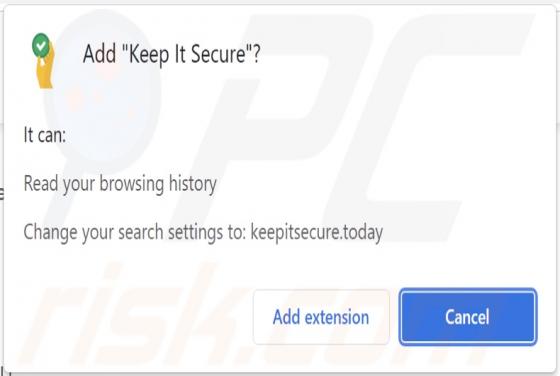
Keep It Secure Browser Hijacker
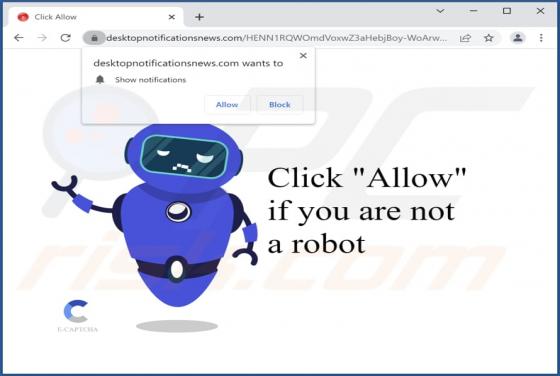
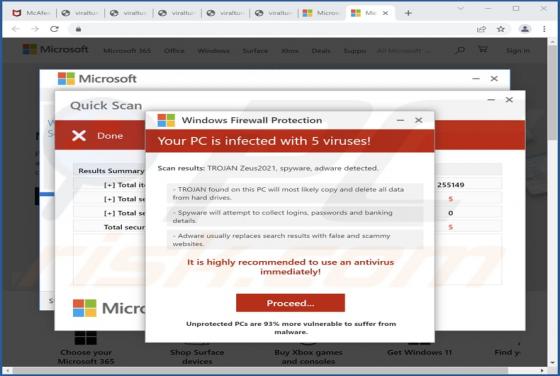
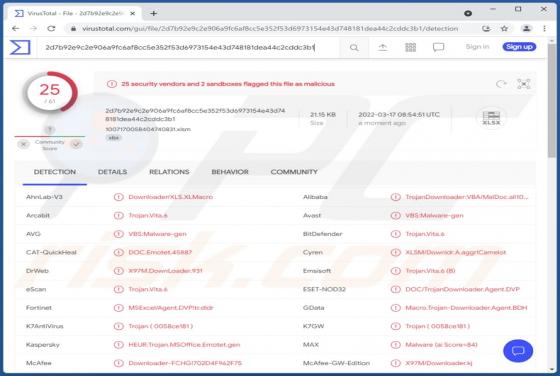
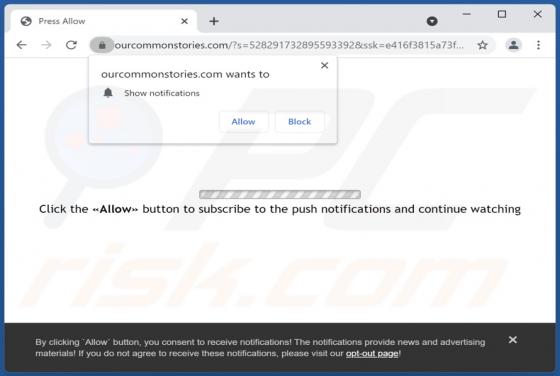
Keep It Secure is a browser extension our researchers discovered while inspecting dubious download webpages. After analyzing this piece of software, we learned that it operates as a browser hijacker. Keep It Secure modifies browser settings to promote (by causing redirects to) the keepitsecure.tod