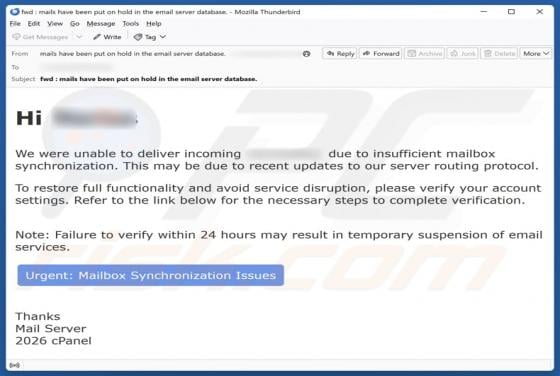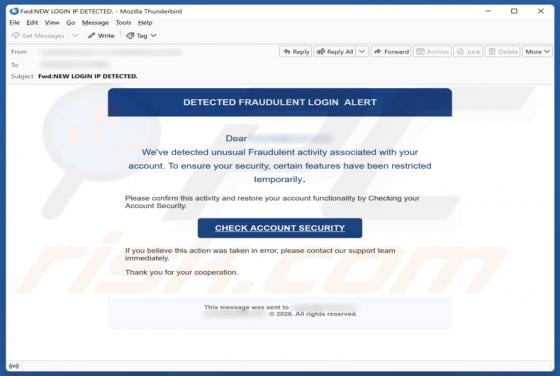
Fraudulent Activity Email Scam
We have checked the message and discovered that it is from scammers. This deceptive email is presented as a notification from an email service provider. It warns recipients about a supposedly detected fraudulent activity to trick them into opening a fake website. The purpose of this scam email is