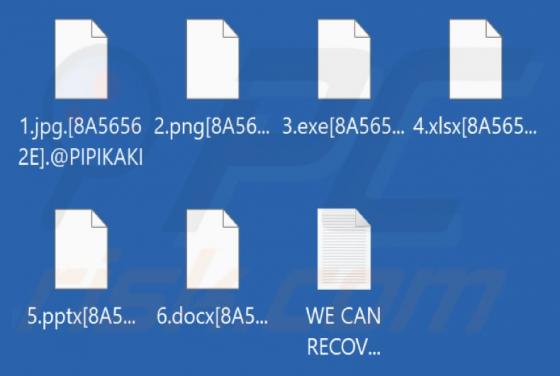
Pipikaki Ransomware
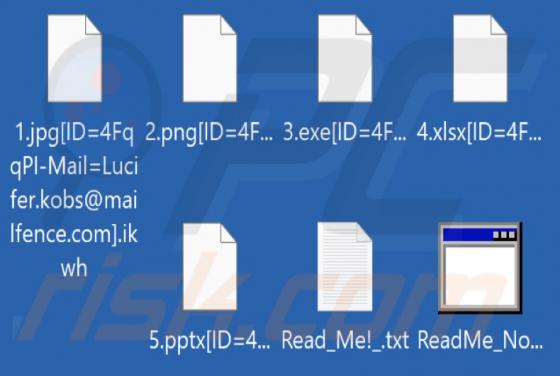
While checking various forums, we found a new ransomware called Pipikaki. It encrypts files, modifies filenames, and creates a ransom note. Pipikaki appends the victim's ID and ".@PIPIKAKI" extension to filenames. Its ransom note is a file named "WE CAN RECOVER YOUR DATA.txt". An example of how P