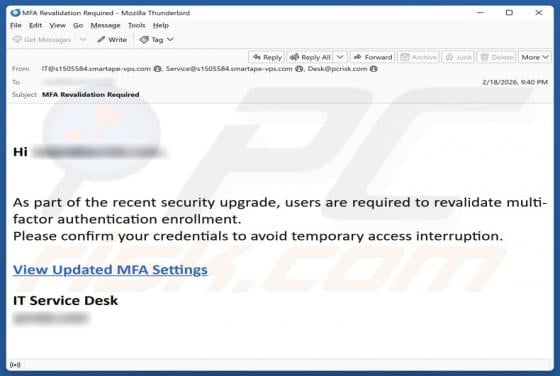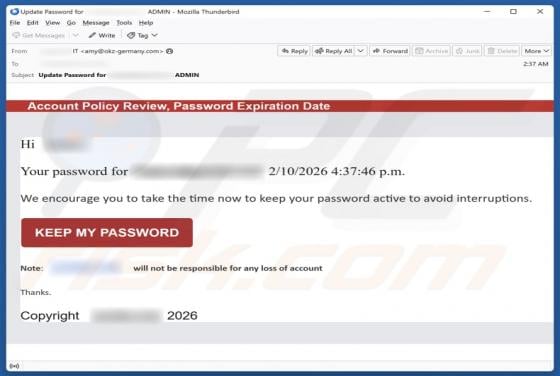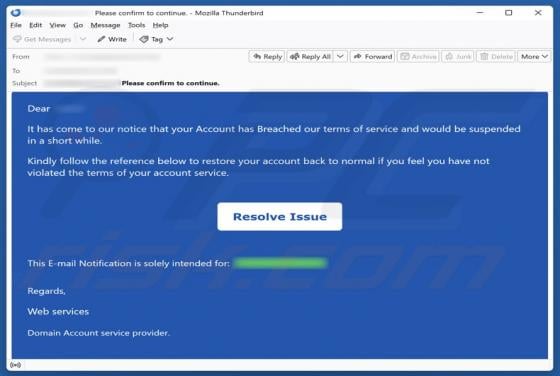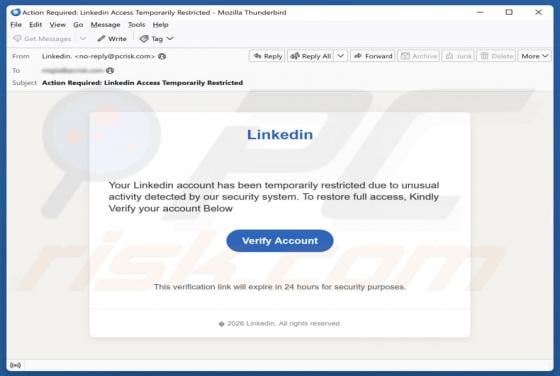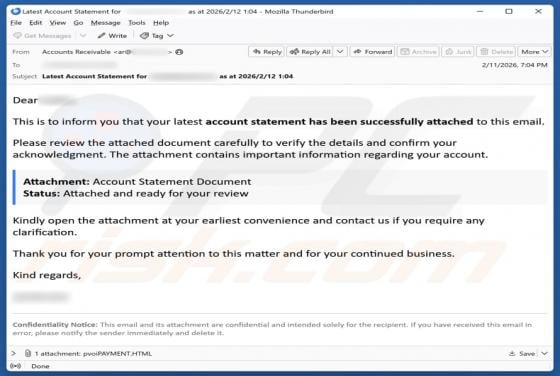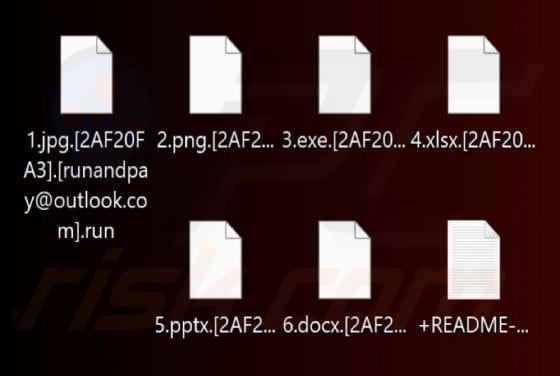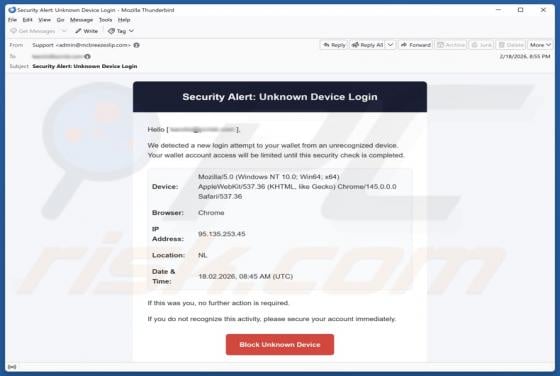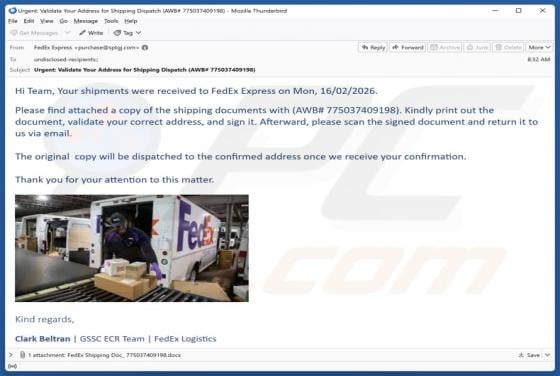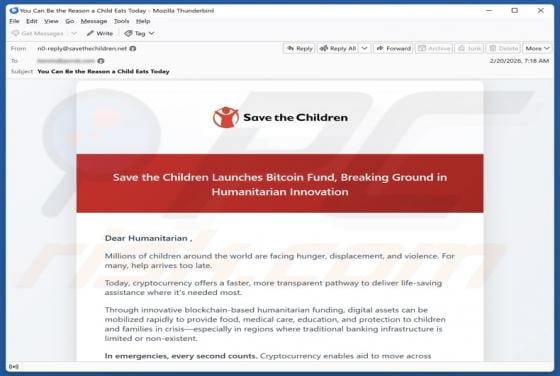
Fake Save the Children Bitcoin Fund Email Scam
We have reviewed the email and concluded that it is disguised as an invitation from the Save the Children non-profit organization to contribute to humanitarian funding. The scammers behind this fraudulent email seek to trick unsuspecting recipients into transferring cryptocurrency to them. This em