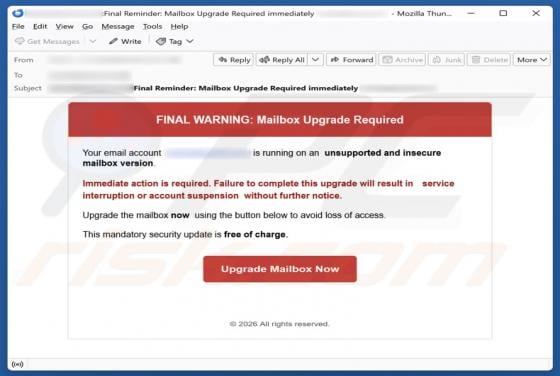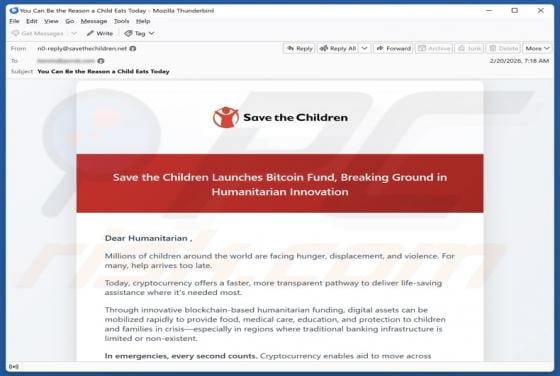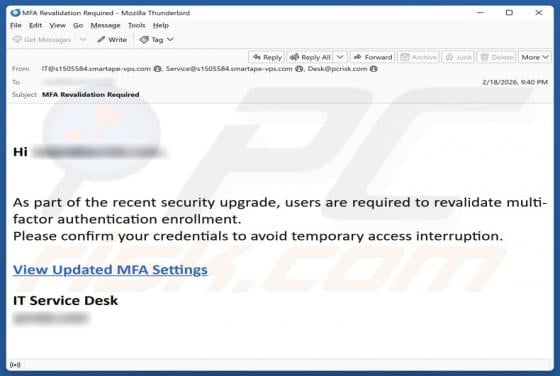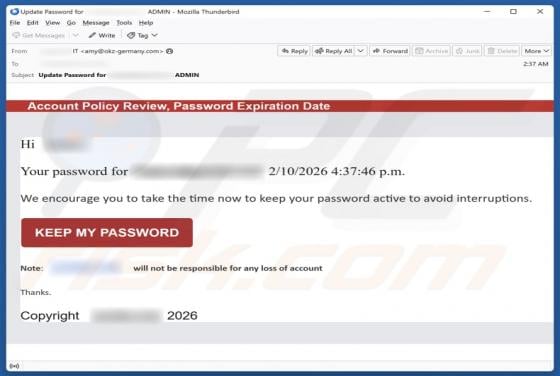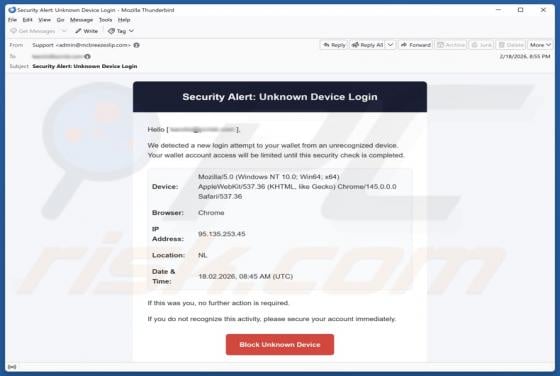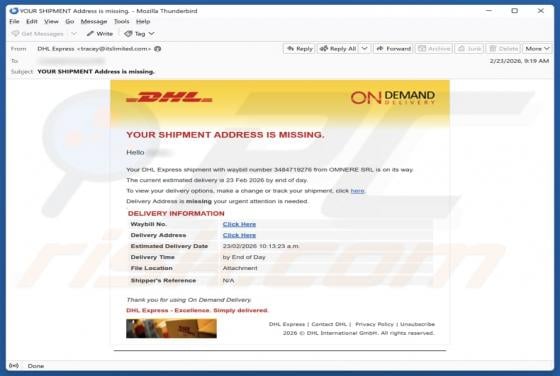
DHL - Shipment Address Is Missing Email Scam
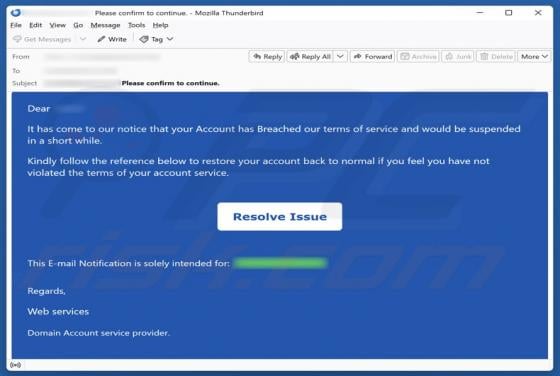
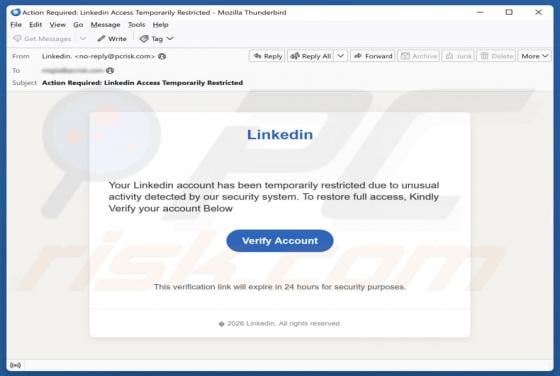
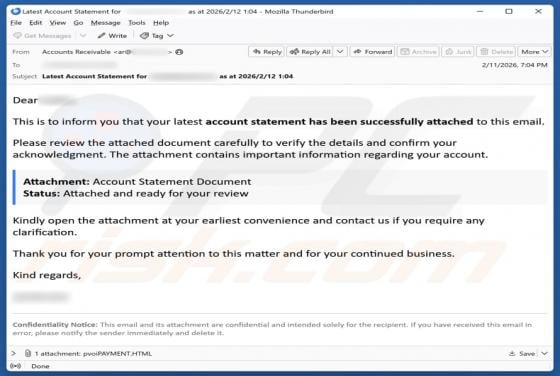
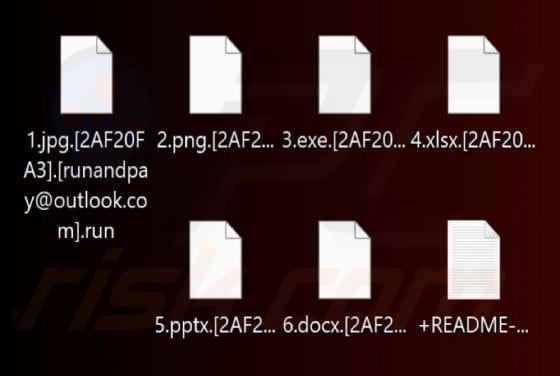
We have examined the email and concluded that it is a phishing attempt presented as a delivery notification from DHL, a legitimate logistics and courier company. It contains a link to a fake website created to trick visitors into entering personal details. Falling for this scam can result in accou