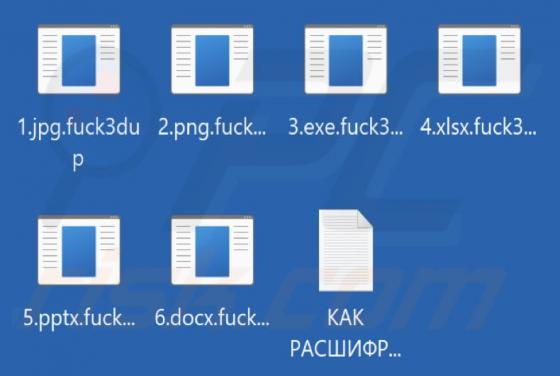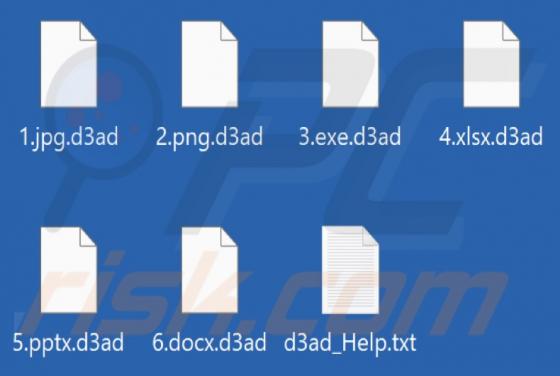
D3adCrypt Ransomware
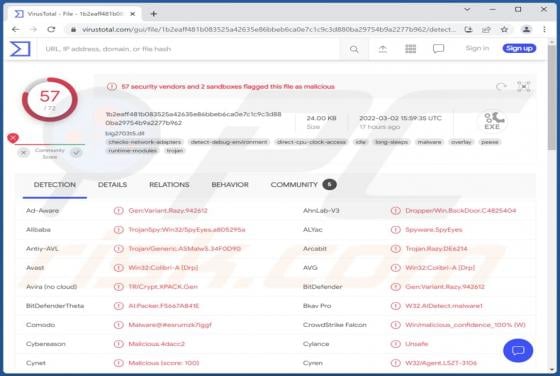
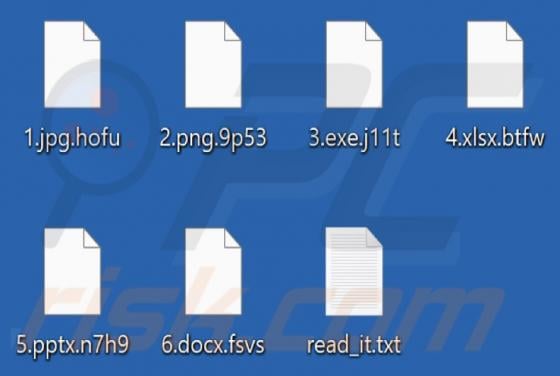
We learned of D3adCrypt when a victim reported it in a support forum. This malicious program is categorized as ransomware; it operates by encrypting data and making ransom demands for the decryption. Our researchers obtained a sample of D3adCrypt from VirusTotal. On our test machine, this ransomw