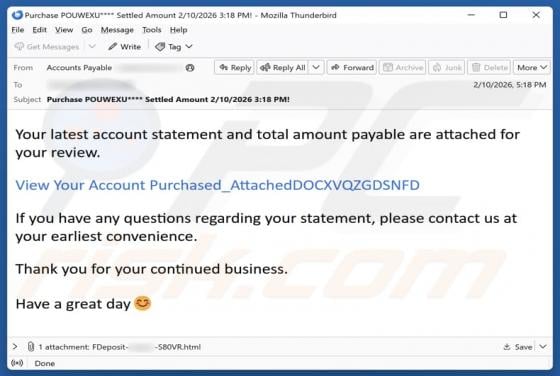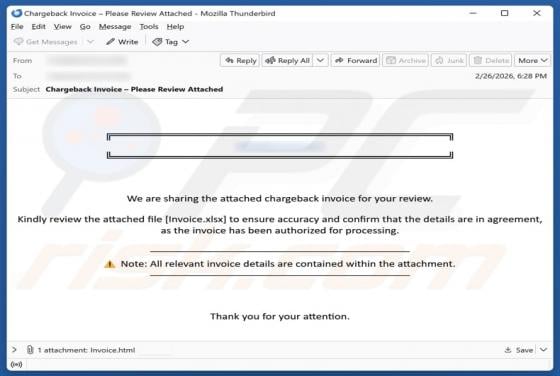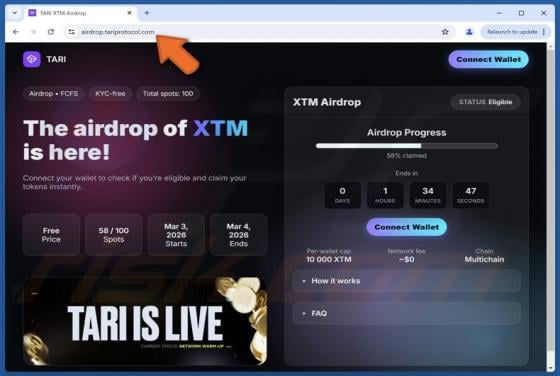
Fake Tari XTM Airdrop Scam
We have reviewed the site (airdrop.tariprotocol[.]com) and determined that it is a scam page posing as the original Tari platform, airdrop.tari.com. The fraudulent copy is operated by scammers who seek to steal cryptocurrency from unsuspecting visitors. It should not be trusted to avoid financial