Adsandcomputer.com Ads
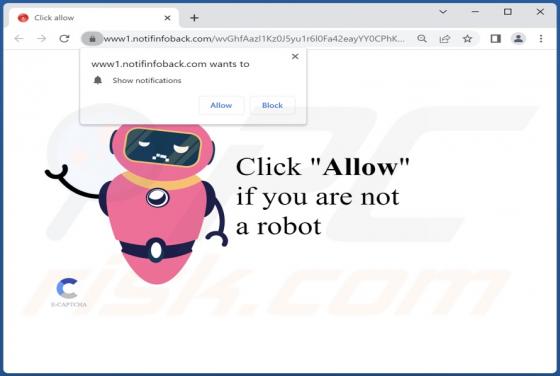
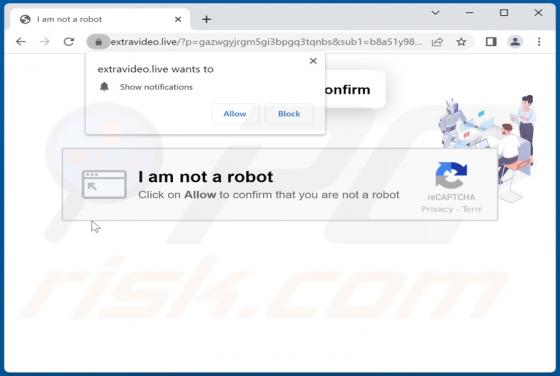
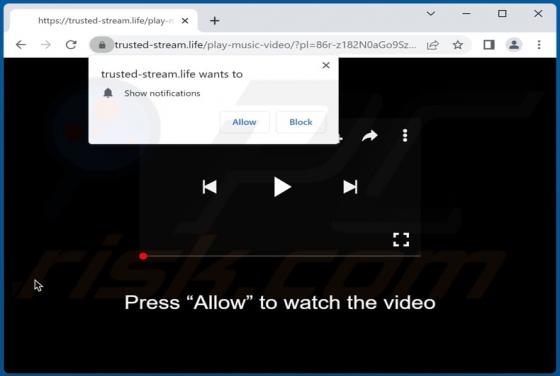
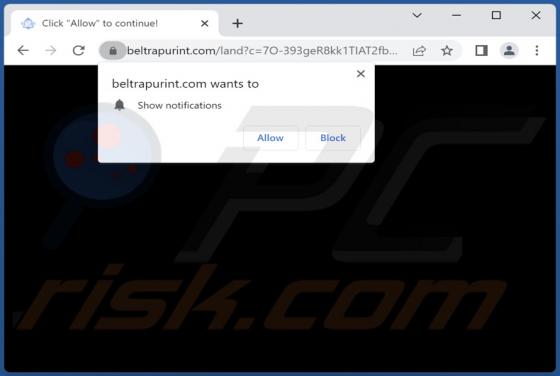
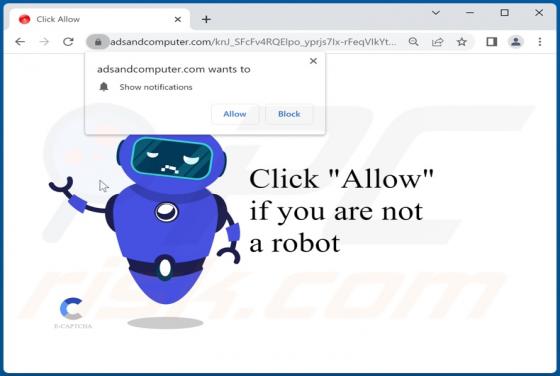
Our research team discovered the adsandcomputer[.]com rogue page while inspecting untrustworthy sites. This webpage promotes spam browser notifications and redirects visitors to other (likely unreliable/harmful) websites. Users typically access such pages via redirects caused by sites using rogue