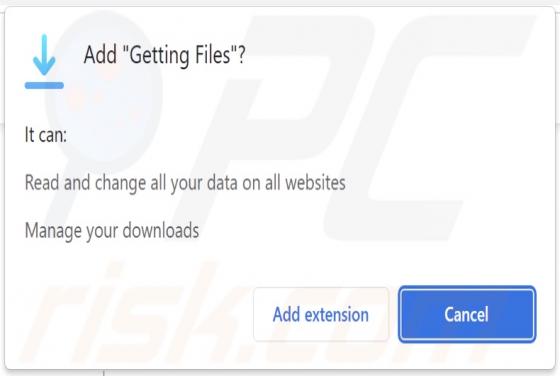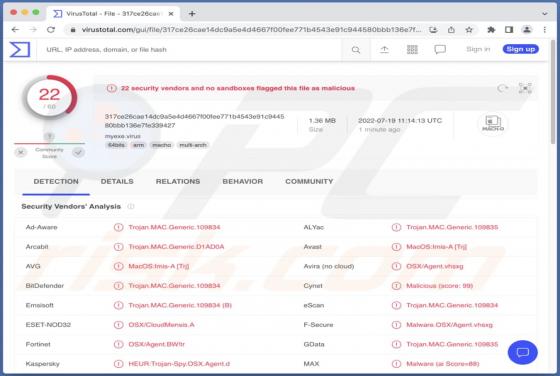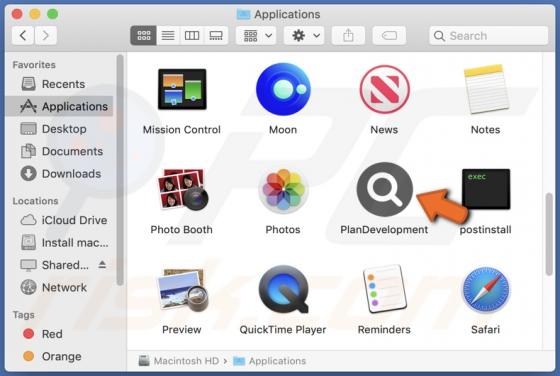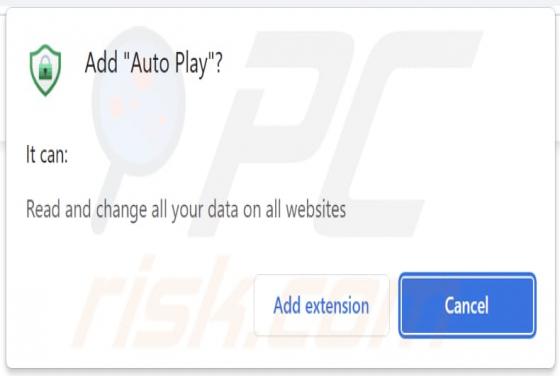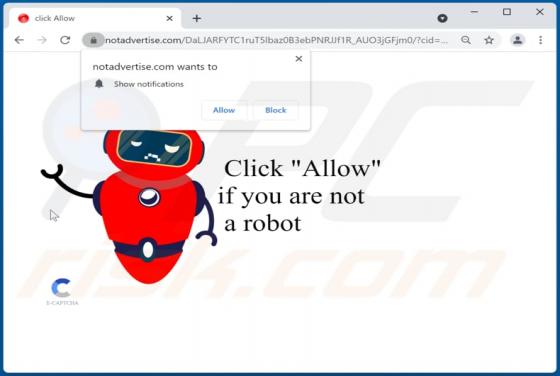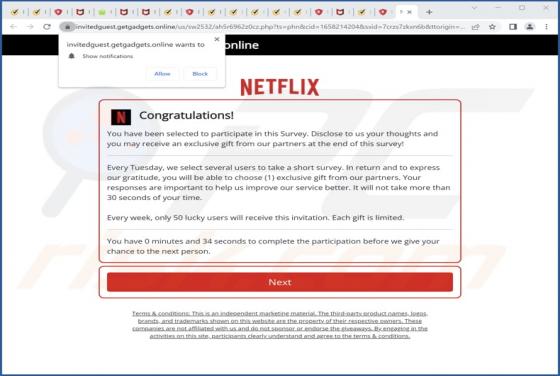
Getgadgets.online Ads
Getgadgets[.]online is a deceptive website that runs a fake survey and wants to display notifications. Our team discovered this page while inspecting other pages that use rogue advertising networks. Getgadgets[.]online is one of the many untrustworthy sites that should never be allowed to show not