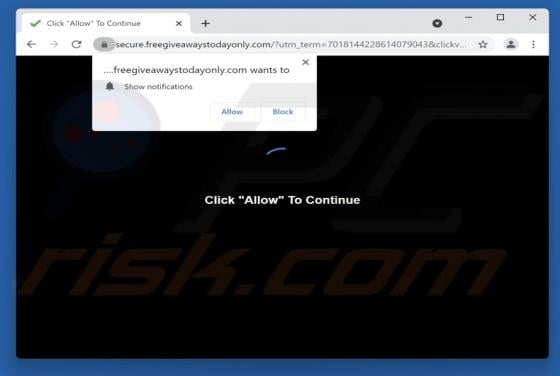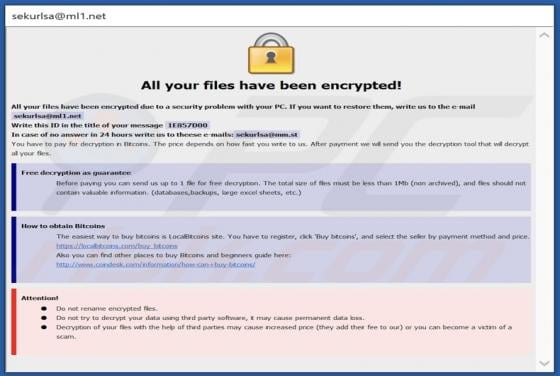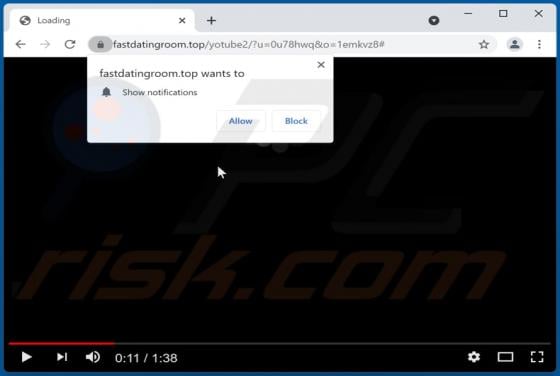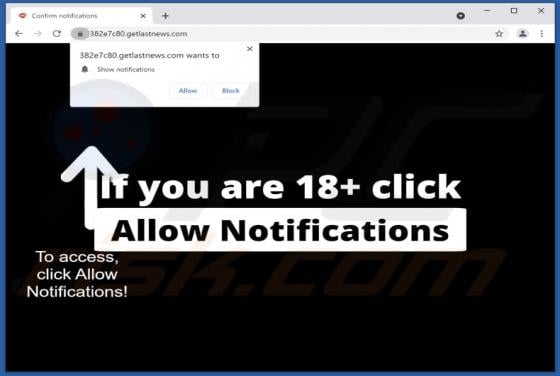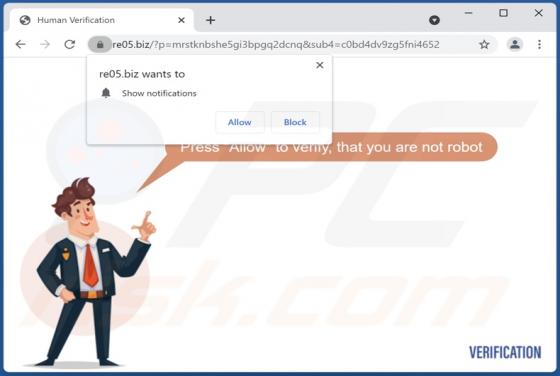
Wanacry Ransomware
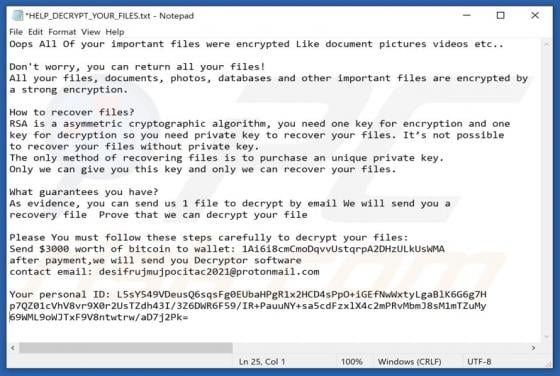
Wanacry is a type of malware that encrypts files, appends the ".wanacry" extension to filenames. For example, it renames a file named "1.jpg" to "1.jpg.wanacry", "sample.jpg" to "sample.jpg.wanacry". Wanacry also creates a ransom note (the "HELP_DECRYPT_YOUR_FILES.txt" file). Screenshot of a m