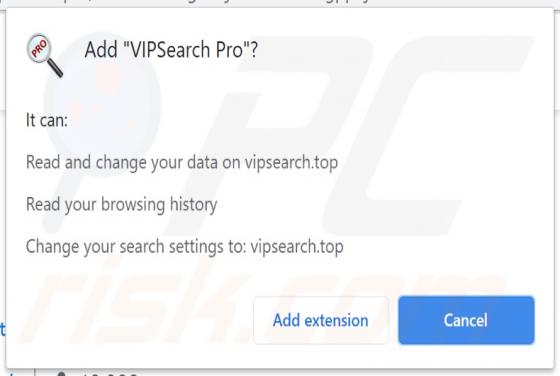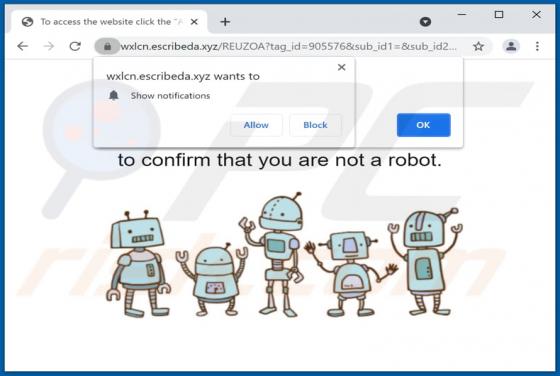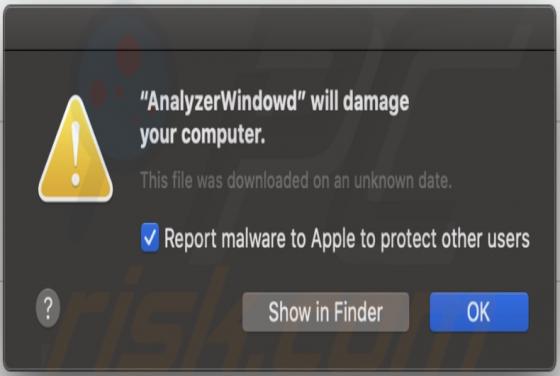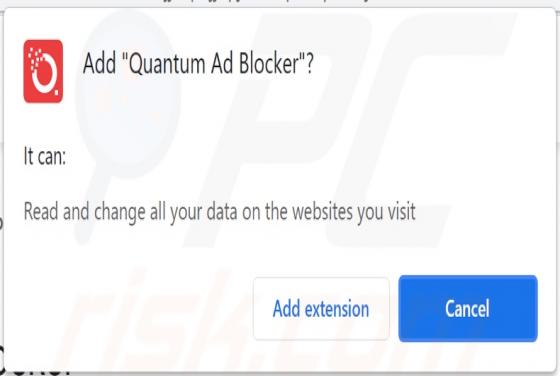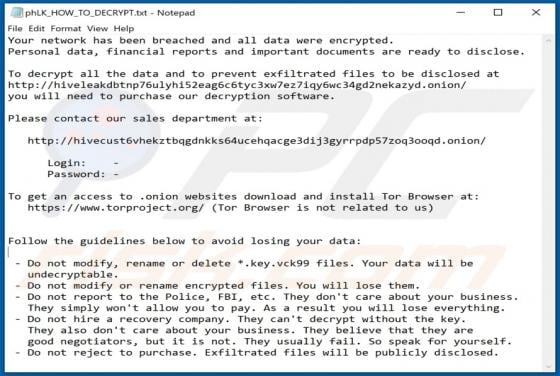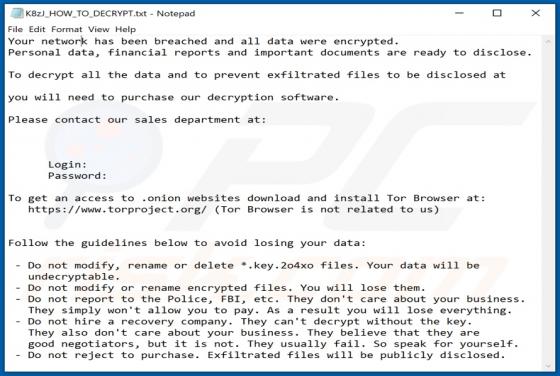
2o4xo Ransomware
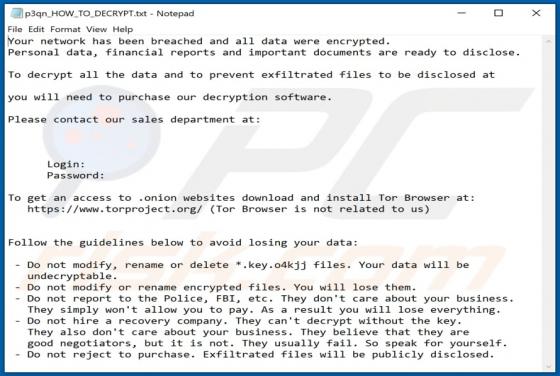
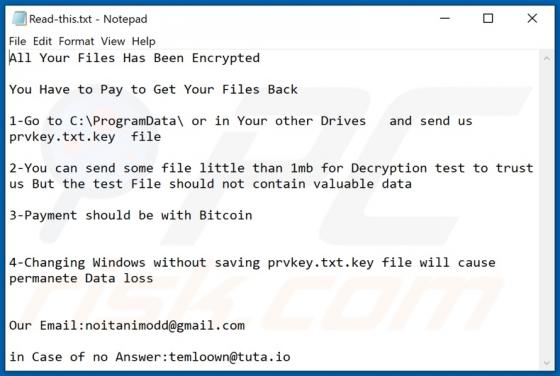
2o4xo is a piece of malicious software classified as ransomware. It is designed to encrypt data and demand payment for the decryption. Affected files are appended with a random character string and the ".2o4xo" extension. For example, a file initially titled "1.jpg" would appear as something simi