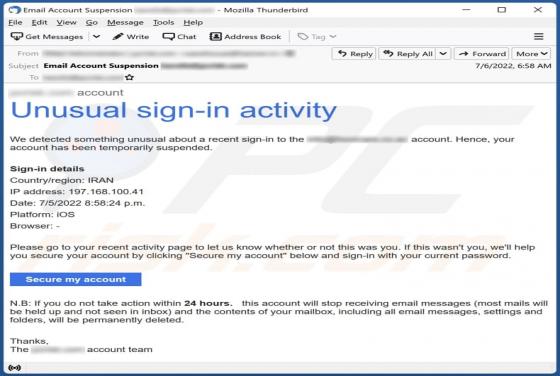
Unusual Sign-in Activity Email Scam
After examining this email, we learned that the scammers behind it attempt to trick recipients into providing their login credentials. They claim that the email account has been suspended due to unusual sign-in activity. They aim to trick recipients into opening the provided page and entering thei