DailyPanel Adware (Mac)
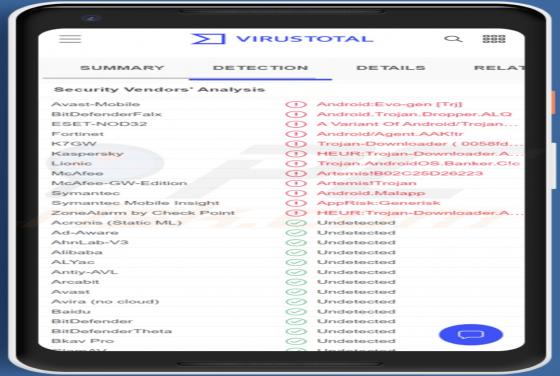
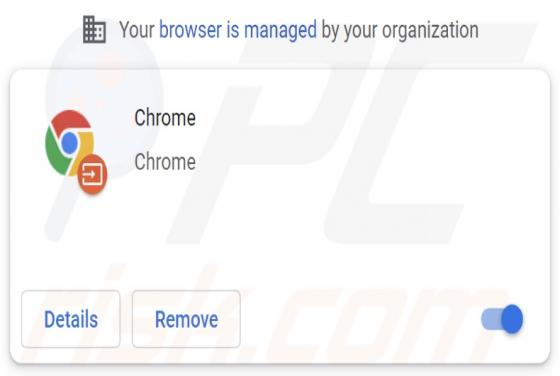
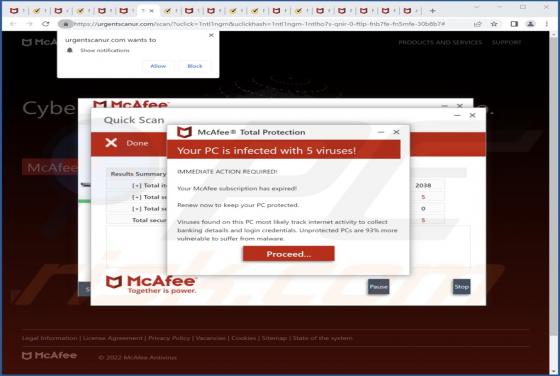
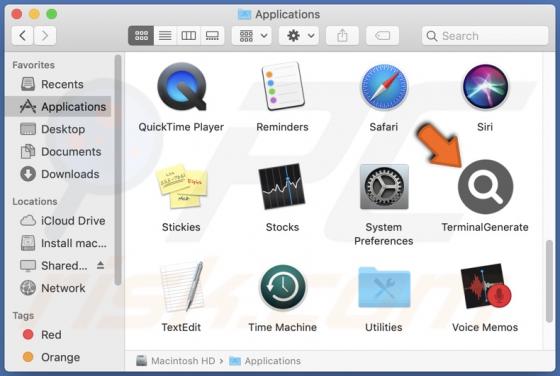
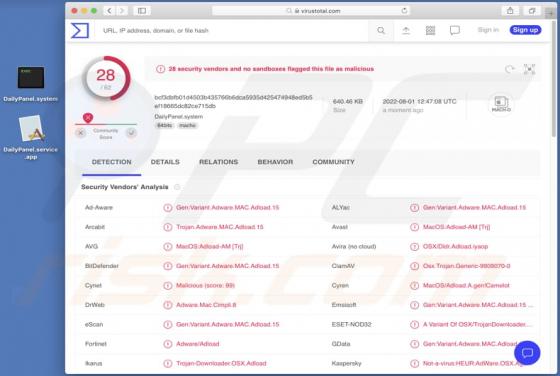
DailyPanel is an application that shows unwanted advertisements. It is an advertising-supported app (adware). Our team discovered DailyPanel while examining websites claiming that the Adobe Flash Player is out of date. DailyPanel is distributed via a fake installer. Advertisements displa