Watchvideo.cc Ads
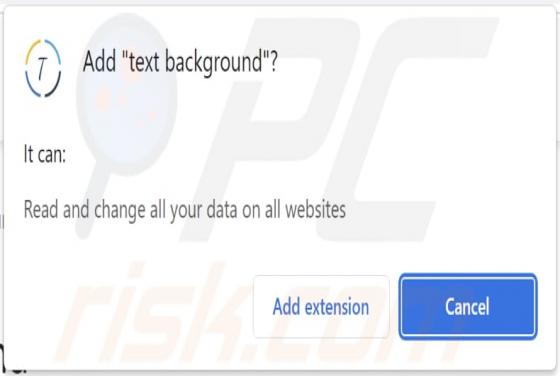
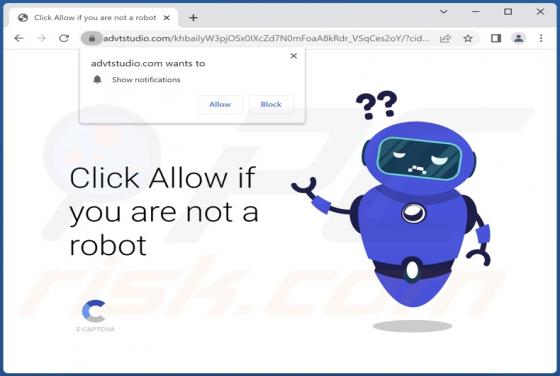
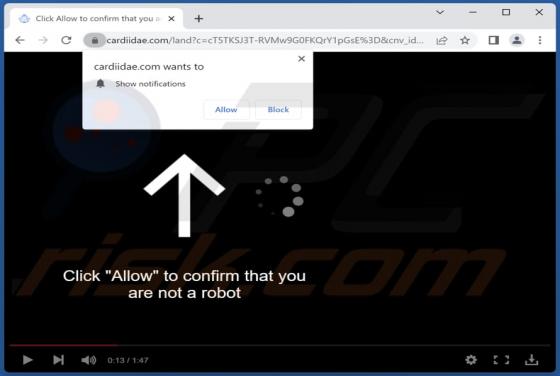
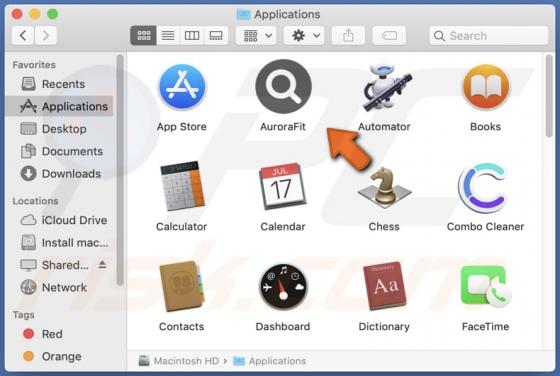
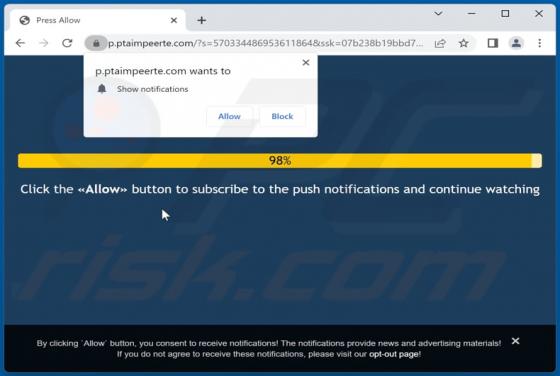
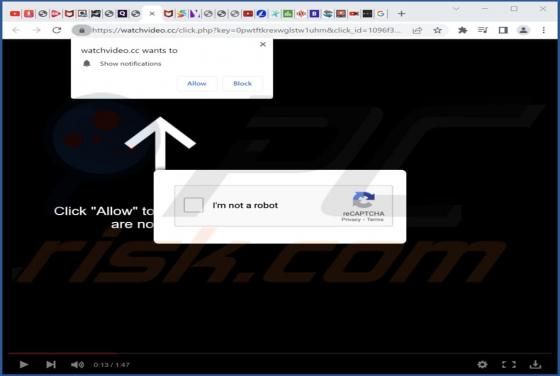
While inspecting websites that use rogue advertising networks (and shady ads), we came across watchvideo[.]cc - another untrustworthy page. We learned that watchvideo[.]cc is a website that wants to show notifications (it displays deceptive content to trick visitors into agreeing to receive notifi